Hello folks,
This blog will be based on Examining the Database using Union-based SQL Injection vulnerabilities. We will understand how we can get the database version and information related to tables and columns present in the database. We will explore the same on the PortSwigger platform.
We have discussed the basics of Union-based SQL injection in our previous blog which you can explore. Let’s start and begin the penetration testing process.
Lab-1 SQL injection attack, querying the database type and version on Oracle
We can identify the database version based on different DBMS by exploiting Union-based SQL injection. We can refer to the SQL injection cheat sheet where under the “Database version” section, we have the useful syntax for querying the database version. In this scenario, we are exploring the same for Oracle databases.
We can read the lab description and click “Access the lab”. This lab can be performed without Burp Suite as well.
We must find a vulnerable parameter to exploit SQL injection attacks. On the home page, we will find different categories of products. Let’s click on any one of the categories to view some parameters. We can now see that we have a GET parameter on the URL named “category” where we can try to provide our malicious SQL query.
We know that this is an Oracle database so there is a mandatory condition that is required to fulfil. In Oracle databases, it is compulsory to provide the “FROM” keyword with a valid table name. Now, let’s create a payload to determine the number of columns. We can start with a single null keyword and then increase it one by one as follows:
‘ UNION SELECT null from dual––
‘ UNION SELECT null,null from dual––
We will find that the second query gives you a valid response which means that there are two columns. Now let’s find out the data type of each column using the following statements:
‘ UNION SELECT ‘a’,null from dual––
‘ UNION SELECT null,’b’ from dual––
Both statements provided a non-error value which confirms that these columns have varchar data type.
Finally, we will use the following query to get the version detail of the Oracle database:
‘ UNION SELECT banner,’a’ from v$version––
Hence, we successfully got the version details related to the Oracle database using the Union attack.
Lab-2 SQL injection attack, querying the database type and version on MySQL and Microsoft
In this scenario, we will identify the database version of MySQL and Microsoft databases using Union-based SQL injection. Let’s explore it.
We can read the lab description and click “Access the lab”. This lab can be performed without Burp Suite as well.
We must find a vulnerable parameter to exploit an SQL injection attack. On the home page, we will find different categories of products. Let’s click on any one of the categories to view some parameters. We can now see that we have a GET parameter on the URL named “category” where we can try to provide our malicious SQL query.
To test the MySQL database, we need to make sure that we provide a space after adding the “––” symbol for comments. If we try to add a space at the end of the query on your browser, we will find that it will not accept the space. So, we have to URL encode the space and then mention it at the end of the malicious SQL query. Now, let’s create a payload to determine the number of columns. We can start with a single null keyword and then increase it one by one as follows:
‘ UNION SELECT null––%20
‘ UNION SELECT null,null––%20
We will find that the second query gives you a valid response which means that there are two columns. We are not required to find the data type of each column as we are targeting the MySQL database which has an exception. It doesn’t matter what data type is assigned to columns.
Finally, we will use the following query to get the version detail of the Oracle database:
‘ UNION SELECT @@version,null––%20
We will find the version of the MySQL database. Hence the lab is solved.
Lab-3 SQL injection attack, listing the database contents on non-Oracle databases
Using Union-based SQL injection, we can list the contents of the database like information related to tables and their columns so that further using this information, we can access all data stored in the database. In this scenario, we will target non-Oracle databases such as MySQL, Microsoft SQL, and PostgreSQL. Let’s explore it.
We can read the lab description and click “Access the lab”. This lab can be performed without Burp Suite as well.
We must find a vulnerable parameter to exploit an SQL injection attack. On the home page, we will find different categories of products. Let’s click on any one of the categories to view some parameters. We can now see that we have a GET parameter on the URL named “category” where we can try to provide our malicious SQL query.
Now, let’s create a payload to determine the number of columns. We can start with a single null keyword and then increase it one by one as follows:
‘ UNION SELECT null––
‘ UNION SELECT null,null––
We will find that the second query gives you a valid response which means that there are two columns. Now let’s find out the data type of each column using the following statements:
‘ UNION SELECT ‘a’,null––
‘ UNION SELECT null,’b’––
Both statements provided a non-error value which confirms that these columns have varchar data type.
Now, let’s get the information related to tables. When we target non-Oracle databases, we can send queries to information_schema.tables for getting table names and information_schema.columns for getting column names. The following statements will help us:
‘ UNION SELECT table_name,null from information_schema.tables––
‘ UNION SELECT column_name,null from information_schema.columns where table_name=’users_csgkjw’––
The first statement will provide all the table names from which we have to target the users table. Then we can use the second statement to get the column names present in the users table.
Now we know everything i.e. table name and its column name using which we can create the following statement to obtain the password of the administrator user:
‘ UNION SELECT username_getuem,password_frlhfy from users_csgkjw––
We successfully got the password for all users present in the users table.
To solve the lab, we have to click on the “My account” button and log in as administrator user.
Lab-4 SQL injection attack, listing the database contents on Oracle
In this scenario, we will get the information about table and column names for Oracle databases. Let’s begin the process.
We must find a vulnerable parameter to exploit an SQL injection attack. On the home page, we will find different categories of products. Let’s click on any one of the categories to view some parameters. We can now see that we have a GET parameter on the URL named “category” where we can try to provide our malicious SQL query.
We know that this is an Oracle database so there is a mandatory condition that is required to fulfil. In Oracle databases, it is compulsory to provide the “FROM” keyword with a valid table name. Now, let’s create a payload to determine the number of columns. We can start with a single null keyword and then increase it one by one as follows:
‘ UNION SELECT null from dual––
‘ UNION SELECT null,null from dual––
We will find that the second query gives you a valid response which means that there are two columns. Now let’s find out the data type of each column using the following statements:
‘ UNION SELECT ‘a’,null from dual––
‘ UNION SELECT null,’b’ from dual––
Both statements provided a non-error value which confirms that these columns have varchar data type.
Now, let’s get the information related to tables. When we target the Oracle database, we can send a query towards all_tables to get table name and all_tab_columns to get column name. The following statements will help us:
‘ union select null,table_name from all_tables––
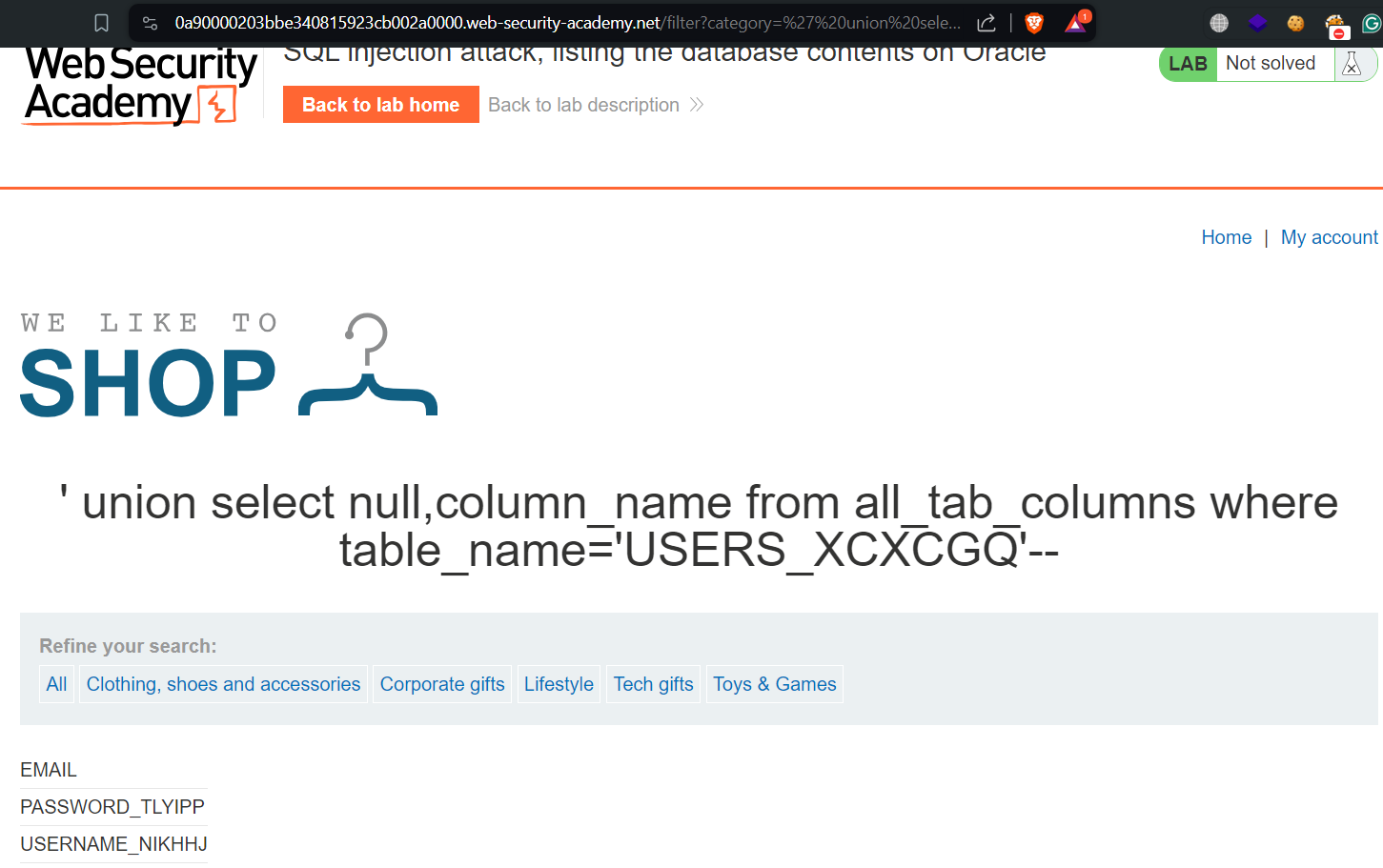
‘ union select null,column_name from all_tab_columns where table_name=’USERS_XCXCGQ’––
The first statement will provide all the table names from which we have to target the users table. Then we can use the second statement to get the column names present in the users table.
Now we know everything i.e. table name and its column name using which we can create the following statement to obtain the password of the administrator user:
‘ union select USERNAME_NIKHHJ,PASSWORD_TLYIPP from USERS_XCXCGQ––
We successfully got the password for all users present in the users table.
To solve the lab, we have to click on the “My account” button and log in as administrator user.
In this blog, we understood the concepts of exploring Union-based SQL injection to exploit the database. In the upcoming blogs, we will cover the concepts related to Blind SQL Injection vulnerability.
You can check out our other web application penetration testing blogs on our website.
Happy Pentesting!
Team CyberiumX