Hello Folks,
All web applications use an Application Programming Interface (API) which is also vulnerable if exploited by an attacker. So as a penetration tester, we should know how to identify and exploit these API-related vulnerabilities. In this blog, we will understand the complete process which starts from identifying API endpoints, supported HTTP methods, and content types.
We will be exploring this vulnerability using PortSwigger’s lab. So without any more delays, let’s first understand what APIs are and begin the penetration testing process.
API is software that works as an intermediary and allows a website to access and share data from different systems across multiple organizations. It is important to secure these APIs as they carry data.
Now, we know about APIs and their importance, so we have to protect them from intruders. To understand the complete API penetration testing process, we will explore a PortSwigger lab. If you want to learn how to exploit API endpoints using documentation, then you can check out our previous blog.
Finding and exploiting an unused API endpoint
Let’s start by reading the lab description where we have to identify and exploit a hidden API endpoint to buy a product without spending any money. For this, we are provided with a credential pair. This lab can be easily solved using the Burp Suite Community edition.
After accessing the target website, we have to first log in with the credential pair as wiener user. To identify API endpoints, we have to interact with a web application to explore all the endpoints. We have many products on the home page, but our target is “Lightweight l33t Leather Jacket”. So, let’s click on it. We can see that the price of this product is $1337 and we have $0.0 in our balance, so we have to find an API endpoint that might help us here.
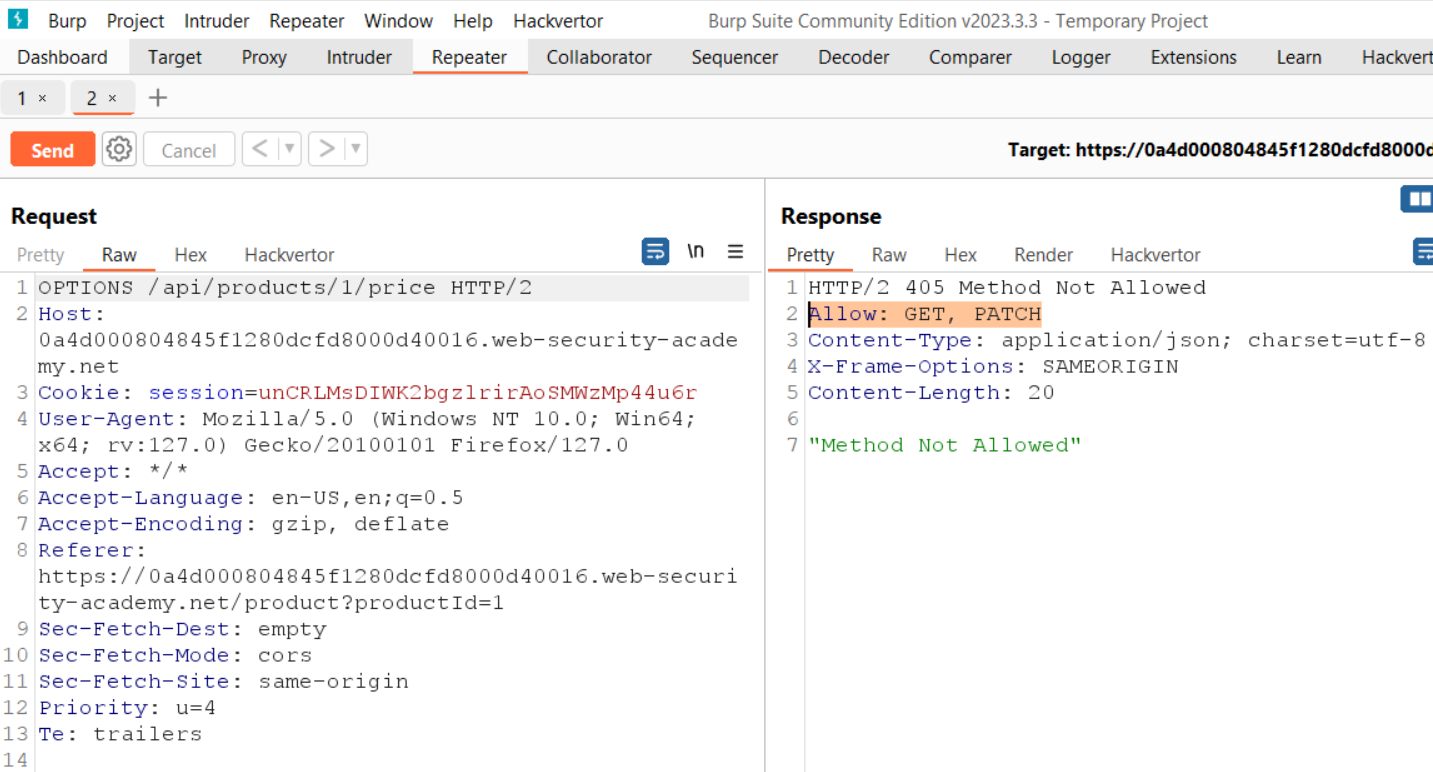
Let’s switch to Burp Suite and under the HTTP History tab, we will find a GET request to the /api/products/1/price endpoint. So we got our API endpoint and have to test it for which we need to take this request to Repeater. On Repeater, we can make some changes in the request, so let’s try to see which HTTP methods are supported by the server. We can simply confirm the same by replacing the GET with OPTIONS in the API request. After receiving the response for this request, we can see that only GET and PATCH methods are allowed.
Let’s change the GET method to PATCH and send the API request. We will get a response that says that the Content-Type header is missing and it should be application/json. So we have to add a Content-Type request header in the API PATCH request and set application/json as the value of the header. Also, as we added this header, so we have to add an empty JSON object {} in the body of the request. As we send this request, we will receive an error that says the price parameter is missing.
Let’s add a Price parameter in the request body and set the value of the price to 0 as follows:
{“price”:0}
Let’s send the request. We will find 200 responses. Let’s go to the browser and refresh the page. We will find that the product’s price has been changed to $0.00. So we have successfully exploited the API vulnerability and changed the price of “Lightweight l33t Leather Jacket”.
Now to solve the lab we have to add this product to our basket and then click on the “Place order” button to purchase the product without paying any cost. Hence the lab is solved.
In this blog post, we have covered the concepts of API and the vulnerability related to an insecure unused API endpoint. You guys can explore our other PortSwigger blogs available on CyberiumX.
Happy Pentesting!
Team CyberiumX