Hello Folks,
This blog focuses on HTTP Host Header vulnerability. We will cover the basics of the HTTP Host header and then we will see a practical implementation of identifying this vulnerability using the PortSwigger platform. In this blog, we will solve the “Basic password reset poisoning” lab under Password Reset Poisoning. So, let’s begin and understand this vulnerability before exploiting the same.
The host header is an HTTP request header that helps to specify which website we want to access. Without this header, our request will not be able to reach the actual web server.
The HTTP Host header vulnerability arises when the server processes the value of the Host header in an insecure way without validating it. The attacker can exploit this header and perform malicious server-side attacks like web cache poisoning, Business logic flaw, routing based SSRF, SQL injection, password reset poisoning, etc.
Here, we are going to see how we can perform a password reset poisoning attack using the Host Header vulnerability. In this attack, the attacker will try to poison the Password reset functionality of a website by pointing the password reset token to the attacker’s public server. Once the attacker can access the token value, the victim’s password can be easily changed.
Let’s understand the same with the help of PortSwigger’s lab.
Lab- Basic password reset poisoning
First, we will read the lab’s description and then click on the “Access the Lab” button. This lab can be solved using Burp Suite Community Edition.
Once the target application is up and running, we have to click on the “My account” button. We will find a login page here. We have to click on the “Forget your password?” button to target the password reset functionality. We need to provide the username/email of the account whose password we have to reset. We will provide “wiener” as the username.
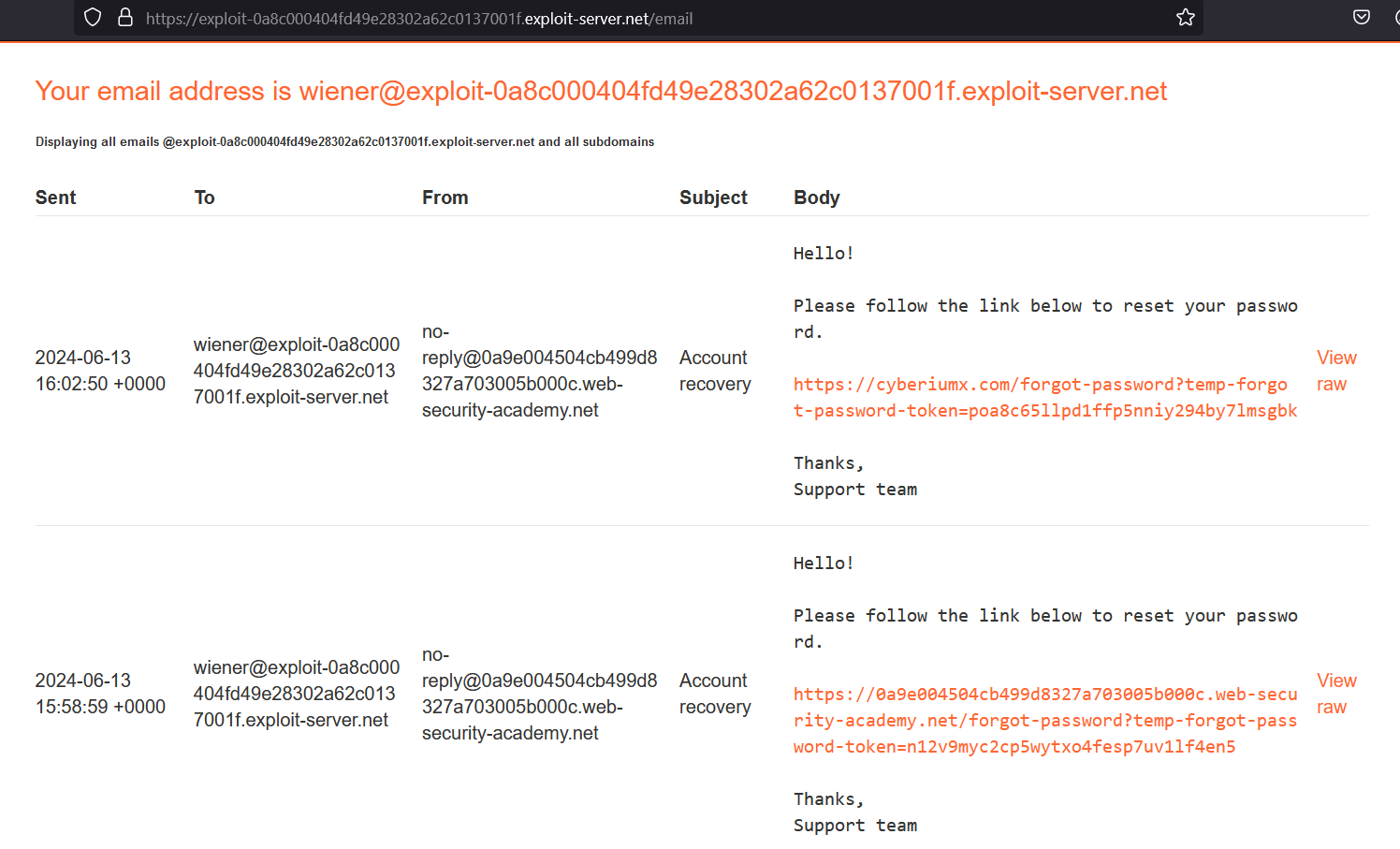
After submitting the username, we have to go to our exploit server and click on the “Email client” button to access the email server. We will find an email with the password reset link for the wiener user. Let’s click on the email to reset the password. We can provide a new password to reset the password of the wiener user. We can now log in as wiener user with the help of the new password.
Now we have to switch to Burp Suite and go to the “HTTP history” sub-tab where we will find a POST request to /forgot-password used to generate the password reset link for the wiener user. To identify HTTP Host header vulnerability, we have to take this request to Repeater and replace the original Host header with any arbitrary URL (cyberiumx.com). Once we send this request, we will find another password reset link on our email where the actual domain name is replaced with our arbitrary domain name.
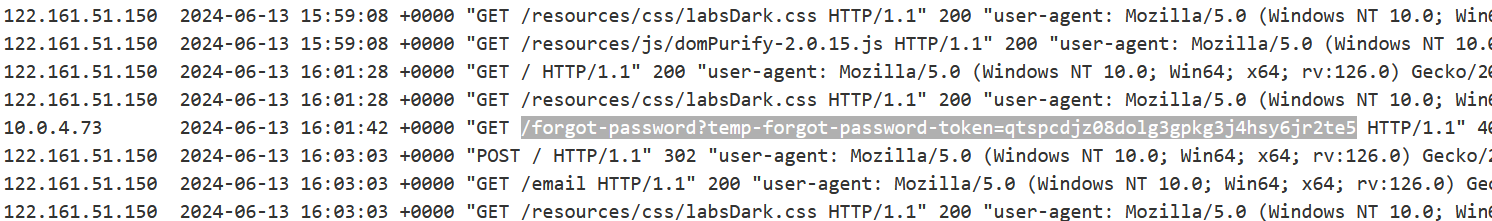
Let’s come back to Burp Repeater and this time we will change the value of the Host header to the URL of our exploit server. Also, we have to change the username to carlos so that we can send a password change email to our victim user. Now as soon as the user clicks on the link, their password reset token will be sent to our exploit server logs. Let’s check the logs of our exploit server by clicking on the “Access log” button available on our exploit server. There we will find an entry with the token of the victim user.
Let’s copy the token and send the following URL to reset the password of carlos user:
https://<Lab_URL>/forgot-password?temp-forgot-password-token=<Token_value>
As soon as we send this request, we will find a password reset page where we can provide a new password for carlos user. Now let’s log in as carlos user to solve the lab.
Using this lab, we understood how can we identify HTTP Host header vulnerability and exploit it to reset the password of any user. In the upcoming labs, we will explore more attacks using HTTP Host header vulnerability.
You can also explore other Web application vulnerabilities on our website.
Happy Pentesting!
Team CyberiumX