Hello folks,
In this blog, we will be discussing one of the most popular certificates for beginners in the field of Cybersecurity. The name of the certification is Certified in Cybersecurity (CC) which is provided by (ISC)2 organization.
ISC2 is providing its free registration for Certified in Cybersecurity certification exam. This certification can help you to enter the Cybersecurity domain that has limitless opportunities throughout the world.
If you want to get this certification for no cost, please follow this blog which will help you to register as well as book an appointment to sit for this exam.
About (ISC)2
International Information System Security Certification Consortium, popularly known as (ISC)2, is an organization devoted to the field of cybersecurity. The organization’s motive is to strengthen the security of companies by promoting Cybersecurity and providing good certification courses to build knowledgeable and highly skilled cybersecurity professionals. The most popular certifications of (ISC)2 are Certified Information Systems Security Professional (CISSP), Certified Cloud Security Professional (CCSP), Certified Authorization Professional (CAP) and many more. Also, they have a beginner level certification recognized as Certified in Cybersecurity (CC) which will help you to provide the first step to advance your career in cybersecurity domain. This certification is available for free under a global initiative ‘One Million Certified in Cybersecurity’ taken by (ISC)2 organization.
Overview of Certified in Cybersecurity (CC) Certification
Certified in Cybersecurity course and exam is an entry level certification which will provide you skills and knowledge to begin your career in the cybersecurity domain. This certification requires no work experience. Upon successful completion, the certification serves as evidence of your skills, knowledge, and qualifications suitable for a junior or entry-level position in cybersecurity.
The CC exam will test your ability on the following five domains of cybersecurity:
- Security Principles
- Business Continuity, Disaster Recovery & Incident Response Concepts
- Access Controls Concepts
- Network Security
- Security Operations
Examination information for Certified in Cybersecurity certification
- Duration of Exam- 2 hours
- Number of MCQs- 100
- Passing Percentage- 70%
- Examination Center- Pearson VUE
The domain weightage is as follows:
- Security Principles- 26%
- Network Security- 24%
- Access Controls Concepts- 22%
- Security Operations- 18%
- Business Continuity, Disaster Recovery & Incident Response Concepts- 10%
You can read the PDF provided by (ISC)2 for more details.
Process of Registration
Now, let’s see how to register and become an (ICS)2 Candidate:
1. Visit the (ISC)2 website where you will find the Registration URL to create a new account.
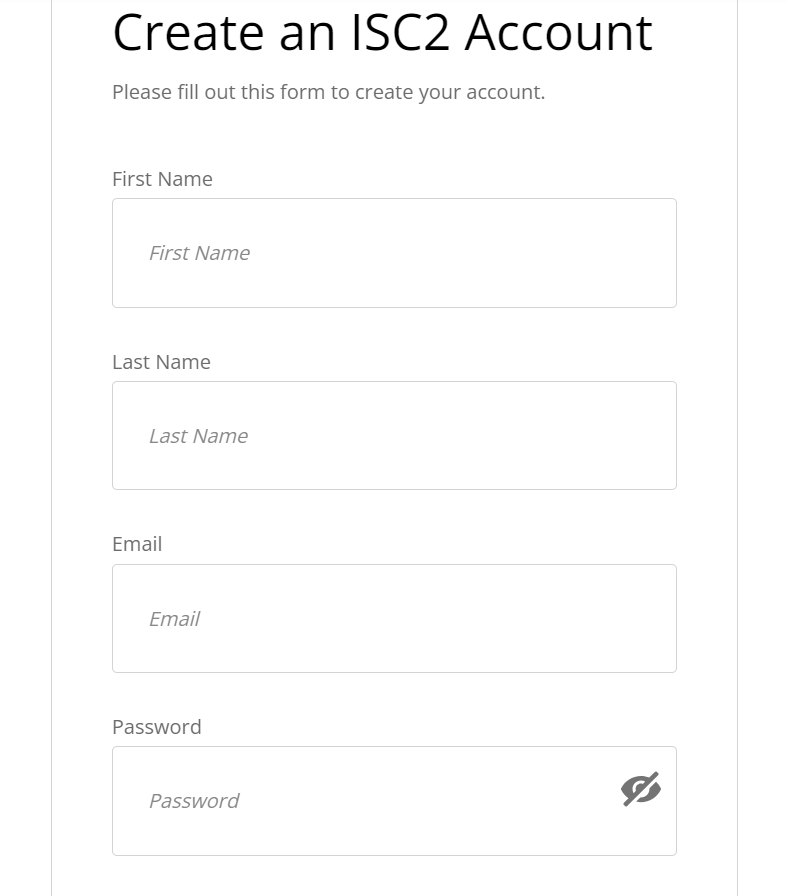
2. On the registration page, you have to provide your details such as Name, Email and Strong Password.
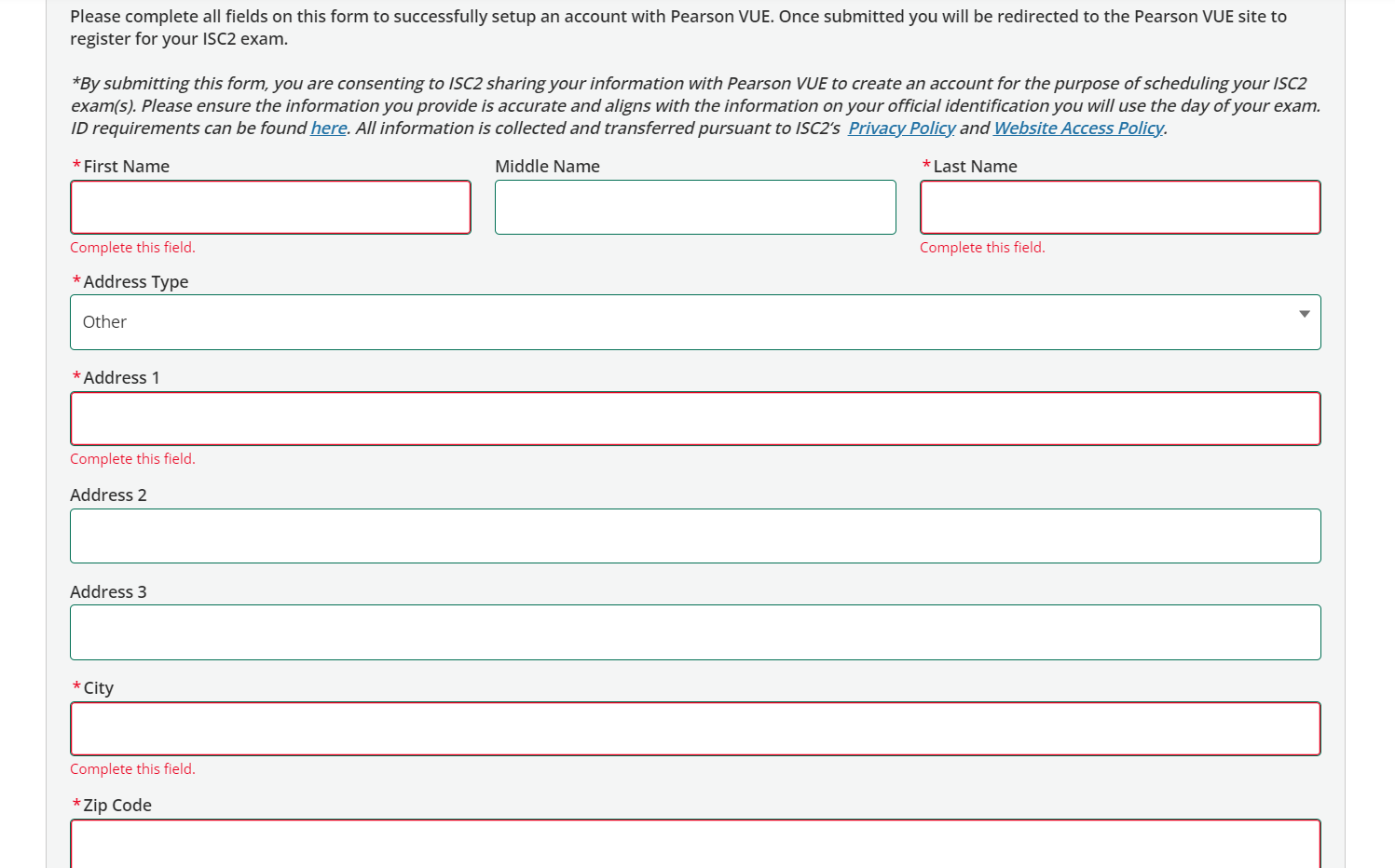
3. After creating your account, you will be redirected to Pearson VUE portal where you have to provide some other information such as Address, Phone number, Education details, Job related information, etc.
4. Your account will be created once your details are submitted. Now you will be redirected to the Dashboard of ‘Pearson VUE’.
Process of Exam Scheduling
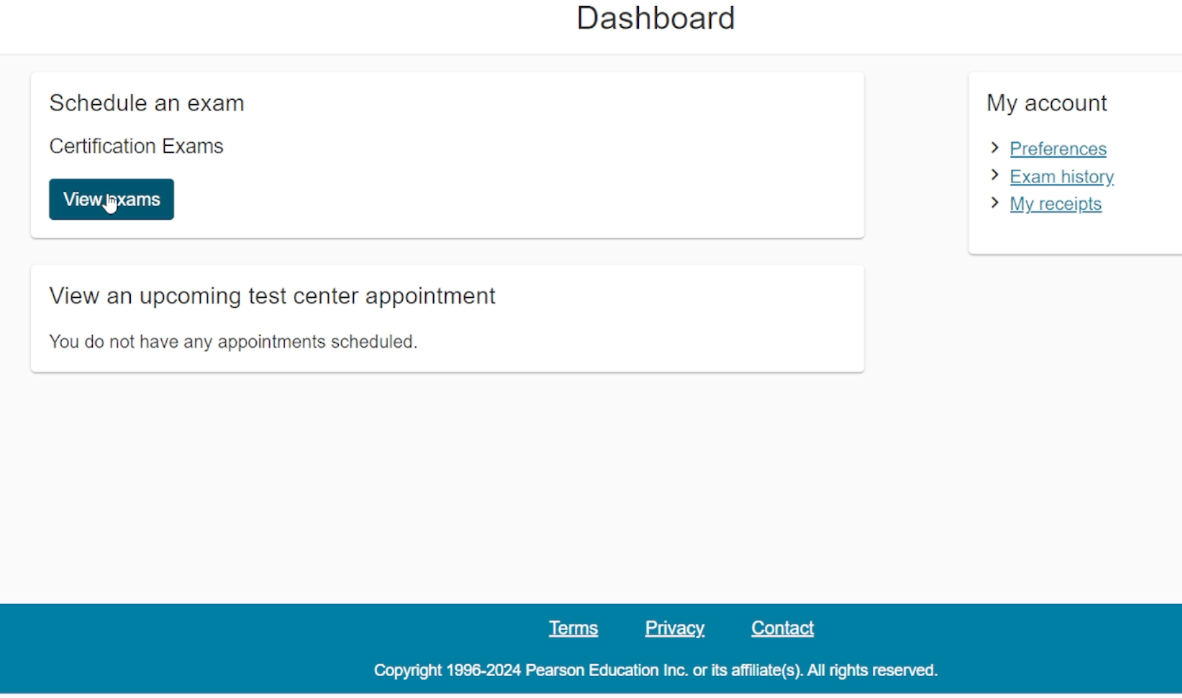
1. On the Pearson VUE Dashboard, click on View Exam button in order to schedule your CC exam.
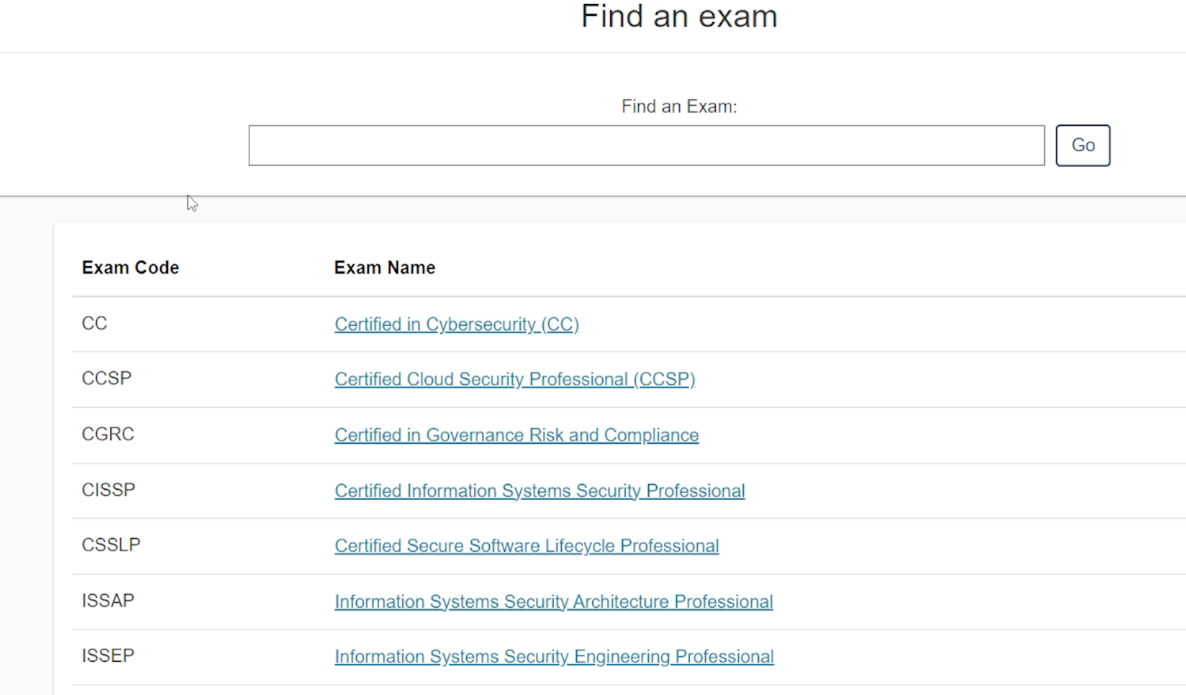
2. Select the Certified in Cybersecurity (CC) exam from the list.
3. Next step is to choose a suitable Language for the exam. You can choose English as your preferred language.
4. Next step is to confirm the exam selection. You can click on Next after confirming the exam that you have selected.
5. Now you have to read the Terms & Conditions of (ISC)2 exam. You can read the guidelines for the exam, reschedule and cancellation policies and then click on Next.
6. In the next step, you have to select an appropriate Pearson VUE Test Center. By default you will be provided with a list of test centers which are near to your home/office location that you have provided while registration. Select any one location where you want to schedule your exam.
7. Now you will be asked to select Date & Time for your exam. You can select a date after 2-3 months as per your convenience. You can click on ‘Explore more times’ to look for other available time for any specific date. Please make sure you have enough time to prepare for this exam. After selecting the Date & Time, you can click on Book this Appointment.
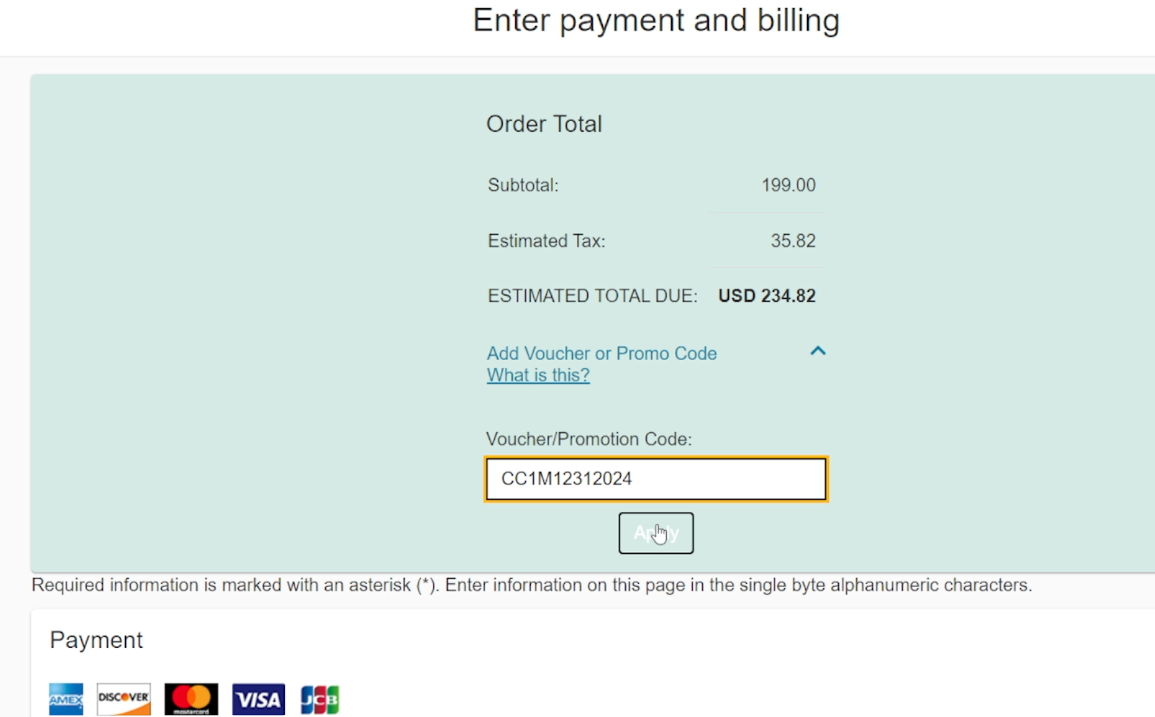
8. Now you will be redirected to your cart where you will find the CC exam is added and the amount for this exam which should be USD 199 (excluding taxes). Please don’t worry as you have to apply for the free coupon for this exam on the checkout page. You can click on Proceed.
9. In the Payment and Billing page, you have an option to ‘Add Voucher or Promo Code’ where we can provide an available Voucher for a free exam. The current voucher as per 2024 year is ‘CC1M12312024’. This voucher is valid till 31 December 2024. Please make sure to search on social media platforms of (ISC)2 for the appropriate voucher as per your exam. Finally click on Apply.
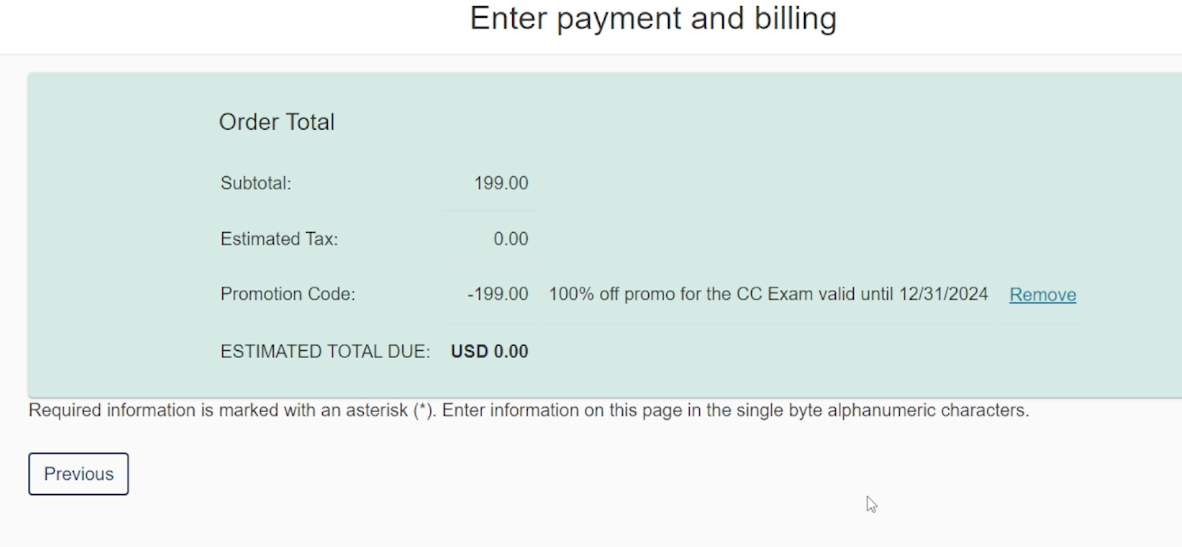
10. You will find that the cost of the exam is reduced to USD 0. Now click on Next.
11. You will reach the final page where you can confirm your details and book your exam for free.
12. You will receive an Email from Pearson VUE for your exam schedule.
We hope that the procedure is clear to you guys and we extend our best wishes as you prepare for this exam. If you have any questions about the procedure or require assistance in preparing for the certification exam, feel free to leave a comment, and we will ensure you receive the necessary support.
Keep Learning !!
Team CyberiumX