Hello folks,
In this write up, we will provide the answers of Logging for Accountability room which is a part of Security Engineer learning path under Managing Incidents section. This is freely accessible to all the users of TryHackMe. By successfully completing these challenges you will gain access to tickets that can boost your chances of winning incredible prizes.
You can access the room by clicking here.
Task 1- Introduction
This task will provide you Learning Objectives and Prerequisites for completing this room.
Read the above before continuing to the next task.
No answer required
Task 2- Importance of Logging and Data Aggregation
In this task, we will understand about Security Information and Event Management system (SIEM) and its benefits.
Q 2.1- A user being held accountable for their actions, as proven by logs, is known as what?
A 2.1- Non-Repudiation
Task 3- Log Ingestion and Storage
In this task, we will learn about the components of SIEM such as Search Head, Indexer and Forwarder.
Q 3.1- What component of an SIEM is responsible for searching data?
A 3.1- Search head
Q 3.2- How many years must all audit data be stored to be PCI DSS compliant?
A 3.2- 1
Task 4- Types of Logs and Data Sources
In this task, we will understand about the types of log sources such as Manual, automated and other types of log sources.
Q 4.1- A change log is an example of what log source?
A 4.1- Manual
Q 4.2- An application log is an example of what log source?
A 4.2- Automated
Task 5- Using Logs Effectively
In this task, we will learn about how to perform logging effectively.
Q 5.1- What is the process of using multiple log types and sources as part of incident response formally known as?
A 5.1- Correlation
Task 6- Improving Incident Response with Accountability
In this task, we will perform the log analysis using Splunk.
Q 6.1- How many total events are indexed by Splunk?
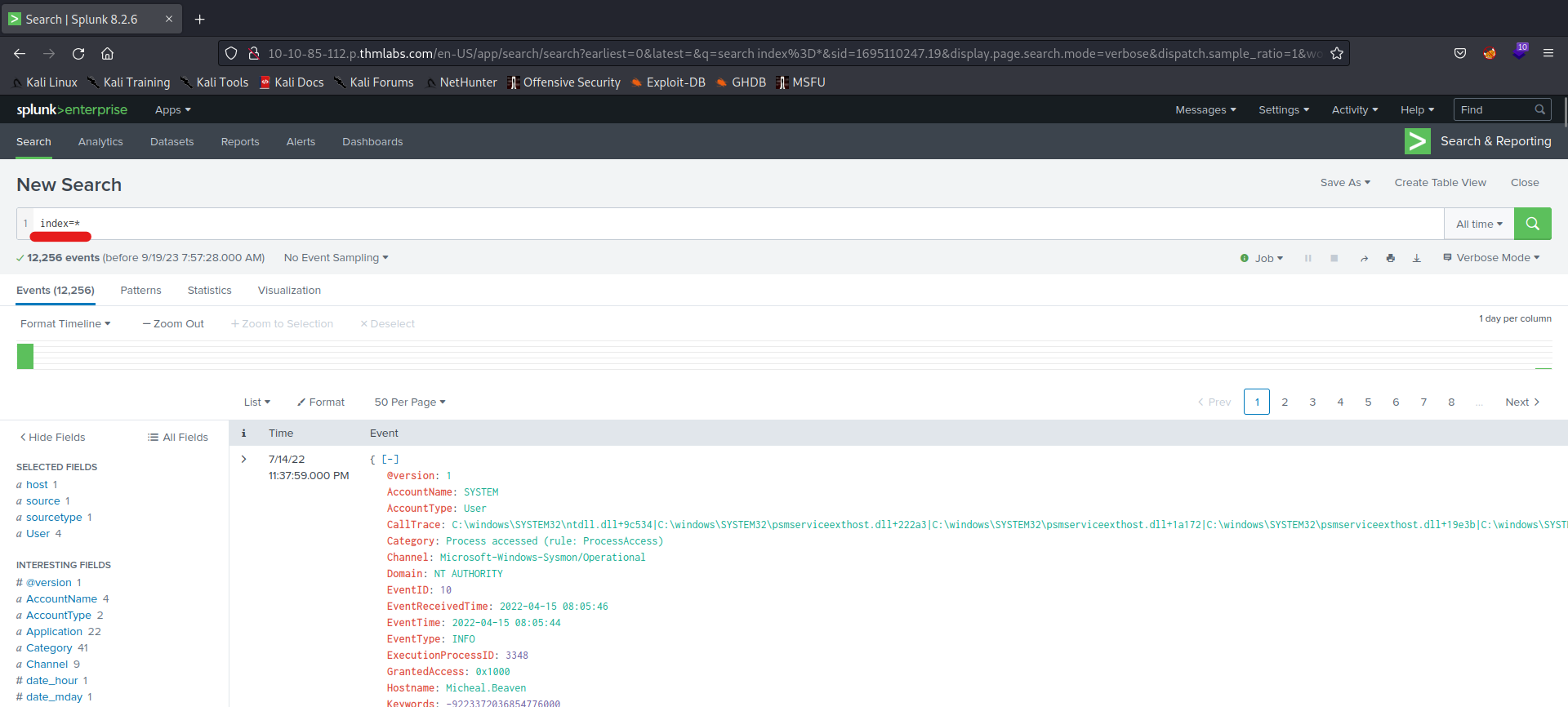
A 6.1- 12,256
Q 6.2- How many events were indexed from April 15th to 16th 2022?
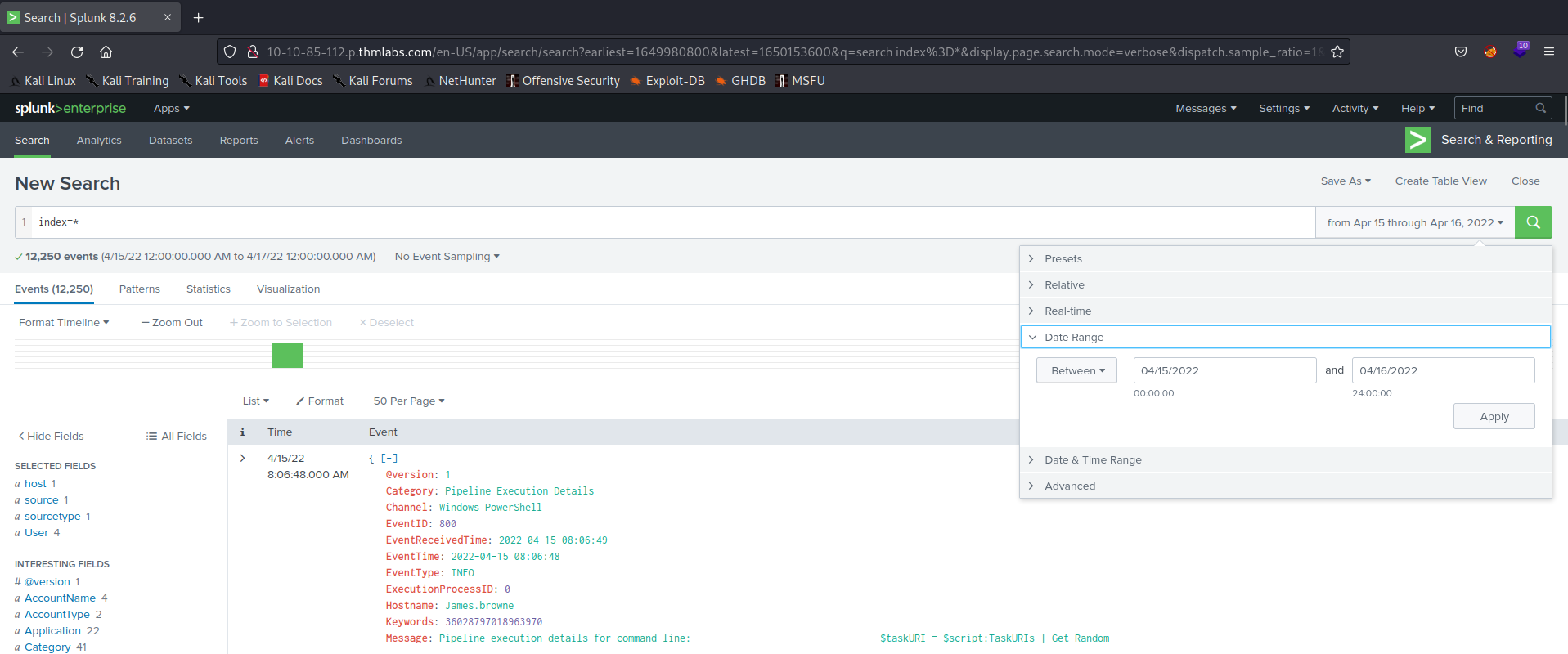
A 6.2- 12,250
Q 6.3- How many unique users appear in the data set?
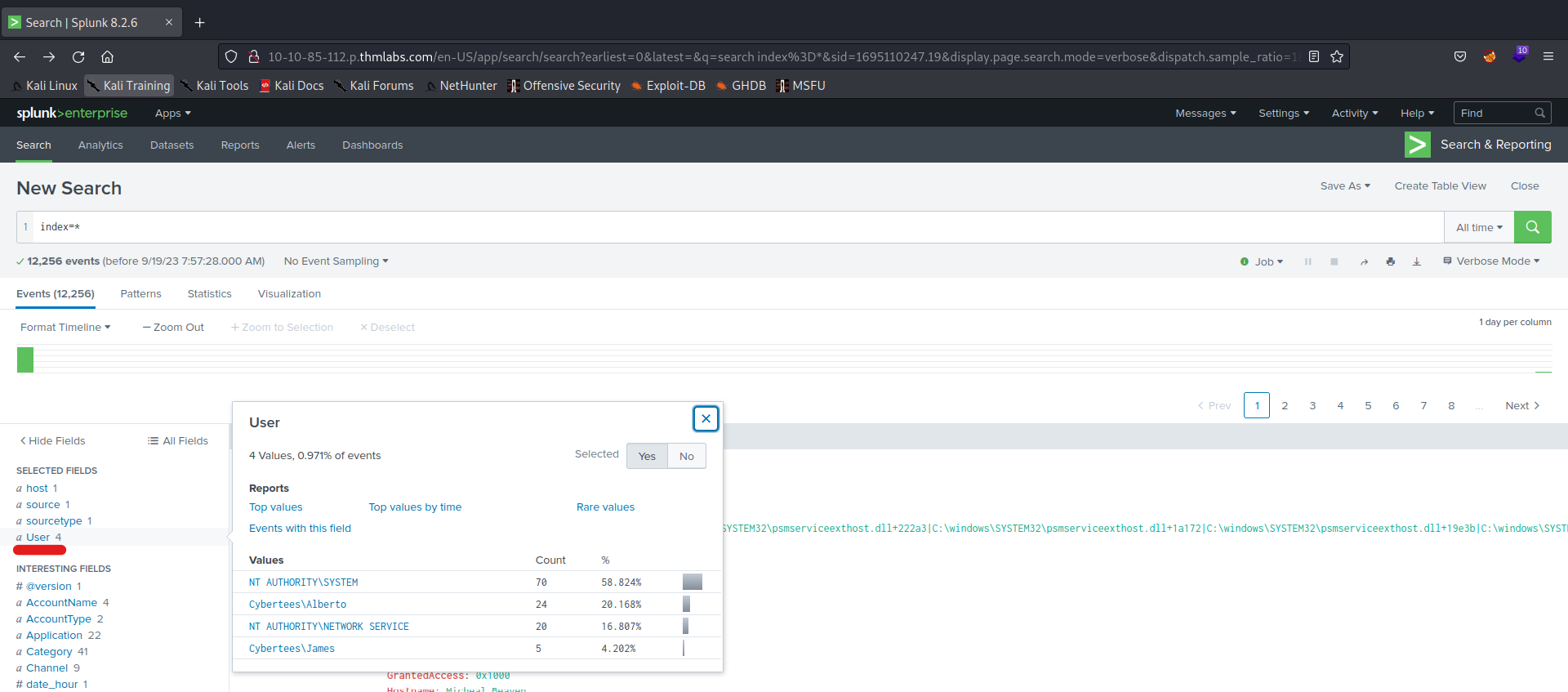
A 6.3- 4
Q 6.4- How many events are associated with the user James”?
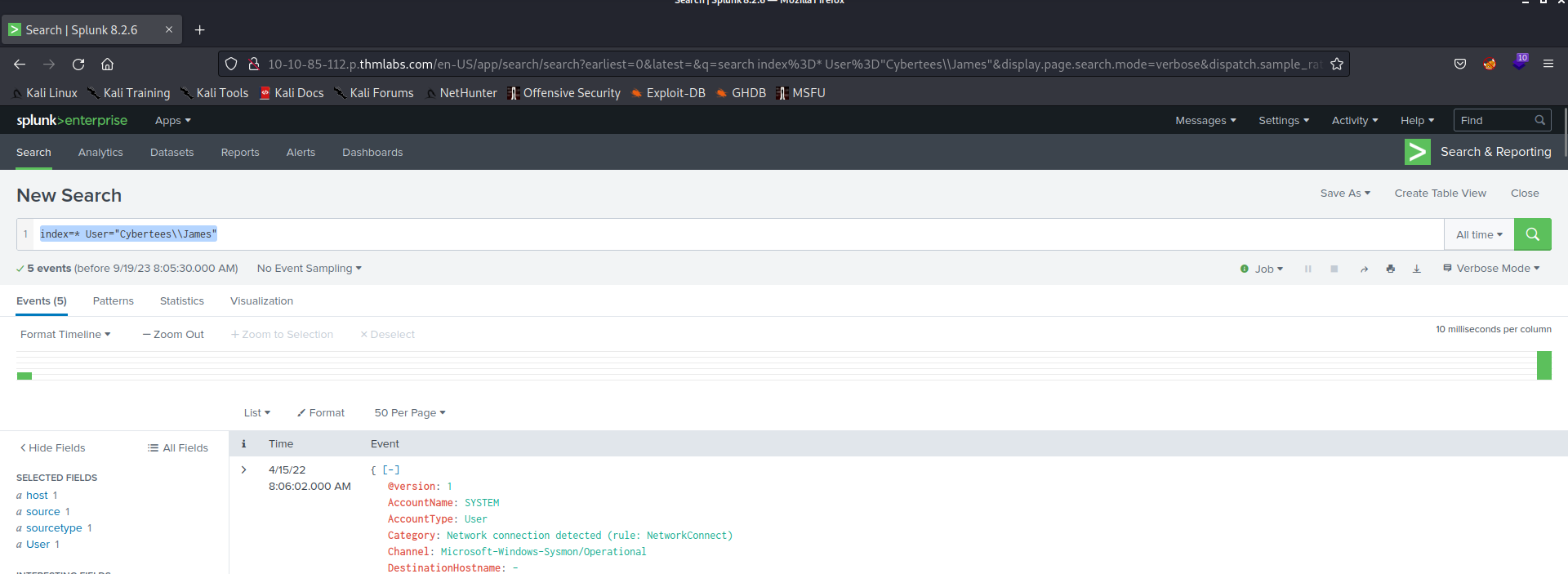
A 6.4- 5
Q 6.5- What utility was used in the oldest event associated with “James”?
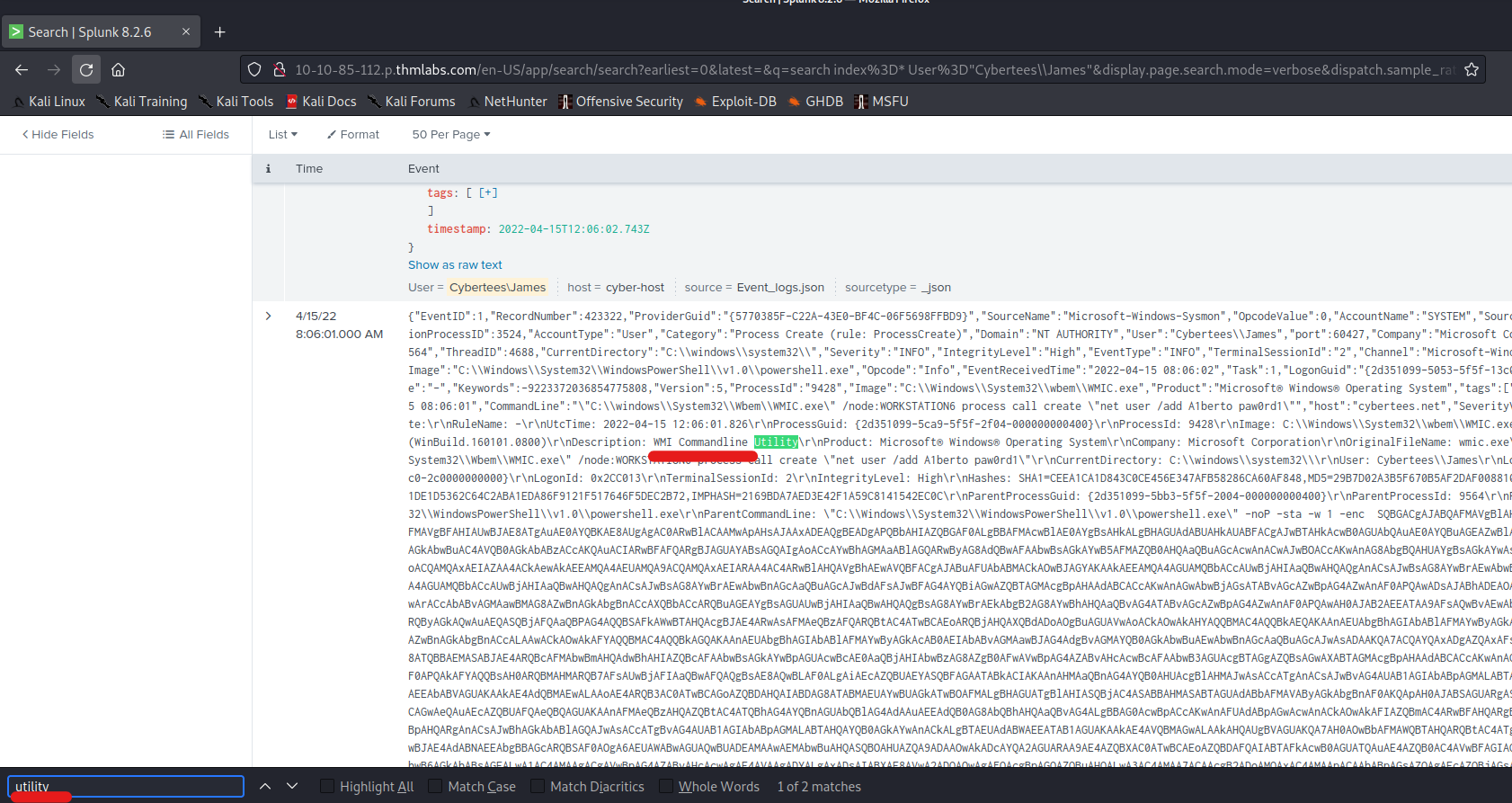
A 6.5- WMIC
Q 6.6- What event ID followed process creation events associated with “James”?
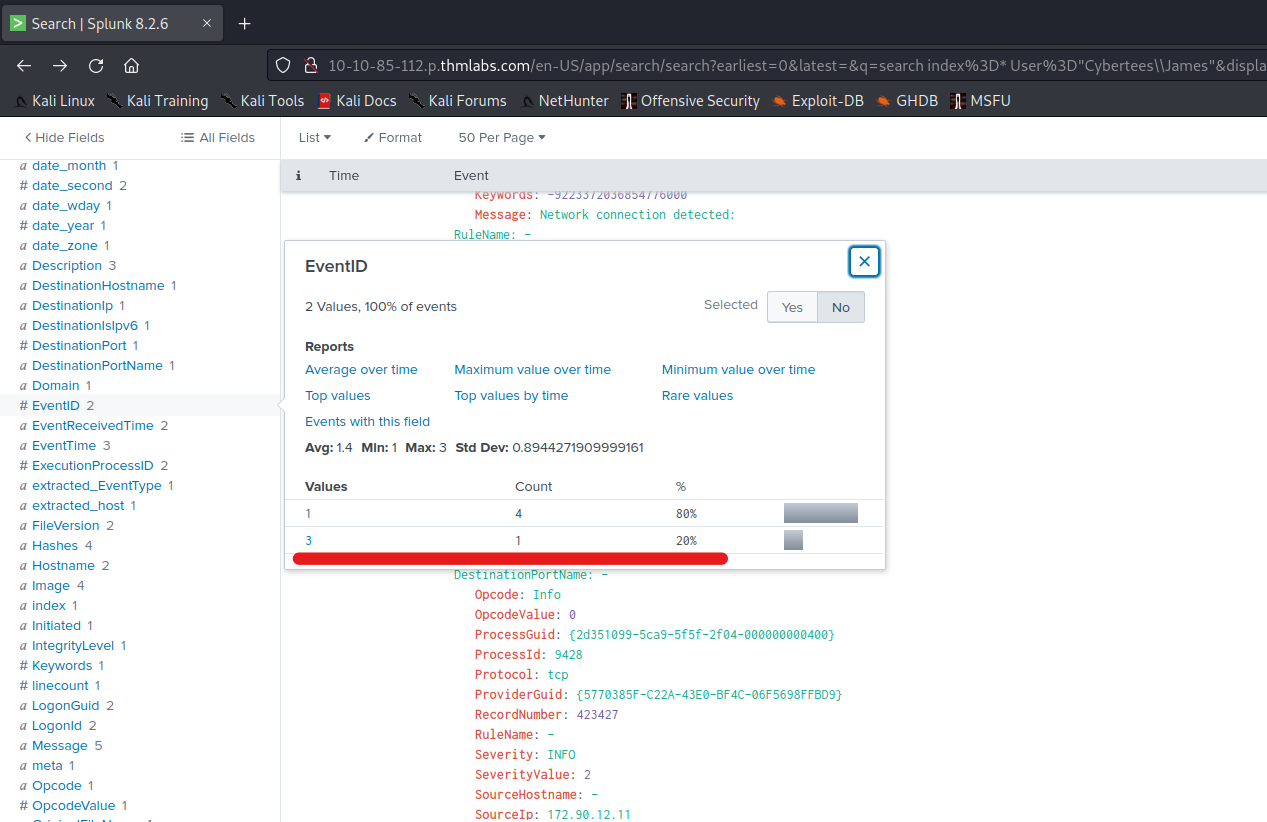
A 6.6- 3
We will be providing the answers for Security Engineer Learning Path. If you need the explanation to these answers, please comment below and we will provide the explanation as per request.
You can check out our other blogs here.
Happy Pentesting!!!
Team CyberiumX

