Hello Folks,
This blog will focus on API Testing where we will learn about APIs and their vulnerabilities using PortSwigger platform. All website consists of the API and it is very important to make them secure. In this blog post, we will explore the vulnerabilities using API documentation. Let’s understand about API in detail and then we will move forward and begin the penetration testing process to secure APIs.
API stands for Application Programming Interface which helps a website to communicate with different systems for sharing and accessing data. Using these APIs, the website receives the data from software systems or applications.
It is important to secure these APIs but firstly we have to find the API endpoint which is normally available at /api. Let’s understand it with the help of an example. Suppose we are making a GET request to /api/movie endpoint to fetch information related to all the movies. There can be other API endpoints available like /api/movie/horror, /api/movie/action, etc. to retrieve information related to horror and action movies respectively.
After identifying the endpoints, we can now send requests to them using various HTTP methods like GET, POST, PUT, DELETE, etc. Some API processes the input data provided by the user using different parameters. So, it is important to have information related to HTTP methods and their input parameters.
Now, the next important way to learn about the APIs is to look for documentation. These documents help the developer to work with the API. To discover these documents on the website using API, we can use the Burp Scanner or directory bursting techniques. If we have identified an endpoint like /api/movie/horror, it is always recommended to check all the paths like /api/movie, /api, etc. Also, we can use the Burp Intruder to brute-force the web pages using a wordlist of various API endpoints.
After getting a basic understanding of APIs let’s now try to find these API endpoints and exploit them using their documentation. We will be using PortSwigger’s lab to see the same in action.
Exploiting an API endpoint using documentation
Let’s read the lab description where we are provided with our credentials. We must identify the exposed API documentation and delete a user from the application. We will require the Burp Suite Community edition to solve the lab.
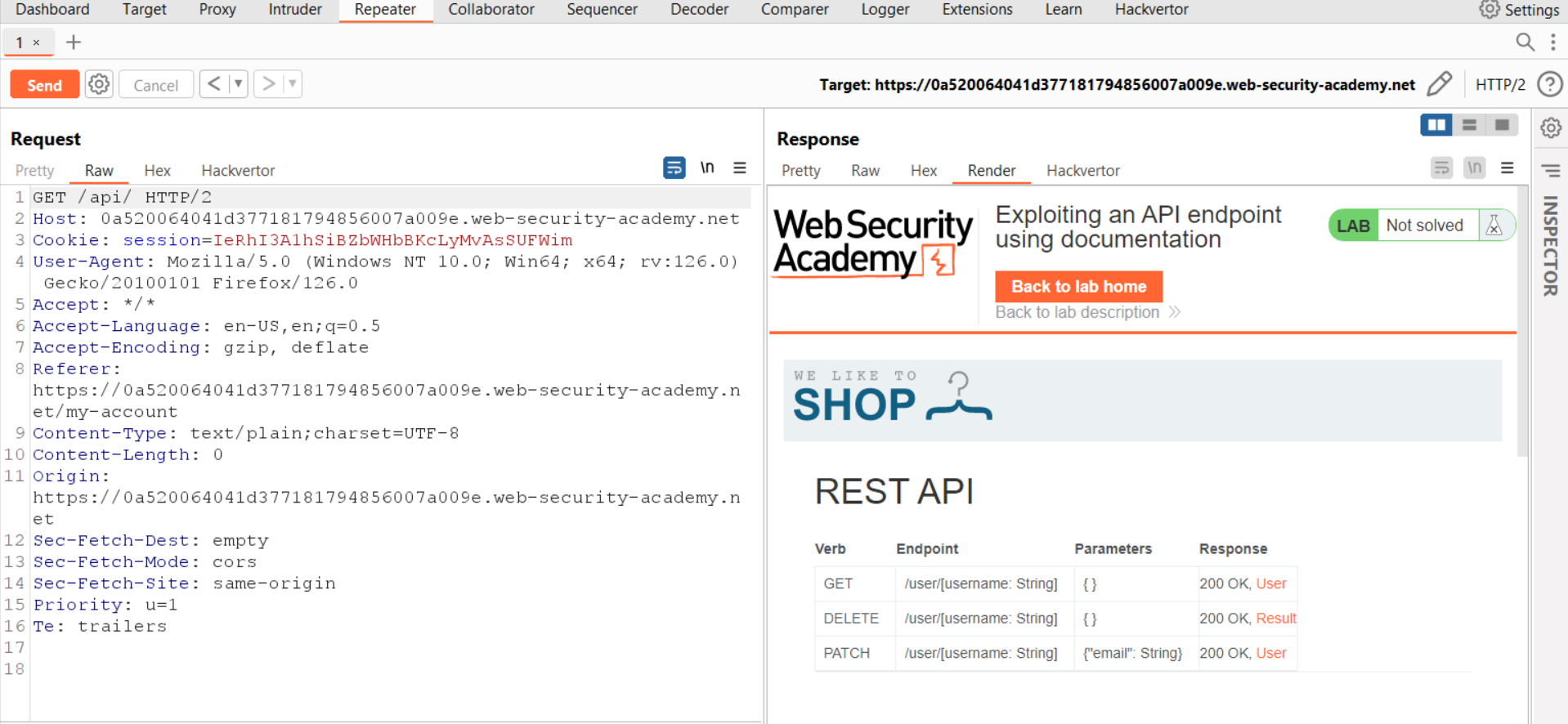
After accessing the target web application, we are required to log in as wiener user using our credentials on the /login page. Once we are logged in as wiener, we will find an email change functionality on our profile. Let’s change our email address to an arbitrary email. On Burp Suite, under HTTP history we will find a PATCH request towards /api/user/wiener which we need to select and send to Repeater. On Repeater, remove the username (wiener) from the endpoint and send the request. We will find an error as the username is not mentioned. Let’s now send a GET request to the /api endpoint and we will notice a response with the API documentation. We can click on the Render tab under the Response section to check the response. We will find other APIs which can perform various tasks.
To solve the lab, we have to delete a user from the application. We can see a DELETE HTTP method is available for the /api/user/<username> endpoint which might delete our target user. This functionality is interactive if we open the same on our browser by right-clicking on the request and selecting “Show response in browser”. Copy and paste the URL on the browser to access the same functionality. We can simply click on the DELETE row and enter the username as carlos to delete the user.
Also, we can use Burp Suite to do the same. We have to make some changes to the available request at Repeater. We have to change the HTTP method to DELETE and send the request to /api/user/carlos. As we click on the “Send” button to send the request to the web server, we will find that the user is successfully deleted from the application.
So this is how we can identify the API documentation and use it to exploit API-related vulnerabilities. Hence the lab is solved.
In this blog post, we have covered the basics of API and the vulnerability related to API documentation. You guys can explore our other PortSwigger blogs available on CyberiumX.
Happy Pentesting!
Team CyberiumX