Hello folks,
In this write up, we will provide the answers of Threat Modelling room which is a part of Security Engineer learning path under Threats and Risks section. This is freely accessible to all the users of TryHackMe. By successfully completing these challenges you will gain access to tickets that can boost your chances of winning incredible prizes.
You can access the room by clicking here.
Task 1- Introduction
This task will let you know the learning objectives and prerequisites of this room.
Let’s start modelling threats!
No answer required
Task 2- Threat Modelling Overview
This task will explain the difference between threat, risk and vulnerability, process of threat modelling and will help us understand the role and purpose of different teams in an organization.
Q 2.1- What is a weakness or flaw in a system, application, or process that can be exploited by a threat?
A 2.1- Vulnerability
Q 2.2- Based on the provided high-level methodology, what is the process of developing diagrams to visualise the organisation’s architecture and dependencies?
A 2.2- Asset Identification
Q 2.3- What diagram describes and analyses potential threats against a system or application?
A 2.3- Attack Tree
Task 3- Modelling with MITRE ATT&CK
This task will help you understand the concepts of MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework and how can we apply and utilise this framework in Threat Modelling Process.
Q 3.1- What is the technique ID of “Exploit Public-Facing Application”?
A 3.1- T1190
Q 3.2- Under what tactic does this technique belong?
A 3.2- Initial Access
Task 4- Mapping with ATT&CK Navigator
In this task you will learn about the famous open-source tool called ATT&CK Navigator which helps the security teams to determine matrices based on threat scenario.
Q 4.1- How many MITRE ATT&CK techniques are attributed to APT33?
A 4.1- 31
Q 4.2- Upon applying the IaaS platform filter, how many techniques are under the Discovery tactic?
A 4.2- 13
Task 5- DREAD Framework
In this task you will understand what is DREAD (Damage, Reproducibility, Exploitability, Affected Users and Discoverability) framework and its guidelines for qualitative Risk Analysis.
Q 5.1- What DREAD component assesses the potential harm from successfully exploiting a vulnerability?
A 5.1- Damage
Q 5.2- What DREAD component evaluates how others can easily find and identify the vulnerability?
A 5.2- Discoverability
Q 5.3- Which DREAD component considers the number of impacted users when a vulnerability is exploited?
A 5.3- Affected Users
Task 6 STRIDE Framework
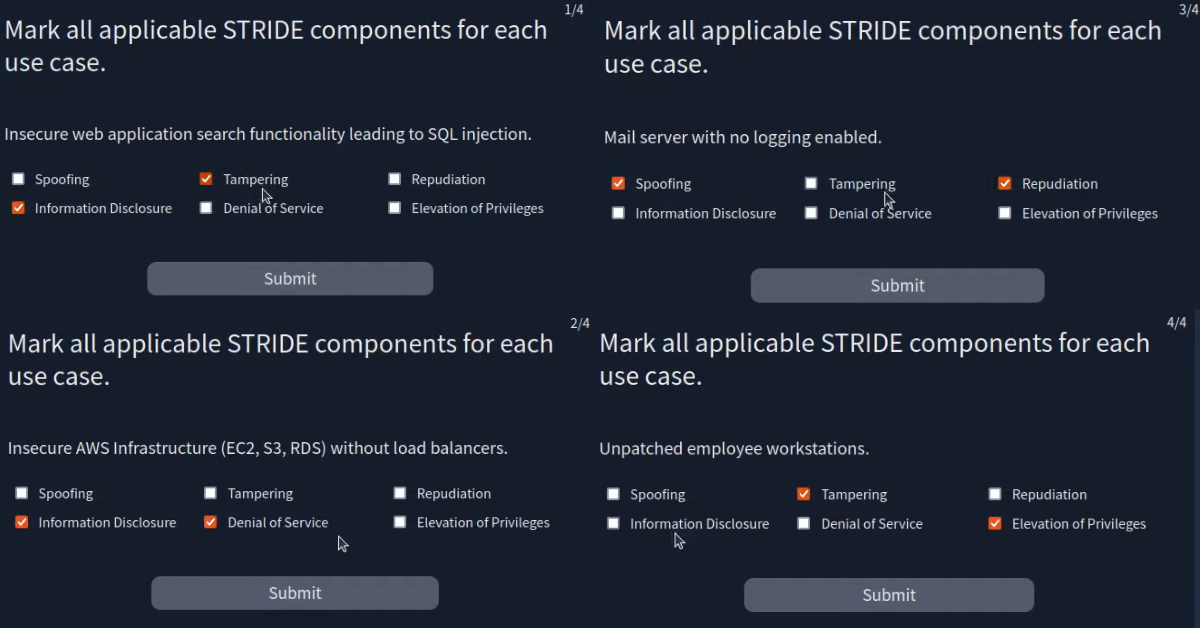
In this task you will learn about STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service and Elevation of Privilege) framework and its application over Threat Modelling.
Q 6.1- What foundational information security concept does the STRIDE framework build upon?
A 6.1- CIA Triad
Q 6.2- What policy does Information Disclosure violate?
A 6.2- Confidentiality
Q 6.3- Which STRIDE component involves unauthorised modification or manipulation of data?
A 6.3- Tampering
Q 6.4- Which STRIDE component refers to the disruption of the system’s availability?
A 6.4- Denial of Service
Q 6.5- Provide the flag for the simulated threat modelling exercise.
A 6.5- THM{m0d3ll1ng_w1th_STR1D3}
Task 7- PASTA Framework
In this task you will understand about another important framework called PASTA (Process for Attack Simulation and Threat Analysis) framework. You will learn about the guidelines, benefits and applications of PASTA Framework.
Q 7.1- In which step of the framework do you break down the system into its components?
A 7.1- Decompose the Application
Q 7.2- During which step of the PASTA framework do you simulate potential attack scenarios?
A 7.2- Analyse the Attacks
Q 7.3- In which step of the PASTA framework do you create an inventory of assets?
A 7.3- Define the Technical Scope
Q 7.4- Provide the flag for the simulated threat modelling exercise.
A 7.4- THM{c00k1ng_thr34ts_w_P4ST4}
We will be providing the answers for Security Engineer Learning Path. If you need the explanation to these answers, please comment below and we will provide the explanation as per request.
You can check out our other blogs here.
Happy Pentesting!!!
Team CyberiumX